Smss32.exe, winlogon32.exe, helper32.dll are components of trojan FakeAlert. Once installed, the trojan will configure itself to run automatically when Windows starts. When the trojan is started, it will display a screen that stats that Worm.Win32.Netsky detected on your computer as an attempt to make you think your computer in danger. The alert is fake and you can safety ignore it.
What is more, the “smss32.exe, winlogon32.exe, helper32.dll” trojan may display a lot of popups, disable Windows Task Manager, change a desktop background, block the ability to run any applications including antivirus and antispyware programs. The trojan will also download and install Internet Security 2010 onto computer automatically without your permission. Internet Security 2010 is a rogue antispyware program, that reports false infections and shows fake security alerts as method to to trick you into purchase so-called “full” version of the software.
Use the removal guide below to remove smss32.exe, winlogon32.exe, helper32.dll and any associated malware from your computer for free.
Symptoms in a HijackThis Log
F2 – REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon32.exe
O4 – HKLM\..\Run: [smss32.exe] C:\WINDOWS\system32\smss32.exe
O10 – Unknown file in Winsock LSP: c:\windows\system32\helper32.dll
O10 – Unknown file in Winsock LSP: c:\windows\system32\helper32.dll
Use the following instructions to remove remove smss32.exe, winlogon32.exe, helper32.dll (Remove Worm.Win32.Netsky Spyware Alert)
Step 1.
Download HijackThis from here and save it to your Desktop.
If you cannot run HijackThis, then re-download it, but before saving HijackThis.exe, rename it first to explorer.exe and click Save button to save it to desktop.
Run HijackThis. Click “Do a system scan only” button. Now select the following entries by placing a tick in the left hand check box, if present:
F2 – REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon32.exe
O4 – HKLM\..\Run: [smss32.exe] C:\WINDOWS\system32\smss32.exe
Place a checkmark against each of them. Once you have selected all entries, close all running programs then click once on the “fix checked” button. Close HijackThis.
Step 2.
Download LSPFix from here and unzip it to your Desktop.
Run LSPFix. Place a tick in the “I know what i`m doing”.
In the KEEP box select helper32.dll and press “>>” button.
Press Finish>> button. When LSPFix is done removing the LSP you will see a summary box. Press OK.
Step 3.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
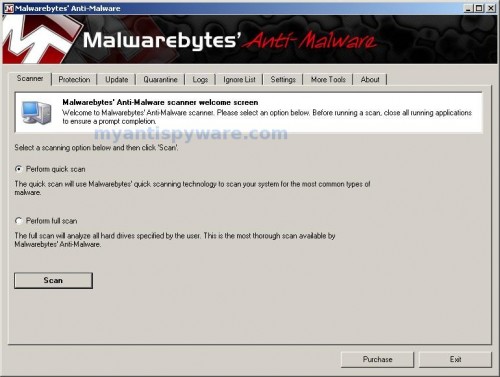
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for remove smss32.exe, winlogon32.exe, helper32.dll. This procedure can take some time, so please be patient.
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
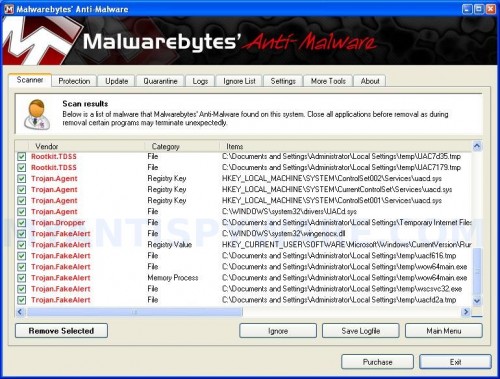
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove THREATNAME. MalwareBytes Anti-malware will now remove all of associated remove smss32.exe, winlogon32.exe, helper32.dll files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Smss32.exe, winlogon32.exe, helper32.dll creates the following files and folders
C:\WINDOWS\system32\helper32.dll
C:\WINDOWS\system32\smss32.exe
C:\WINDOWS\system32\winlogon32.exe
C:\WINDOWS\system32\41.exe
C:\WINDOWS\system32\warning.html
Smss32.exe, winlogon32.exe, helper32.dll creates the following registry keys and values
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\ActiveDesktop | NoChangingWallpaper = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer | NoSetActiveDesktop = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\policies\Explorer | NoActiveDesktopChanges = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run | smss32.exe = “C:\WINDOWS\system32\smss32.exe”
HKEY_CURRENT_USER\Software | 8636065b-fef0-4255-b14f-54639f7900a4 = “8636065b-fef0-4255-b14f-54639f7900a4”
HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Desktop\General | Wallpaper = “C:\WINDOWS\system32\warning.html”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer | NoSetActiveDesktop = 1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer | NoActiveDesktopChanges = 1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\ActiveDesktop | NoChangingWallpaper = 1
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Policies\System | DisableTaskMgr = 1
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon | Userinit = “C:\WINDOWS\system32\winlogon32.exe”










Now Malwarebytes is up to 58!!!
My task manager is disabled, my regedit is disabled, what’s coming up now? I have to restart now.
I’m STUNNED, AMAZED etc… I have never had a virus before. NOW PLEASE TELL ME WHERE THE HECK THIS THING CAME FROM!!!!!!!!!!!!!!! I would like to see what caused it, and uninstall the program or change the web browser or WHATEVER! Thank you so much!!!!!! I didn’t have helper32 or the desktop background change, nor did i have the gone taskbar and icons. Thank you Thank you Thank you!!!!!! NOW I HAVE MY TASK MANAGER BACK, MY REGEDIT BACK, AND neither did I have the startup reboot loop.!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!! Thank You SO MUCH
THANK YOU VERY MUCH!!!
can I uninstall hijectthis and Malwarebytes after I have removed my virus?
