What is Easy file
.[easybackup@aol.com].easy is a file extension that is used by the latest variant of Phobos ransomware. ‘Easy’ variant is very similar in its characteristics to other variants of this ransomware. It also encrypts files, and then renames them, giving them a new filename consisting of their old and ‘.id[user-id].[easybackup@aol.com].easy’ appended at the end. Criminals demand a ransom for a key-decryptor pair, which is necessary to unlock encrypted data.
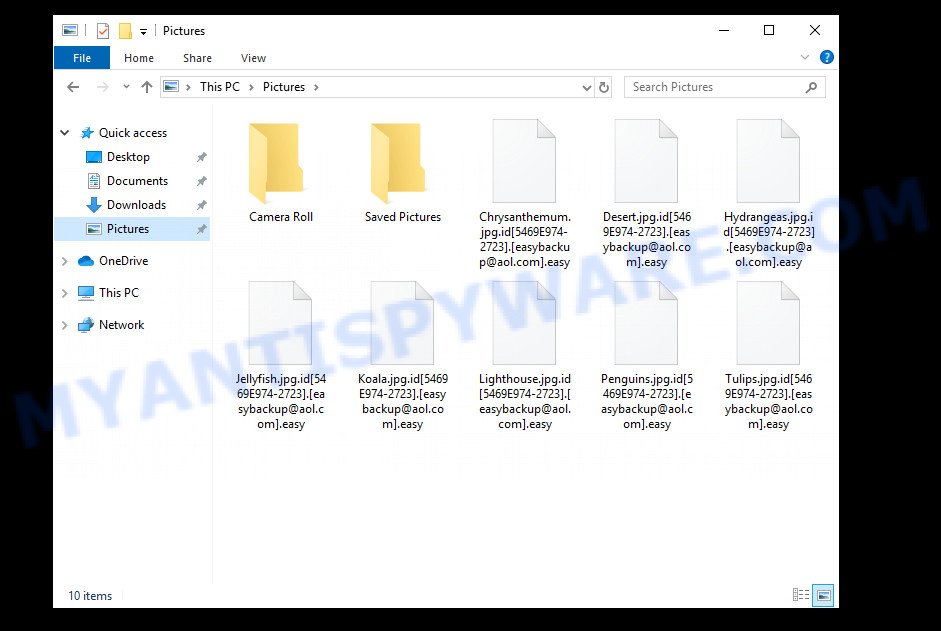
Files encrypted with .Easy extension
What is Easy ransomware
Easy ransomware is one of the variants of the Phobos ransomware. It appends the ‘.Easy’ extension to each file that it encrypts using a complex encryption mechanism. As its previous variants, it can use the same distribution methods (spam emails, adware, cracks, key generators and so on). Upon execution, Easy starts working in the background immediately. First of all, the virus configures the Windows so that it starts automatically every time the computer is turned on. Easy ransomware uses this mechanism to continue encrypting files if it was interrupted by turning off or restarting the computer. Further, the ransomware contacts its control server to send information about the infected computer and receive additional commands.
After all the preparatory steps are completed, Easy proceeds to the main thing, it begins to encrypt files. All files will be encrypted, regardless of where they are located, on the local disk or on a network-connected disk. That is, the contents of the following common file types can be encrypted:
.apk, .wmv, .csv, .wbk, .mef, .fos, .wma, .odm, .erf, .xmmap, .big, .pptx, .xml, .0, .rtf, .t12, .xmind, .lvl, .x, .wma, .wmo, .wm, .ai, .wgz, .iwd, .wpg, .doc, .svg, .pem, .upk, .yal, .xbplate, .txt, .docm, .syncdb, .raw, .qdf, .bc6, .yml, .wpd, .blob, .pak, .xlk, .cdr, .webdoc, .dmp, .wbd, .xar, .wb2, .ibank, .icxs, .dbf, .wbm, .m3u, .accdb, .m4a, .xlgc, .rofl, .mdbackup, .sidn, .iwi, .wbc, .wsh, .dba, .hkdb, .bay, .srw, .wav, .fsh, .ztmp, .xdl, .menu, .zw, .map, wallet, .pfx, .webp, .kf, .wire, .zip, .vpp_pc, .psd, .forge, .ods, .wbmp, .sie, .wpt, .ltx, .wotreplay, .wpb, .bc7, .pst, .orf, .lrf, .wpd, .odt, .wdp, .xf, .qic, .litemod, .esm, .p7b, .xxx, .sis, .zabw, .odb, .vcf, .rb, .sidd, .layout, .jpeg, .wcf, .raf, .sum, .db0, .wbz, .itm, .wp6, .wot, .ws, .xlsm, .m2, .mov, .wp, .y, .zip, .xdb, .pef, .3fr, .mpqge, .xpm, .odc, .pdd, .ff, .docx, .rar, .rwl, .wps, .wn, .mp4, .z, .bik, .odp, .xy3, .hplg, .sav, .ptx, .wpe, .dwg, .xll, .p12, .re4, .sql, .xls, .cr2, .mlx, .cas, .xls, .rw2, .z3d, .srf, .wpw, .asset, .ppt, .bar, .desc, .wmv, .avi, .dxg, .epk, .pdf, .css, .wpl, .bsa, .3dm, .zi, .r3d, .mdf, .dng, .js, .mddata, .tor, .sb, .xyp, .cfr, .wmf, .cer, .wp5, .arch00, .itl, .xlsb, .zdb, .dcr, .x3f, .lbf, .eps, .xbdoc, .xld, .der, .wsd, .sid, .flv, .vfs0, .2bp, .nrw, .xx, .itdb, .ybk, .indd, .1st, .png, .rim, .arw, .w3x, .zif, .snx, .zdc
When a file is encrypted, the ‘.id[user-id].[easybackup@aol.com].easy’ extension is added at the end of its name, that is, if you had a file called ‘document.docx’, then a file with the name ‘document.docx.id[28B111A0-2571].[easybackup@aol.com].easy’ will appear in its place. If you change the file name, just delete the added extension, then nothing will change. The file will remain encrypted, and as before, this file will not be possible to open in the program with which it is associated.
Perhaps you found on your computer or its desktop new files called ‘info.txt’ and ‘info.hta’ that for some reason are not encrypted. Examples of such files are given below.
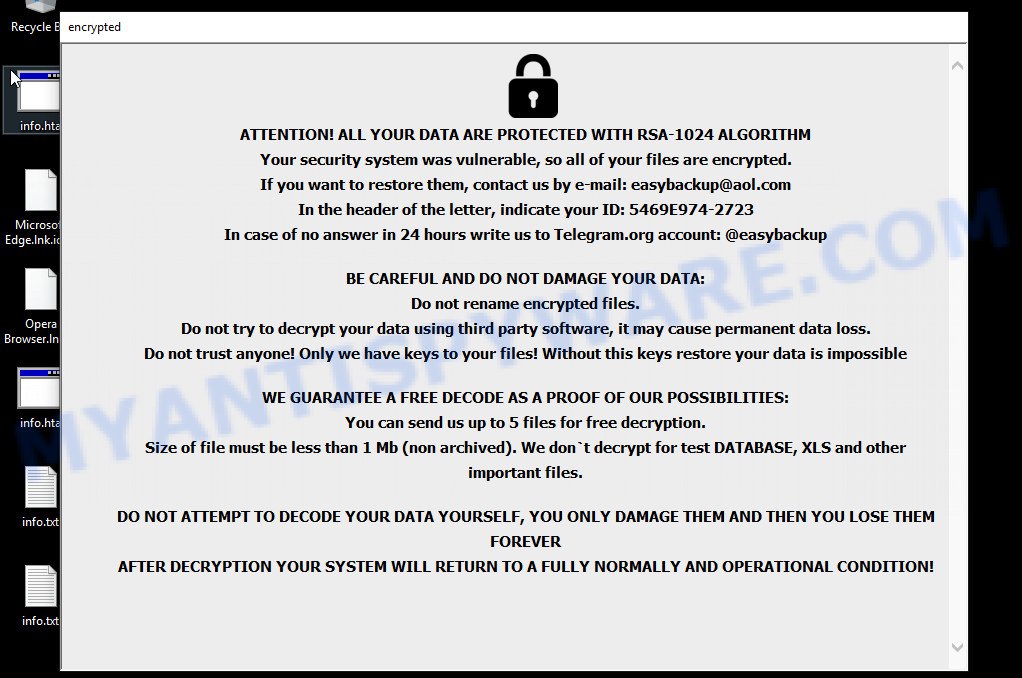
Easy virus ransomnote pop-up
Criminals use the files to demand ransom from the Easy ransomware victims. The ransom demand message said that the victim’s files are encrypted. The authors of the ransomware demand a ransom in exchange for a key and a decryptor. Attackers offer to decrypt 5 files for free, but these files should not contain any valuable information. Of course, decryption of 5 files cannot guarantee that, after paying the ransom, the victim will be able to recover files affected with the ransomware.
