What is Qlocker virus
Qlocker virus is a new malware that belongs to the category of ransomware. Ransomware usually encrypt files, but this malware works differently. It does not encrypt files directly, but archives them with a password. Qlocker virus uses the 7z archiver, so the extension of all infected files is changed to .7z. So, if the file had a name “photo.jpg”, then after encryption its name will change to “photo.7z”, a file with the name “document.docx” will be renamed to “document.7z”, “info.pdf” to “info.7z”, and so on. When all files are encrypted, the virus creates a file named “!!!READ_ME.txt”, which contains the cybercriminals’ demands. To date, it is known that Qlocker targets only QNAP brand Network-attached storage (NAS) devices; security researchers have not found other types of devices infected with this malware.
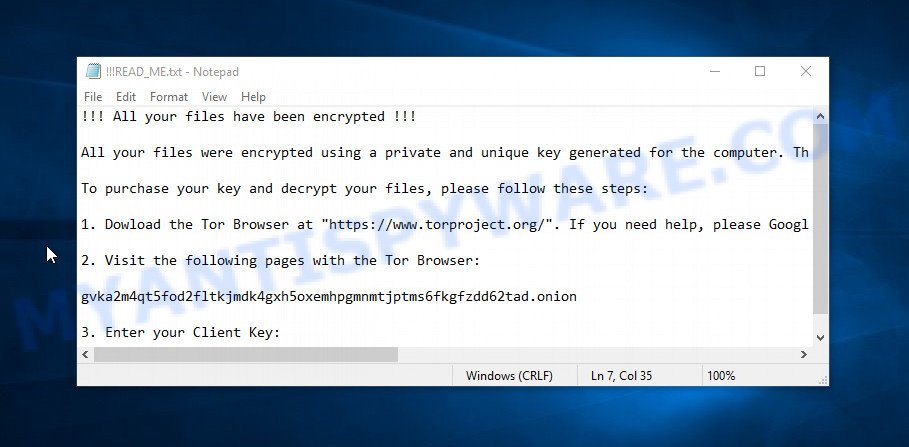
Qlocker virus – ransom note
QUICK LINKS
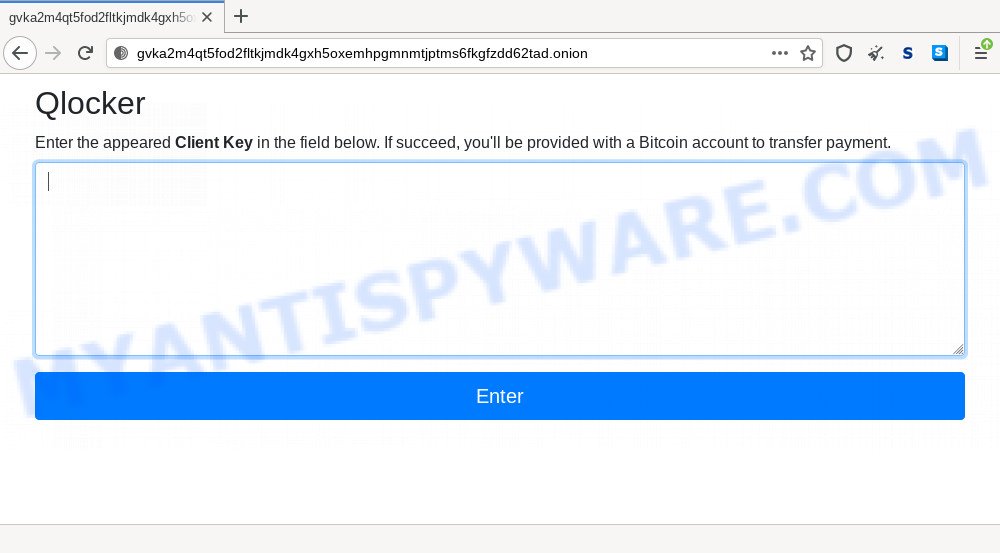
The ‘!!!READ_ME.txt’ file is a ransom note that is a message from the Qlocker creators. In this message, the criminals report that the victim’s files are encrypted and there is only one way to decrypt them – purchase the key from them. Although the message does not indicate the price of the key, it is usually at least $500, and in some cases reaches several thousand dollars or more. To find out the exact size of the ransom and to decrypt the files, attackers instruct victims to go to the gvka2m4qt5fod2fltkjmdk4gxh5oxemhpgmnmtjptms6fkgfzdd62tad.onion website using the TOR browser. To access this site, victims will need a “Client Key”, which is listed at the bottom of the ‘!!!READ_ME.txt’ file. After entering the key, a page is displayed that states that the value of the key is 0.01 bitcoin, which at the current exchange rate is about $500 (this amount is not fixed, since the bitcoin exchange rate is constantly changing). After paying the ransom (transferring 0.01 bitcoin to the attackers’ account), the victims must enter the transfer ID and submit it. After that, the attackers promise to provide a password to decrypt the encrypted files.
