Have you ever received an email from a supposed “professional hacker” claiming to have gained access to your computer and your personal information? One such email starts with the alarming line: “Hi there! I am a professional hacker and have successfully managed to hack your operating system.” This is a type of online scam known as a “sextortion” or “sexual extortion” scam, where scammers use stolen email credentials to send out fraudulent messages to millions of people around the world. In this article, we will delve into the details of this particular scam and what you should do if you receive a similar message.
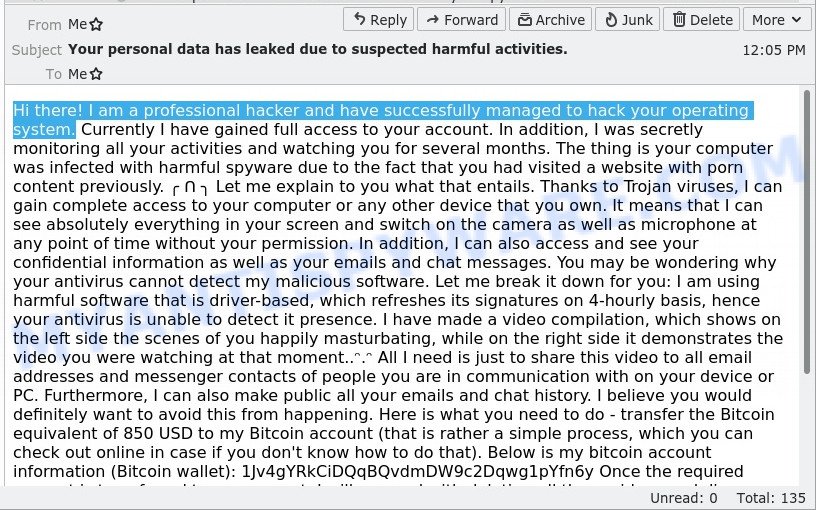
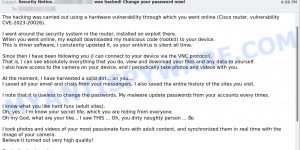
Here’s an example of the “I am a professional hacker” scam email:
QUICK LINKS
- Is this a scam email?
- How the scam works
- Should you pay?
- What to do when you receive the scam email?
- How to spot such scams?
Is this a scam email?
Yes, the email you received claiming to be from a professional hacker threatening to reveal compromising information about you is a common online scam known as a sextortion scam.These scams are sent out to millions of people using stolen email credentials, and the scammers hope to trick recipients into paying a ransom. In most cases, the scammer does not have any actual compromising information on the recipient and is simply using scare tactics to extort money. It is crucial that you do not engage with these scammers or send any money. We will provide more information about this scam and how to protect yourself in the section below.
How the scam works
The scam starts with an email, which claims to be from a professional hacker, who has successfully hacked your operating system and gained full access to your account. The scammer then goes on to say that they have been secretly monitoring all of your activities, including watching you for several months. They claim that your computer was infected with harmful spyware due to the fact that you had visited a website with pornographic content, and that they can see everything on your screen and switch on your camera and microphone at any time.
The scammer then threatens to share a video compilation of you engaging in sexual activities with your contacts unless you pay a ransom. The ransom demand is usually in the form of Bitcoin, and the scammer provides their Bitcoin wallet address for payment. The scammer may also claim to have a list of your contacts and threaten to send the video to them if the ransom is not paid within a certain time frame.
It is important to note that these scammers often do not have any actual compromising information on you and are simply using scare tactics to extort money. In some cases, they may use real passwords that you have used in the past to make the threat seem more credible. However, these passwords are usually obtained from previous data breaches and are not a sign that the scammer has actually hacked your computer.
