.Nesa file extension, unable to open images, documents and music, the file explorer shows a blank icon for many file types instead of the associated applications (such as Word, Excel, etc), the file named ‘_readme.txt’ in each folder with at least one .Nesa file. All these are indicative of the presence of ransomware in your computer.
Ransomware also known as Crypto virus, Crypto malware, Filecoder and File locker is a malware that was created by cybercriminals with one goal – to encrypt files, and then demand a ransom for decrypting them. A virus that encrypts files and changes their extensions to ‘.Nesa’ is a new ransomware. It was first discovered by Michael Gillespie (link) on September 23. This virus belongs to a large group of ransomware, which currently includes 166 variants.
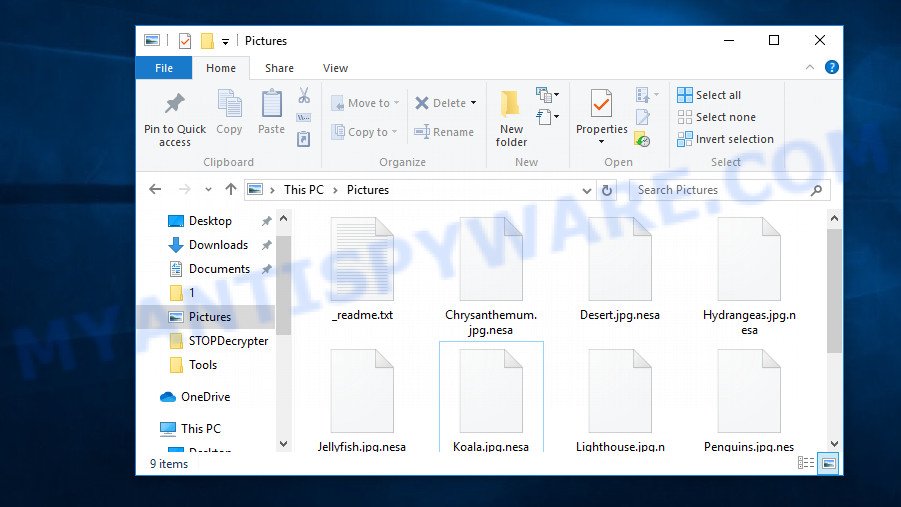
“.Nesa extension” is a sign of ransomware infection
According to victims who first encountered the consequences of ransomware infection, before their files were encrypted, they downloaded a program and installed it on their computer. This is also confirmed by securirty experts, most often crypto viruses are distributed as part of free and hacked software.
Immediately after the virus is launched, it begins to encrypt files. For example, the virus finds the file named ‘document.doc’, it first encrypts it, then renames it, adding ‘.nesa’ at the end of its name. As a result, instead of the original file, a new one appears on the disk with the name ‘document.doc.nesa’. This process will continue until the virus encrypts all the files. Of course, the virus does not encrypt absolutely all types of files, most often ransomware only encrypts files of the following types:
.kdb, .db0, .pptm, .fsh, .dmp, .wp7, .odp, .blob, .wot, .xmmap, .wbd, .xdl, .wbc, .map, .ibank, .xls, .xld, .wp, .arw, .yal, .menu, .big, .bay, .wpw, .xlgc, .wsh, .wma, .flv, .dcr, .wpl, .psd, .vfs0, .zip, .py, .xlk, .dba, .vdf, .wbmp, .pdd, .bc7, .ai, .ws, .mov, .wire, .wmv, .lrf, .crw, .docx, .mdbackup, .xyp, .x, .xdb, .gdb, .ptx, .odc, .mcmeta, .bsa, .indd, .sb, .gho, .wcf, .odm, .wdb, .rtf, .das, .pfx, .kf, .sr2, .wpd, .sum, .1st, .bik, .pak, .svg, .mpqge, .iwi, .y, .wbk, .vpp_pc, .raw, .zip, .xlsx, .cr2, .cfr, .vcf, .bkp, .vpk, .p7b, .wp5, .mddata, .sie, .ods, .apk, .syncdb, .cas, .snx, .wn, .icxs, .ff, .esm, .wm, .arch00, .png, .bc6, .3fr, .bar, .xlsm, .xml, .sid, .ysp, .p12, .lbf, .m3u, .3ds, .jpeg, .wpb, .sidn, .d3dbsp, .x3f, .raf, .qdf, .hkdb, .orf, .ltx, .hkx, .wp6, .crt, .xll, .sav, .2bp, .odt, .xbdoc, .sql, .wri, .cdr, .wpd, .t13, .xlsb, .mrwref, .odb, .xbplate, .upk, .w3x, .wma, .pptx, .iwd, .wpe, .litemod, .z3d, .rim, .forge, .avi, .m4a, .0, .ppt, .der, .pst, .p7c, .mp4, .fpk, .xx, .bkf, .zw, .asset, .txt, .wgz, .wbm, .mef, .vtf, .tax, .js, .srw, .accdb, .itl, .x3f, .xlsm, .hvpl, .css, .wpt, .jpe, .sis, .layout, .wpa, .wmo, .desc, .dng, .mlx, .wb2, .rar, .srf, .pdf, .wp4, .webp, .mdf, .x3d, .rofl, .psk, .z, .wmd, .wpg, .wmv, .slm, .epk, .zdc, .kdc, .cer, .wps, .xf, .wps, .wdp, .ncf, .m2, .pef, .xwp, .nrw, .zif, .r3d, .dwg, .wotreplay, .doc, .xlsx, .hplg, .xy3, .1, .xar, .dbf, .sidd, .jpg, .rgss3a, .xxx, .webdoc, .wsd, .eps, .3dm, wallet, .zabw, .itm, .zdb, .erf, .fos
