 Data Recoveryis a fake computer optimization software that detects numerous false problems and displays various critical errors alerts on the computer. The rogue program from same malware family as Master Utilities, PC Repair, System Repair, Windows XP Repair, Windows XP Fix, etc. It is promoted and installed itself on your computer without your permission and knowledge through the use of trojans or other malicious software. Moreover, the scammers may also distribute Data Recovery on Twitter, My Space, Facebook, and other social networks. Please be careful when opening attachments and downloading files or otherwise you can end up with a rogue program on your PC.
Data Recoveryis a fake computer optimization software that detects numerous false problems and displays various critical errors alerts on the computer. The rogue program from same malware family as Master Utilities, PC Repair, System Repair, Windows XP Repair, Windows XP Fix, etc. It is promoted and installed itself on your computer without your permission and knowledge through the use of trojans or other malicious software. Moreover, the scammers may also distribute Data Recovery on Twitter, My Space, Facebook, and other social networks. Please be careful when opening attachments and downloading files or otherwise you can end up with a rogue program on your PC.
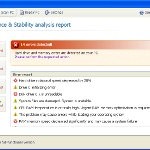
When Data Recovery is installed, it will state that your computer has some critical problems. It will imitate a scan computer`s hard disks, Windows registry and computer memory for errors. The rogue will report that “Read time of hard drive clusters less than 500 ms”, “32% of HDD space is unreadable”, “Bad sectors on hard drive or damaged file allocation table”, etc. Next, Data Recovery will prompt you to purchase a full version of the program to fix supposedly found system errors. Of course, all of these errors are a fake. Most important, don`t pay for the bogus program and just ignore the false scan results.
Data Recovery will block legitimate Windows applcations on your computer and won’t let you download anything from the Internet. Last, but not least, the rogue will display numerous fake warnings and nag screens. Some of the warnings are:
The system has detected a problem with one or more installed IDE / SATA hard disks.
It is recommended that you restart the system.
Critical error
Windows can`t find disk space. Hard drive error.
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
Windows – No Disk
Exception Processing Message 0×0000013
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
Of course, all of these warnings are a fake. This is an attempt to make you think your computer in danger. Like false scan results you can safely ignore them.
As you can see, obviously, Data Recovery is a scam, which created with only one purpose – to steal your money. Most important, don`t purchase the program! You need as quickly as possible to remove the malicious software. Follow the removal instructions below, which will remove Data Recovery and any other infections you may have on your computer for free.
Use the following instructions to remove Data Recovery infection
Click Start, Type in Search field %allusersprofile% and press Enter (if you use the Windows XP, then click Start, Run and type a command in Open field). It will open a contents of “ProgramData” folder (“All Users” folder for Windows XP).
Data Recovery hides all files and folders, so you need to change some settings and thus be able to see your files and folders again. Click Organize, select ”Folder and search options”, open View tab (if you use Windows XP, then open Tools menu, Folder Options, View tab). Select “Show hidden files and folders” option, uncheck “Hide extensions for known file types”, uncheck “Hide protected operating files” and click OK button.
Open “Application Data” folder. This step only for Windows XP, skip it if you use Windows Vista or Windows 7.
Now you will see Data Recovery associated files as shown below.
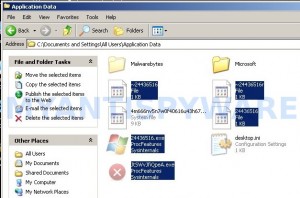
Basically, there will be files named with a series of numbers or letter (e.g. 2636237623.exe or JtwSgJHkjkj.exe), right click to it and select Rename (don`t rename any folders). Type any new name (123.exe) and press Enter.
![]() You can to rename only files with .exe extension. Its enough to stop this malware from autorunning.
You can to rename only files with .exe extension. Its enough to stop this malware from autorunning.
Reboot your computer.
Now you can unhide all files and folders that has been hidden by Data Recovery. Click Start, type in Search field cmd and press Enter. Command console “black window” opens. Type cd \ and press Enter. Type attrib -h /s /d and press Enter. Close Command console.
If your Desktop is empty, then click Start, type in Search field %UserProfile%\desktop and press Enter. It will open a contents of your desktop.
