Michael Gillespie reports on his Twitter account: “STOP Djvu Ransomware with extension .werd spotted on ID Ransomware”. This means that a new version of STOP ransomware has appeared. It encrypts files, after which it changes their name, adding the .werd file extension at the end, thus marking all encrypted files.
Ransomware with extension ‘.werd’ spotted on ID Ransomware
This variant of STOP Djvu Ransomware is already 174 in its group and is very similar to previous variants, such as Nols, Leto, Bora and so on. Earlier, a free decryptor for past versions of STOP ransomware was created. It seems that in some cases, this decryptor will be able to decrypt .werd files that have been encrypted with this variant of STOP Djvu ransomware. There is also another way to restore the original state of encrypted files. Read more about how to remove the ransomware, how to decrypt or restore files below.
What is Werd ransomware
Werd is the latest version of STOP ransomware. And at the moment, it is not known about any major differences. Like other variants, it encrypts all the contents of a computer and requires a ransom for unlocking files. All files that have been encrypted receive a new .werd extension, by which they can be easily noticed. The ransomware masquerades itself as freeware, cracks, key generators and so on. Another distribution method is: When the ransomware is installed on a victim’s computer that is already infected with other malware or adware. When Werd ransomware is launched, it creates a folder in the Windows system directory where it places a copy of itself. Then it changes the system settings so that it starts up every time the computer is turned on or restarted. The ransomware tries to establish a connection with the control server to send information about the infected computer, as well as to receive commands or download additional malware.
After the initialization and the steps described above, the ransomware starts to perform its main task, it encrypts the files. To encrypt files, the ransomware looks for files in the directory. If the file has the extension: .sys, .bat, .dll, .lnk, .ini, or its name is ‘_readme.txt’, then the ransomware skips this file and does not encrypt it. In addition, the ransomware may not encrypt files in some system directories: %AppDataLocal%, %Application Data%, %Windows%, %Program Files%. All other contents of the victim’s computer will be encrypted.
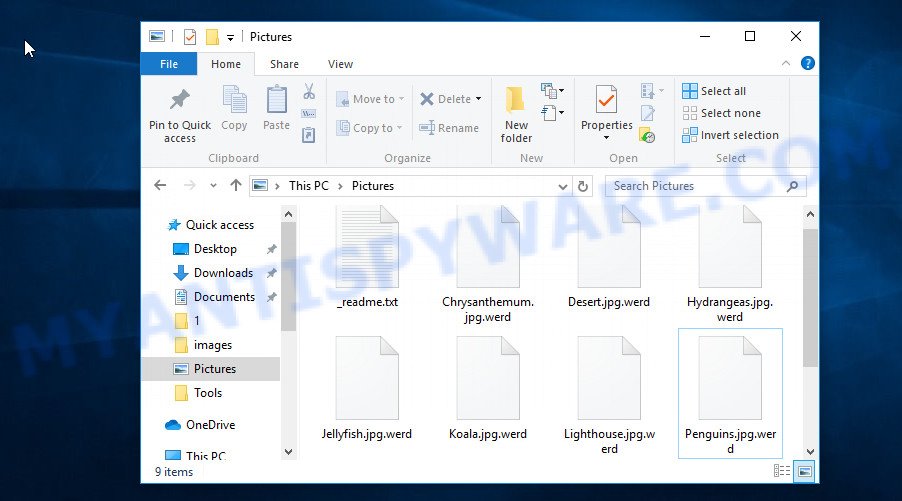
Files encrypted with ‘.werd’ extension
No files will be skipped. All documents, photos, archives located on local disks, system disks and connected network drives will be encrypted. The ransomware encrypts the contents of all disks file by file. Each file that has been encrypted is marked, the ransomware adds the extension ‘.werd’ to its name. That is, as soon as a document with the name ‘document.doc’ is encrypted, it will immediately be renamed to ‘document.doc.werd’. If you remove this extension, the file will remain locked. The associated program will not be able to read its contents. When all files are encrypted in a directory, the ransomware creates a new file in it named ‘_readme.txt’.