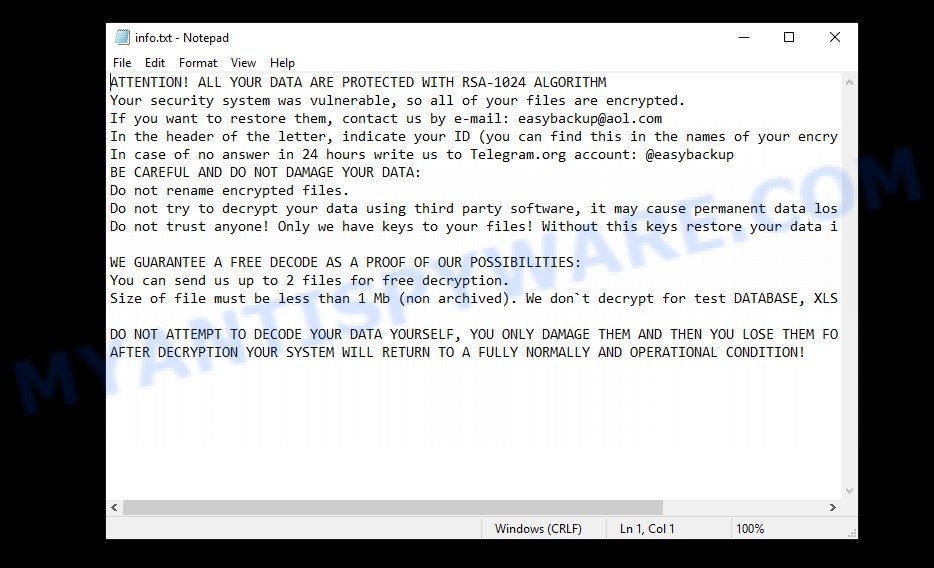
Easy ransomware – info.txt
The full text of the info.txt file:
ATTENTION! ALL YOUR DATA ARE PROTECTED WITH RSA-1024 ALGORITHM
Your security system was vulnerable, so all of your files are encrypted.
If you want to restore them, contact us by e-mail: easybackup@aol.com
In the header of the letter, indicate your ID (you can find this in the names of your encrypted files)
In case of no answer in 24 hours write us to Telegram.org account: @easybackup
BE CAREFUL AND DO NOT DAMAGE YOUR DATA:
Do not rename encrypted files.
Do not try to decrypt your data using third party software, it may cause permanent data loss.
Do not trust anyone! Only we have keys to your files! Without this keys restore your data is impossibleWE GUARANTEE A FREE DECODE AS A PROOF OF OUR POSSIBILITIES:
You can send us up to 2 files for free decryption.
Size of file must be less than 1 Mb (non archived). We don`t decrypt for test DATABASE, XLS and other important files.DO NOT ATTEMPT TO DECODE YOUR DATA YOURSELF, YOU ONLY DAMAGE THEM AND THEN YOU LOSE THEM FOREVER
AFTER DECRYPTION YOUR SYSTEM WILL RETURN TO A FULLY NORMALLY AND OPERATIONAL CONDITION!
Threat Summary
| Name | Easy ransomware |
| Type | Ransomware, Crypto virus, Crypto malware, File locker, Filecoder |
| Encrypted files extension | .[easybackup@aol.com].easy |
| Ransom note | info.hta, info.txt |
| Contact | easybackup@aol.com |
| Ransom amount | $500-$1500 in Bitcoins |
| Detection Names | Trojan/Win32.FileCoder.C4060711, Trojan.Ransom.Phobos, Trojan[Ransom]/Win32.Phobos, Ransom.Phobos.S17079261, Win.Ransomware.Ulise-7594403-0, W32/Ransom.NA.gen!Eldorado, Ransom.Phobos, Trojan.Malware.300983.susgen, Win32.Trojan.Raas.Auto, HEUR:Trojan.Win32.Generic |
| Symptoms | When you try to open your file, Windows notifies that you do not have permission to open this file. Files are encrypted with a .[easybackup@aol.com].easy file extension. Files called like ‘info.txt’, ‘#_README_#’, ‘_DECRYPT_’ or ‘recover’ in each folder with at least one encrypted file.. Ransom note displayed on your desktop. |
| Distribution ways | Unsolicited emails that are used to deliver malicious software. Drive-by downloading (when a user unknowingly visits an infected webpage and then malware is installed without the user’s knowledge). Social media, such as web-based instant messaging programs. Cybercriminals use misleading ads to distribute malicious software with no user interaction required. |
| Removal | Easy ransomware removal guide |
| Recovery | Easy File Recovery Guide |
As we have already said, Easy ransomware is not the first in its series. The fact that to date, antivirus companies have not created a way to decrypt the encrypted files, and just have not found a 100% way to protect the user’s computers (otherwise how would you be on our site), indicates the complexity of the ransomware virus and the method that it uses to encrypt files. Nevertheless, you do not need to despair. There are several ways to find and remove Easy ransomware, and there is also a chance to restore part or even all encrypted files to their original state. Below we will describe in detail how to do this.