Kris, yes of course.
Worked like a charm! Thank you!
Works like a dream the very first time…
I actually followed this to fix my mom’s pc via a remote control server. Just goes to show, it works, nice and easy to follow.
Great!
Thanks for safing a lot of my time .-)
tnx patrik! =)
Well, it worked, but now my SYSTEM RESTORE is “turned off”. I tried turning it on in the following ways:
1.) Right Click My Computer, Go to System, System Restore Tab ,BUT THE TAB IS NOT THERE!
2.) Opened System Restore by Start Menu> All Programs> Accessories> System Tools> System Restore.
It says the Following:
“System Restore has been turned off by group policy. To turn on System Restore, contact your domain Administrator.”.
3.) Hacked Registry to try and unlock it. NOPE-DIDN’T WORK!
A LITTLE HELP?
I do not know of any other way to turn it on- I shouldn’t have to, anyways!
I do not know what to do now. Like I was saying:
A LITTLE HELP?
I have winXP by the way. Planning on upgrading to 7 soon, but I still want SysRestore incase something goes bad.
I DO NOT WANT THIRD PARTY SOFTWARE THOUGH!!!
Hello. I am having trouble running HijackThis. I have downloaded it and renamed it multiple times as explorer.exe however I get an error message which states it “is not a valid Win32 application.”
Thank you! I got hit by this and following your instructions, the whole thing was cleared up in no time. I second ‘ComputerPro101’: I got this thing while browsing – most likely and infected Blog. Any hints on how it was injected into my computer? I suspect something like an infected Flash or other such.
ComputerPro101, you have tried:
1. remove DisableConfig and DisableSR values from “HKEY_LOCAL_MACHINE \ Software \ Policies \ Microsoft \ Windows NT \ SystemRestore” key of Windows registry
2. click Start, Run, type gpedit.msc and press Enter. Navigate to Computer Configuration-> Administrative Templates-> System-> System Restore and set “Turn off System Restore” to “Not Configured” and “Turn off Configuration” to “Not Configured”
matt, try re-download this file or use another computer.
Thankyou so much, you saved me alot of time and effort with this.
Excellent article! Exactly, what I was looking for. You save me a lot of time. My computer was clean in 20 minutes, following the steps above.
Many many thanks and good luck!
Forgot to tell you…
My Windows XP Pro SP3 was snowing blue screen before logon dialog with the following error:
windows logon process system process terminated unexpectedly with a status of 0xc0000005
After the repear of the OS, I understood, that it was infected.
thank you for your help so far… we’ve run through all these steps but now every time we get into the desktop on windows it says that our active desktop has changed and there’s a big white screen with an exclamation mark. Also, we get a pop up that says “your system has recovered from a serious error”- no kidding! Anyways, we can’t get this pop up to go away and when we try to change the desktop the computer shuts off and restarts, same when we get on again and try to run Malwarebytes again… basically after 5 minutes it reboots itself. We started it up in safe mode this time and went looking for the files you mentioned above to Blair and they are gone so that’s good. We ran Malwarebytes againin SafeMode this time. It found 2 more issues and we removed them. Then we rebooted the computer again and went in normally… again we got about a dozen “your system has recovered from a serious error” send this report to Microsoft. I said yes to one of them and no to the rest. Then I was able to change the background and actually get the internet back up and running. But everything is really, really slow… any suggestions for getting things back to their regular speed??
BTW- we picked up this virus on perezhilton.com so watch out for his site right now!
thanks a lot
this post really help
i got these virus but i try to do other way
the result is i cant login to windows
so i try to fix my registry by Hiren boot CD
after i can login ti windows then I use all anti virus as in this page and it work perfectly.
it really save all my work in Harddisk
many many thanks
Well I’ll be damned, it worked! Or at least it appears to have worked after five minutes after restarting my computer.
Was cleaning a friends computer of this before I came on your page, I cleaned everything out succesfully. I installed an anti virus program on his computer and it picked up the helper32 and removed it. Now the computer can’t connect to the internet, explorer just crashes and firefox forever stays at untitled.
Any advice on how to fix this?
Wish I came across this page before I started cleaning his comp >_< woulda saved me a few headaches.
Sim, use the step 2 above.
I want to thank the autors of this extremely useful post. I followed the virus removal instructions and everything went very smoothly (I was not able to login and I had to use first the Recovery Console).
Thank you very much!
Has anyone gone through these steps and gotten a 0 problem malware report and then in a few days found the Userinit registry key to have returned to c:\windows system32\winlogon32.exe? I have done these steps 3 times now and still get this registry key change. I will copy userinit.exe to winlogon32.exe but expect that Symantec corporate will delete the file. I fear that there must be something still lurking on the machine. Has any one experienced this and successfully repaired without a wipe and reload?
Mike, open a new topic in our Spyware removal forum. I will check your computer.
Thanks much. Instructions were very easy to follow, infection on my daughter’s PC was removed/quarantined, and it now appears that all is ok. Entire process took less than one hour (although researching for a solution and deciding to go with your approach took several hours)!!
Many thanks from France !!
Thanx for posting this, helped me a lot! I successfully removed all files from a friends computer and got rid of the messages, however the network still seems to be blocked now.
Can’t run ‘InternetOptions’ or IE. Firefox doesn’t load any pages, skype/MSN/updates for antivirus programm can’t access the internet.
A ping works, so DNS is not the problem. Did not apply the LSPfix yet, will do it tonight to see if helper32.dll is still in there.
I’ll try also to check proxy-server settings via registry then, maybe that’s the problem?
When LSPfix doesn’t show helper32.dll, would running ‘WinsockXPfix’ maybe help?
Any other ideas?
jaydee, you have tried run Malwarebytes ?