Computer security experts discovered a new variant of Bitcoin email scam that is titled This information concerns the security of your account. The bitcoin blackmail scam spreads via spam emails. The spam is sent out to thousands of emails at a time.
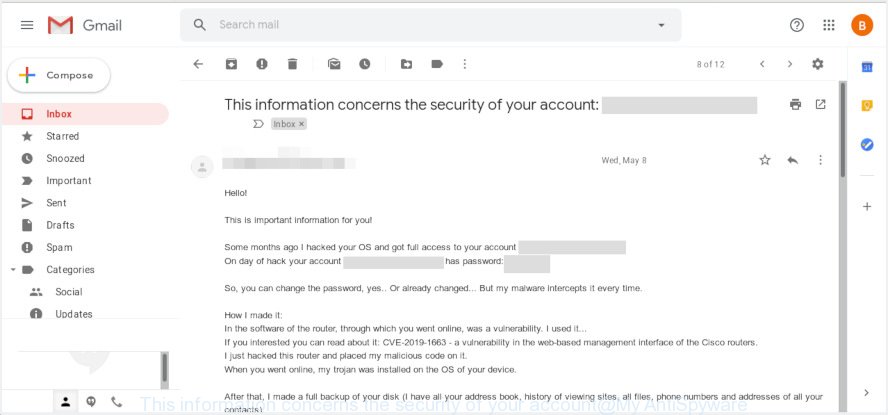
“This information concerns the security of your account” email scam
There are variations in the wording of the email body, but all of these messages are basically the same:
This information concerns the security of your account: *** Hello! This is important information for you! Some months ago I hacked your OS and got full access to your account *** On day of hack your account *** has password: *** So, you can change the password, yes.. Or already changed... But my malware intercepts it every time. How I made it: In the software of the router, through which you went online, was a vulnerability. I used it... If you interested you can read about it: CVE-2019-1663 - a vulnerability in the web-based management interface of the Cisco routers. I just hacked this router and placed my malicious code on it. When you went online, my trojan was installed on the OS of your device. After that, I made a full backup of your disk (I have all your address book, history of viewing sites, all files, phone numbers and addresses of all your contacts). A month ago, I wanted to lock your device and ask for a not big amount of btc to unlock. But I looked at the sites that you regularly visit, and I was shocked by what I saw!!! I'm talk you about sites for adults. I want to say - you are a BIG pervert. Your fantasy is shifted far away from the normal course! And I got an idea.... I made a screenshot of the adult sites where you have fun (do you understand what it is about, huh?). After that, I made a screenshot of your joys (using the camera of your device) and glued them together. Turned out amazing! You are so spectacular! I'm know that you would not like to show these screenshots to your friends, relatives or colleagues. I think $723 is a very, very small amount for my silence. Besides, I have been spying on you for so long, having spent a lot of time! Pay ONLY in Bitcoins! My BTC wallet: 1EnVwSYoCQ5hA6fqCxh56Dzqh17BydBnCy You do not know how to use bitcoins? Enter a query in any search engine: "how to replenish btc wallet". It's extremely easy For this payment I give you two days (48 hours). As soon as this letter is opened, the timer will work. After payment, my virus and dirty screenshots with your enjoys will be self-destruct automatically. If I do not receive from you the specified amount, then your device will be locked, and all your contacts will receive a screenshots with your "enjoys". I hope you understand your situation. - Do not try to find and destroy my virus! (All your data, files and screenshots is already uploaded to a remote server) - Do not try to contact me (you yourself will see that this is impossible, the sender address is automatically generated) - Various security services will not help you; formatting a disk or destroying a device will not help, since your data is already on a remote server. P.S. You are not my single victim. so, I guarantee you that I will not disturb you again after payment! This is the word of honor hacker I also ask you to regularly update your antiviruses in the future. This way you will no longer fall into a similar situation. Do not hold evil! I just good do my job. Good luck.
While terrifying at first, it is classic Bitcoin Blackmail Scam. Blackmail Email Scam is old extortion scheme – which try to guilt people into paying off someone claiming to have secretly recorded video or compromising information. Scammers uses the database of emails and stolen passwords to increase trust and sent this email scam out to millions of people around the World. The messages are sent to email addresses exposed in previous known data breaches in which the user database (email address and password) was indexed online.
Threat Summary
| Type | Bitcoin Blackmail Scam |
|---|---|
| Subject line | “This information concerns the security of your account”, “Important information about your account:” |
| Ransom amount | $723, $781 |
| BTC Wallet |
|
What to do when you receive the “This information concerns the security of your account” email scam
If you have received the email scam, just ignore the scammers’ empty threats. The best way to deal with the Bitcoin email scam is to mark the email as spam (JUNK) and move it to trash! After that, follow some easy steps listed below!
- Do not panic.
