The “Facebook Account Recovery Code” scam is a phishing attempt targeting Facebook users. The scam involves sending a fake email that claims Facebook has received a request to reset the recipient’s password. The email attempts to trick users into entering a reset code provided in the message. However, this is a fraudulent attempt to steal the user’s login credentials or gain unauthorized access to their Facebook account.
Quick Links:
- Introduction to the Facebook Account Recovery Code Scam
- Signs of the Scam Email
- How the Scam Works
- What to Do If You Receive the Scam Email
- Reporting the Scam
- Summary Table for Facebook Account Recovery Code Scam
- Conclusion
Introduction to the Facebook Account Recovery Code Scam
The Facebook Account Recovery Code scam involves a fraudulent email that pretends to be from Facebook’s support team. The email subject typically includes a recovery code, and the message claims that a password reset request has been made for the recipient’s Facebook account. The scam aims to deceive users into thinking their account security is at risk and prompts them to enter the provided recovery code.
The email typically includes the following information:
- Sender: Facebook
- Subject: ****** is your Facebook account recovery code
Signs of the Scam Email
Here are some signs that can help identify the Facebook Account Recovery Code scam:
- Unsolicited email. You did not initiate a password reset request.
- The email is not sent from an official Facebook email address. In the example provided, the reply-to addresses are suspicious and do not match legitimate Facebook contacts.
- The email uses urgency and alarm to prompt the recipient to take immediate action.
- There may be grammatical errors or awkward phrasing in the email.
- The email asks the recipient to enter a recovery code provided in the message.
- There is a sense of urgency to respond and confirm whether the password reset request was made by the recipient or not.
How the Scam Works
The Facebook Account Recovery Code scam operates as follows:
- The scammer sends a fake email claiming to be from Facebook’s support team.
- The email includes a recovery code and informs the recipient that a password reset request has been made.
- The scam email creates a sense of urgency and prompts the recipient to enter the recovery code to verify the request.
- If the recipient falls for the scam and enters the code, the scammer gains access to their Facebook account.
- The scammer can then use the compromised account for various malicious activities, such as spreading spam, phishing other users, or engaging in identity theft.
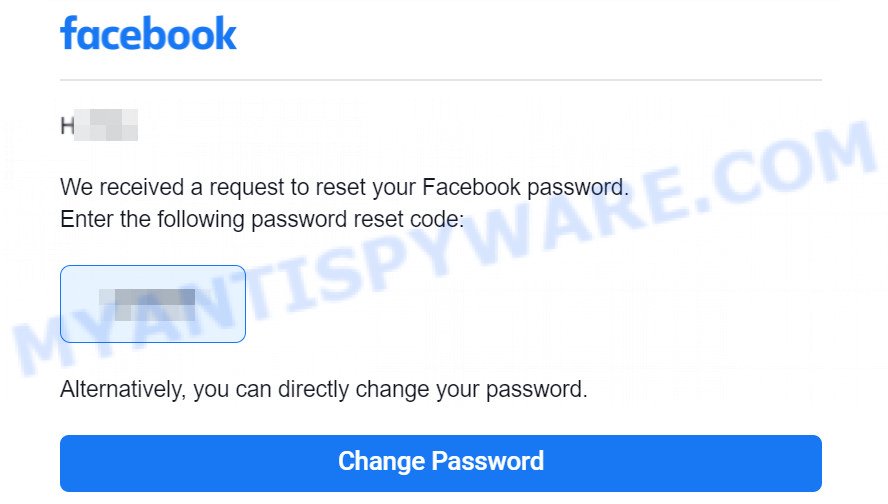
A typical Facebook Account Recovery Code Scam Email reads as follows:
From: Facebook
Subject: ***** is your Facebook account recovery code
Hi,We received a request to reset your Facebook password.Enter the reset code from the following password :5***88
If it was not you, please let us know:
Not my request
You did not ask for this change??
If you have not asked for new password, please let us know
What to Do If You Receive the Scam Email
If you receive the Facebook Account Recovery Code scam email, here’s what you should do:
- Do not click on any links or download any attachments in the email.
- Do not enter the recovery code or provide any personal information.
- Report the email as spam or phishing to your email provider.
- Forward the email to Facebook’s official support team or report it through their designated channels.
- If you have mistakenly entered your recovery code, change your Facebook password immediately and enable additional security measures, such as two-factor authentication.
- Regularly monitor your account for any suspicious activity and report any unauthorized access to Facebook.
By staying vigilant, being cautious of suspicious emails, and taking immediate action to protect your account, you can safeguard yourself against scams like the Facebook Account Recovery Code scam.
