UsualAccess is an adware, Mac virus that has recently been discovered by security researchers. This dangerous program can cause significant harm to a user’s computer by displaying intrusive ads, redirecting searches, and changing browser settings. It can also act as a backdoor, opening up the system to other malware and stealing sensitive data. In this article, we will explore the impact of UsualAccess adware and provide some tips on how to protect your computer from this malicious program.
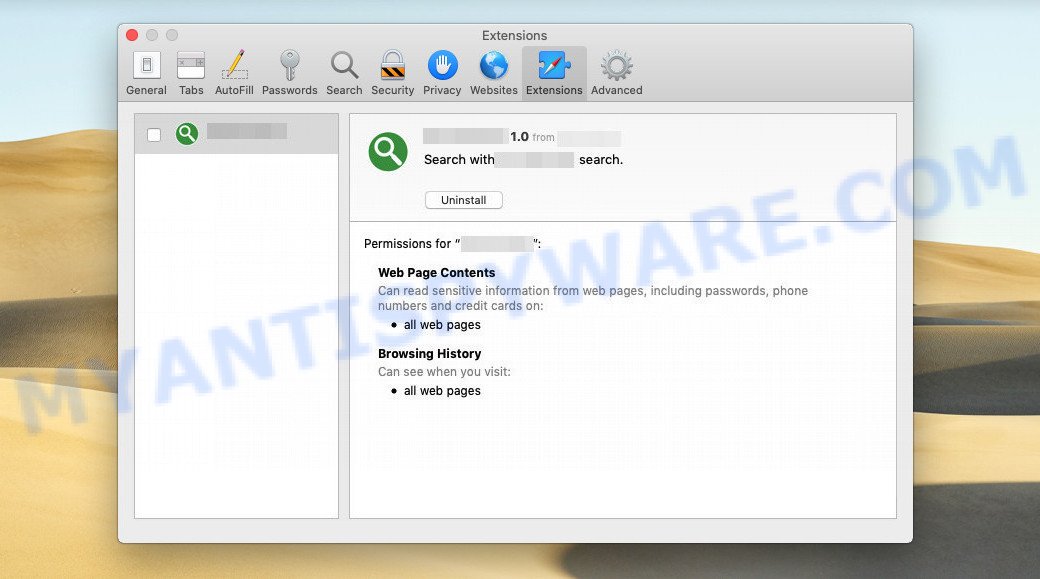
UsualAccess app (extension) is an malicious application (adware) designed to display ads and change browser settings
Table of Contents
UsualAccess adware in detail
UsualAccess is a new Mac adware that is part of the ‘AdLoad’ adware family. It is designed to run intrusive advertisement campaigns which can be harmful. Here are the key points about UsualAccess:
📢 Ad Display
Like other members of the AdLoad family, UsualAccess displays various types of advertisements. Users might encounter pop-ups, banners, and other intrusive ad formats during their browsing sessions.
🔍 Conditional Ad Display
Interestingly, UsualAccess’s ad display behavior is conditional. It may not activate its ad campaigns if the browser or system environment is incompatible, the user’s geographical location doesn’t match certain criteria, or if specific websites are not accessed.
⚠️ Risks Even Without Ads
The threat of UsualAccess extends beyond just displaying ads. Its mere presence on a system poses significant risks, compromising device security and user safety, even if no ads are displayed.
🚨 Promotion of Scams and Malware
Ads shown by UsualAccess often promote dubious content, including online scams, unreliable or harmful software, and malware. These ads can be particularly dangerous as clicking them may trigger unauthorized downloads or stealth installations of harmful programs.