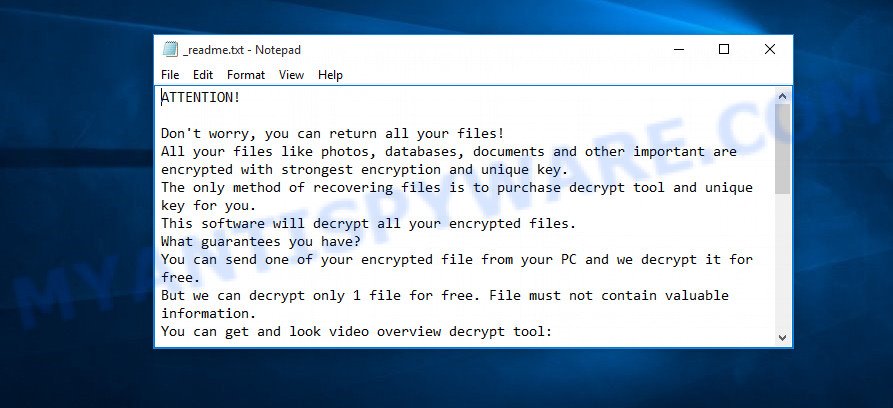
Werd ransom note
This file is a ransom demand message from Werd creators, it will be in all directories where there are encrypted files and its contents do not depend on which directory it is in. In this ransom note, attackers say that the victim’s files are encrypted and the only working way to decrypt them is to pay a ransom. They demand a ransom of $980, and in order to make the victim pay the ransom as soon as possible, they promise to reduce the ransom to $490 if it is paid within 72 hours. The victim must send them a Personal ID in order to get an address where to transfer the ransom. Typically, authors of ransomware use the anonymous Bitcoin wallet to receive a ransom.
Threat Summary
| Name | Werd |
| Type | Ransomware, Filecoder, Crypto malware, File locker, Crypto virus |
| Encrypted files extension | .werd |
| Ransom note | _readme.txt |
| Contact | gorentos@bitmessage.ch |
| Ransom amount | $980/$490 when paid within the first 72 hours |
| Detection Names | TrojanRansom.Win32/Stop, TrojanTR.Crypt, RansomWin32.STOP, W32/Kryptik |
| Symptoms | Files encrypted with ‘.werd’ file extension. You get an error message like ‘Windows can’t open this file’, ‘How do you want to open this file’. Your file directories contain a ‘ransom note’ file that is usually a _readme.txt file. |
| Distribution methods | Freeware, Malicious links in emails, Adware, Exploit kits, Cracks, Social media, Key generators, Malicious advertisements, Torrents. |
| Removal | To remove Werd ransomware use the removal guide |
| Decryption | To decrypt Werd ransomware use the steps |
Since this version of STOP Djvu Ransomware has just appeared, at the current moment, a free decryptor from Emsisoft cannot decrypt encrypted files. There are no other free decryptors. Therefore, the victims of this ransomware can only wait, hoping that the decryptor will be updated and the ability to decrypt .werd files will be added to it. If you do not want to wait (how long it is unknown, usually 1-2 weeks at least), then there is another way. This method involves the use of data recovery tools. You will find all information about this method below. You will also find out what free data recovery utilities are available that will help you restore some, or maybe all, encrypted files to their original state.
Quick links
- How to remove Werd ransomware
- How to decrypt .werd files
- How to restore .werd files
- How to protect your computer from Werd ransomware
How to remove Werd ransomware
The first thing to do before proceeding with the recovery or decryption of encrypted files is to scan the computer, find and remove Werd ransomware. You must be completely sure that all components, files and directories related to the ransomware are deleted. To do this manually is almost very difficult, but without special knowledge it is impossible. We recommend that every victim use a simple way – is to scan the computer with malware removal tools that are designed to find and remove ransomware and other malicious software. Some of the most popular free tools, both among specialists and ordinary users, can be found below. For each of the programs there is a small instruction with pictures.
Remove Werd ransomware with Zemana Anti-Malware
Zemana AntiMalware is a program that is designed to search for and remove various types of malware. It has the ability to quickly scan a computer, identify and remove ransomware, trojans, worms, adware, browser hijackers and other malicious software. More importantly, Zemana will allow you to remove the found malware for free. You do not have to install and buy a paid version.