In each directory where the virus encrypted the files, it creates a new file called ‘_readme.txt’. As the name of this file shows, attackers want to attract maximum attention to it. Moreover, in the file name, as its first character, they use the character ‘_’, which guarantees that this file will be shown in the directory first and will be accurately seen by the victim. This file is really important because it contains necessary information. It contains a message demanding a ransom as well as the contact details of the attackers and the personal number of the victim. Below we give an example of such a message:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-4ltSd5zdAc
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.chReserve e-mail address to contact us:
gerentoshelp@firemail.ccYour personal ID:
0166Bgas391udjgkhuirvdq9MNaL0MiA9uN1baL0oPzAWDhnvqOURnbs8k1o
Attackers suggest writing an email to them using gorentos@bitmessage.ch and gerentoshelp@firemail.cc to get the bitcoin wallet address to which the ransom must be transferred. They also offer to check the possibility that the .Nesa files can be decrypted. For this, the victim of ransomware infection can put one small file in the email letter. This file should not contain any important information.
Threat Summary
| Name | Nesa |
| Type | Ransomware, Crypto virus, Crypto malware, Filecoder, File locker |
| Encrypted files extension | .nesa |
| Ransom note | _readme.txt |
| Contact | gorentos@bitmessage.ch |
| Ransom amount | $3980 in Bitcoins |
| Symptoms | Files won’t open. Your photos, documents and music have new extension. Files named ‘_readme.txt’, or ‘_readme’ in each folder with at least one encrypted file. |
| Distribution ways | Spam or phishing emails that are created to get people to open an attachment or click on a link. Malicious downloads that happen without a user’s knowledge when they visit a compromised website. Social media posts (they can be used to mislead users to download malicious software with a built-in ransomware downloader or click a malicious link). Malvertising campaigns. |
| Removal | To remove Nesa ransomware use the removal guide |
| Decryption | To decrypt Nesa ransomware use the steps |
As we mentioned at the beginning of the article, this virus is far from the first in its group. Other versions of this ransomware are Karl, Domn and Kvag. There is not much difference between them. The method of infecting computers, the method of encrypting files, and etc., are all the same. The main difference that is immediately visible is the file extension, which is added to the encrypted file. In the most recent case, attackers use the .nesa extension. Despite the apparent similarity, the victims will not be able to unite. In each case, for each specific computer, its own unique decryption key is needed.
At the moment, only attackers have these keys. Antivirus companies and security experts cannot help the victims in any way. There is only one reason – the virus uses a very strong encryption method to encrypt files. That is, you cannot decrypt files without a key. However, do not panic and do not pay a ransom. Despite the above information, it cannot be said that there is no hope of being able to recover all encrypted files. We want to say that there is an opportunity to recover part or even all files without decryption and you should definitely use this opportunity.
Quick links
- How to remove Nesa ransomware
- Is it possible to decrypt .nesa files?