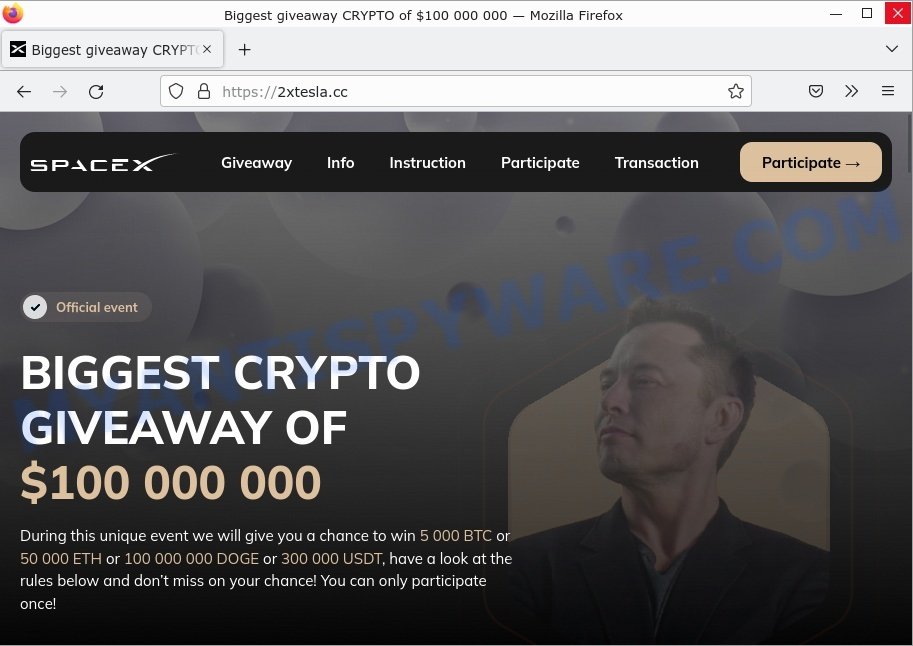
- Elon Musk SpaceX Crypto Giveaway is a SCAM
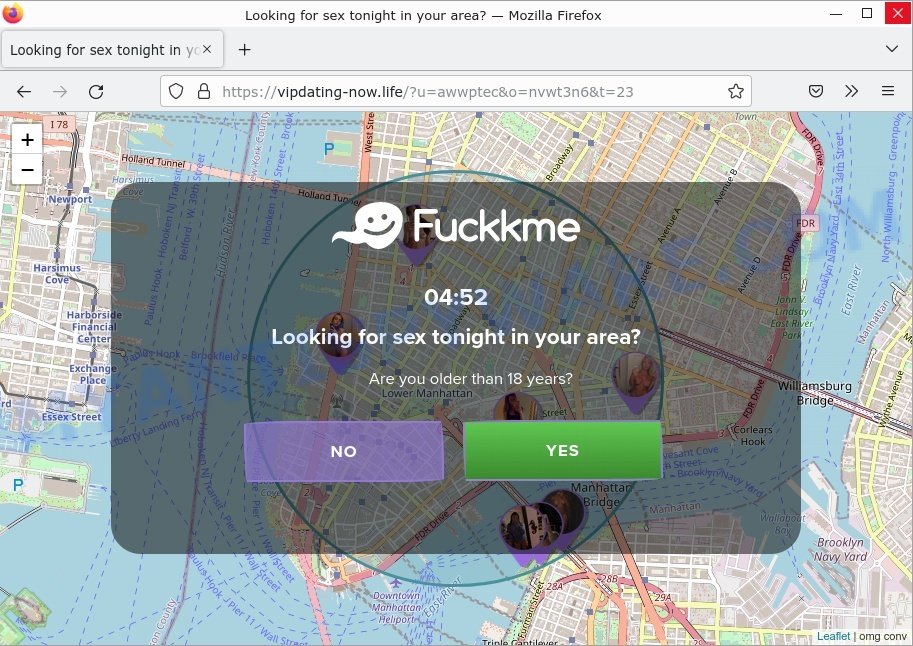
- Vipdatingtoday.top Looking for sex Scam
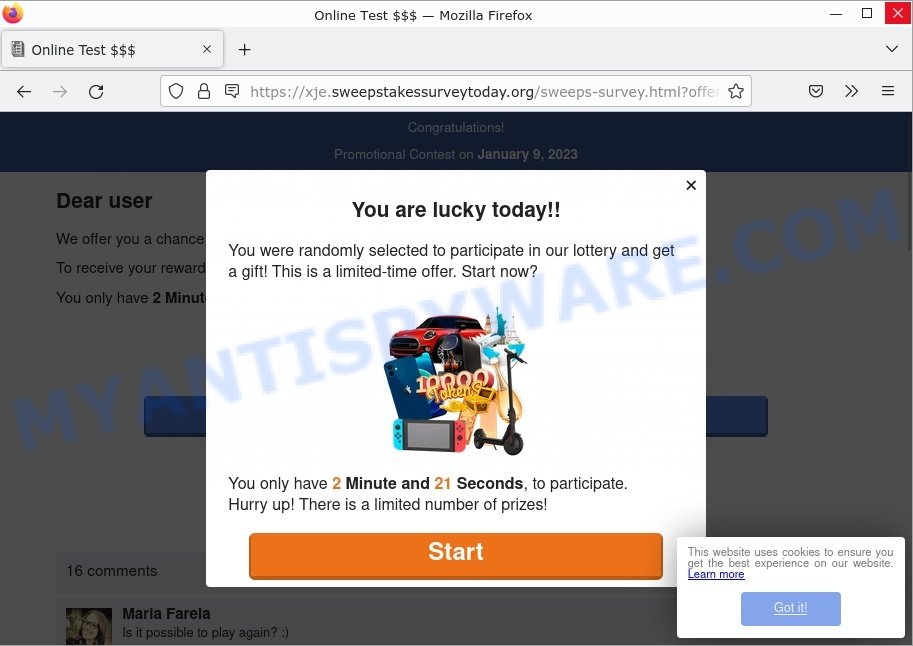
- Sweepstakessurveytoday.org Survey Scam
🔗 Lack of Legitimate Endorsements
It’s worth noting that while you might occasionally come across legitimate content in these ads, such content is rarely, if ever, endorsed by official sources. The promotion is likely done by scammers exploiting affiliate programs for illicit gains.
🌐 Browser Hijacking Capabilities
Unlike Pipidae, UsualAccess has been observed to possess browser hijacker functionalities. This means it can modify browser settings without user consent, potentially changing the homepage, search engine, or causing unwanted redirects.
🔄 Rogue Redirects
A notable feature of UsualAccess is its ability to produce rogue redirects. This means that when users attempt to navigate the internet, they might be unwillingly redirected to different websites. Observed redirects include addresses like chillsearch.xyz and nearbyme.io, among possibly others.
🔗 Diverse Redirect Chains
The redirect chains caused by UsualAccess can lead to various websites. This unpredictability adds to the intrusive nature of the adware, as users cannot anticipate what kind of content or site they might be forced to visit.
👁️🗨️ Data-Tracking Abilities
A particularly concerning feature of UsualAccess is its potential for data tracking. It can gather sensitive information, including visited URLs, search queries, Internet cookies, account log-in credentials, personally identifiable details, and even credit card numbers. This information could be exploited or sold to third parties.
