What is YOUR IPHONE HAS BEEN COMPROMISED?
YOUR IPHONE HAS BEEN COMPROMISED is a browser-based scam that disguises itself as an Apple Security page and claims that your iPhone has been compromised due to malware/trojan/virus infection. Scammers use such scams to target victims and force them to install untrusted and even possibly malicious apps. The most common among these apps are PUAs (potentially unwanted applications), adware, browser hijackers and spyware.
Usually, victims end up on “YOUR IPHONE HAS BEEN COMPROMISED” and similar scams by going to a misspelled URL or clicking on a fake link. In addition, they can be redirected to this scam by push notfications, malicious advertisements (malvertising) and Adware.
The “YOUR IPHONE HAS BEEN COMPROMISED” message is a SCAM
QUICK LINKS
The “YOUR IPHONE HAS BEEN COMPROMISED” scam is a widespread form of Internet scam in which scammers instruct victims to install software as a way to prevent data theft, remove malware/trojan/virus, and protect the iPhone from personal information leaks.
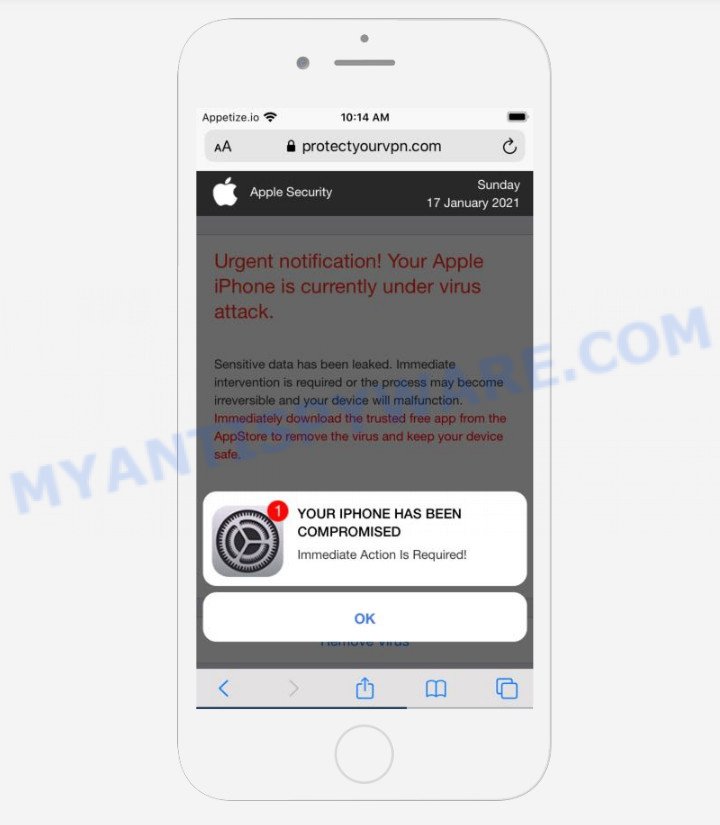
This scam is being promoted by sites that are designed to look like a security warning from Apple. It contains the Apple logo and repeated “Apple Security”, “Apple”, “Detected By Apple” phrases, but this does not mean that Apple has anything to do with the creation of these sites, the scammers are simply trying to create the illusion that they are legitimate Apple sites. These sites cannot be trusted and their content should be ignored.
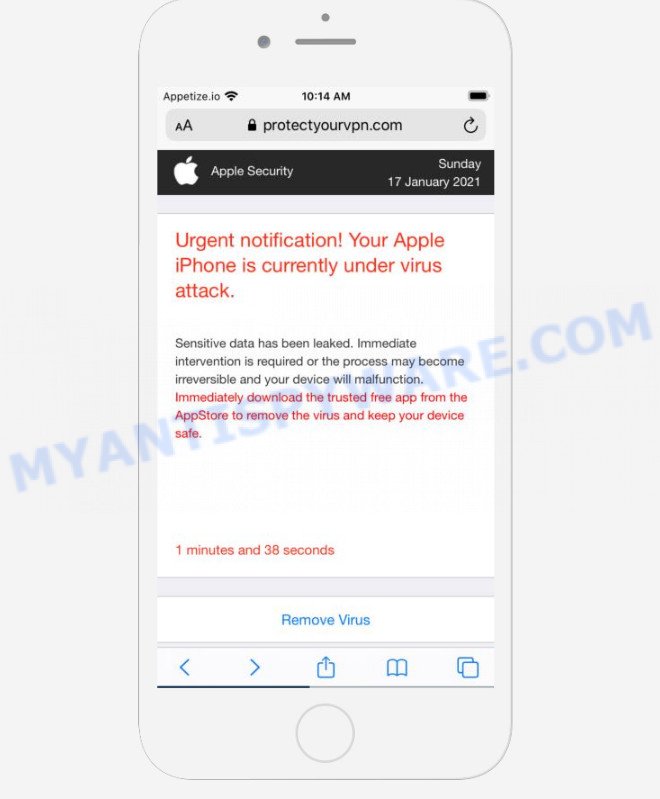
Text presented on the scam:
Apple Security
Urgent notification! Your Apple iPhone is currently under virus attack.