Text presented in the ransom note:
!!! All your files have been encrypted !!!
All your files were encrypted using a private and unique key generated for the computer. This key is stored in our server and the only way to receive your key and decrypt your files is making a Bitcoin payment.
To purchase your key and decrypt your files, please follow these steps:
1. Dowload the Tor Browser at “https://www.torproject.org/”. If you need help, please Google for “access onion page”.
2. Visit the following pages with the Tor Browser:
gvka2m4qt5fod2fltkjmdk4gxh5oxemhpgmnmtjptms6fkgfzdd62tad.onion
3. Enter your Client Key:
While attackers always promise to provide a key or software to decrypt files after paying the ransom, this is not always the case. In some cases, attackers simply ignore victims without sending them the key and decryptor; in other cases, having received the ransom, the attackers increase it, demanding additional payments from the victims. There are also cases when the ransomware contains bugs (flaws), due to which it is impossible to decrypt files at all. Thus, the payment of the ransom turns into a loss of money, the victim’s files remain locked. According to QNAP (the developer of devices affected by the Qlocker virus), it is strongly recommended to immediately download the malware removal utility from the official website (more information can be found in QNAP’s recent response). This tool is used to scan the device, find and remove malware. After scanning, it is recommended to contact the official QNAP Technical Support. It is important not to turn off the QNAP device. Unfortunately, removing Qlocker does not restore affected files; these files remain encrypted. Thus, only those files that the virus did not have time to encrypt remain accessible to the victim.
Threat Summary
| Name | Qlocker virus |
| Type | Crypto virus, Crypto malware, Filecoder, Ransomware, File locker |
| Files extension | .7z (in fact, an encrypted file is a “7z” archive with a password) |
| Ransom note | !!!READ_ME.txt |
| Cybercriminal Contacts | gvka2m4qt5fod2fltkjmdk4gxh5oxemhpgmnmtjptms6fkgfzdd62tad.onion using TOR browser |
| Symptoms | Encrypted personal files. Odd, new or missing file extensions. Files named such as ‘!!!READ_ME.txt’, ‘READ-ME’, ‘_open me’, _DECRYPT YOUR FILES’ or ‘_Your files have been encrypted” in every folder with an encrypted file. Ransom demanding message on your desktop. |
| Distribution ways | Spam or phishing emails that are created to get people to open an attachment or click on a link. Drive-by downloading (when a user unknowingly visits an infected web site and then malware is installed without the user’s knowledge). Social media, such as web-based instant messaging programs. Remote desktop protocol (RDP) hacking. |
| Removal | Ransomwaree removal guide |
How to remove Qlocker using the QNAP malware remover
To remove Qlocker virus, it is recommended to use software from the creators of QNAP devices.
Qlocker virus remover
- Log on to QTS as administrator.
- Open the app store, click on the Search icon.
- In the search bar, type “Malware Remover” and press Enter. Type “Malware Remover”, and then press ENTER. The Malware Remover application appears in the search result list.
- Find Malware Remover in the list of found applications, click Install.
- Open Malware Remover and click Start Scan.
- Malware Remover scans the NAS for malware.
How to recover ransomware encrypted files
There is a way to recover encrypted files to their original state. No decryption key is required to recover files in this way. Before you begin, you must be 100% sure that the QNAP device does not have active ransomware. Therefore, if you have not yet checked your device for ransomware, do it right now. The last chance to restore encrypted files to their original state is using data recovery tools. We recommend a program called TestDisk. It has all the necessary functions to restore the contents of encrypted files. It helped many victims recover data when it seemed like there was no more hope.
Use the steps to recover encrypted files. For more information about the TestDisk tool, read this manual:
Finish words
This guide was created to help all victims of the Qlocker ransomware virus. If you have questions, then write to us, leaving a comment below. If you need more help with Qlocker related issues, go to here.













Thanks for the credit guys…
Not just PhotoRec but best with EaseUS. It at least get some files with names, mainly mp3 files.
Tried many Data Recovories. Stellar, Get Data Back Nas Data Recovery et al
Where does one go to see if any geniuses are trying to crack the Qlocker pwd code. Is there a thread on a forum or some other place? Who knows they may crack it sooner than later. Anytime ins better than not at all.