🔓 Consequences of UsualAccess Presence
The consequences of having UsualAccess on a device are far-reaching. Users may face risks such as system infections, severe privacy breaches, financial losses, and even identity theft.
💻 Mac System Warning
Mac systems can identify the presence of malicious apps and typically warn the user with a message that suggests moving the application to the trash. This serves as a crucial alert for users to take immediate action to protect their system.
Text presented in this alert:
“UsualAccess” will damage your computer. You should move it to the Trash.
This file was downloaded on an unknown date.
‘Move to Trash’ ‘Cancel’
🛡️ Overall, the presence of UsualAccess on any device is a significant concern. Users should take immediate steps to remove this adware to protect their systems from potential harm and maintain privacy and security.
UsualAccess: Methods of Infection and Spread
UsualAccess can infect a computer in various ways. One of the most common methods is through software bundling. UsualAccess is included as an optional component alongside legitimate software installation. If the user fails to deselect UsualAccess during the installation process, it will be installed on their system along with the desired software.
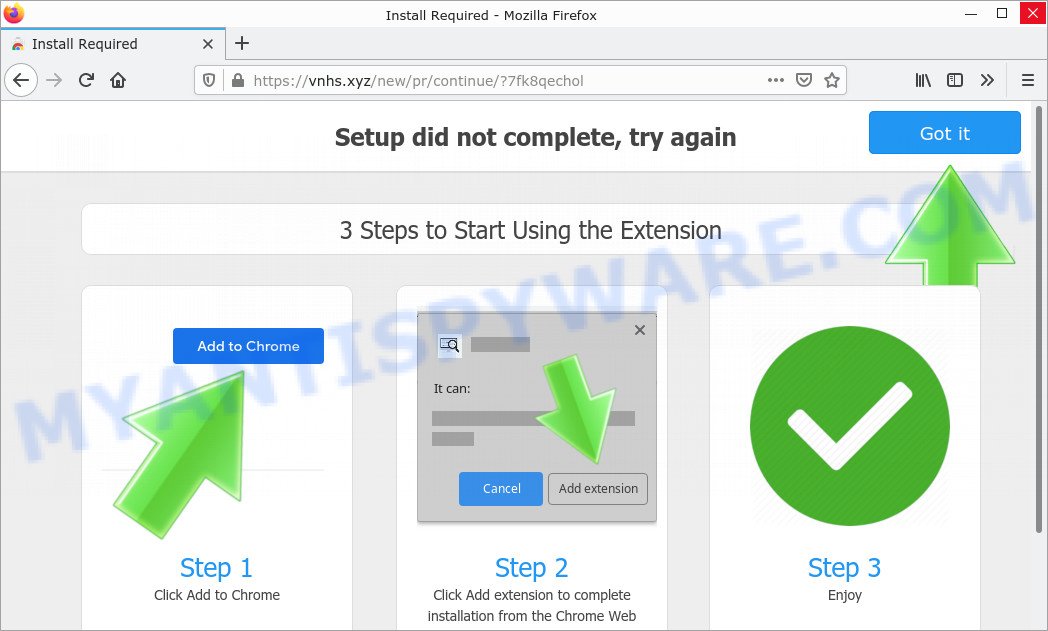
Another way UsualAccess can infect a computer is through malicious advertising, where attackers use ad networks to distribute malicious ads that, when clicked on, download and install UsualAccess onto the victim’s computer. These ads can be found on various websites, including those that are normally considered safe and trustworthy.
Examples of scam pages that are designed to trick users into installing malicious software:
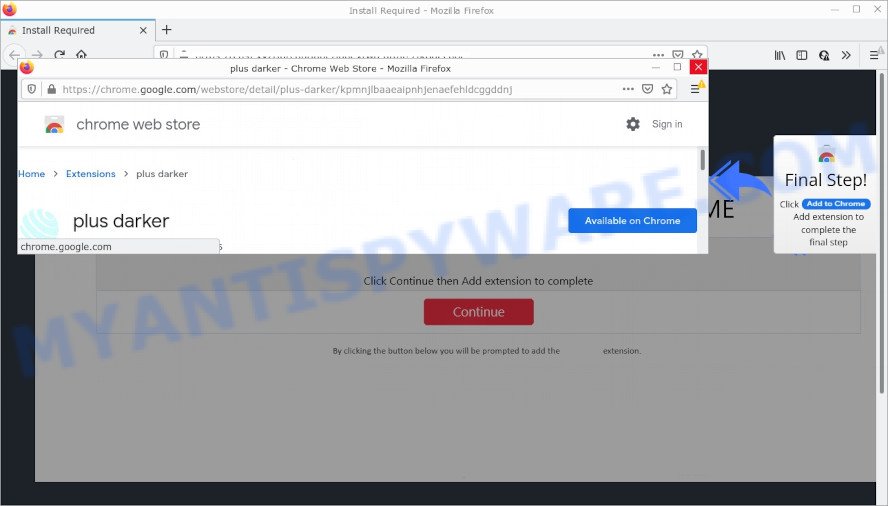
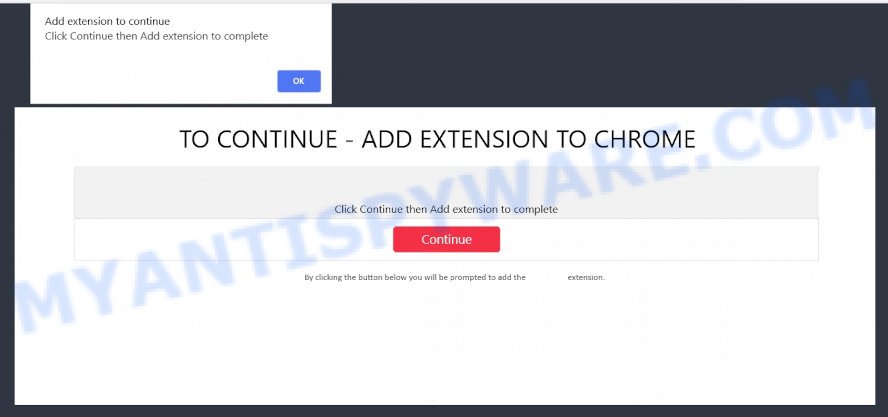
- TO CONTINUE – ADD EXTENSION TO CHROME pop-ups promote a browser hijacker
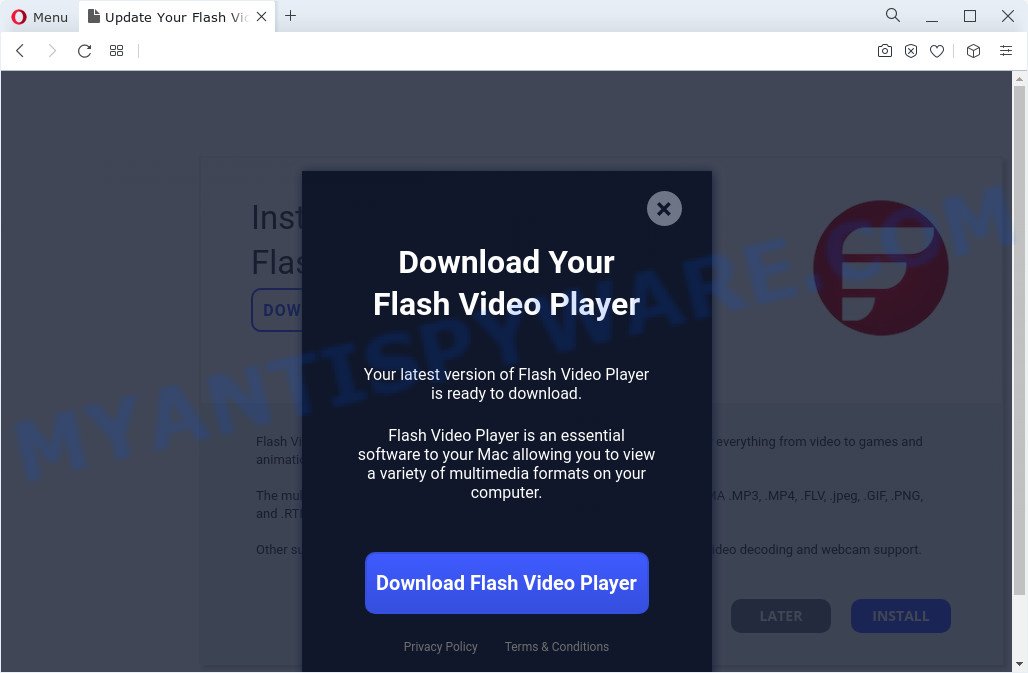
- Fake “Flash Video Player” updates Adware
- “TO CONTINUE – ADD EXTENSION TO CHROME” POP-UP is a SCAM
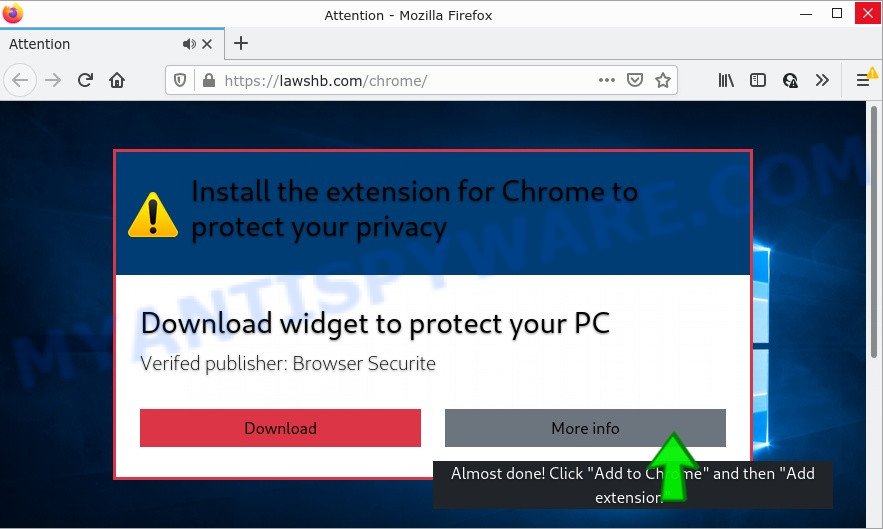
- Install the extension for Chrome to protect your privacy POP-UPS are a SCAM
In some cases, UsualAccess can also be spread through spam email campaigns, where the email contains a link to a website that downloads and installs the adware when clicked on. This type of attack is less common, but it still poses a risk to unsuspecting users who may click on the link without realizing the potential consequences.