Reporting the Scam
If you have received the phishing email, it is important to report it to Facebook. Here’s how you can report the scam:
- Open the suspicious email and locate the “Report” or “Spam” button in your email client.
- Click on the appropriate button to report the email as a phishing scam.
- If possible, forward the email to Facebook’s dedicated email address for reporting scams (e.g., phish@fb.com).
Examples of such scams
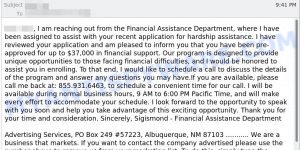
Unfortunately, the Facebook Account Recovery Code Scam is just one of many similar types of scams that cybercriminals use to steal personal and financial information from unsuspecting victims. These types of scams often rely on social engineering tactics, such as urgency or fear, to trick victims into divulging sensitive information. Here are some other examples of scams that operate in a similar manner: Financial Assistance Department Scam Email, Cash Settlement Awarded Email Scam, and Geek Squad Email Scam.
- Avira Assistance PayPal Scam Invoice Email
- Cash Settlement Awarded Email Scam
- BNC Billing Canceled Invoice PayPal Email Scam
- Walmart Order Shipped Email Scam
- Financial Assistance Department Email Scam
Summary Table for Facebook Account Recovery Code Scam
| Name | Facebook Account Recovery Code Scam |
|---|---|
| Type | Phishing scam, spam |
| Danger Level | High |
| Attack Vector | Fake email impersonating Facebook support |
| Purpose | Stealing login credentials, gaining unauthorized access to Facebook accounts |
| Prevention Tips | Be cautious of unsolicited emails, never provide personal information through email, enable two-factor authentication for Facebook |
Conclusion
The Facebook Account Recovery Code scam is a dangerous phishing attempt aimed at stealing users’ login credentials and gaining unauthorized access to their Facebook accounts. Users should be vigilant and exercise caution when receiving emails claiming to be from Facebook’s support team. By recognizing the signs of the scam email, being aware of the scam’s operation, and taking prompt action to report and protect oneself, users can avoid falling victim to this phishing scam.

















Whatever… Someone hacked into my Facebook change it all the passwords whatever email and I’ve got a hold of Facebook my friends have gotten a hold of Facebook and let him know and they said they’re not doing anything wrong and he’s not pretending to be me. Trying to get money from my friends and ruin my business. Person has a picture of me with my driver’s license but I have my damn birth certificate! won’t hear anything about it
That’s why Facebook scary. I don’t know the requirements in your country, but in my country, every account must verify data using a legal identity card. So if an account gets hacked, all of our data can be stolen.
I really hate facebook, but sadly I need my account to advertise my business in meta universe.
Started happening for me since 3 days ago and i receive the same email every few hours! Dont know how to stop the whole risk !
So what can do now that my account was stolen?
I’ve actually got a bunch of these in the past couple of days as well they’re actually legit emails from Facebook. I’ve checked the email headers it is 100% legit from Facebook either some bot or some actor is going around and entering people’s usernames and making password reset requests go out the emails are legit they’re not fraudulent now there may actually be fraudulent ones but all the ones I received are legit from Facebook.
This scam is out of control past couple days…. these emails just keep coming.
What is strange is that the email headers ARE from facebook.. but its the EXACT same account recovery code in all the emails which makes it more so obvious its a scam.
I just can’t for the life of me figure out how they manage to use FB’s real email in the email headers.
Zach. That’s a more sophisticated scam, but it is a scam. You’ll see the same passcode throughout he emails, but passcode generation changes on each repeated attempt. The originating email is from facebook URL but it’s spoofed. I don’t know how they do it, but its faked.
You can enter the passcode and it will reset your password – or if you report it from the link it will take you to a spoofed FB login page which will capture your credentials.
It turns out that many have experienced the same thing as me. These days I still get an email that someone asked for a password recovery code. About 10 emails per day, and those emails come from the official facebook domain (facebookmail.com).
I once clicked on the link in the “Didn’t request this change?” and it seems my account is still safe, meaning the email is not phishing. My assumption is that there are someone who use tools to brute force tons of accounts.
I’ve also been getting a bunch of these the last few days.
I can also verify what Zach is saying that headers are legitimately from FB and originating IP address from FB.