Sensitive data has been leaked. Immediate intervention is required or the process may become irreversible and your device will malfunction.
Immediately download the trusted free app from the AppStore to remove the virus and keep your device safe.0 minutes and 41 seconds
Remove Virus
Detected By Apple.YOUR IPHONE HAS BEEN COMPROMISED
Immediate Action Is Required!
OK
How to protect against the YOUR IPHONE HAS BEEN COMPROMISED scam
To avoid becoming a victim of scammers, it is important to always keep in mind:
- There are no sites that can detect compromised iPhones.
- Never install apps promoted by scam sites, as it can be useless, and besides, it can be dangerous for you and your iPhone.
- Close the scam as soon as it appears on your iPhone screen. Scammers can prevent you from closing it in various ways. In such cases, close your browser using the App Switcher (Open the App Switcher, Tap and hold on the web-browser until the red circles with a minus sign appears. Tap the minus sign on it to Force Quit the web-browser). If the next time you launch the browser, it prompts you to restore the previous session, abandon it, otherwise this scam will reopen on your screen.
Threat Summary
| Name | YOUR IPHONE HAS BEEN COMPROMISED |
| Type | phishing, scam, fake alerts |
| Associated domains | iosdfnc.com, yourlandsecurity.com, browsereport.com, tech-notify24.com, applde1fencce.com, protect-os.com, iosnotification.com, protectyourvpn.com, sysmobilenotify.com, spaceshellvpn.com, ios-protect-defence.com, mobile-sys-tem.com, browsernotification.com |
| Fake claims | “WARNING! Your Apple iPhone is severely damaged by 13 viruses!”, “Urgent notification! Your Apple iPhone is currently under virus attack”, “A Trojan virus is detected! The processor is totally overheated, so it can lead to the complete failure of the device”, “Your iPhone was hacked by a virus after visiting an adult website and your screen was recorded” |
| Symptoms |
|
| Removal | YOUR IPHONE HAS BEEN COMPROMISED removal guide |
The YOUR IPHONE HAS BEEN COMPROMISED scam isn’t the only one on the Internet that aims to trick users into installing untrusted and malicious apps. We have already reported on other types of scams on several occasions, such as Your connection might not be secure, Iphone Calendar Virus/Spam, SYSTEM NOTIFICATION scam, Your iPhone Has Been Hacked.
Another variant of this scam:

Text presented in this scam message:
Apple Security
Urgent action is required!A Trojan virus is detected! The processor is totally overheated, so it can lead to the complete failure of the device and the of all data, including iCloud.
Also, all data stored on this device will be available to third parties.
Apple Security has urgently selected the required app, which can be downloaded following the link below.It will remove viruses and protect your device in an instant.Remove Virus
YOUR IPHONE HAS BEEN COMPROMISED
Immediate Action Is Required!
OK
A new variant of the YOUR IPHONE HAS BEEN COMPROMISED scam:
Apple Security
Warning!Your iPhone was hacked by a virus after visiting an adult website and your screen was recorded!
If this problem is not resolved within two minutes, the video recording and all your photos might be leaked.In order to fix the problem you must download trusted VPN app and activate data protection.