In conclusion, users must be cautious when downloading and installing software and clicking on links or ads from unknown sources. Regularly running anti-virus software and keeping it up-to-date can help prevent UsualAccess and other forms of malware from infecting your system.
Threat Summary
| Name | UsualAccess, “UsualAccess adware”, “UsualAccess virus”, “UsualAccess Mac malware” |
| Type | Adware |
| Detection names | AdWare:MacOS/AdLoad.7ed3698c, Gen:Variant.Adware.MAC.AdLoad.5, MacOS:MaxOfferDeal-FL [Adw], ADWARE/GM.MaxOffe.JN, Adware.ADWARE/GM.MaxOffe.JN, Mac.Trojan.AdLoad.2, A Variant Of OSX/Adware.AdLoad.BM, AdWare.OSX.AdLoad, Not-a-virus:HEUR:AdWare.OSX.AdLoad.ac |
| Symptoms | Pop-up ads, browser redirects, slow computer performance |
| Damage | System infections, privacy issues, financial losses, identity theft |
| Prevention | Use ad-blockers, exercise caution when downloading software, avoid clicking on suspicious links and ads, keep browser and operating system up-to-date |
| Distribution | Software bundling, deceptive ads, fake software updates |
| Removal | Use reputable antivirus software, scan downloads before installation, keep software up-to-date |
Malware examples
On the Internet, users can come across many malicious programs that perform various malicious actions. Among them there are such as Communique adware, HackTool:Win32/Keygen malware, WhiskerSpy Backdoor Malware, Altruistics Virus, Your File Is Ready To Download.iso virus, although, of course, there are many more.
Some of the malware designed to collect user data, others install ransomware and trojans on computers, and still others add infected computers to botnets, and so on. In any case, each malicious program (adware, browser hijacker, trojan, worm, …) is a huge threat to both user privacy and computer security. Therefore, malicious programs must be removed immediately after detection; using an infected computer is very dangerous.
How to remove UsualAccess from Mac (Virus removal guide)
Removing UsualAccess from your Mac is important to ensure that your system is not vulnerable to further infections, and your privacy is not compromised. To remove UsualAccess, you can follow these steps: First, uninstall UsualAccess associated software. Then, remove any UsualAccess related files and reset your browser settings to their default. It is also recommended to scan your system with a reliable anti-malware software to ensure that no traces of the adware remain. Finally, take preventive measures such as being cautious of downloading unfamiliar software and keeping your system and security software up to date to prevent future infections.
To remove UsualAccess, follow the steps below:
- Remove profiles created by UsualAccess
- Uninstall UsualAccess associated software by using the Finder
- Remove UsualAccess related files and folders
- Scan your Mac with MalwareBytes
- Remove UsualAccess from Safari, Chrome, Firefox
- How to stay safe online
Remove profiles created by UsualAccess
UsualAccess can install a configuration profile on the Mac system to block changes made to the browser settings. Therefore, you need to open system preferences, find and delete the profile installed by the adware.
Click the System Preferences icon ( ![]() ) in the Dock, or choose Apple menu (
) in the Dock, or choose Apple menu ( ![]() ) > System Preferences.
) > System Preferences.
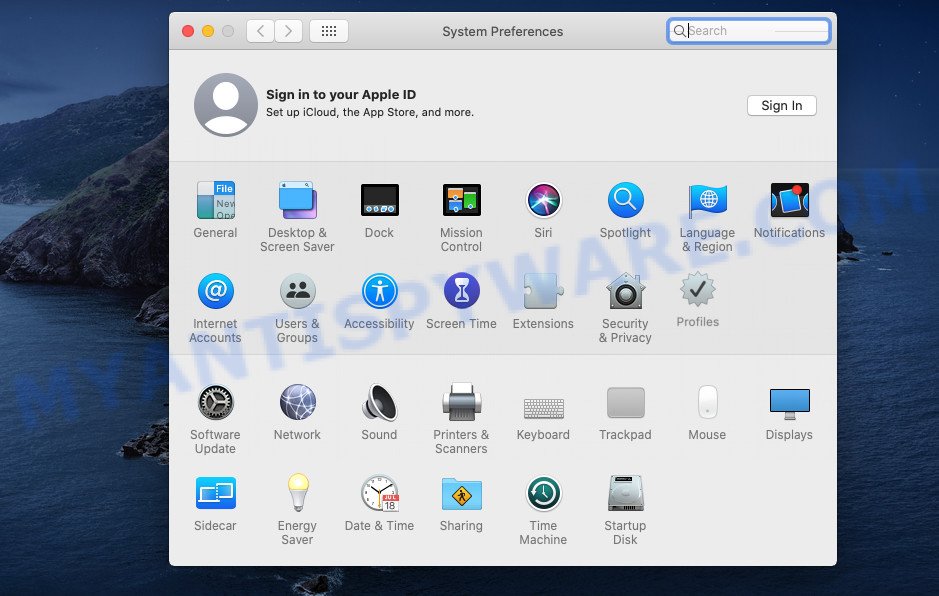
In System Preferences, click Profiles, then select a profile associated with UsualAccess.