- How to restore .nesa files
- Finish words
How to remove Nesa ransomware
Before you try to recover encrypted files, you need to find and remove ransomware. Doing it manually is very difficult. The main reason is that ransomware can use different names and locations. Often, even anti-virus programs installed on a computer cannot detect a virus or block its launch. By the way, perhaps it happened in your case. Therefore, we recommend using malware removal tools called Zemana Anti-malware, Malwarebytes or KVRT. Most experts will agree with us. Of course you can use other malware removal utilities. If you do not have an antivirus, then at this stage you can also install it and perform a full scan.
Remove Nesa with Zemana Anti-Malware (ZAM)
One of the best programs among malware removers is Zemana AntiMalware. Compared with antivirus software, it has a small size, simple interface, can quickly scan your computer and remove the found malware. If you have an antivirus, then this tool can work with it without any conflicts. Unlike other malware removal tools that you can find, Zemana AntiMalware can not only find malware, but also remove it for free. You do not have to pay anything for this. To find and remove Nesa virus, do the following:
Download Zemana from the following link. Save it to your Desktop so that you can access the file easily.
165094 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
After downloading is done, close all windows on your system. Further, launch the setup file named Zemana.AntiMalware.Setup. If the “User Account Control” dialog box pops up as displayed in the figure below, press the “Yes” button.
It will show the “Setup wizard” which will help you install Zemana Anti-Malware on the system. Follow the prompts and do not make any changes to default settings.
Once installation is complete successfully, Zemana AntiMalware will automatically run and you may see its main window as shown on the image below.

Next, press the “Scan” button. Zemana Anti Malware (ZAM) utility will start scanning the whole system to detect the Nesa crypto malware, other malicious software, worms and trojans. Depending on your personal computer, the scan may take anywhere from a few minutes to close to an hour. While the Zemana tool is scanning, you may see how many objects it has identified as being affected by malicious software.

Once Zemana has completed scanning, Zemana Free will display a scan report. Once you’ve selected what you wish to remove from your computer click “Next” button.
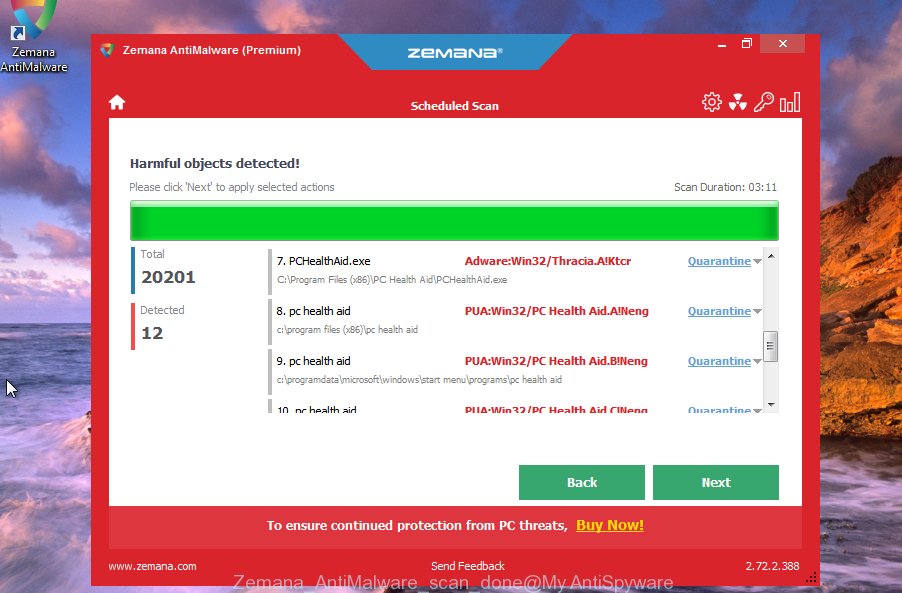
The Zemana Anti-Malware (ZAM) will uninstall Nesa ransomware and other kinds of potential threats like malware and trojans and move all threats to the program’s quarantine. After disinfection is finished, you can be prompted to restart your PC system.
Automatically remove Nesa ransomware with MalwareBytes Anti-Malware
Another good way to detect ransomware and remove it for free is to use a well-known utility called MalwareBytes Anti-Malware. This is a very powerful program and in its capabilities it is comparable to a good antivirus. For more than 10 years, we offer to use it. You can learn more about MalwareBytes on this page.
