What is As you can see, this is not a formal email SCAM?
As you can see, this is not a formal email is a new ‘sextortion’ scam that spreads through spam email campaigns. Like most sextortion scams, it relies on “social engineering”, a process through which the scammers induce shame, panic or guilt. Scammers usually use an attention-grabbing email subject/title, in this case “Cooperation Offer”, to trick users into opening scam emails. The scam emails claim that a sender obtained material compromising the user (as a result of a computer hack, email account hack, router hack, etc) and threaten to publish it if the ransom is not paid. All these claims are not based on anything, they are just deception. Therefore, scam emails should be ignored, marked as SPAM/JUNK and deleted.
The “As you can see, this is not a formal email” message is a SCAM
QUICK LINKS
- What is As you can see, this is not a formal email SCAM?
- Should you pay?
- What to do when you receive the email scam?
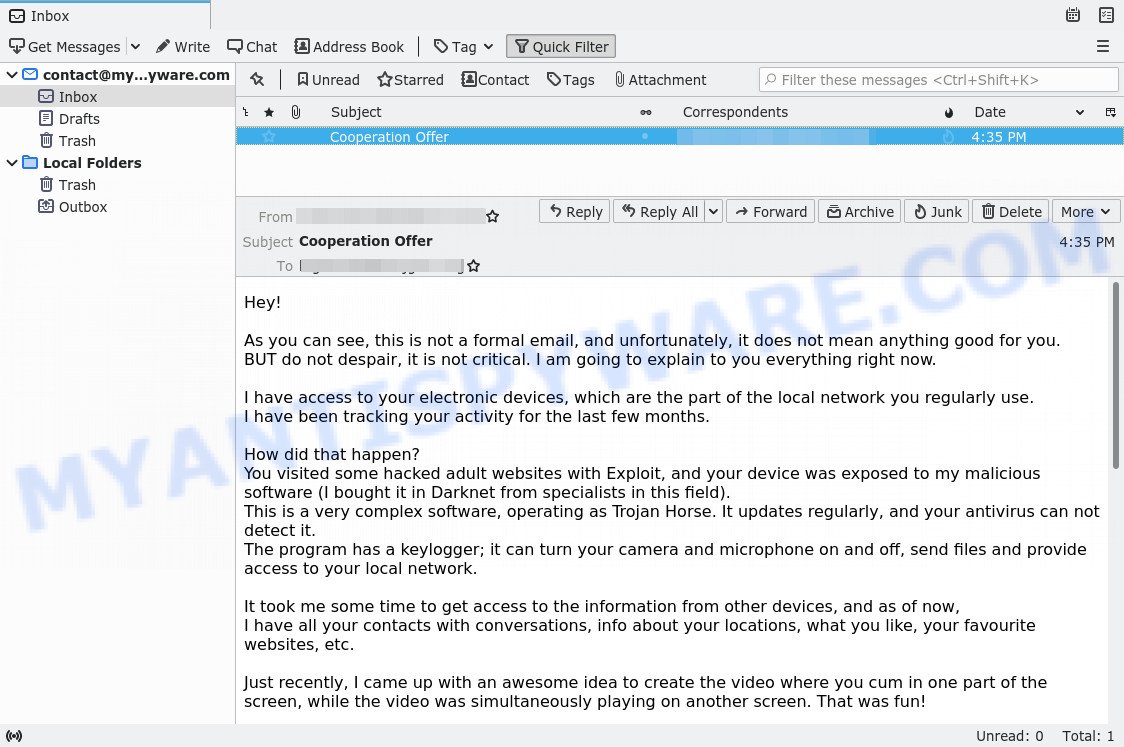
The sender of the email claims to have compromised some adult sites and that the recipient of the email (victim) visited those sites. Using compromised sites, the hacker was able to infect the victim’s device with malware that acts as a Trojan and keylogger. Further in the email, the attacker claims that this Trojan allowed him record a video in which the victim masturbates while watching a porn video. The hacker threatens to send the video to everyone on the victim’s contact list unless the victim pays a ransom of $1650. If the victim pays the required amount in Bitcoin, the hacker promises to delete all the data and videos permanently. Next, the scam email contains the bitcoin address to which the ransom should be transferred.