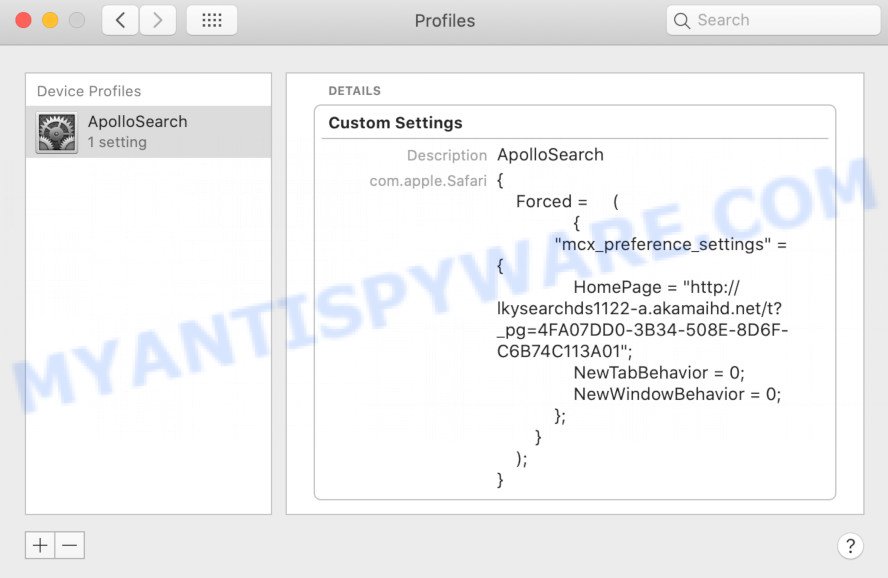
Click the minus button ( – ) located at the bottom-left of the Profiles screen to remove the profile.
Note: if you do not see Profiles in the System Preferences, that means there are no profiles installed on your Mac, which is normal.
Uninstall UsualAccess associated software by using the Finder
In order to get rid of adware, PUPs and browser hijackers, open the Finder and click on “Applications”. Check the list of installed applications. For the ones you do not know, run an Internet search to see if they are PUPs, browser hijackers and adware. If yes, remove them off. Even if they are just a programs which you do not use, then removing them off will increase your MAC start up time and speed dramatically.
Open Finder and click “Applications”.
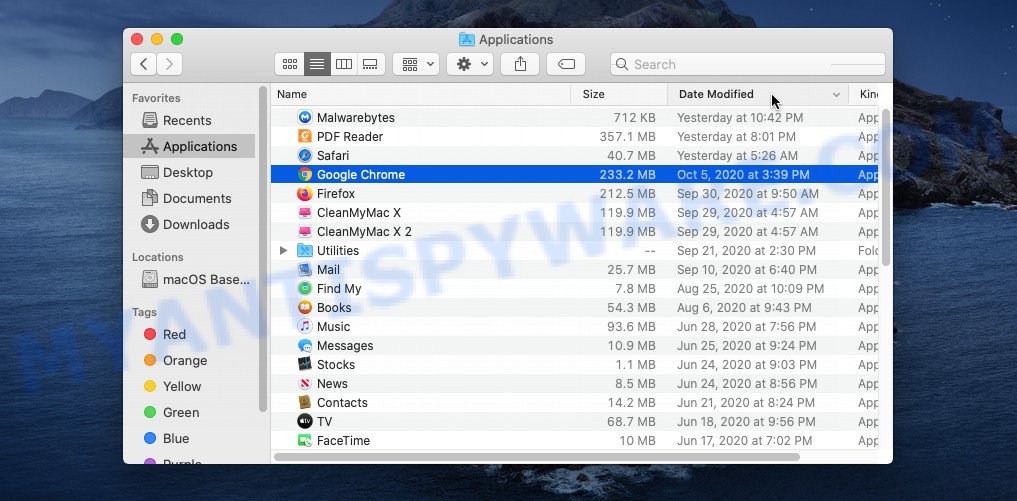
Carefully browse through the list of installed apps and remove all dubious and unknown software.
Once you’ve found anything dubious that may be the UsualAccess or other potentially unwanted program, then right click this program and select “Move to Trash”. Once complete, Empty Trash.
Remove UsualAccess related files and folders
Now you need to try to find UsualAccess related files and folders, and then delete them manually. You need to look for these files in certain directories. To quickly open them, we recommend using the “Go to Folder…” command.
UsualAccess creates several files, these files must be found and removed. Below is a list of files associated with this unwanted application.
- /Library/LaunchAgents/com.laser.plist
- /Library/LaunchDaemons/com.(RANDOM).plist
Some files created by UsualAccess are hidden from the user. To find and delete them, you need to enable “show hidden files”. To do this, use the shortcut CMD + SHIFT + . Press once to show hidden files and again to hide them. There is another way. Click Finder -> Applications -> Utilities -> Terminal. In Terminal, paste the following text: defaults write com.apple.finder AppleShowAllFiles YES
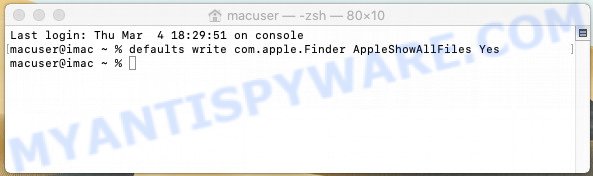
Press Enter. Hold the ‘Option/alt’ key, then right click on the Finder icon in the dock and click Relaunch.
Click on the Finder icon. From the menu bar, select Go and click “Go to Folder…”. As a result, a small window opens that allows you to quickly open a specific directory.
