.Karl file extension at the end of your file names indicates that your computer has become a victim of malware that belongs to the ransomware family. Even if you delete this extension or rename a file with this extension, nothing will change; you will not be able to open these files. All programs installed on your computer will not be able to open these files because they are encrypted by ransomware. In this article we will try to answer the following questions: Is it possible to decrypt files? and What to do if you become a victim of “.Karl file extension” infection. That is, these are the questions that users, who are victims of this infection, most often ask us.
Threat Summary
| Name | “.Karl file extension” infection |
| Type | Ransomware, Crypto malware, File locker, Filecoder, Crypto virus |
| Encrypted files extension | .karl |
| Ransom note | _readme.txt |
| Contact | gorentos@bitmessage.ch |
| Ransom amount | $980 in Bitcoins |
| Symptoms | Your photos, documents and music fail to open. Your photos, documents and music have a new extension, or don’t look right when you open them. Your file directories contain a ‘ransom note’ file that is usually a .txt file. |
| Distribution methods | Unsolicited emails that are used to deliver malware. Drive-by downloads (ransomware virus has the ability to infect the machine simply by visiting a web-site that is running harmful code). Social media, like web-based instant messaging programs. Malvertising campaigns. |
| Removal | To remove Karl ransomware use the removal guide |
| Decryption | To decrypt Karl ransomware use the steps |
What is Ransomware?
Ransomware is a type of malicious software which is used to encrypt files, after which the attackers demand a ransom for decrypting them. In the case of “.Karl file extension” infection, the same thing. This ransomware encrypts all the files that it finds on the infected computer. It has the ability to encrypt files located not only on local disks, but also on connected external media and network drives. The following types of files can be encrypted:
.raw, .mpqge, .accdb, .mdbackup, .wav, .wmo, .mlx, .psd, .avi, .zip, .wmv, .xlsm, .odt, .wsc, .mef, .ltx, .snx, .sav, .wire, .ysp, .sie, .apk, .icxs, .js, .docx, .ybk, .map, .yml, .xbplate, .w3x, .txt, .wbz, .wp6, .xlk, .wpd, .forge, .re4, .ibank, .bar, .xyw, .flv, .xxx, .p7c, .cfr, .wmv, .bkp, .sql, .csv, .syncdb, .wbd, .qdf, .asset, .z3d, .zdb, .desc, .der, .m2, .wgz, .r3d, .mrwref, .sidn, .xll, .jpe, .wm, .vdf, .wma, .lvl, .mcmeta, .bay, .x, .t13, .rar, .1, .pkpass, .hplg, .wdp, .mdb, .bc7, .iwd, .wma, .wbm, .sb, .dwg, .pfx, .wpt, .xlsm, .3fr, .kdb, .pptm, .xmmap, .kf, .ff, .rw2, .mov, .sr2, .dmp, .3ds, .wri, .ntl, .wbc, .ppt, .wn, .xlgc, .jpeg, .hkdb, .zi, .fsh, .zw, .cas, .xlsx, .mdf, .bc6, .zabw, .iwi, .ws, .xf, wallet, .pdd, .hkx, .gho, .svg, .indd, .gdb, .vtf, .lbf, .p12, .wpl, .vpk, .xld, .mddata, .doc, .jpg, .wpg, .wpw, .xpm, .rim, .ai, .litemod, .tor, .esm, .odb, .wpe, .png, .x3f, .webdoc, .fpk, .rwl, .wsd, .hvpl, .itdb, .bkf, .x3d, .eps, .xdl, .orf, .xlsb, .ztmp, .xml, .wps, .xy3, .xx, .nrw, .pdf, .epk, .bik, .odc, .xls, .wmf, .wotreplay, .odm, .qic, .p7b, .1st, .srw, .mp4, .pem, .3dm, .wps, .y, .xyp, .db0, .tax, .crw, .pak, .slm, .cr2, .upk, .xwp, .fos, .rtf, .arw, .d3dbsp, .t12, .ptx, .wcf, .wdb, .pptx, .vfs0, .dbf, .erf, .zif, .itm, .xlsx, .xls, .dng, .zip, .wpa, .dazip, .css, .kdc, .menu, .sid, .ods, .blob, .wpd, .m4a, .dcr, .arch00, .yal, .wbmp, .psk, .vpp_pc, .cer, .docm, .wot, .zdc, .wp5, .wpb, .big, .xmind, .wp4, .cdr, .wb2, .xar, .sis, .itl, .xdb, .dba, .lrf, .m3u, .srf, .wp, .pst, .rb, .xbdoc, .wsh, .z
The “.Karl file extension” infection encrypts data file by file, directory by directory. In every directory where there is at least one encrypted virus, the ransomware places a file called “_readme.txt”. It contains a message from the creators of the virus demanding a ransom. Below we give an example of this ransom note:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-JbqssVgS78
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.To get this software you need write on our e-mail:
gorentos@bitmessage.ch
In this message, the attackers tell the victim that the files are encrypted, and the only way to decrypt them is to pay a ransom of $980. Those who transfer the ransom within 72 hours, they promise a 50% discount. We think you do not need to say that you can not trust attackers, who infected the computer and blocked all the files on it. There is no guarantee that after paying the ransom, the attackers will contact you and be able to decrypt the encrypted files.