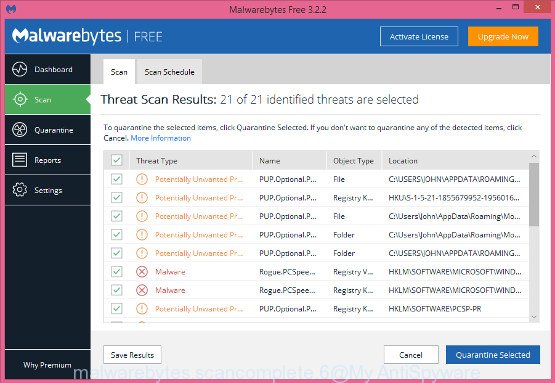
So, to use MalwareBytes Anti-Malware to identify Nesa ransomware and remove it, you need to do the following:
- Please go to the following link to download MalwareBytes Free. Save it to your Desktop so that you can access the file easily.
Malwarebytes Anti-malware
327319 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- At the download page, click on the Download button. Your web-browser will show the “Save as” prompt. Please save it onto your Windows desktop.
- When downloading is finished, please close all software and open windows on your personal computer. Double-click on the icon that’s called mb3-setup.
- This will run the “Setup wizard” of MalwareBytes AntiMalware onto your personal computer. Follow the prompts and don’t make any changes to default settings.
- When the Setup wizard has finished installing, the MalwareBytes Anti Malware (MBAM) will launch and open the main window.
- Further, click the “Scan Now” button to perform a system scan with this utility for the Nesa ransomware virus, other malware, worms and trojans. This task can take quite a while, so please be patient. While the MalwareBytes Free utility is scanning, you can see how many objects it has identified as being infected by malware.
- Once MalwareBytes AntiMalware has completed scanning your personal computer, MalwareBytes will open a scan report.
- Once you have selected what you want to remove from your machine click the “Quarantine Selected” button. After finished, you may be prompted to restart the PC system.
- Close the Anti-Malware and continue with the next step.
Video instruction, which reveals in detail the steps above.
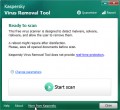
Use KVRT to remove Nesa crypto malware from the PC system
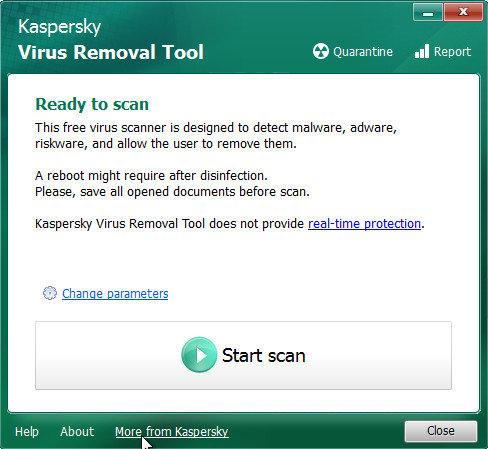
The last option, but which, according to most security experts, has great potential is Kaspersky virus removal tool. This is a malware removal tool, part of the famous antivirus, which has all its capabilities to find and remove ransomware, trojans, worms, adware, browser hijackers and so on. This program does not have only one thing – a computer protection module. At the same time, you can use the KVRT for free, both for the search for malware and for it’s removal. To find and remove Nesa crypto malware, follow these simple steps below.
Download Kaspersky virus removal tool (KVRT) by clicking on the link below.
129312 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
After the downloading process is finished, double-click on the KVRT icon. Once initialization procedure is done, you will see the KVRT screen as displayed on the image below.
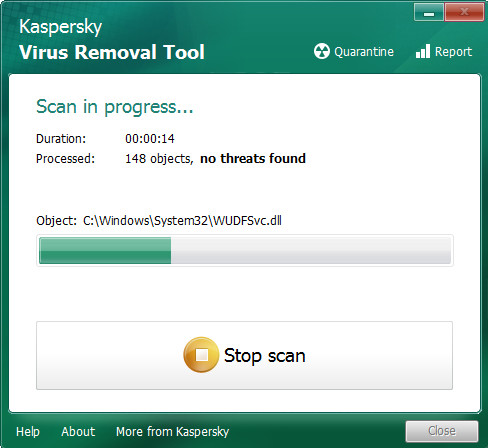
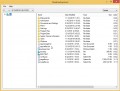
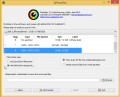
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next click Start scan button to perform a system scan with this utility for the Nesa ransomware and other malware. Depending on your machine, the scan may take anywhere from a few minutes to close to an hour. When a threat is detected, the number of the security threats will change accordingly.
