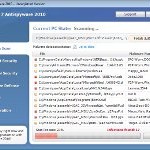
 Win 7 Security 2011 is a rogue antispyware program, clone of Win 7 Anti-Virus 2011. The program reports false infections, displays numerous fake security alerts and blocks legitimate Windows applications from running in order to trick you into purchasing its full version. So, do not trust anything that this malware will display you and remove Win 7 Security 2011 from your system as soon as possible. Read below what you’ll want to know though is what does this malware do and how to remove the rogue from your computer for free.
Win 7 Security 2011 is a rogue antispyware program, clone of Win 7 Anti-Virus 2011. The program reports false infections, displays numerous fake security alerts and blocks legitimate Windows applications from running in order to trick you into purchasing its full version. So, do not trust anything that this malware will display you and remove Win 7 Security 2011 from your system as soon as possible. Read below what you’ll want to know though is what does this malware do and how to remove the rogue from your computer for free.
Like other rogues, Win 7 Security 2011 is installed via trojans without your permission and knowledge. Immediately after launch, it will register itself in the Windows registry to run automatically every time when you start an application (files with “exe” extension). The rogue also uses this method of running to block the ability to run any programs, including legitimate antivirus and antispyware applications.
Once running, Win 7 Security 2011 will perform a system scan and detect a lot of infections. Then it will ask you to pay for a full version of the program to remove these infections. Of course, all of these infections are a fake. This malware want to scare you into thinking that your computer is infected with malicious software. Thus do not trust the scan results, simply ignore them!
While Win 7 Security 2011 is running, it will display numerous fake security alerts. Some of the alerts are:
System danger!
Your system is in danger. Privacy threats detected.
Spyware, keyloggers or Trojans may be working in the
background right now. Perform an in-depth scan and removal
now, click here.
Attention: DANGER!
ALERT! System scan for spyware, adware, trojans and viruses is complete.
Win 7 Security 2011 detected 35 critical system objects.
Last but not least, Win 7 Security 2011 will hijack Internet Explorer and Firefox, so it will display a fake warning page instead a site that you want to visit. The fake warning is:
Win 7 Security 2011 ALERT
Internet Explorer alert. Visiting this site may pose a security threat to your system
Of course, all of these messages, warnings and alerts are a fake and supposed to scare you into thinking your computer in danger! Just like false scan results, ignore all of them!
As you can see, Win 7 Security is a scam which created with one purpose to scare you into thinking that your computer in danger as method to trick you into purchasing the full version of the program. If your computer is infected with this malware, then most importantly, do not purchase it! Uninstall the rogue from your PC as soon as possible. Use the removal guide below to remove Win 7 Security 2011 and any associated malware from your computer for free.
Use the following instructions to remove Win 7 Security 2011 (Uninstall instructions)
Step 1. Repair “running of .exe files”.
Method 1
Click Start. Type in Search field command and press Enter. It will open the command prompt. Type into it notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\pezfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
Save this as fix.reg to your Desktop (remember to select Save as file type: All files in Notepad.)
Double Click fix.reg and click YES for confirm.
Reboot your computer.
Method 2
Click Start. Type in Search field command and press Enter. It will open the command prompt. Type into it notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
[Version]
Signature="$Chicago$"
Provider=www.myantispyware.com
[DefaultInstall]
DelReg=regsec
AddReg=regsec1
[regsec]
HKCU, Software\Classes\.exe
HKCU, Software\Classes\pezfile
HKCR, .exe\shell\open\command
[regsec1]
HKCR, exefile\shell\open\command,,,"""%1"" %*"
HKCR, .exe,,,"exefile"
HKCR, .exe,"Content Type",,"application/x-msdownload"
Save this as fix.inf to your Desktop (remember to select Save as file type: All files in Notepad.)
Right click to fix.inf and select Install. Reboot your computer.
Note: if Windows returns error message “Installation failed”, then you need disable UAC control. Click Start, Control Panel, User accounting, Click “Turn User Account Control on or off”. Uncheck “Use User Account Control (UAC)” and click OK. Now try install fix.inf once again.