Is it possible to decrypt files
Currently, there is no way to decrypt files encrypted by this ransomware. The reason for this is that the virus uses a very strong encryption system, which allows attackers to be sure that no one can decrypt files in any way. Even anti-virus software, companies developing them, as well as any security experts will not be able to help you. But this does not mean that you need to pay a ransom. All experts say one thing, do not pay the ransom.The payment of a ransom will only encourage attackers to create a new ransomware.
The above does not mean that you have no way out and you must accept that all your files are lost. Yes, at the moment, you can’t decrypt .Karl files for free, but who said that after some time this will not change. But it repeatedly happened that after some time, experts find an opportunity that allows victims to unlock all files. In addition, there is always the opportunity to try a method that allows you to restore encrypted files to their original state. We will talk about this method in detail below.
What to do if you become a victim of “.Karl file extension” infection
If you, your relatives or work colleagues have become a victim of this virus, then below we give a few steps that we recommend you to follow.
- Do not panic
- Do not pay a ransom, and ignore all threats by hackers
- Remove Karl virus
- Restore .karl files to their original state
- Protect computer from ransomware
- Report to the police
Remove Karl virus
The first thing you need to do, after your computer has become a victim of the “.Karl file extension” infection, is to check your computer for malware, find and remove ransomware. By doing this, you can breathe freely and be sure that your computer will no longer encrypt files, nor will it become a source of infection for other computers.
This ransomware, like any other, is not easy to remove! Do not believe the instructions on the Internet that say that this can be done by switching the computer to safe mode or deleting a couple of some files. Unfortunately, this cannot be done in this way. We recommend that you use malware removal tools that are specially made to detect and remove malware and ransomware. In addition, we advise you to scan your computer with not one program, but at least two.
Use Zemana AntiMalware to remove Karl virus
Pay attention to the malware removal tool, which is called Zemana AntiMalware. It has a simple and intuitive interface and has powerful capabilities to detect and remove malware. This program is powerful enough to find and remove the “.Karl file extension” infection. If there is an antivirus on your computer, then you do not need to uninstall or disable it, Zemana AntiMalware can work simultaneously with antiviruses.

- Download Zemana AntiMalware from the following link.
Zemana AntiMalware
165033 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
- Close all programs a run a file named Zemana.AntiMalware.Setup.
- Follow the prompts and do not make any changes to default settings.
- When the Setup wizard has finished installing, the Zemana Anti-Malware (ZAM) will run and display the main window.
- When the installation of the Zemana is completed, start the full scan by clicking on the ‘Scan’ button.
- After the computer scan is completed, you just have to press the ‘Next’ button.
Use MalwareBytes Anti-Malware to remove Karl virus
As we said above, to be sure that the “.Karl file extension” infection has been completely removed, we recommend that you scan your computer with several malware removal tool. In addition to the one that we proposed to use above, we also recommend that you check your computer with MalwareBytes AntiMalware. This is a very famous malware removal tool and we offer our readers to use it to search for and remove malware and ransomware for more than 10 years. As before, you can remove the found malware for free, you do not need to pay anything.
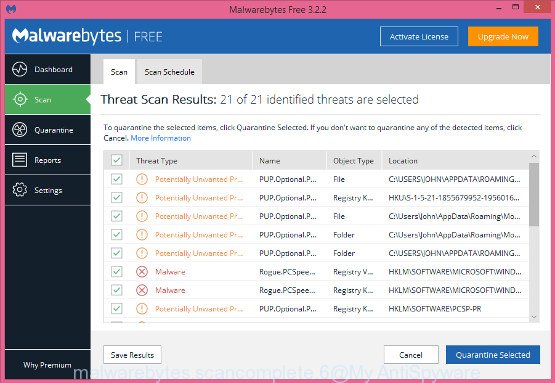
- Download the MalwareBytes Anti-Malware from the link below.