- Visit the page linked below to download Zemana Anti-Malware. Save it directly to your Windows Desktop.
Zemana AntiMalware
165041 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
- When downloading is complete, close all programs and windows on your system. Open a file location. Double-click on the icon that’s named Zemana.AntiMalware.Setup.
- Further, click Next button and follow the prompts.
- Once installation is done, click the “Scan” button. Zemana AntiMalware application will scan through the whole machine for the Werd virus and other security threats. This task can take quite a while, so please be patient. While the Zemana Free program is checking, you can see count of objects it has identified as threat.
- When Zemana is finished scanning your system, it will display a screen that contains a list of malware that has been found. Review the scan results and then click “Next”. Once the task is complete, you can be prompted to reboot your machine.
Remove Werd ransomware virus with Hitman Pro
Another malware removal tool that allows you to find and remove Werd ransomware virus is Hitman Pro. It is a fantastic tool that is small in size and does not require installation on a computer. Hitman Pro has a powerful anti-virus engine and easily identifies and removes various malicious software, including ransomware, adware, worms, trojans, browser hijackers. Like Zemana, it will remove the found malware for free. Please go to the following link, then press the ‘Download’ button in order to download the latest version of HitmanPro.
After the downloading process is complete, open the file location and double-click the Hitman Pro icon. It will start the Hitman Pro utility. If the User Account Control prompt will ask you want to launch the program, press Yes button to continue.
Next, click “Next” . HitmanPro utility will begin scanning the whole personal computer to find out Werd ransomware. This procedure can take quite a while, so please be patient. While the tool is checking, you can see number of objects and files has already scanned.
Once the system scan is complete, HitmanPro will display a screen that contains a list of security threats that has been detected as shown in the following example.
All found items will be marked. You can delete them all by simply click “Next” button. It will open a dialog box, click the “Activate free license” button. After the cleaning process is finished, the tool may ask you to restart your personal computer.
Remove Werd virus with Kaspersky virus removal tool
If after using the previous utilities you still have doubts and you still think that there is a hidden ransomware on the computer, then we recommend that you check the computer with Kaspersky virus removal tool (KVRT). It is a completely free utility, which is based on the core from a well-known antivirus product created by Kaspersky Labs. KVRT can identify a wide range of security threats, find and remove all components of ransomware, trojans, worms, adware, browser hijackers and other malware. Download Kaspersky virus removal tool on your Desktop from the link below.
129295 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
When the downloading process is done, double-click on the KVRT icon. Once initialization process is finished, you’ll see the Kaspersky virus removal tool screen as shown below.
Click Change Parameters and set a check near all your drives. Press OK to close the Parameters window. Next click Start scan button. KVRT will scan through the whole PC system for Werd ransomware virus. A system scan may take anywhere from 5 to 30 minutes, depending on your system. While the Kaspersky virus removal tool tool is scanning, you can see count of objects it has identified as being infected by malicious software.
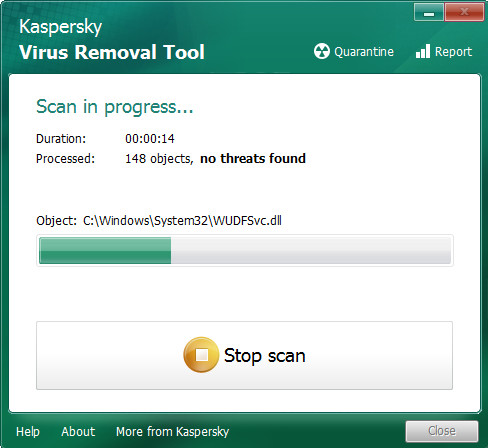
Once Kaspersky virus removal tool completes the scan, Kaspersky virus removal tool will display you the results as shown in the figure below.