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
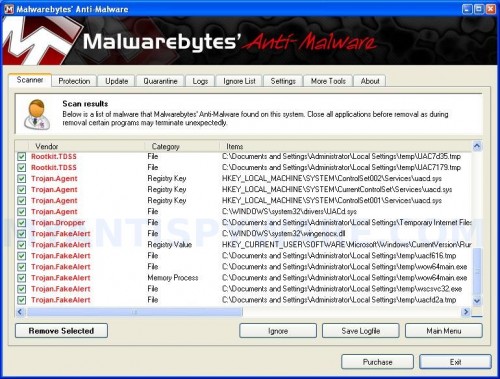
Malwarebytes Anti-malware, list of infected items
Make sure that everything is checked, and click Remove Selected for start Data Recovery removal process. When disinfection is completed, a log will open in Notepad. Reboot your computer.
Data Recovery may be bundled with TDSS trojan-rootkit, so you should run TDSSKiller to detect and remove this infection.
Download TDSSKiller from here and unzip to your desktop. Open TDSSKiller folder. Right click to tdsskiller and select rename. Type a new name (123myapp, for example). Press Enter. Double click the TDSSKiller icon. You will see a screen similar to the one below.
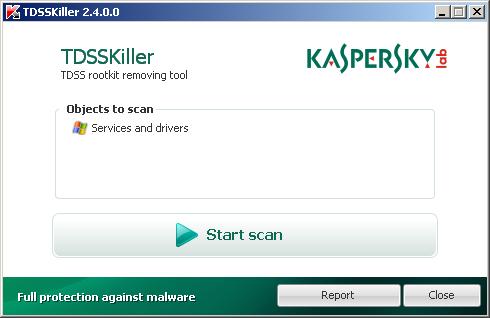
TDSSKiller
Click Start Scan button to start scanning Windows registry for TDSS trojan. If it is found, then you will see window similar to the one below.
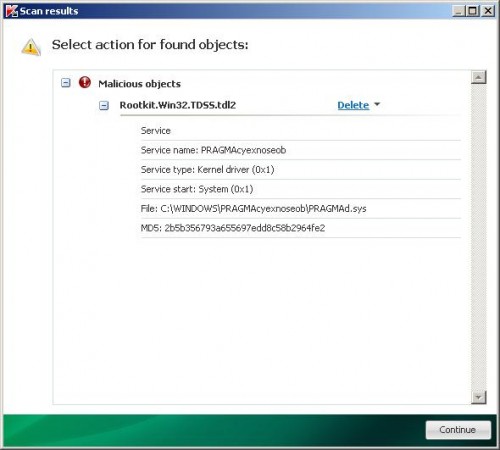
TDSSKiller – Scan results
Click Continue button to remove TDSS trojan.
![]() If you can`t to download or run TDSSKiller, then you need to use Combofix. Download Combofix. Close any open browsers. Double click on combofix.exe and follow the prompts. If ComboFix will not run, please rename it to myapp.exe and try again!
If you can`t to download or run TDSSKiller, then you need to use Combofix. Download Combofix. Close any open browsers. Double click on combofix.exe and follow the prompts. If ComboFix will not run, please rename it to myapp.exe and try again!
Your system should now be free of the Data Recovery virus. If you need help with the instructions, then post your questions in our Spyware Removal forum.
Data Recovery removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
Data Recovery creates the following files and folders
%UserProfile%\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
%CommonAppData%\[RANDOM]
%CommonAppData%\~[RANDOM]
%UserProfile%\Desktop\Data Recovery.lnk
%CommonAppData%\[RANDOM].exe
%Temp%\smtmp\
%Temp%\smtmp\1
%Temp%\smtmp\1
%Temp%\smtmp\2
%Temp%\smtmp\3
%Temp%\smtmp\4
Note: %CommonAppData% is C:\Documents and Settings\All Users\Application Data (for Windows XP/2000) or C:\ProgramData (for Windows 7/Vista)
Data Recovery creates the following registry keys and values
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\USE FORMSUGGEST = Yes
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CERTIFICATEREVOCATION = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WARNONBADCERTRECVING = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WARNONZONECROSSING = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\3\1601 = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\WINTRUST\TRUST PROVIDERS\SOFTWARE PUBLISHING\STATE = 146944
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\CONTROL\SESSION MANAGER\PENDINGFILERENAMEOPERATIONS = \??\%CommonAppData%\[RANDOM].exe
Data Recovery removal – Video instructions
Data Recovery is basically clone of Windows XP Repair, so you can use the video guide below to remove this malware.











YOU guys are genius thank you so much for your help fixed it first try with your information what else can i say THANK you
Awsome, you saved my friend. Thanks for writing this. Mahalo