Update, March 5, 2021
A new variant of the YOUR IPHONE HAS BEEN COMPROMISED scam (“Your Apple iPhone is severely damaged by 13 viruses”):
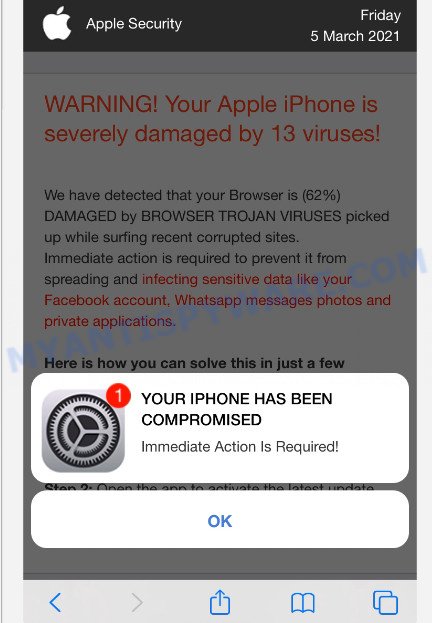
Text presented in this scam message:
Apple Security
WARNING! Your Apple iPhone is severely damaged by 13 viruses!We have detected that your Browser is (62%) DAMAGED by BROWSER TROJAN VIRUSES picked up while surfing recent corrupted sites.
Immediate action is required to prevent it from spreading and infecting sensitive data like your Facebook account, Whatsapp messages photos and private applications.Here is how you can solve this in just a few seconds (Step by Step)
Step 1: Tap REMOVE VIRUS to install VPN from the App Store.
Step 2: Open the app to activate the latest update and remove any older (Infected) versions.
Remove Virus
Detected By Apple.YOUR IPHONE HAS BEEN COMPROMISED
Immediate Action Is Required!
OK
Where the YOUR IPHONE HAS BEEN COMPROMISED pop-ups comes from
If your browser redirects to the scam regularly, then it is possible that Adware or PUAs are installed on your iPhone. Adware’s basic purpose is to show advertisements. These advertisements are often displayed as sponsored links, unclosable windows, fake warnings or push notifications. Clicks on the advertisements produce a monetary payoff for the adware creators. Adware can work like Spyware, since it sends confidential data such as searches and trends to advertisers.
Adware spreads bundled with various freeware. This means that you need to be very careful when installing free apps downloaded from the App Store. Be sure to read the Terms of Use and the Software license. Download only reputable applications. NEVER install any unknown and dubious software.