How to remove Easy ransomware, Restore .Easy files
If you encounter the malicious actions of Easy ransomware, and your files have been encrypted with ‘.Easy’ extension, then you need to remove the virus or be 100% sure that there is no ransomware on your computer, and then proceed to restore the files. Both the ransomware removal process and the file recovery process will take a lot of time, so do not believe the magical instructions that say that this can be done very quickly. We definitely recommend, even if for some reason one of the methods proposed below did not suit you, try another one and try all of them. Perhaps one of them will help you. Feel free to ask questions in the special section on our website or in the comments below. In addition, we want to say that all the tools that we recommend using in our instructions are free and verified by security experts. And the last, before proceeding with the instructions, we advise you to read it thoroughly carefully, and then print or open it on a tablet or smartphone to have it always at hand.
- How to remove Easy ransomware virus
- How to decrypt .[easybackup@aol.com].easy files
- How to restore .[easybackup@aol.com].easy files
- How to protect your computer from Easy ransomware
How to remove Easy ransomware virus
First you need to remove the Easy ransomware autostart entries before recovering encrypted files. Another option is to perform a full scan of the computer using antivirus software capable of detecting and removing ransomware infection.
It is very important to scan the computer for malware, as security researchers found that spyware could be installed on the infected computer along with the Easy ransomware. Spyware is a very dangerous security threat as it is designed to steal the user’s personal information such as passwords, logins, contact details, etc. If you have any difficulty removing Easy ransomware, then let us know in the comments, we will try to help you.
To remove Easy ransomware, follow the steps below:
- Kill Easy ransomware
- Disable Easy ransomware Start-Up
- Delete Easy virus File
- Scan computer for malware
Kill Easy ransomware
Press CTRL, ALT, DEL keys together.
Click Task Manager. Select the “Processes” tab, look for something suspicious that is the Easy ransomware then right-click it and select “End Task” or “End Process” option. If your Task Manager does not open or the Windows reports “Task manager has been disabled by your administrator”, then follow the guide: How to Fix Task manager has been disabled by your administrator.
A process is particularly suspicious: it is taking up a lot of memory (despite the fact that you closed all of your programs, its name is not familiar to you (if you are in doubt, you can always check the program by doing a search for its name in Google, Yahoo or Bing).
Disable Easy ransomware Start-Up
Select the “Start-Up” tab, look for something similar to the one shown in the example below, right click to it and select Disable. Pay attention to the icon to find the Easy virus. If at the previous step you could not determine the name of the virus process, then after finding the virus on this tab, open the Process tab and look for the process with the same name.
Close Task Manager.
Delete Easy virus File
Run Task Manager and select the “Start-Up” tab. Right click to the Easy ransomware Start-Up entry and select Open File Location as shown below.
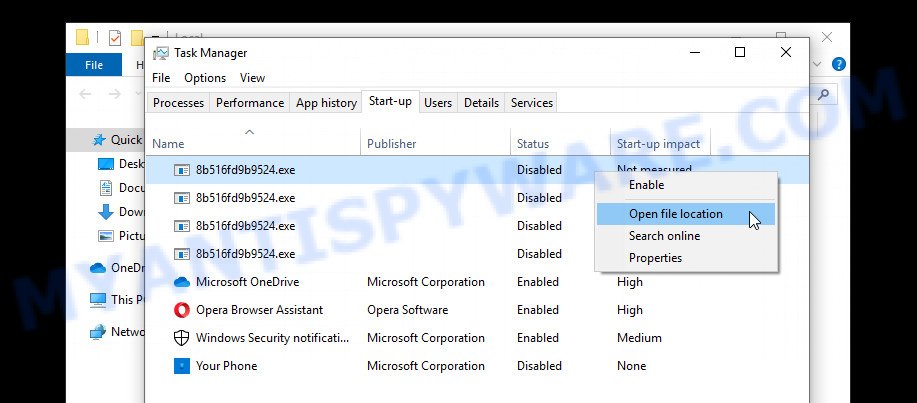
Right-click on the Easy virus file, select Delete.