Once the system scan is done, you will be shown the list of all detected threats on your computer as shown on the screen below.
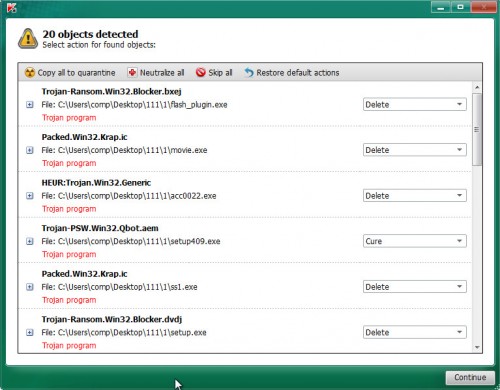
Review the results once the utility has complete the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply press on Continue to start a cleaning procedure.
Is it possible to decrypt .nesa files?
As we have already reported several times in this article, there is currently no way to decrypt .nesa files. But this does not mean that such an opportunity does not appear in the future. Anti-virus companies and security experts are looking for a way to decrypt files. Therefore, do not despair.
If you become a victim of the ‘Nesa extension’ infection, then you need to do:
- Do not panic
- Do not pay a ransom, and ignore all threats by hackers
- Remove Nesa virus
- Try to restore .nesa files to their original state
- Bookmark this page and visit it from time to time, when any way to decrypt .nesa files appears, we will inform about it.
How to restore .nesa files
Fortunately, although it is not possible to decrypt files without an unique key, there is little opportunity to recover them without decryption. For this, we recommend using the programs listed below. Both of these programs are free and have proven their worth. Probably they will not be able to recover all the files, but even if you return part of the files, it will be better than nothing. Please note – before you start recovering files, you must definitely check your computer for malware. You need to be 100% sure that the virus is completely removed.
Use ShadowExplorer to restore .nesa files
The first way to return files to a state before they were encrypted is to use a program called ShadowExplorer. As we said, this is a free program. It does not use any ‘magic’ technology, just allows you to easily use the ‘Previous Versions’ feature of Microsoft Windows. Unfortunately, very often viruses delete all previous copies (Shadow Copies) and therefore this program may not always help. But it’s worth a try. To recover .nesa files using ShadowExplorer, follow these steps.
Visit the following page to download the latest version of ShadowExplorer for MS Windows. Save it on your Desktop.
439713 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
When the downloading process is done, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as shown in the following example.
Launch the ShadowExplorer tool and then choose the disk (1) and the date (2) that you wish to recover the shadow copy of file(s) encrypted by the Nesa crypto malware as shown on the image below.
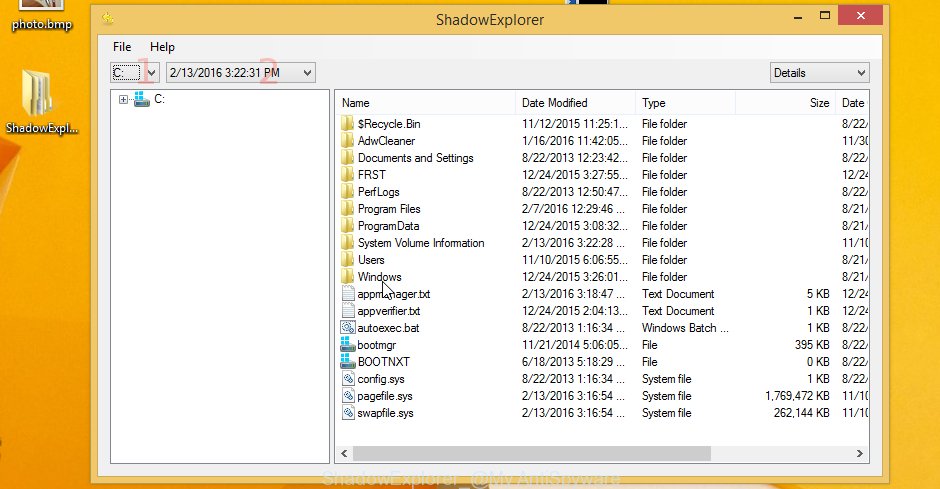
Now navigate to the file or folder that you wish to recover. When ready right-click on it and click ‘Export’ button as displayed in the following example.