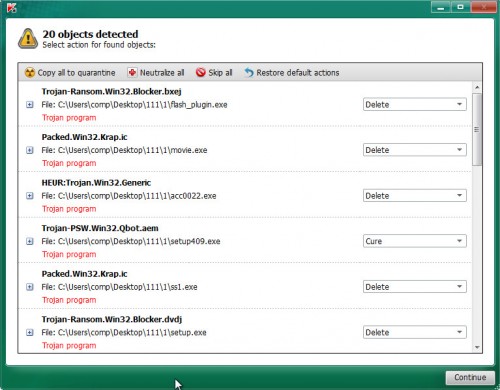
Review the scan results and then press on Continue to begin a cleaning task.
How to decrypt .werd files
As you already understood, it is impossible to decrypt .werd files simply by deleting their new extension. Unfortunately, at the time of this writing, there is no easy way to decrypt encrypted files. But based on the experience in decrypting files encrypted with previous versions of STOP Djvu Ransomware, we can assume that in the near future there will be a way to decrypt some, and possibly all, files. Also, there is always a chance to restore encrypted files to their original state using data recovery tools.
As we have said, in the near future it may be possible to decrypt files for free. Why you have to wait? The answer to this question lies in how the ransomware encrypts files. The researchers found that the ransomware can use two types of keys: an online key and an offline key. The first type of keys is used if the ransomware was able to connect to the control server. Files encrypted with this key cannot be decrypted. The ransomware uses the second type of keys if it could not connect to the server. What is very important, unlike an online key, the offline key is not unique; it is the same for different cases of ransomware infection. Therefore, as soon as researchers find this key, then all victims whose files were encrypted with an offline key will be able to decrypt files for free. Experience shows that usually an offline key is detected within a few weeks.
How to determine which key Werd used to encrypt your files. First of all, you can look at the Personal ID that is given in the ‘_readme.txt’ file (ransom note). Another way, look on disk ‘C’ for ‘SystemID\PersonalID.txt’ file. This is a file in which Werd ransomware stores the Personal IDs used for encryption.
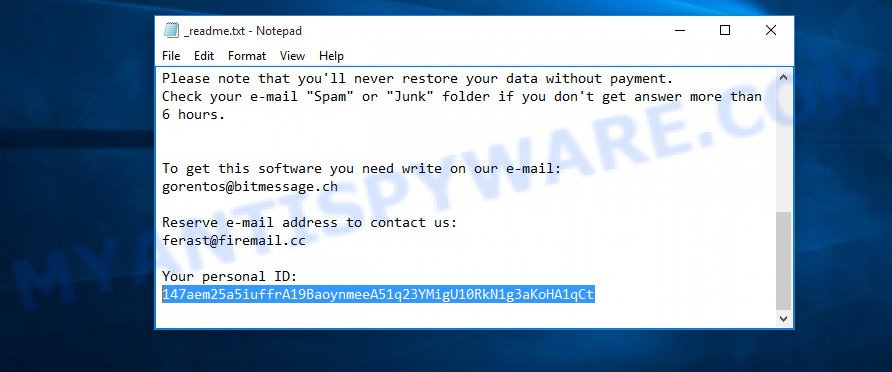
Personal ID is highlighted here
If there is an ID ending in ‘t1’, then you are lucky, your files are encrypted using an offline key, and when researchers find this key, you can decrypt your files. In this case, to decrypt the files, you need to use free STOP Djvu Decryptor from Emsisoft. If your Personal ID does not end with ‘t1’, then the ransomware used an online key. Even so, there is little chance of recovering encrypted files. This method will be discussed in the next part of the article.
How to restore .werd files
If your files are encrypted using an online key, or a free decryptor says that it cannot decrypt them, then you have one last chance – try to recover files using data recovery tools. Our experience shows that one or both of the methods listed below can restore encrypted files to their state in which they were before encryption. Therefore, be sure to try them. Both methods are easy to follow and do not require the installation of paid software. We suggest you use several free programs that have worked well. The only thing we want to repeat is that before you start restoring your data you need to be 100% sure that the ransomware is completely removed. Ransomware actions can disrupt the file recovery process, block it, or even cause the files to be permanently lost.