If the YOUR IPHONE HAS BEEN COMPROMISED scam keeps popping up on the device screen and, after closing it, it appears again and again, then try the following simple steps to solve the problem: turn on pop-up blocker; turn on fraudulent website warnings; delete web browsing data. Below we will demonstrate how to do this.
Open the Apple device settings, then scroll down the list of settings to Safari, tap on it.
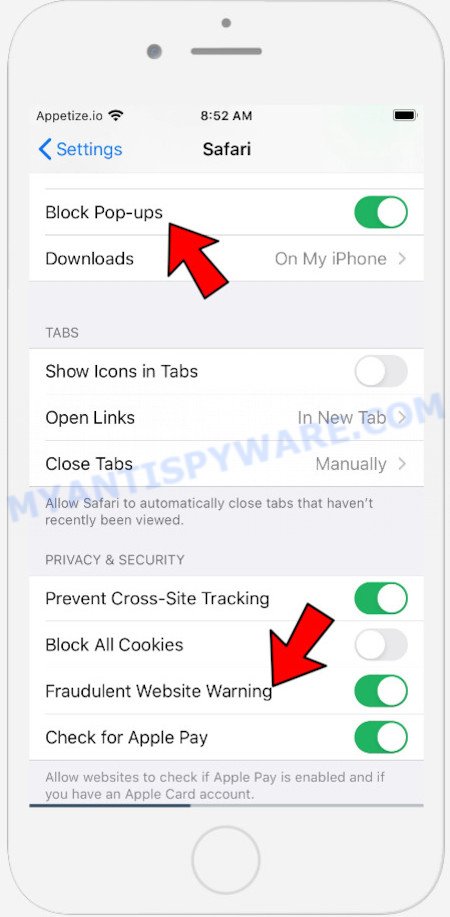
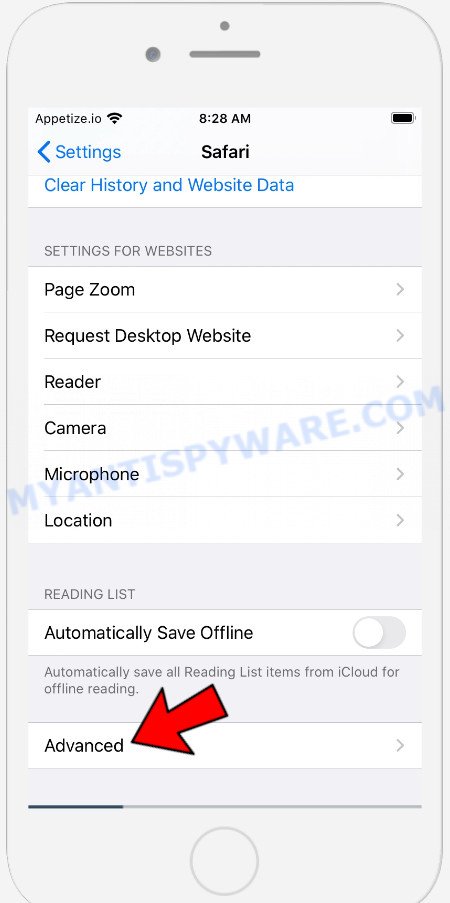
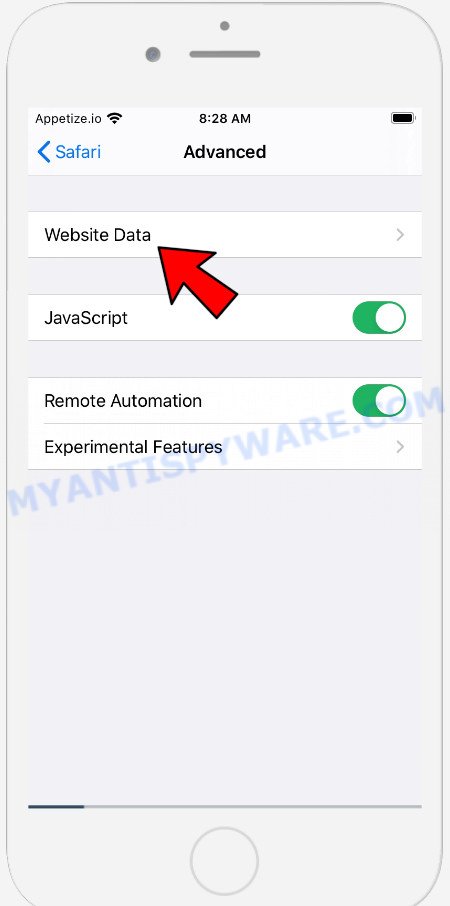
In the list of settings, find switches “Block Pop-ups” and “Fraudulent Website Warning”, check if they are enabled. If any of the switches are off, then it must be turned on. Having done this, scroll down the settings and tap “Advanced”.
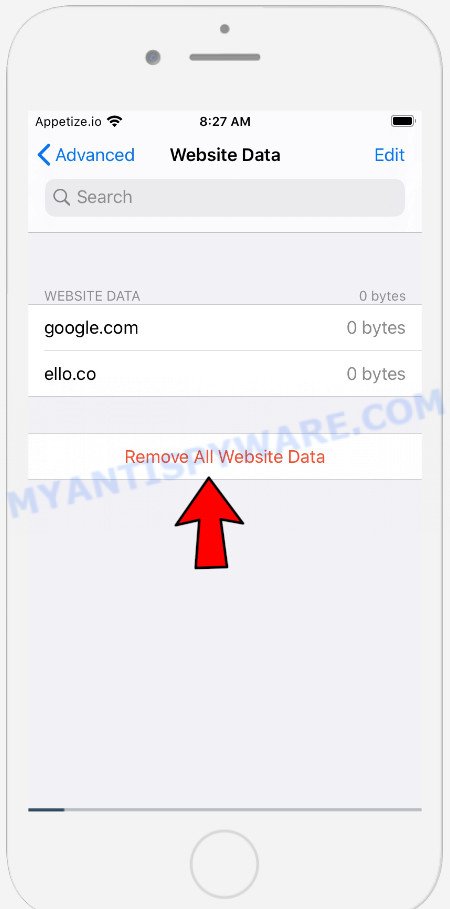
On the Advanced settings screen, tap “Website Data”, scroll down the list of web-domains and tap “Remove All Website Data”.
How to Remove YOUR IPHONE HAS BEEN COMPROMISED scam from Mac (removal instructions)
Fortunately, it is not hard to remove adware software responsible for the YOUR IPHONE HAS BEEN COMPROMISED pop-ups. In the following instructions, we will provide two ways to free your machine of this adware. One is the manual removal solution and the other is automatic removal solution. You can select the method that best fits you. Please follow the removal steps below to remove YOUR IPHONE HAS BEEN COMPROMISED pop ups right now!