Recover .nesa files with PhotoRec
Another way to recover files is to use any program created to recover deleted data. Often these programs cost a lot of money, and do not allow you to recover found files for free. We suggest you use the program, which is called PhotoRec. It has all the necessary features and it is completely free. It’s easy to use. The instructions that we provide below show in detail how to use PhotoRec to recover .nesa files.
Download PhotoRec on your Windows Desktop from the following link.
After the downloading process is done, open a directory in which you saved it. Right click to testdisk-7.0.win and select Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as on the image below.

Double click on qphotorec_win to run PhotoRec for Windows. It will show a screen as displayed on the image below.
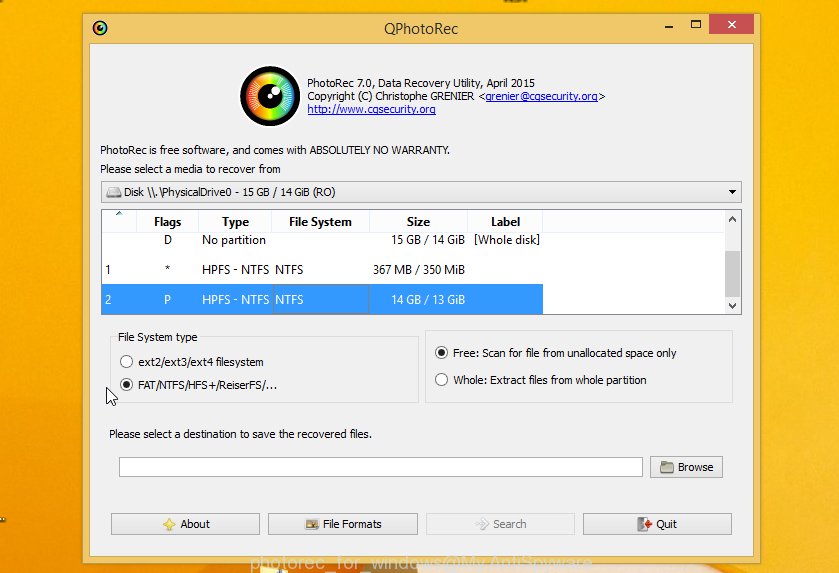
Select a drive to recover such as the one below.
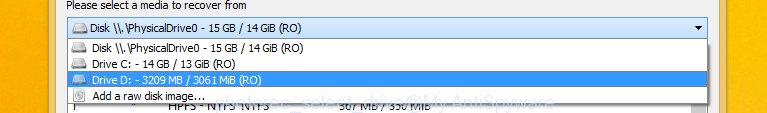
You will see a list of available partitions. Choose a partition that holds encrypted photos, documents and music like below.
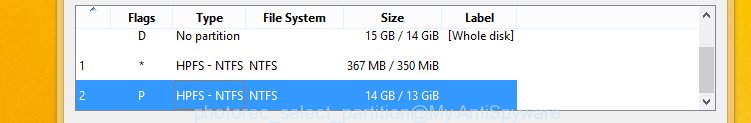
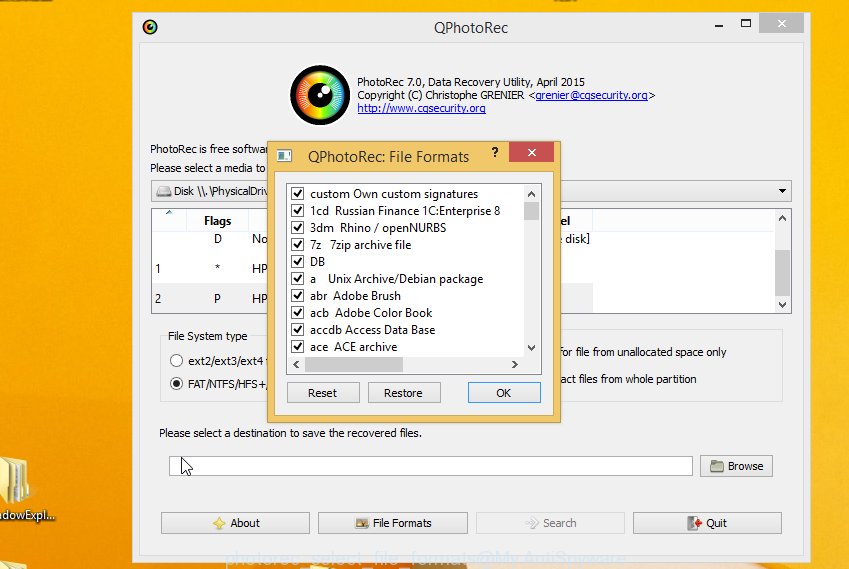
Click File Formats button and choose file types to restore. You can to enable or disable the recovery of certain file types. When this is finished, click OK button.