Malwarebytes Anti-malware
327261 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- Double-click on the icon that’s named mb3-setup.
- Click Next button and follow the prompts.
- Once setup is finished, click the “Scan Now” button.
- Once the scan is done, press “Quarantine Selected”.
You can find more information about the program in this article or by watching the following video.
If the problem with Karl ransomware is still remained
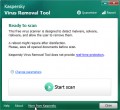
If you performed a system scan using the tools proposed above, you still have doubts that the “Karl file extension” infection has been completely removed, then for an additional computer scan, we recommend that you check your computer using a very powerful program called Kaspersky virus removal tool.
- Download Kaspersky virus removal tool (KVRT) from the link below.
Kaspersky virus removal tool
129291 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
- Once the download is done, Run the Kaspersky virus removal tool.
- Click ‘Start scan’ button.
- After the program checks your computer, click ‘Continue’.
Restore .karl files to their original state
We have already said that decrypting files without a decryptor is impossible. But you can try to restore .karl files to their original state using tools designed to search and recover lost and deleted files. Remember that before you begin to recover files, you need to check your computer and remove ransomware!
Recover .karl files with ShadowExplorer
First of all, try to restore the files using a program called ShadowExplorer. This program uses the standard features of modern versions of the OS and will try to recover your files from their Shadow Volume Copies. The only thing I want to pay attention to is that in most cases the virus deletes all Shadow Volume Copies, so this method does not always work. But, you should definitely try it.
Click the link below to download ShadowExplorer.
439663 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
Once downloading is complete, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as on the image below.
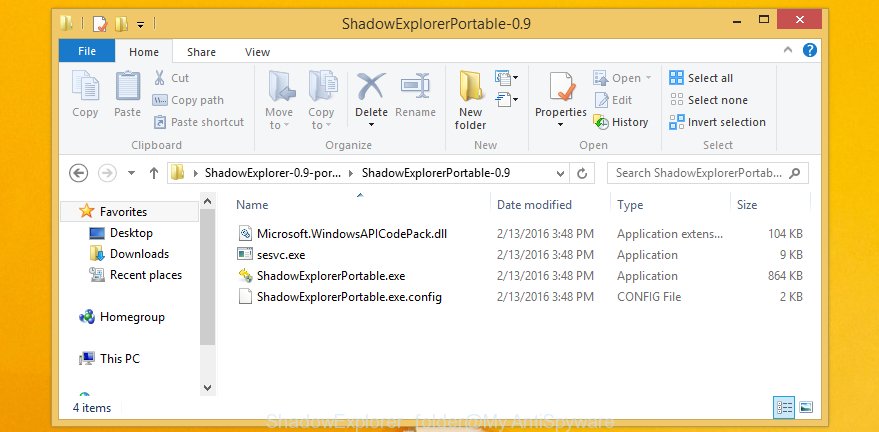
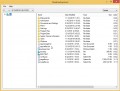
Start the ShadowExplorer tool and then select the disk (1) and the date (2) that you want to recover the shadow copy of file(s) encrypted by the Karl ransomware virus as displayed below.
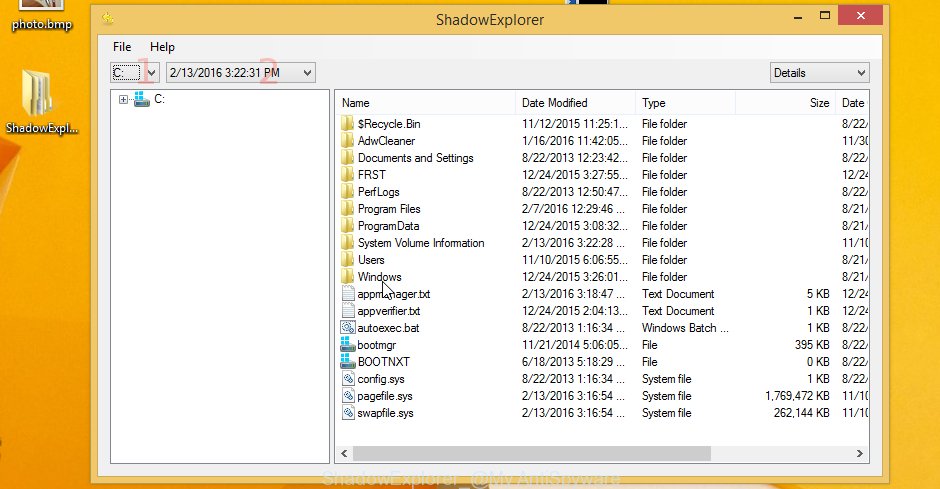
Now navigate to the file or folder that you wish to recover. When ready right-click on it and click ‘Export’ button as shown in the figure below.