Use shadow copies to restore .werd files
In some cases, it is possible to restore files from their ‘shadow copies’. Shadow copies are copies of files that the Windows creates automatically when a user modifies or performs other actions with their files. Although the ransomware tries to remove them, sometimes this does not happen and all shadow copies remain intact. It gives just a fintastic result, allowing you to recover all encrypted files very quickly and simply. For easy access to all shadow copies, we suggest using a small and very handy tool called ShadowExplorer. Click the link below, then click the ‘Download’ button in order to download the latest version of Shadow Explorer.
439670 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
After the downloading process is complete, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as displayed in the following example.
Run the ShadowExplorer utility and then choose the disk (1) and the date (2) that you wish to recover the shadow copy of file(s) encrypted by the Werd ransomware as displayed in the following example.
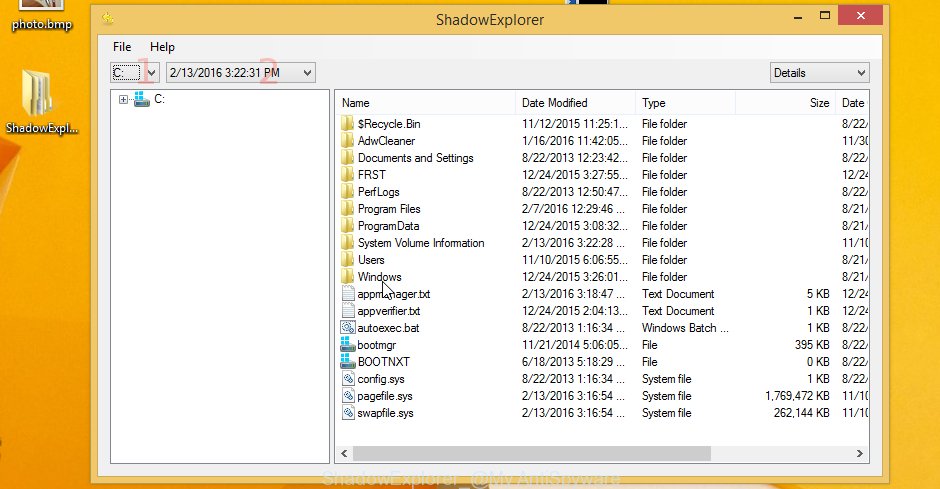
Now navigate to the file or folder that you wish to recover. When ready right-click on it and click ‘Export’ button as displayed on the image below.

Use PhotoRec to restore .werd files
There is another way to restore encrypted files to their original state. This method is slower and requires quite a lot of time. To use it, we recommend that you use a free utility called PhotoRec. It is a small free program that does not require installation on a computer. Photo Rec is designed to recover lost and deleted data. Why PhotoRec can help you recover encrypted files? The answer lies in how the Windows deletes files. When a user wants to delete a file, he simply presses one key. The system receives a signal that this or that file needs to be deleted. When the command to delete a file is completed, it does not mean that the file has disappeared, the Windows simply marks it as deleted and hides it from the user. This allows you to recover some, and sometimes even all encrypted files. Our advice is a must try. The only thing you need to consider is that the disk space where the files marked as deleted are located is considered empty. That is, the Windows OS can write new files there. That is, what we want to say, the more you used your computer after the moment of the ransomware attack, the less chance that you will be able to recover encrypted files.
Download PhotoRec on your MS Windows Desktop from the link below.
When the download is complete, open a directory in which you saved it. Right click to testdisk-7.0.win and choose Extract all. Follow the prompts. Next please open the testdisk-7.0 folder like the one below.

Double click on qphotorec_win to run PhotoRec for MS Windows. It’ll open a screen as on the image below.