Step 2. Remove Win 7 Security 2011 associated malware.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
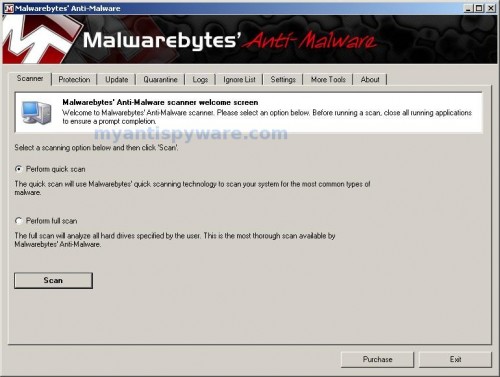
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for Win 7 Security 2011 associated malware. This procedure can take some time, so please be patient.
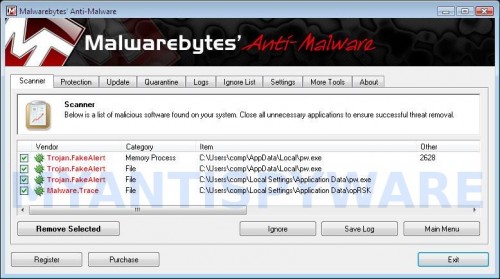
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove Win 7 Security 2011. MalwareBytes Anti-malware will now remove all of associated Win 7 Security 2011 files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Win 7 Security 2011 creates the following files and folders
%AppData%\[RANDOM].exe
Win 7 Security 2011 creates the following registry keys and values
HKEY_CURRENT_USER\Software\Classes\.exe
HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\.exe\shell
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start\command
HKEY_CURRENT_USER\Software\Classes\pezfile
HKEY_CURRENT_USER\Software\Classes\pezfile\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\pezfile\shell
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\runas
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\start
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\start\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | @ = “”%AppData%\hee.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | IsolatedCommand = “”%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe | @ = “pezfile”
HKEY_CURRENT_USER\Software\Classes\.exe | Content Type = “application/x-msdownload”
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command | @ = “”%AppData%\hee.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\pezfile\shell\open\command | IsolatedCommand = “”%1″ %*”










i guarantee this software the anti-malware it is reliable fast and can delete all abnormalities.. just follow the instruction written up
This virus was running local to a user profile on Win7. Logging in as an administrator and running MalwareBytes got rid of several viruses, running our company’s TrendMicro caught a few more. Once you log back in to the user’s profile, the virus reincarnates.
After doing this several more times, and several more AV programs later, I finally found and deleted two [random 3 letters].exe files in the user’s AppData directory (via the administrative login). Logging into the user account again, the virus popup stopped, but still needed to manually restore ‘.exe’ execution using method 1 above.
I have a virus protector on my computer that is active. Can you explain why it did not capture this before it locked me off the internet?
I followed these instructions and the virus was removed by McAfee after the restart before I could even download malwarebytes. However now I can’t even open IE, firefox or any other programs including task manager. Is there anything I can do to fix this other than restoring it?
Chris 2, when you tried to run these apps what was displayed ?
Thank you so much. Your directions worked marvellously on my PC, although I went with a different Spyware programme (SuperAntiSpyware) and it didn’t find the malware.
One question though: I now have the fixreg file sitting on my desktop. Can I remove it? If so, where do I put it or do I simply scrap it altogether?
Beverly, yes of course you can remove the fix.reg file.
I have the same problem as Chris 2. Any desktop icon I click it brings up the \Open with\ box. All my system restore dates have gone too. Any suggestions?
If anyone is still having the same problem as Chris 2 I may have a solution. My father had the same problem and we finally found that the registry hacker was still active. It has a way of hiding normally so what you will have to do is either run a program called rkill (free program that stops know virus and malware processes) or reboot in safe mode (no networking) and run the Malwarebytes. It should find something still hidden in the system.
Thank you so much for this! I seemed to have picked up Vista 2012 Antivirus, and Method 1 worked in removing the virus. Luckily, I caught it before it locked me out of the Internet.
I only did Method 1, as it seemed to do the trick, and as a rule for using my dad’s computer, I can’t download anything.
6 days after I got rid of it, a generic pop-up comes up, saying something along the lines of “User Account Control” comes up. I X it out, and it pops up less than a second later. I clicked Continue and turned off my comp. No signs of the virus reoccured, but only the volume is in my toolbar is volume. I haven’t run a scan yet. The Internet isn’t slow or acting strange, and ever since the pop-up showed up, things have been normal, except the toolbar.
Should I be worried about this and download Malwarebytes, or should I disregard it?
Also, if You suggest that I download Malwarebytes, can I uninstall it after I get rid of the remains of the virus?