Next, click Browse button to select where restored files should be written, then press Search.
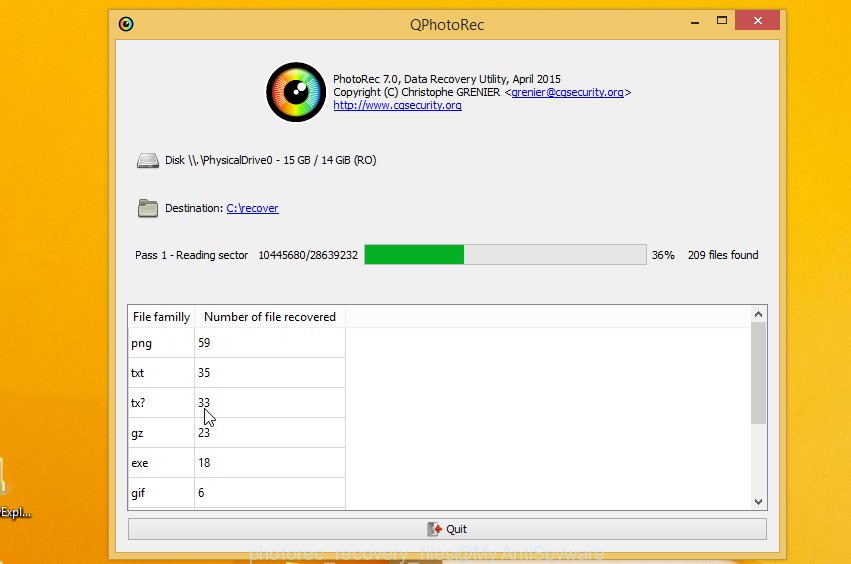
Count of recovered files is updated in real time. All recovered files are written in a folder that you have chosen on the previous step. You can to access the files even if the restore process is not finished.
When the recovery is complete, press on Quit button. Next, open the directory where restored files are stored. You will see a contents as shown in the figure below.
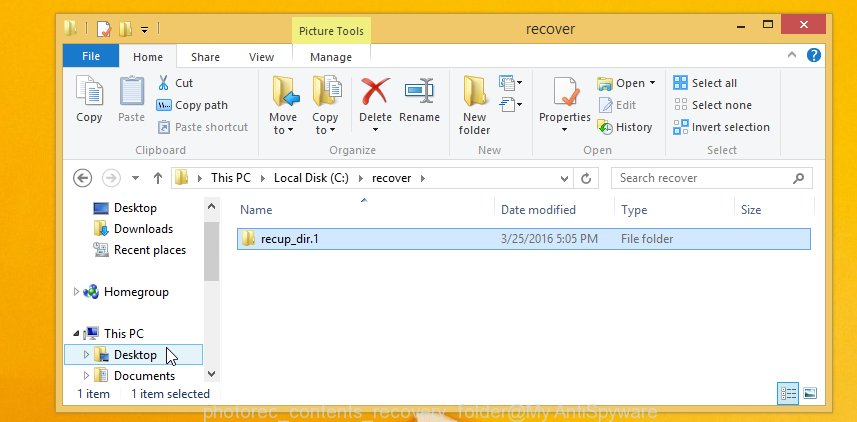
All restored photos, documents and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you are looking for a specific file, then you can to sort your restored files by extension and/or date/time.
Finish words
At the moment, this is the basic information that is known about the ‘.nesa exension’ infection. We hope this information helped you find and remove ransomware, as well as restore encrypted files. If you have additional information, comments or questions, then write to us by adding a message below.












Hi Casper Sky, I was infected with the ransomware which is from nesa. Is it possible to help me, thank you
Try a new free STOP Djvu decryptor. Read more here – Emsisoft STOP Djvu Ransomware Decryptor – Free way to decrypt encrypted files.