Use PhotoRec to recover .karl files
The second method I want to offer you is to use a program that is designed to recover deleted files. When you moved, copied, edited, or deleted files, the Windows OS physically did not delete these files, it just marked in the system area that the files were deleted. The PhotoRec searches for such files, by their properties, and restores them.
Download PhotoRec by clicking on the following link.
Once the downloading process is finished, open a directory in which you saved it. Right click to testdisk-7.0.win and choose Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as shown in the following example.

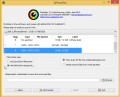
Double click on qphotorec_win to run PhotoRec for Windows. It’ll show a screen like the one below.
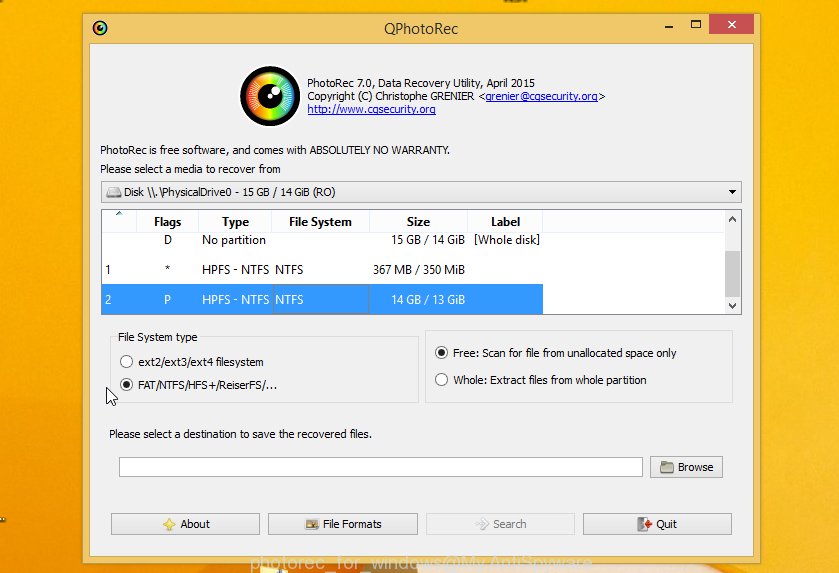
Choose a drive to recover as on the image below.
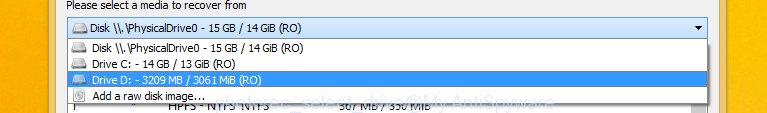
You will see a list of available partitions. Select a partition that holds encrypted personal files like below.
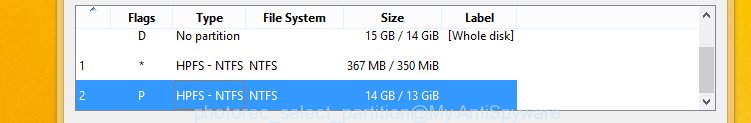
Press File Formats button and specify file types to restore. You can to enable or disable the restore of certain file types. When this is finished, press OK button.
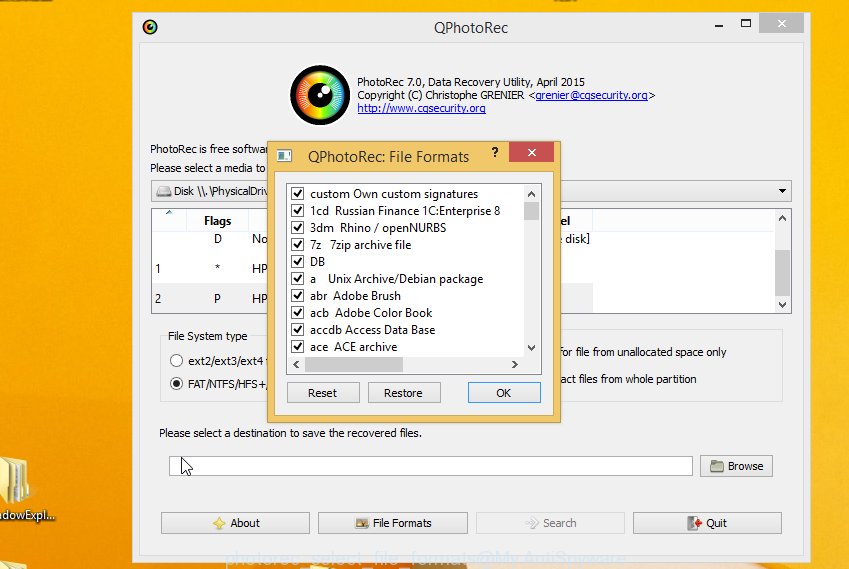
Next, press Browse button to select where restored documents, photos and music should be written, then click Search.