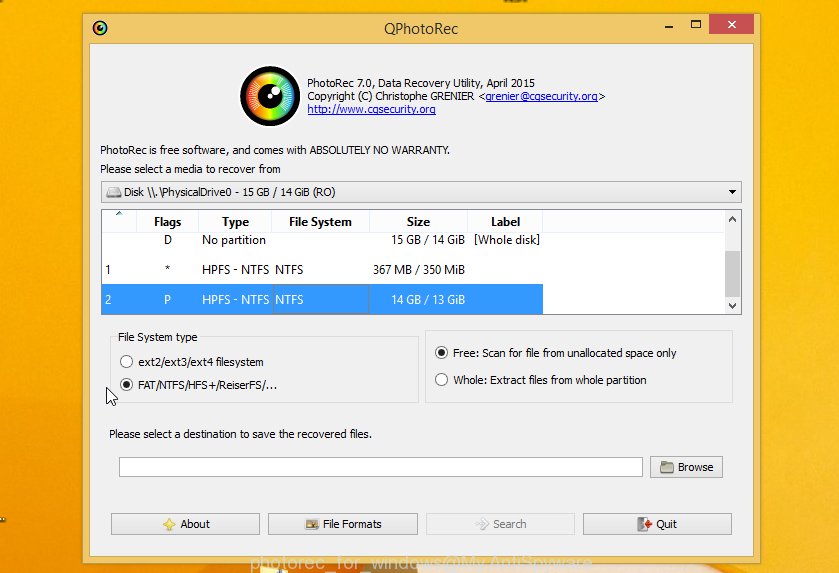
Select a drive to recover as displayed in the figure below.
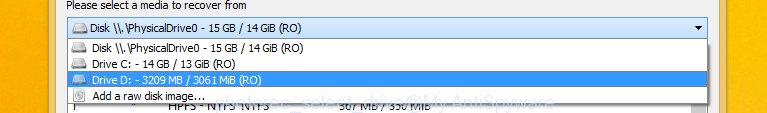
You will see a list of available partitions. Choose a partition that holds the encrypted files as displayed on the image below.
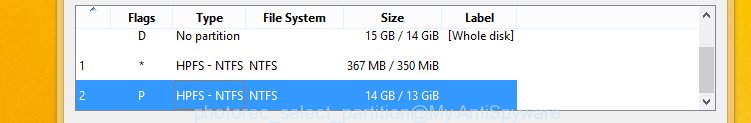
Press File Formats button and choose file types to recover. You can to enable or disable the recovery of certain file types. When this is finished, click OK button.
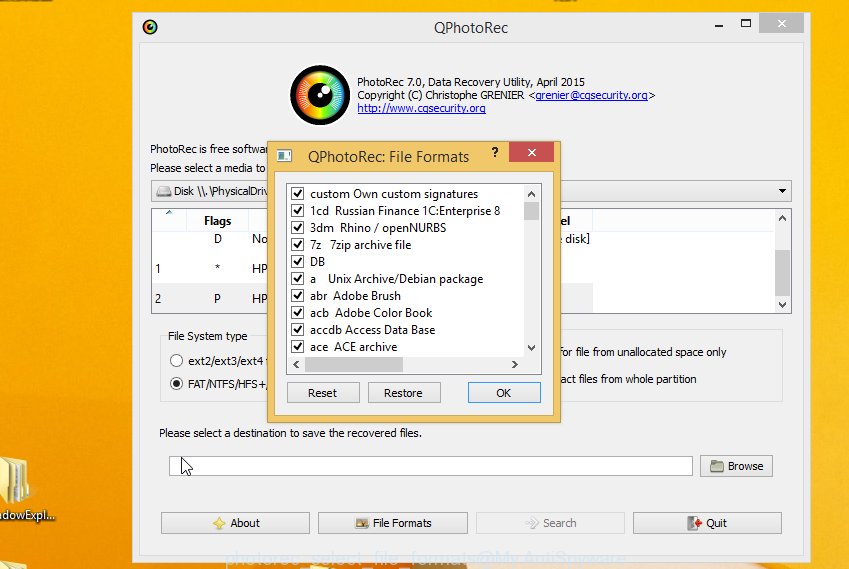
Next, press Browse button to choose where restored files should be written, then press Search.