- Do not pay the ransom!!!
- Do not respond to the email spam.
- If the password emailed to you is one that you still use, then stop using it and change it right now!
- Avoid clicking links in email.
- Scan your computer for malware
- Install an anti-phishing software
- If you receive an email scam that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this blog post.
How to scan your your computer malware
There are not many good free anti malware applications with high detection ratio. The effectiveness of malicious software removal utilities depends on various factors, mostly on how often their virus/malware signatures DB are updated in order to effectively detect modern potentially unwanted programs, adware, hijacker infections and other malware. We suggest to run several programs, not just one. These programs that listed below will allow you delete all components of malware from your disk and Windows registry.
Zemana Anti Malware (ZAM) highly recommended, because it can locate security threats such adware and malicious software that most ‘classic’ antivirus programs fail to pick up on. Moreover, if you have any malware removal problems which cannot be fixed by this utility automatically, then Zemana AntiMalware (ZAM) provides 24X7 online assistance from the highly experienced support staff.
Zemana Free can be downloaded from the following link. Save it directly to your MS Windows Desktop.
165075 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
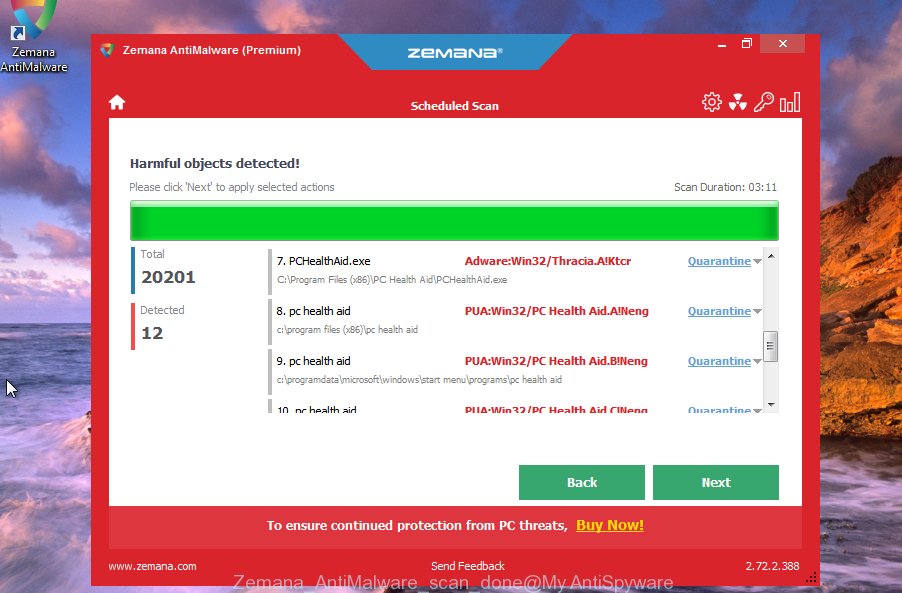
Once the download is finished, launch it and follow the prompts. Once installed, the Zemana Anti-Malware (ZAM) will try to update itself and when this task is complete, click the “Scan” button . Zemana Anti Malware (ZAM) program will scan through the whole computer for malicious software.

Depending on your computer, the scan can take anywhere from a few minutes to close to an hour. While the Zemana AntiMalware (ZAM) utility is checking, you can see how many objects it has identified as being affected by malware. All found items will be marked. You can remove them all by simply press “Next” button.
If malware problem persists, use the HitmanPro and scan if your machine is hijacked by malicious software. The HitmanPro is a downloadable security utility that provides on-demand scanning and allows get rid of adware, potentially unwanted apps, and other malicious software. It works with your existing antivirus software.
Installing the HitmanPro is simple. First you’ll need to download HitmanPro by clicking on the link below. Save it to your Desktop.
Download and use Hitman Pro on your machine. Once started, click “Next” button to detect malware. A scan can take anywhere from 10 to 30 minutes, depending on the number of files on your computer and the speed of your personal computer. When a malware, adware or potentially unwanted applications are detected, the number of the security threats will change accordingly. .