To remove YOUR IPHONE HAS BEEN COMPROMISED, use the following steps:
- Remove profiles created by adware
- Check the list of installed apps
- Remove adware related files and folders
- Scan your Mac with MalwareBytes
- Remove YOUR IPHONE HAS BEEN COMPROMISED from Safari, Chrome, Firefox
- How to stop YOUR IPHONE HAS BEEN COMPROMISED pop up scam
Remove profiles created by adware
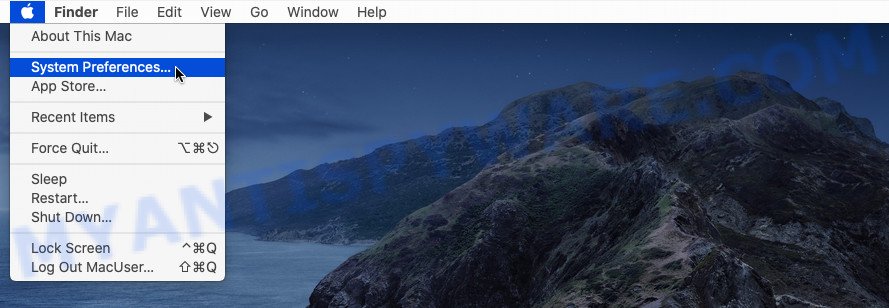
Adware and PUAs can install a configuration profile on the Apple Mac system to block changes made to the browser settings. Therefore, you need to open system preferences, find and delete the profile installed by the adware.
Click Apple menu ( ![]() ) > System Preferences.
) > System Preferences.
In System Preferences, select Profiles. if there is no Profiles in the list of preferences, that means there are no profiles installed on the Mac. If there is Profiles in the list, then click on it, then select a profile related to YOUR IPHONE HAS BEEN COMPROMISED.
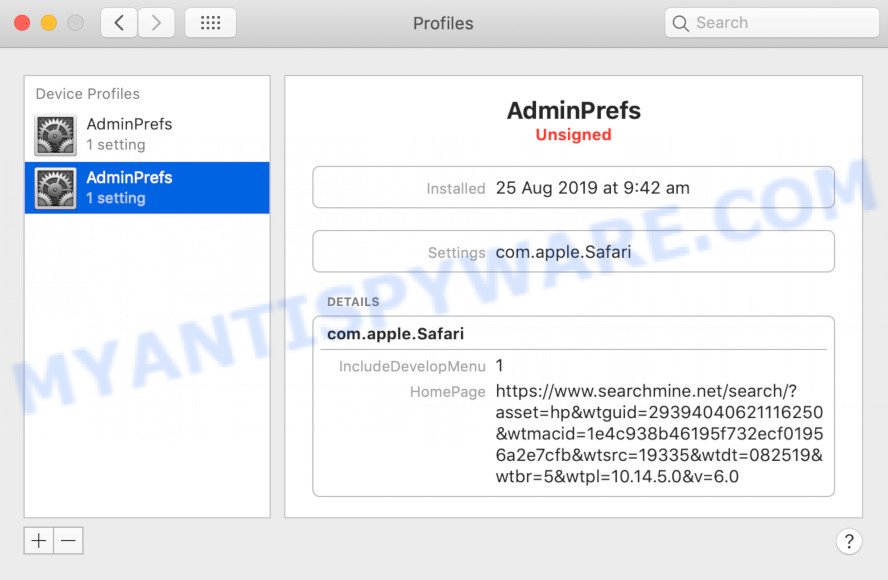
To delete a malicious profile, click on the minus button ( – ) located at the bottom-left of the Profiles screen.
Check the list of installed apps
Check the list of installed apps on your Mac and remove all unknown and recently installed software. If you see an unknown program with incorrect spelling or varying capital letters, it have most likely been installed by malware and you should clean it off first with malicious software removal utility such as MalwareBytes Anti Malware.

- Open the Finder.
- Click “Applications”.
- It will display a list of all programs installed on the MAC system.
- Scroll through the all list, and remove suspicious and unknown apps. Pay maximum attention to the program you installed last.
- Drag the questionable program from the Applications folder to the Trash.
- Empty Trash.
Remove adware related files and folders
Now you need to try to find adware related files and folders, and then delete them manually. You need to look for these files in certain directories. To quickly open them, we recommend using the “Go to Folder…” command.