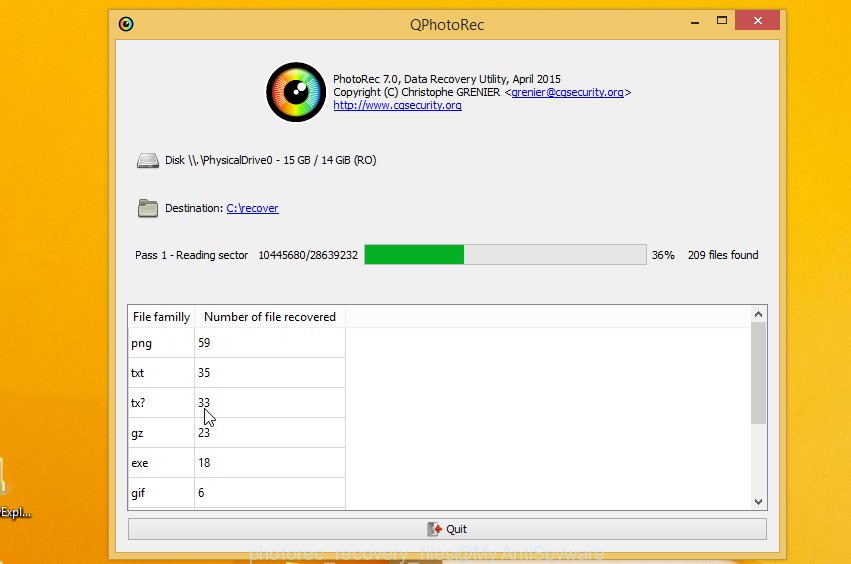
Count of restored files is updated in real time. All restored photos, documents and music are written in a folder that you have chosen on the previous step. You can to access the files even if the restore process is not finished.
When the recovery is complete, click on Quit button. Next, open the directory where recovered documents, photos and music are stored. You will see a contents as shown on the screen below.
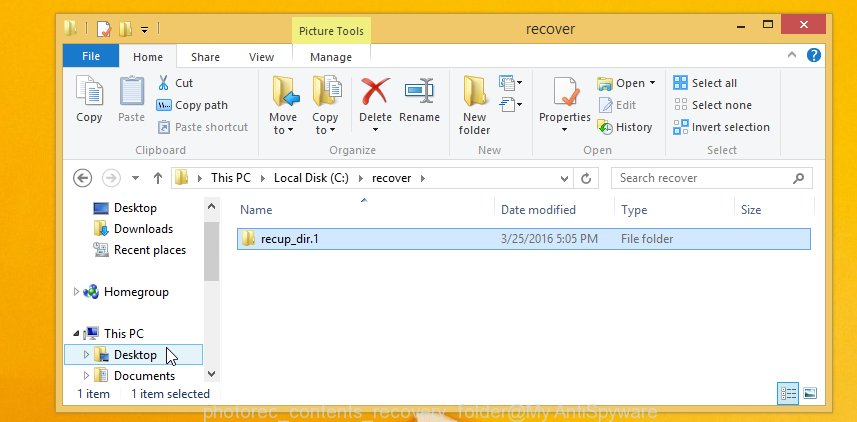
All restored documents, photos and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you’re searching for a specific file, then you can to sort your recovered files by extension and/or date/time.
How to protect your computer from Werd ransomware
Since the number of ransomware attacks is increasing every year, most anti-virus products have protection against ransomware. If your computer has become a victim of Werd virus, this means that your antivirus has poor protection against such attacks. Therefore, as an extra protection, we advise you to use HitmanPro.Alert. It is a small security utility. Hitman Pro Alert can check the system integrity and alerts you when critical system functions are affected by malware. HitmanPro.Alert can detect, remove, and reverse ransomware effects. Visit the following page to download HitmanPro Alert. Save it on your Desktop.
Once the download is finished, open the folder in which you saved it. You will see an icon like below.

Double click the HitmanPro Alert desktop icon. Once the tool is started, you will be displayed a window where you can select a level of protection, as displayed in the figure below.

Now click the Install button to activate the protection.
Finish words
We hope that this guide helped you understand what ransomware is and how to remove it. But most importantly, you were able to decrypt .werd files or restore them to their original state. If you have questions about using the programs proposed in this article, there are comments or questions then write to us. We advise you to follow us on Facebook or check this page from time to time. As new information appears, we will immediately inform you about it.