In some cases, such emails may contain real passwords that the victim has used in the past (or even uses). Usually passwords are appended to these emails as proof, that is, if the password was actually used by the victim, then what is described in the email is true. Scammers get these real passwords by buying them on darknet. However, the email is just a sextortion scam, all statements are fake. Therefore, this email and other emails containing such content should be ignored.
Text presented in the “As you can see, this is not a formal email” message:
Hey!
As you can see, this is not a formal email, and unfortunately, it does not mean anything good for you.
BUT do not despair, it is not critical. I am going to explain to you everything right now.I have access to your electronic devices, which are the part of the local network you regularly use.
I have been tracking your activity for the last few months.How did that happen?
You visited some hacked adult websites with Exploit, and your device was exposed to my malicious software (I bought it in Darknet from specialists in this field).
This is a very complex software, operating as Trojan Horse. It updates regularly, and your antivirus can not detect it.
The program has a keylogger; it can turn your camera and microphone on and off, send files and provide access to your local network.It took me some time to get access to the information from other devices, and as of now,
I have all your contacts with conversations, info about your locations, what you like, your favourite websites, etc.Just recently, I came up with an awesome idea to create the video where you cum in one part of the screen, while the video was simultaneously playing on another screen. That was fun!
Rest assured that I can easily send this video to all your contacts with a couple clicks, and I assume that you would like to prevent this scenario.
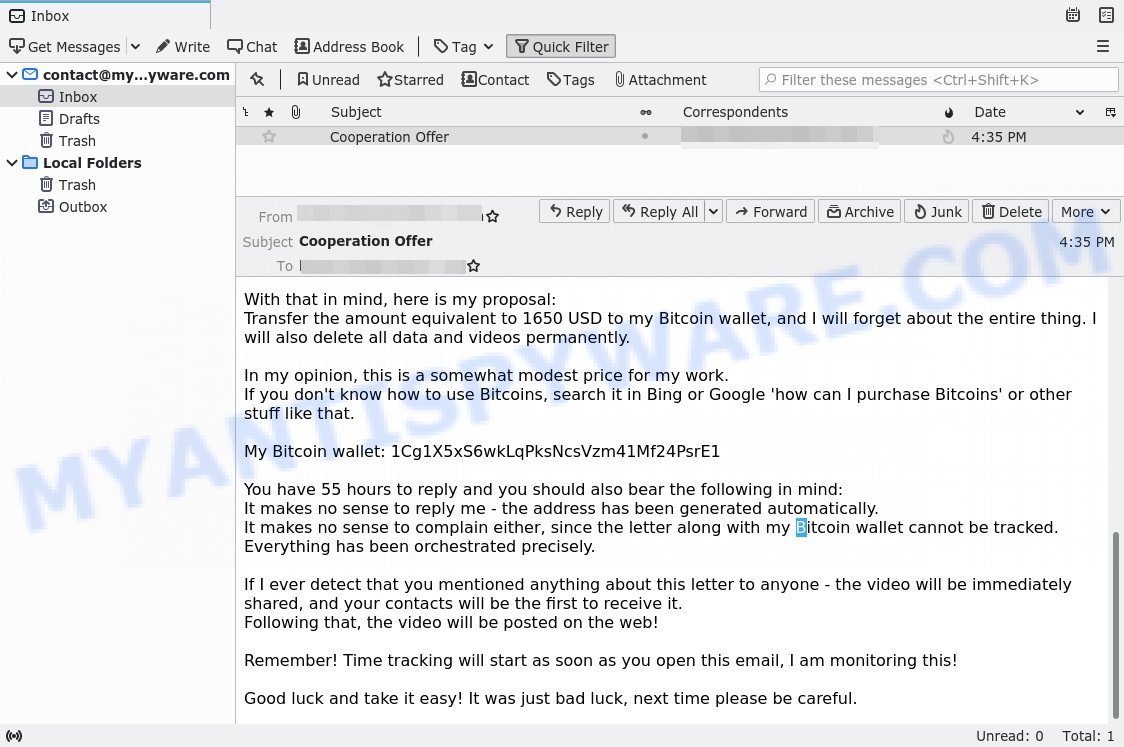
With that in mind, here is my proposal:
Transfer the amount equivalent to 1650 USD to my Bitcoin wallet, and I will forget about the entire thing. I will also delete all data and videos permanently.In my opinion, this is a somewhat modest price for my work.