Click on the Finder icon. From the menu bar, select Go and click “Go to Folder…”. As a result, a small window opens that allows you to quickly open a specific directory.
Check for adware generated files in the /Library/LaunchAgents folder
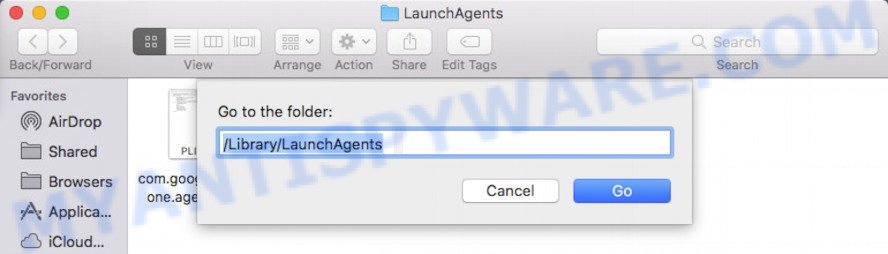
In the “Go to Folder…” window, type the following text and press Go:
/Library/LaunchAgents
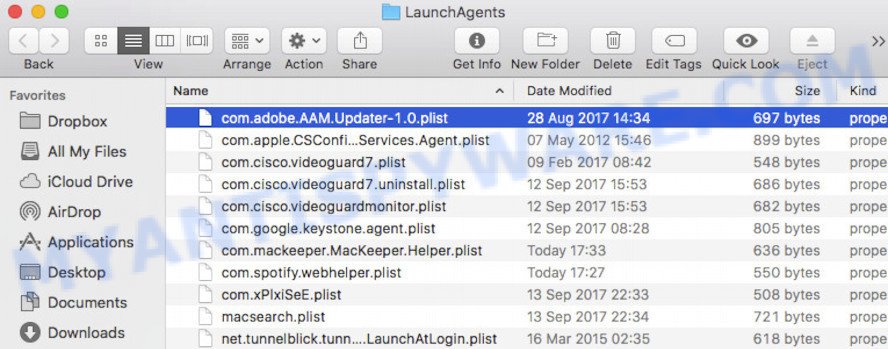
This will open the contents of the “/Library/LaunchAgents” folder. Look carefully at it and pay special attention to recently created files, as well as files that have a suspicious name. Move all suspicious files to the Trash. A few examples of files: installapp.plist, macsearch.plist, search.plist and com.machelper.plist. Most often, adware, PUPs and browser hijackers create several files with similar names.
Check for adware generated files in the /Library/Application Support folder
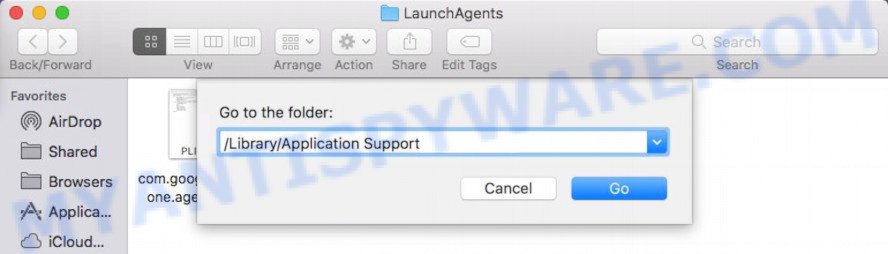
In the “Go to Folder…” window, type the following text and press Go:
/Library/Application Support
This will open the contents of the “Application Support” folder. Look carefully at its contents, pay special attention to recently added/changed folder. Move all suspicious folders to the Trash.
Check for adware generated files in the “~/Library/LaunchAgents” folder
In the “Go to Folder…” window, type the following text and press Go:
~/Library/LaunchAgents
Proceed in the same way as with the “/Library/LaunchAgents” and “/Library/Application Support” folders. Look for suspicious and recently added files. Move all suspicious files to the Trash.
Check for adware generated files in the /Library/LaunchDaemons folder
In the “Go to Folder…” window, type the following text and press Go:
/Library/LaunchDaemons
Carefully browse the entire list of files and pay special attention to recently created files, as well as files that have a suspicious name. Move all suspicious files to the Trash. A few examples of files to be deleted: com.macsearch.plist, com.machelper.plist, com.installapp.plist, and com.search.plist. In most cases, adware, browser hijackers and PUPs create several files with similar names.