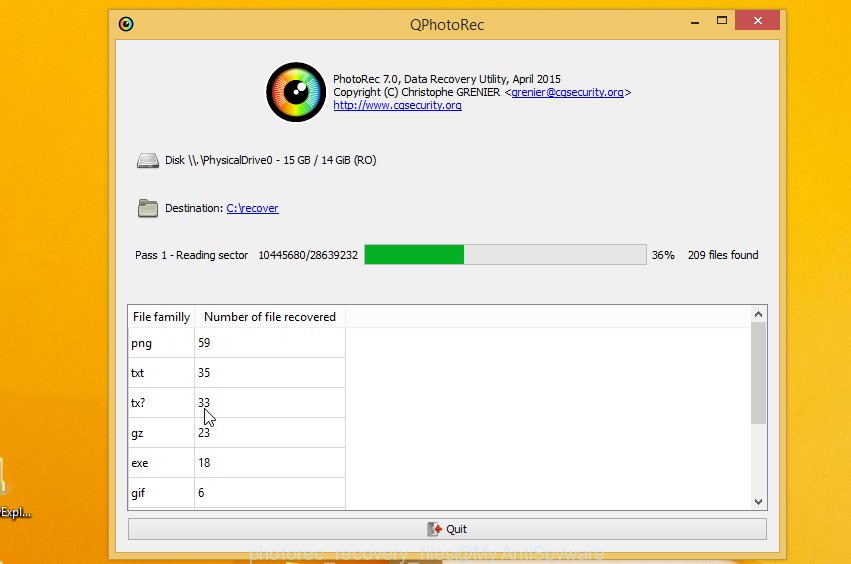
Count of restored files is updated in real time. All restored files are written in a folder that you have chosen on the previous step. You can to access the files even if the restore process is not finished.
When the recovery is complete, click on Quit button. Next, open the directory where restored files are stored. You will see a contents as displayed in the figure below.
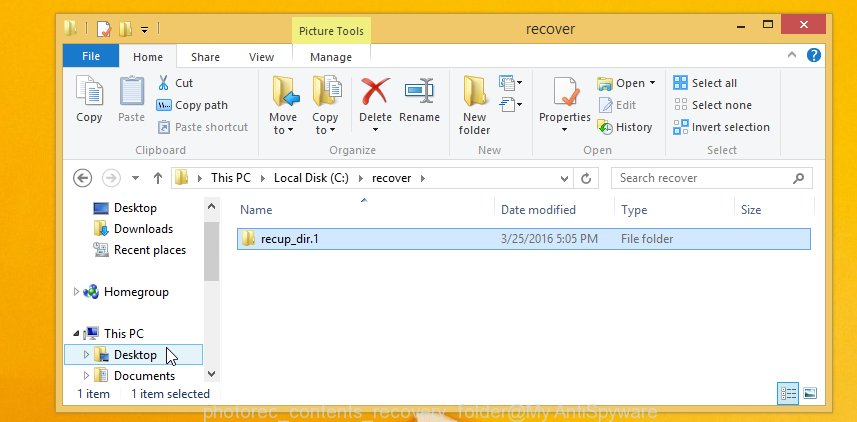
All restored personal files are written in recup_dir.1, recup_dir.2 … sub-directories. If you are looking for a specific file, then you can to sort your recovered files by extension and/or date/time.
Protect computer from ransomware
If you do not have an antivirus software installed, now is the time to download and install it. Moreover, now there are a lot of free anti-virus programs, including those that are presented on our website. In addition to antivirus, we recommend using a program called HitmanPro.Alert. HitmanPro.Alert is a very powerful tool to combat ransomware. It can protect your computer, and if malware is found in the system, it will quickly neutralize it.

- Click the link below to download the HitmanPro.Alert for Windows.
- Double click the HitmanPro Alert.
- Select a level of protection.
- Click the ‘Install’ button to activate the protection.
To sum up
The team of our site, hopes that this article helped you remove “Karl file extension” infection and, most importantly, restore the encrypted files. If you have additional information about the virus, any questions or comments, then write to us.