Check for UsualAccess generated files in the /Library/LaunchAgents folder
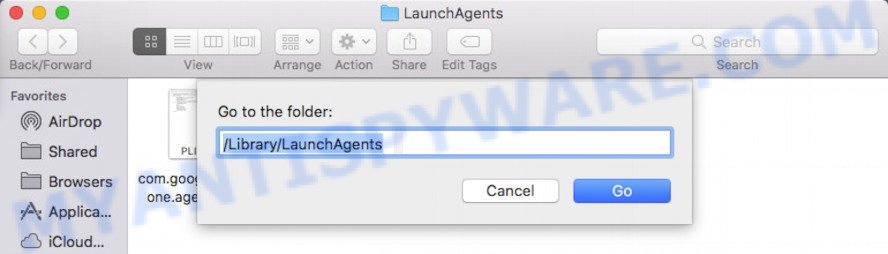
In the “Go to Folder…” window, type the following text and press Go:
/Library/LaunchAgents
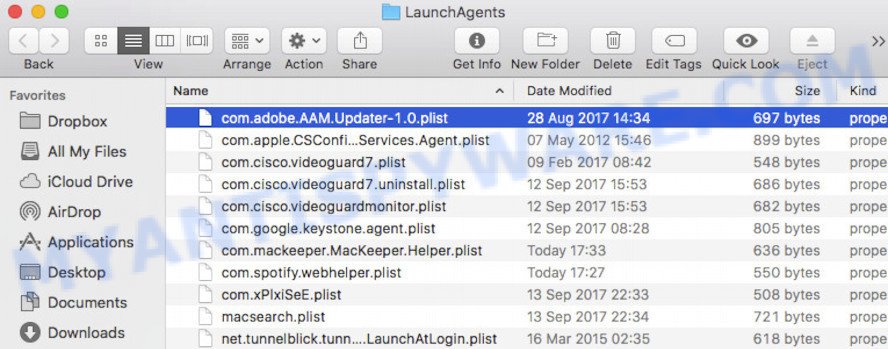
This will open the contents of the “/Library/LaunchAgents” folder. Look carefully at it and pay special attention to recently created files, as well as files that have a suspicious name. Move all suspicious files to the Trash. A few examples of files: com.identification.plist, com.Sorbonical.plist, com.myzostomatous.plist, com.described.plist, com.prepared.plist, com.taskmond.plist, com.memberd.plist, com.funcd.plist, mega.mac.megaupdater.plist, com.interungular.plist, com.jirin.plist, com.rp2.plist, com.firmly.qz.plist, com.repick.plist, com.laser.plist, com.Hatchway.plist, com.centinol.plist, com.chunago.plist. Most often, adware software, potentially unwanted programs and browser hijackers create several files with similar names.
Check for UsualAccess generated files in the /Library/Application Support folder
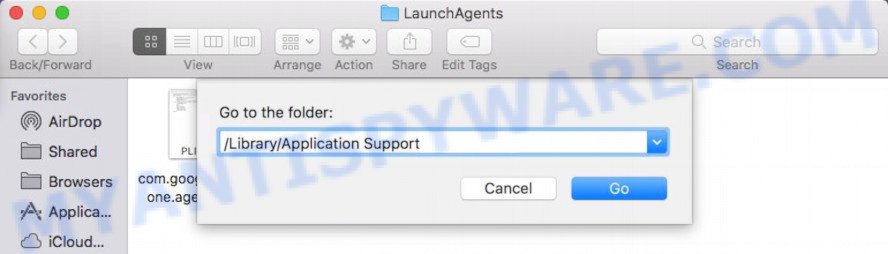
In the “Go to Folder…” window, type the following text and press Go:
/Library/Application Support
This will open the contents of the “Application Support” folder. Look carefully at its contents, pay special attention to recently added/changed folders and files. Check the contents of suspicious folders, if there is a file with a name similar to com.UsualAccess.system, then this folder must be deleted. Move all suspicious folders and files to the Trash.
Check for UsualAccess generated files in the “~/Library/LaunchAgents” folder
In the “Go to Folder…” window, type the following text and press Go:
~/Library/LaunchAgents
Proceed in the same way as with the “/Library/LaunchAgents” and “/Library/Application Support” folders. Look for suspicious and recently added files. Move all suspicious files to the Trash.
Check for UsualAccess generated files in the /Library/LaunchDaemons folder
In the “Go to Folder…” window, type the following text and press Go:
/Library/LaunchDaemons
Carefully browse the entire list of files and pay special attention to recently created files, as well as files that have a suspicious name. Move all suspicious files to the Trash. A few examples of files to be deleted: com.slotting.plist, com.dwlxT.plist, com.apple.efiao.plist, com.afdhjufdghjk.plist. In most cases, adware software, potentially unwanted programs and browser hijackers create several files with similar names.