If you don’t know how to use Bitcoins, search it in Bing or Google ‘how can I purchase Bitcoins’ or other stuff like that.My Bitcoin wallet: 1Cg1X5xS6wkLqPksNcsVzm41Mf24PsrE1
You have 55 hours to reply and you should also bear the following in mind:
It makes no sense to reply me – the address has been generated automatically.
It makes no sense to complain either, since the letter along with my Bitcoin wallet cannot be tracked.
Everything has been orchestrated precisely.If I ever detect that you mentioned anything about this letter to anyone – the video will be immediately shared, and your contacts will be the first to receive it.
Following that, the video will be posted on the web!Remember! Time tracking will start as soon as you open this email, I am monitoring this!
Good luck and take it easy! It was just bad luck, next time please be careful.
What is Sextortion email scam
Sextortion is the practice of extorting money from victims by blackmailing them; threatening to reveal evidence of their sexual activity. It is an old scam scheme – which try to guilt people into paying off someone claiming to have secretly recorded video or compromising information. Scammers use a database of stolen email to send out scam emails to to millions of people around the World. The messages are sent to email addresses exposed in previous known data breaches in which the user database (email address and/or password) was indexed online.
Bottom of the scam email
Should you pay?
The best advice is: Don’t pay the ransom! If you receive the sextortion email scam, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
Threat Summary
| Name | As you can see, this is not a formal email SCAM |
| Type | Phishing, Bitcoin Email Scam, Fraud, Scam |
| Email subject line | Cooperation Offer |
| Ransom amount | $1650 |
| Bitcoin Address | 18GaQVHRKASCZu9B9oH1gnHENfSHL352G8, 1Cg1X5xS6wkLqPksNcsVzm41Mf24PsrE1 |
| Distribution method | spam email campaigns, WhatsApp |
| Removal | If you gets an email like As you can see, this is not a formal email, our computer security experts recommend follow some easy steps below |
What to do when you receive the As you can see, this is not a formal email SCAM
We advise anyone who has received this scam email:
- Do not panic.
- Do not pay a ransom.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the scam email to the FTC at https://www.ftc.gov/
- Scan your computer for malware.
- Install an anti-phishing software.
How to scan your PC for malware
If you suspect that your computer is infected with malicious software, we recommend scanning it for viruses. In addition to anti-virus software, we recommend using Zemana Anti Malware. It is a lightweight utility which designed to use alongside your antivirus software, detecting and removing malicious software, adware and PUPs that other security tools miss. Zemana Anti Malware is easy to use, fast, does not use many resources and have great detection and removal rates.
- Installing the Zemana is simple. First you’ll need to download Zemana on your device by clicking on the link below.
Zemana AntiMalware
165033 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
- Once you have downloaded the setup file, make sure to double click on the Zemana.AntiMalware.Setup. This would start the Zemana installation on your device.
- Select installation language and click ‘OK’ button.
- On the next screen ‘Setup Wizard’ simply click the ‘Next’ button and follow the prompts.

- Finally, once the installation is finished, Zemana will run automatically. Else, if doesn’t then double-click on the Zemana icon on your desktop.