The scam email read as follows:
Hi there! I am a professional hacker and have successfully managed to hack your operating system. Currently I have gained full access to your account. In addition, I was secretly monitoring all your activities and watching you for several months. The thing is your computer was infected with harmful spyware due to the fact that you had visited a website with porn content previously. ╭ ᑎ ╮ Let me explain to you what that entails. Thanks to Trojan viruses, I can gain complete access to your computer or any other device that you own. It means that I can see absolutely everything in your screen and switch on the camera as well as microphone at any point of time without your permission. In addition, I can also access and see your confidential information as well as your emails and chat messages. You may be wondering why your antivirus cannot detect my malicious software. Let me break it down for you: I am using harmful software that is driver-based, which refreshes its signatures on 4-hourly basis, hence your antivirus is unable to detect it presence. I have made a video compilation, which shows on the left side the scenes of you happily masturbating, while on the right side it demonstrates the video you were watching at that moment..ᵔ.ᵔ All I need is just to share this video to all email addresses and messenger contacts of people you are in communication with on your device or PC. Furthermore, I can also make public all your emails and chat history. I believe you would definitely want to avoid this from happening. Here is what you need to do – transfer the Bitcoin equivalent of 850 USD to my Bitcoin account (that is rather a simple process, which you can check out online in case if you don’t know how to do that). Below is my bitcoin account information (Bitcoin wallet): 1Jv4gYRkCiDQqBQvdmDW9c2Dqwg1pYfn6y Once the required amount is transferred to my account, I will proceed with deleting all those videos and disappear from your life once and for all. Kindly ensure you complete the abovementioned transfer within 50 hours (2 days +). I will receive a notification right after you open this email, hence the countdown will start. Trust me, I am very careful, calculative and never make mistakes. If I discover that you shared this message with others, I will straight away proceed with making your private videos public. Good luck!
If you receive an email like this, do not engage with the scammer and do not send any money. Instead, delete the email and report it to the relevant authorities. It is also important to ensure that your computer has up-to-date anti-virus software and that you use strong, unique passwords for all of your accounts to reduce the likelihood of falling victim to scams like this.
Examples of such scams
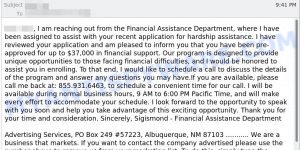
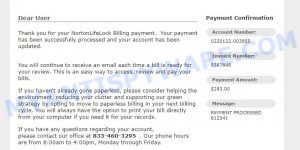
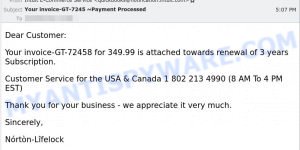
In addition to the “I am a professional hacker” email scam, there are many other types of phishing and extortion scams that are common on the internet. These scams can range from fake tech support calls and emails to more elaborate schemes involving fake job offers, fake lottery winnings, and more. Many of these scams use fear and intimidation tactics to pressure victims into providing sensitive information or paying money. Below are some other common types of scams that you should be aware of to help you stay safe online: Metamask Email Scam, Geek Squad Email Scam, and Financial Assistance Department Scam.
- Walmart Order Shipped Email Scam
- Financial Assistance Department Email Scam
- NortonLifeLock Billing Payment Scam Email
- Intuit Norton Lifelock Scam Email
- I am a spyware software developer Email Scam
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to do when you receive the scam email
If you receive the “I am a professional hacker” email scam, it’s important to stay calm and not panic. The scammers are trying to intimidate you, but remember that their threats are empty and baseless. Here are some steps you can take:
- Do not panic! While these emails are designed to instill fear and panic in the victim, it is important to stay calm and take a measured response to the situation. Remember that the email is fake, and that the attacker does not have access to the sensitive information they are threatening to release
- Avoid clicking on links in sextortion emails as they may lead to malware or phishing sites that can compromise your computer or steal sensitive information.
- Do not reply to the email, or send any money to the attacker.
- Report the scam to the FTC at https://www.ftc.gov/ and relevant authorities, such as your email provider or local law enforcement.
- Delete the email from your inbox and trash folder.
- Take steps to secure your online accounts and personal information, such as changing your passwords and enabling two-factor authentication.
- Stay informed about current scams and the tactics used by attackers, so that you can better recognize and avoid them in the future.
- If you suspect that your computer is infected with spyware or malware, or if you clicked on a link in the scam email, it’s always a good idea to scan your computer for viruses. Use a reputable anti-virus program to scan your computer thoroughly, and make sure it’s up-to-date with the latest virus definitions.
Remember, the scammers are counting on you to be scared and make impulsive decisions. Don’t fall for their tricks and take the necessary steps to protect yourself.