The email in the article for forwarding phishing reports is incorrect.
per https://www.facebook.com/help/225602007465207
THE CORRECT EMAIL IS : phish@fb.com
i have been receiving same emails for the past 3 days too
There is a good follow up on this Reddit thread:
https://www.reddit.com/r/facebook/comments/154goal/someone_keeps_trying_to_reset_my_facebook_password/
Same as other reports, here are my findings:
-> The emails (in my case) seem to be legit, not spoofed, with the correct SFP verified headers from Facebook, see:
https://www.facebook.com/help/1634546593478660
-> This seems to be a brute force attack on a list of emails, and seems to be either “trying to log in to Facebook” or “creating an account in Facebook”, and when failing it triggers the the security code being sent to the user’s email.
-> I have been able to replicate this behavior manually and been able to trigger the message, with the same legit headers from Facebook (see screenshot):
https://monosnap.com/file/RkY0OXaBhB31xOy9oShtIIU81stJEi
-> Checked my “recent emails” on Facebook and they don’t seem to show there though, but probably not being recorded as these are merely notifications, not changes ¯\_(ツ)_/¯You can check those on your account here:https://www.facebook.com/recent_emails/security/?hide_back_button=1&from_accounts_center=1
-> Having a closer look at the link in “If you didn’t request a new password, let us know.”, I did noticed a difference though, the link I received without my action looks like:https://www.facebook.com/login/recover/cancel/?n=12345678&id=123456789012345&i=otherand the one I received from my own replication from a web browser looks like:https://www.facebook.com/login/recover/cancel/?n=12345678&id=123456789012345&i=web
-> In the links “other” implies that this was made via API while my replication was made from a browser (“www”), so this are probably attacks by some bot, trying to find vulnerable accounts.
Also, either link will show you the “Thanks for letting us know” message (even this “fake” link examples), so that is expected behavior from Facebook recording the id of the Facebook Account and the request number (I suppose).
In resume:
-> As long as your account has 2FA and you don’t see any suspicious activity in your logged in sessions, these attacks should be “relatively harmless”
-> Check your login sessions here:https://accountscenter.facebook.com/password_and_security/login_activity
-> It would be worth making sure your email account security is also up to date and no suspicious login activity, or suspicious logged in devices have been detected.
-> Check as well resources like https://haveibeenpwned.com/Passwords to check if your email/passwords may have been compromised.
As for the code being “the same in all emails”, that part is weird, although the emails seem “legit” not sure why the same code is sent, but I feel that may be expected behavior, here is why:
:
-> I visited the “If you didn’t request a new password, let us know.” link of the initial first suspicious email and that “recorded my request”
-> After that I replicated myself by triggering this message and “send it to myself” (as seen in my screenshot).
-> This generated a new code because the previous password reset request # (a.k.a. “the code”) had already been reported as not being requested by me.
-> After I posted this yesterday, I have received 5 more messages and all of them include the same code I received when I replicated this myself, this “code” is not generated by the attacker, is merely a “request number” generated by Facebook and associated with your account id “permanently” (or perhaps “semi-permanently”) and will continue to be valid for further requests unless acted upon (by reporting via the “let us know” link)
-> The code itself does not seem to be “secure” itself as it is actually part of the plain text URL in the “let us know link” and can be seen right after “cancel/?n=”.
In the example I shared, the “code” in the email would be “12345678” and my Facebook ID would be 12345678912345 :
https://www.facebook.com/login/recover/cancel/?n=12345678&id=123456789012345&i=web
I’m pretty sure that if I acknowledge the “let us know” link again, this will invalidate the “request number” (the “code”) and the next attempt will have a “new code”. I’ll post again once I’ve get a new attack and confirmed this.
At this point I’ll be more interested on how could we collectively report this to Facebook, since their “human customer service” is legendary almost non-existent.
I have started to receive these emails saying I have requested a password reset. As I have not, I looked at the Accounts Centre and then Recent Emails which only showed one they sent me over a year ago, nothing relating to this one.
Scammers can inject anyone’s email address into the headers and hence it will look like it has come from a legitimate address. It is the links which are dangerous. Never click on anything. Move the email to your Junk Email account in Outlook (if you are using that). This disables the links and shows them in clear text.
What, if anything, will happen if you reply to the email scam? I mean, can replying to it effectively give them them the information they’re looking for or do you have to quote the number they supplied in order for their nefarious plans to come to fruition?
Something else that is in these scams is them telling you NOT to forward the email “to keep your account secure”.
“To help keep your account secure, please don’t forward this email. Learn more” that’s the quote at the end of the email.
I think these emails are tricks from Fb to get people to log into their accounts if they haven’t been on the platform in a while. It’s a way to spike the engagement numbers by scaring people into logging into their accounts to count them as active.