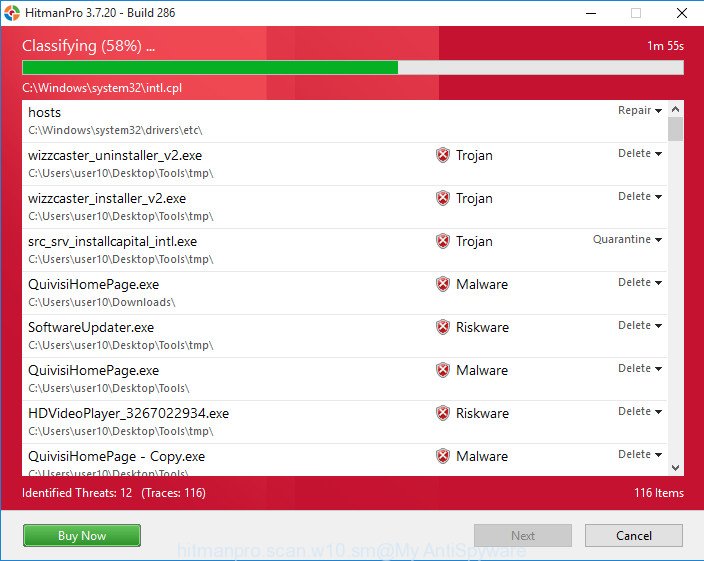
After HitmanPro has completed scanning your computer, a list of all threats found is prepared.
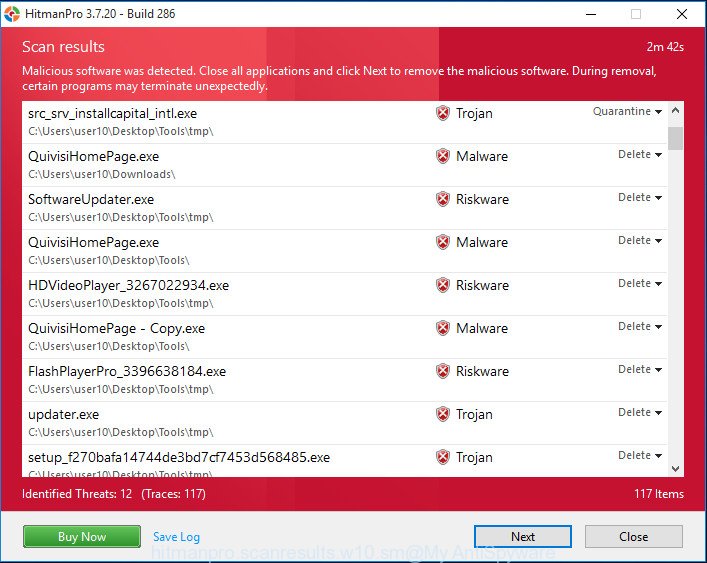
Review the scan results and then click Next button.
It will display a dialog box, click the “Activate free license” button to begin the free 30 days trial to remove all malicious software found.
How to protect yourself from phishing websites
In order to increase your security and protect your personal computer against new phishing websites, you need to use ad-blocker program that blocks an access to harmful advertisements and misleading web-pages. Moreover, the application can block the open of intrusive advertising, which also leads to faster loading of web-pages and reduce the consumption of web traffic.
Download AdGuard by clicking on the following link. Save it to your Desktop so that you can access the file easily.
26905 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
When downloading is finished, start the downloaded file. You will see the “Setup Wizard” screen as on the image below.
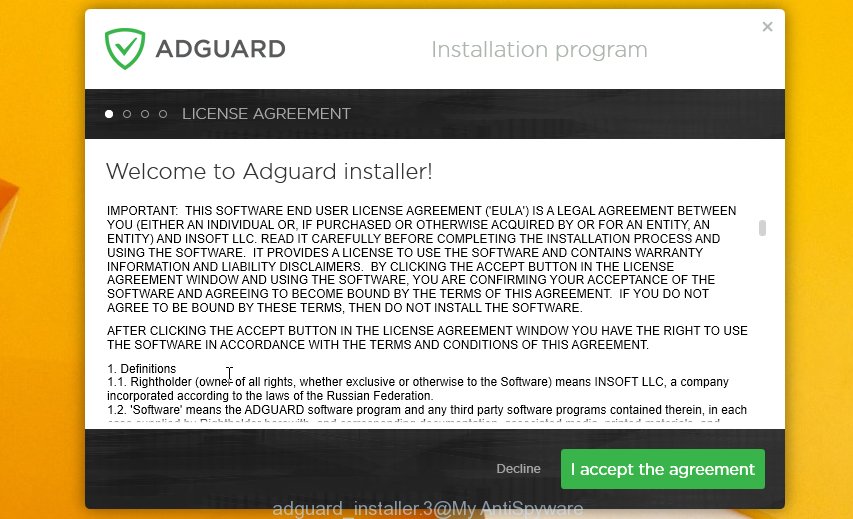
Follow the prompts. After the install is finished, you will see a window as displayed in the figure below.

You can press “Skip” to close the installation program and use the default settings, or click “Get Started” button to see an quick tutorial which will allow you get to know AdGuard better.
In most cases, the default settings are enough and you don’t need to change anything. Each time, when you start your personal computer, AdGuard will start automatically and stop unwanted advertisements, block phishing, malicious or misleading webpages. For an overview of all the features of the program, or to change its settings you can simply double-click on the AdGuard icon, that may be found on your desktop.