Threat Summary
| Name | I am a professional hacker SCAM |
| Type | Sextortion, Phishing, Bitcoin Blackmail Scam |
| Ransom amount | $990, $950, $850 |
| Bitcoin Address | 1MSafx9aRzRybiqgGJnH1Ah4EJz5usuSxy, 1DxrzqzwqDBw1jcHUZv1Qb9eFFfYzdiXCY, 18JafCUSR3JWJuxbSH9Wp4AUizzTwkZz9D, 16rGyggURQvJw6RMwigDVzEGjjoCC5fZFP, 1AsRkzQSorZAc66fdXof9NHTNJdU4T8nC8, Bc1q8pzqk08mrxvgmvzh55eqvgljhedsmm7wpw7xzy, 1Jv4gYRkCiDQqBQvdmDW9c2Dqwg1pYfn6y, 1Er1bTsfVpy2uZ88hBDJf1i66SuYxQCRKb, 1CRJGomhCirQGNUVwjCC8uNRwA5AWDZafd, 1GyYujUxs2eJpECpYu3Ns6F4RvZqsp8NT6 |
| Fake Claims | Scammers claim to have hacked the victim’s computer and obtained sensitive information or videos |
| Disguise | Emails appear to come from a professional hacker threatening to release embarrassing videos of the victim |
| Damage | Emotional distress, possible monetary loss from paying ransom |
| Distribution | Scammers use stolen email credentials to send out millions of messages to email addresses exposed in previous data breaches |
| Tactics | The scammers may use various tactics to make their threats seem more credible, such as including the victim’s actual password in the email |
| Variations | spam email campaigns |
| Removal | There are several variations of this scam, including ones that claim to have compromised the victim’s webcam or have installed malware on the victim’s computer |
How to spot such scams?

To avoid falling prey to similar scams, it is important to know how to spot them. Here are some tips to help you identify such scams:
- Check the sender’s email address. Scammers often use fake or slightly altered email addresses to appear legitimate. So, always check the sender’s email address before opening an email or clicking on any links.
- Beware of urgent or threatening language. Scammers often use urgent or threatening language to create a sense of urgency and make you act quickly without thinking. So, be wary of emails that demand immediate action or threaten you with dire consequences.
- Don’t trust unsolicited emails. Scammers often send unsolicited emails claiming to offer you a deal that’s too good to be true or warning you about a problem that you didn’t know existed. So, always be skeptical of such emails and verify the claims before taking any action.
- Look for spelling and grammar errors. Scammers often use poor grammar and spelling errors in their emails. So, if you notice such mistakes, it’s a red flag that the email may not be legitimate.
- Don’t click on suspicious links. Scammers often use phishing links to trick you into revealing your personal information or installing malware on your device. So, never click on suspicious links or download attachments from unknown sources.
By following these tips, you can avoid falling prey to similar scams and protect yourself from financial losses and identity theft.
Conclusion
In conclusion, the “I am a professional hacker” email scam is a serious threat to people’s privacy and financial security. Scammers are using stolen email credentials to send out scam messages, tricking people into paying a ransom by threatening to release compromising information. It is important to be vigilant and to never respond to such emails or pay any ransom demands. The best way to protect yourself is to follow the prevention tips mentioned in this article and report any suspicious activity to the relevant authorities. Remember, prevention is better than cure, so stay safe and be alert!















Attention ,
I am the IT of my company , all the files and documents sent to you pass through me and I attached spyware along . I have full access to your computer thanks to my Trojan virus .
I know all your secrets, that is your business and life . It’s not my problem , I just need quick money to solve a family problem .
Even if you report me to my company , I have resigned already and I have what I have . You have no proof this email is from and I still have what I have .
I can see absolutely everything on your screen , I see your confidential information as well as your emails and chat messages . I am using harmful software that is driver-based, which refreshes its signatures on a 4-hourly basis, hence your antivirus is unable to detect its presence .
I have been secretly monitoring all your activities and watching you for several months. I made a video compilation , all I need is just to share this video to all email addresses and messenger contacts of people you are in communication with on your device or PC .
I can also make public all your emails and chat history but it’s not important to me. I just want money for the information I have and I believe you would definitely want to avoid this from happening .
You will transfer the Bitcoin equivalent of 3500 USD to my Bitcoin account ( in case you don’t know how to do that , it’s a simple process which you can check out online ) .
This is my bitcoin account information ( Bitcoin wallet : BELOW ATTACHED ) Once the required amount is transferred to my account, I promise to delete all those videos and disappear from your life once and for all . My Father is in the hospital and I need this money . Please don’t make me do this .
Ensure you complete the above mentioned transfer within 60 hours (2 days +). I will receive a notification right after you open this email , the countdown will start .
If I discover that you shared this message with others, I will straight away proceed with making your private videos public . Trust me , I am very careful , calculative and never make mistakes .
those scammers info
IP address: 27.145.152.215
hostname: cm-27-145-152-215.revip12.asianet.co.th
ISP: True Online
ASN: AS17552
City: Nakhon Ratchasima
Region: Sisaket
Country: Thailand (TH) flag
latitude: 14.9707
longitude: 102.1019
Please tell me about this email, whats happen after 2 day. because i also received this type of email. Please help.
nothing will happen it is a scam
Hi, I was scammed. Does anybody knows how to help me ? Thanks