- Now that you have successfully install Zemana AntiMalware, let’s see How to use this tool to detect and remove malware from your computer.
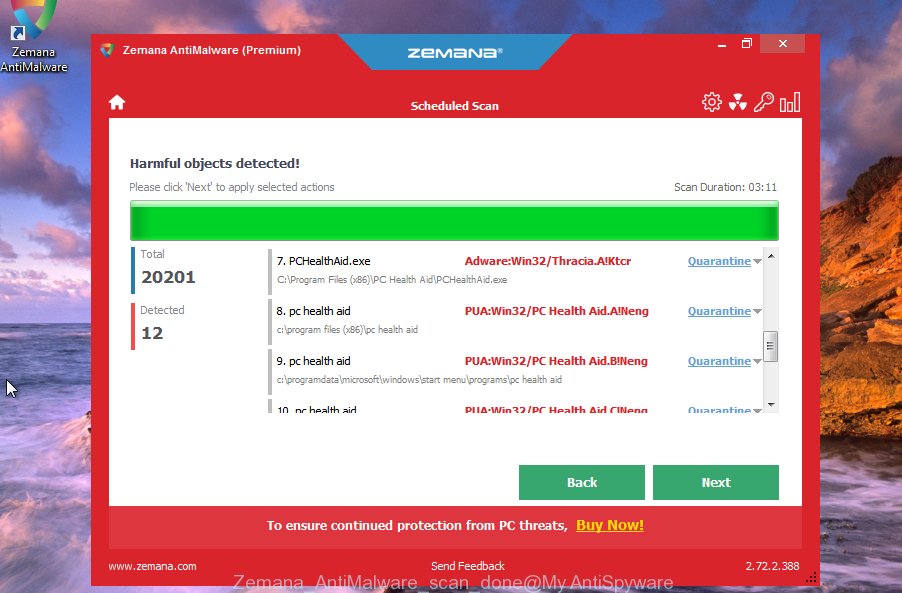
- After you have started the Zemana AntiMalware, you’ll see a window as shown on the image below, just click ‘Scan’ button to perform a system scan with this tool for malicious software.

- Now pay attention to the screen while Zemana scans your device.

- Once Zemana Anti Malware has finished scanning, it will display a list of all items found by the scan. Once you’ve selected what you wish to remove from your computer click ‘Next’ button.

- Zemana Anti Malware may require a reboot computer in order to complete the malware removal procedure.
- If you want to permanently remove malicious software from your PC, then click ‘Quarantine’ icon, select all malware, adware, PUPs and other items and click Delete.
- Reboot your personal computer to complete the malware removal process.
If you are having issues with malware removal, then check out MalwareBytes. We recommend this free malware removal utility because it may easily delete trojans, spyware, browser hijackers, adware, potentially unwanted software and toolbars with all their components such as files, folders and registry entries. Visit the page linked below to download the latest version of MalwareBytes Anti-Malware for Windows.
327261 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
We suggest you look at the following video, which completely explains the process of using the MalwareBytes Anti Malware to remove malicious software.
How to protect yourself from phishing, malicious and misleading websites
If you want to protect yourself from phishing websites, then install an ad blocker program such as AdGuard. It can block malicious and misleading web sites, stop unwanted advertisements and popups when using the Internet Explorer, Google Chrome, Firefox and Edge. So, if you like surf the Internet, and want to protect your computer from malicious web pages, then the AdGuard is your best choice.
Installing the AdGuard is simple. First you’ll need to download AdGuard by clicking on the link below.
26898 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as displayed below.
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick guide as displayed on the screen below.

Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick guidance which will assist you get to know AdGuard better.
Each time, when you start your system, AdGuard will start automatically and stop unwanted advertisements, block phishing, as well as other harmful or misleading websites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, which can be found on your desktop.
Finish words
We hope that this article helped you understand what the “As you can see, this is not a formal email” SCAM is and not succumb to the threats of scammers. If you receive an email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. It will help our team monitor the latest scams.