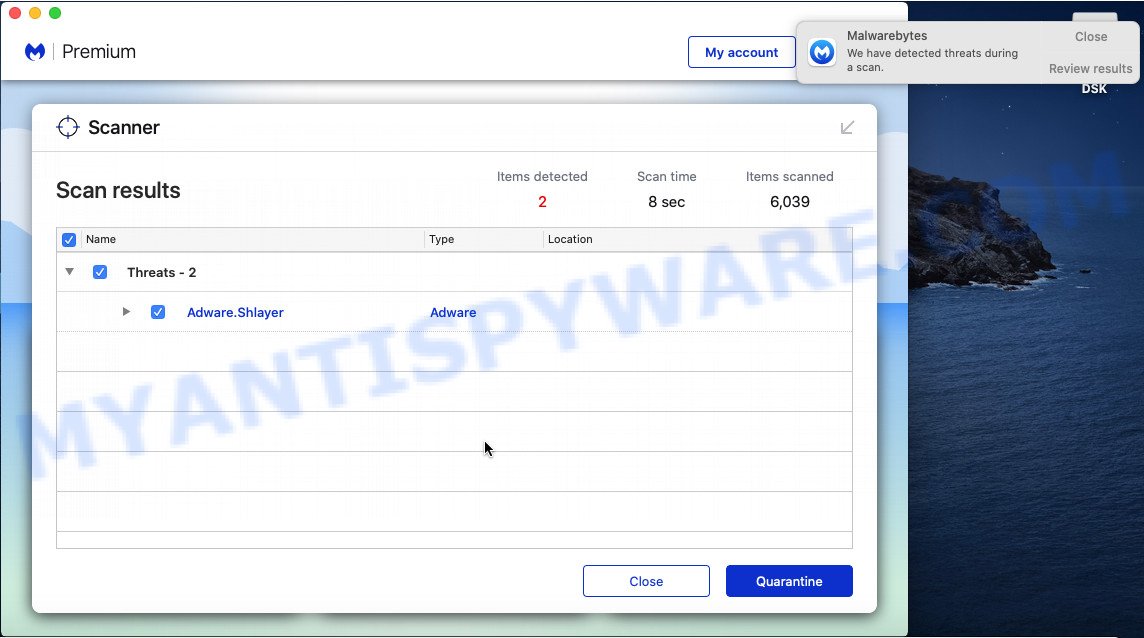
Scan your Mac with MalwareBytes
You can delete UsualAccess associated files automatically with a help of MalwareBytes. We recommend this free malware removal tool because it can easily remove potentially unwanted programs, adware, browser hijackers and toolbars with all their components such as files, folders and system entries.
Download MalwareBytes AntiMalware on your machine from the link below.
21024 downloads
Author: Malwarebytes
Category: Security tools
Update: September 10, 2020
When the download is done, run it and follow the prompts. Click the “Scan” button . MalwareBytes Anti-Malware program will scan through the whole computer for the UsualAccess adware. Review the report and then click the “Quarantine” button.
The MalwareBytes is a free program that you can use to delete all detected folders, files, malicious services and so on.
Remove UsualAccess from Safari, Chrome, Firefox
Remove unwanted extensions is a simple method to delete UsualAccess adware and return web browser’s settings which have been replaced by adware.
You can also try to delete UsualAccess adware by reset Chrome settings. |
If you are still experiencing problems with UsualAccess adware removal, you need to reset Firefox browser. |
|
How to stay safe online
In order to increase your security and protect your MAC system against new intrusive ads and malicious websites, you need to run ad blocking program that blocks an access to malicious ads and websites. Moreover, the program can block the open of intrusive advertising, which also leads to faster loading of web-pages and reduce the consumption of web traffic.
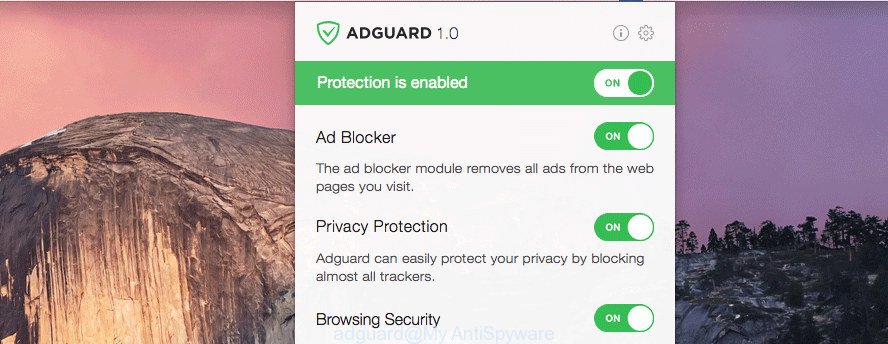
Installing the AdGuard is simple. First you will need to download AdGuard on your Apple Mac by clicking on the link below.
3782 downloads
Author: © Adguard
Category: Security tools
Update: January 17, 2018
When downloading is finished, launch the downloaded file. You will see the “Setup Wizard” screen. Follow the prompts.
Each time, when you start your Mac, AdGuard will start automatically and stop unwanted popup ads, block harmful and misleading websites.
Tips to Prevent Infection
Here are some steps you can take to prevent infection from UsualAccess:
- Only download software from official sources or trusted third-party websites. Avoid downloading from peer-to-peer (P2P) networks or free file hosting websites.
- Keep your operating system and software up-to-date with the latest security patches and updates. These updates often include security fixes that can prevent malware infections.
- Be cautious of suspicious emails or attachments. Hackers often use social engineering tactics to trick users into downloading malware. Avoid clicking on links or downloading attachments from unknown senders.
- Use strong and unique passwords for all your accounts. Avoid using the same password for multiple accounts, and consider using a password manager to help you generate and store strong passwords.
- Use a reputable ad blocker. Ad blockers allow you to browse sites without ads, thus eliminating the possibility of clicking on something malicious and preventing it from being downloaded to the machine.
- Pay for premium versions of popular services. The easiest way to avoid adware is to pay for the service you use. Many Internet services make it possible to use them without ads if you purchase a premium subscription. This helps ensure that malicious adware cannot reach you.
By following these steps, you can significantly reduce your risk of infection from UsualAccess and other types of malware.