Scan your Mac with MalwareBytes
If you’re still having problems with the YOUR IPHONE HAS BEEN COMPROMISED scam removal or just wish to check your Mac occasionally for adware and other malicious software, then download MalwareBytes AntiMalware (MBAM). It is free for home use, and searches for and removes various unwanted programs that attacks your MAC system or degrades machine performance. MalwareBytes Free can remove adware software, browser hijackers, toolbars and PUPs as well as malware, including ransomware and trojans.
Download MalwareBytes AntiMalware (MBAM) by clicking on the following link.
21020 downloads
Author: Malwarebytes
Category: Security tools
Update: September 10, 2020
Once the download is finished, close all programs and windows on your Apple Mac. Run the saved file. Follow the prompts.
The MalwareBytes Anti-Malware (MBAM) will automatically start and you can see its main screen as displayed in the figure below.
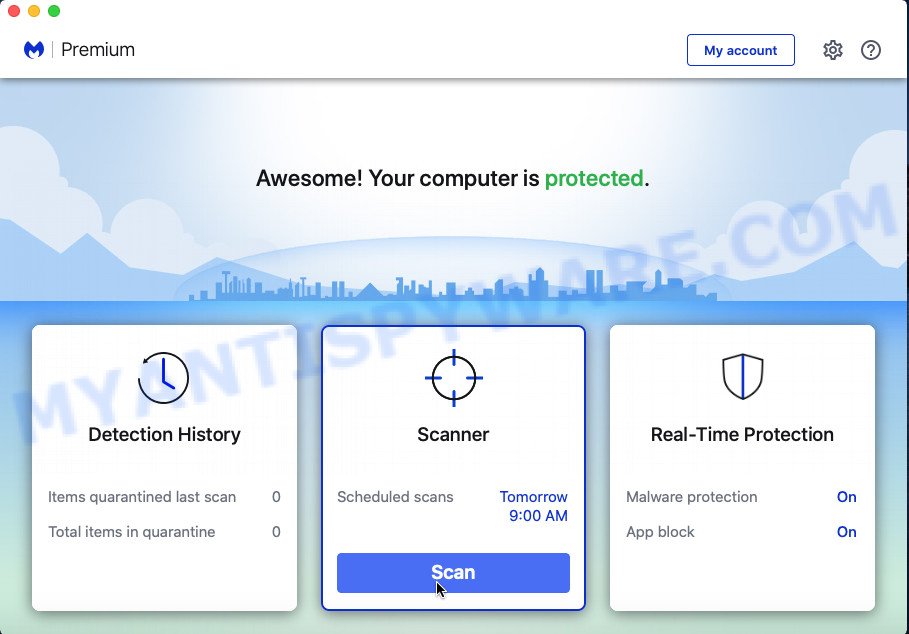
Now press the “Scan” button . MalwareBytes Anti Malware (MBAM) program will scan through the whole MAC OS for the adware responsible for the YOUR IPHONE HAS BEEN COMPROMISED scam. A system scan can take anywhere from 5 to 30 minutes, depending on your MAC. When a malware, adware or PUPs are detected, the count of the security threats will change accordingly.
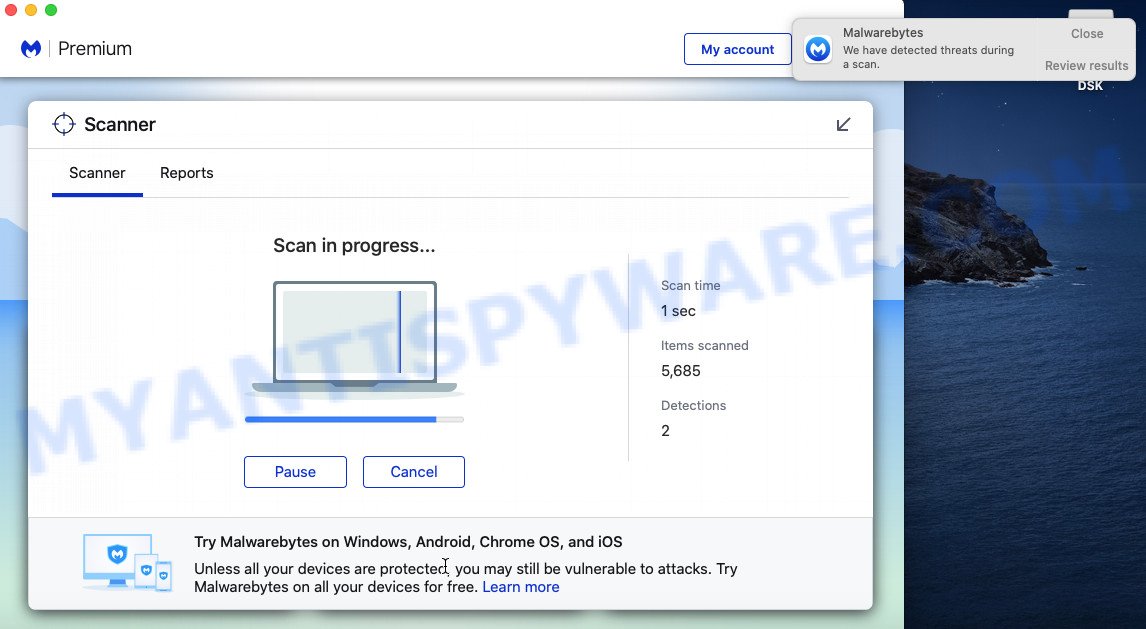
Once the scan get finished, MalwareBytes will show a list of all threats found by the scan. All detected threats will be marked. You can delete them all by simply click the “Quarantine” button. The MalwareBytes Anti-Malware (MBAM) will start to delete adware that causes the YOUR IPHONE HAS BEEN COMPROMISED pop ups in your web-browser.
Remove YOUR IPHONE HAS BEEN COMPROMISED from Safari, Chrome, Firefox
If you have ‘YOUR IPHONE HAS BEEN COMPROMISED pop-up scam’ removal problem, then remove unwanted add-ons can help you. In the steps below we’ll show you the way to remove harmful plugins without reinstall. This will also allow to delete YOUR IPHONE HAS BEEN COMPROMISED popups from your web browser.
You can also try to remove YOUR IPHONE HAS BEEN COMPROMISED pop up scam by reset Chrome settings. |
If you are still experiencing problems with YOUR IPHONE HAS BEEN COMPROMISED pop up scam removal, you need to reset Firefox browser. |
|
How to stop YOUR IPHONE HAS BEEN COMPROMISED pop up scam
If you browse the Internet, you can’t avoid malvertising. But you can protect your web-browser against it. Download and run an ad blocking program. AdGuard is an ad-blocker that can filter out a lot of of the malvertising, stoping dynamic scripts from loading harmful content.
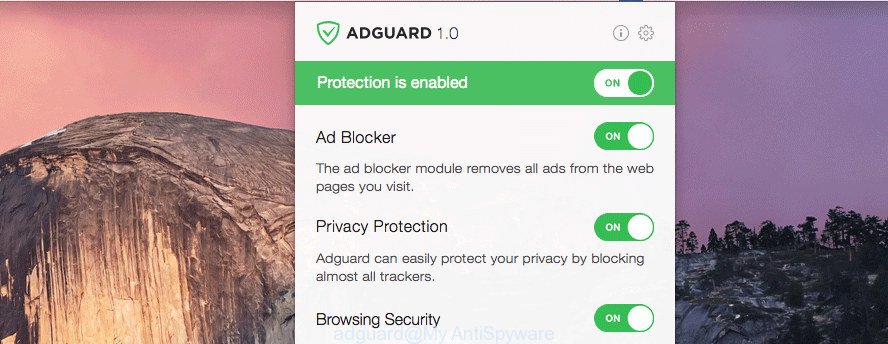
Click the link below to download the latest version of AdGuard for Mac.
3780 downloads
Author: © Adguard
Category: Security tools
Update: January 17, 2018
After the downloading process is finished, run the downloaded file. The “Setup Wizard” window will show up on the computer screen.
Follow the prompts. AdGuard will then be installed. A window will show up asking you to confirm that you want to see a quick tutorial. Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick tutorial that will allow you get to know AdGuard better.
Each time, when you run your machine, AdGuard will run automatically and stop intrusive pop-up advertisements, block YOUR IPHONE HAS BEEN COMPROMISED scam, as well as other malicious or misleading websites.
Finish words
Once you’ve finished the instructions shown above, your Apple device should be free from adware responsible for the YOUR IPHONE HAS BEEN COMPROMISED scam and other malware. The Firefox, Safari and Google Chrome will no longer redirect you to various scam web-pages similar to YOUR IPHONE HAS BEEN COMPROMISED. Unfortunately, if the step-by-step instructions does not help you, then you have caught a new adware, and then the best way – ask for help here.