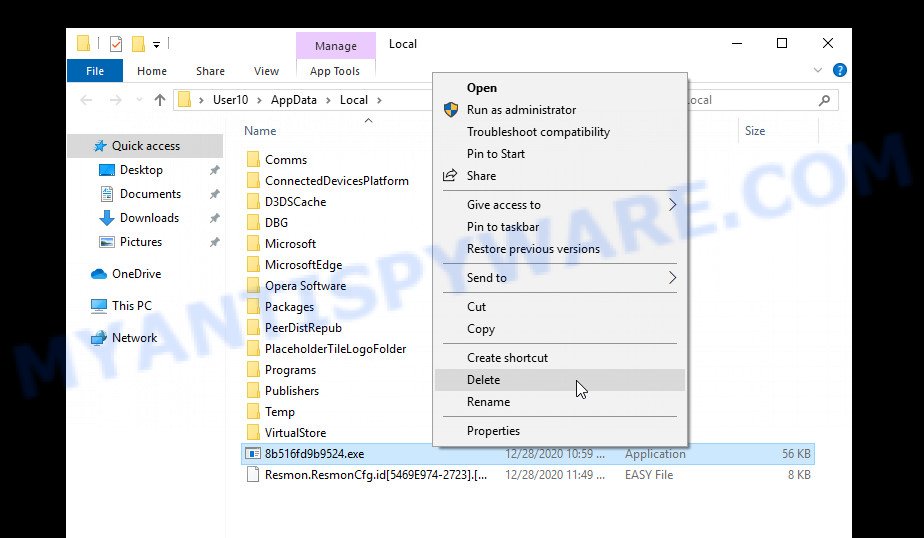
Scan computer for malware
Zemana is a complete package of antimalware utilities that can help you remove the Easy ransomware virus. Despite so many features, it does not reduce the performance of your computer. Zemana can be used to delete almost all the forms of security threats such as ransomware, trojans, worms, adware, hijackers, PUPs and other malware. Zemana AntiMalware has real-time protection that can defeat most malware and ransomware. You can run Zemana with any other anti-virus without any conflicts.

- Installing the Zemana Anti-Malware is simple. First you will need to download Zemana on your Windows Desktop by clicking on the link below.
Zemana AntiMalware
165075 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
- At the download page, click on the Download button. Your browser will open the “Save as” prompt. Please save it onto your Windows desktop.
- After downloading is complete, please close all apps and open windows on your personal computer. Next, launch a file named Zemana.AntiMalware.Setup.
- This will start the “Setup wizard” of Zemana Anti Malware onto your computer. Follow the prompts and don’t make any changes to default settings.
- When the Setup wizard has finished installing, Zemana will run and display the main window.
- Further, click the “Scan” button to perform a system scan for the Easy crypto malware, other kinds of potential threats like malicious software and trojans. During the scan Zemana Anti Malware will look for threats exist on your personal computer.
- When that process is done, Zemana Anti-Malware will produce a list of unwanted apps and ransomware.
- Make sure all threats have ‘checkmark’ and click the “Next” button. The utility will remove Easy crypto virus related folders,files and registry keys and move the selected threats to the program’s quarantine. When that process is done, you may be prompted to reboot the device.
- Close the Zemana AntiMalware and continue with the next step.
In order to be 100% sure that the computer no longer has Easy ransomware virus, we recommend using the Kaspersky virus removal tool (KVRT). This tool, as its name suggests, is designed by the Kaspersky lab and uses the core of the Kaspersky Antivirus. Unlike the Kaspersky Antivirus, KVRT has a smaller size and, most importantly, it can work together with an already installed antivirus. This utility has great capabilities and therefore we recommend using KVRT in the last turn to be sure that the Easy ransomware virus has been removed.
Download Kaspersky virus removal tool on your device by clicking on the following link.
129305 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
After downloading is done, double-click on the KVRT icon. Once initialization process is done, you’ll see the Kaspersky virus removal tool screen as displayed on the image below.
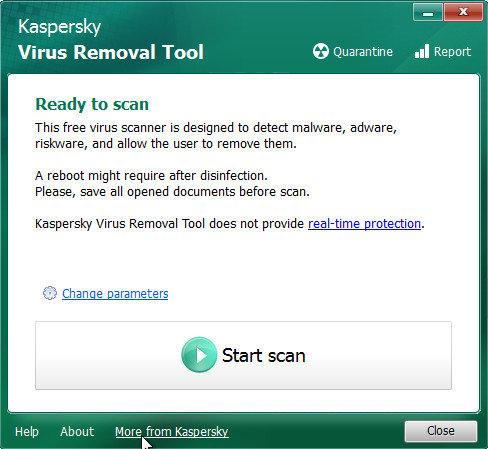
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next click Start scan button to perform a system scan for the Easy crypto virus and other malicious software. A system scan can take anywhere from 5 to 30 minutes, depending on your PC. While the Kaspersky virus removal tool program is scanning, you can see how many objects it has identified as threat.
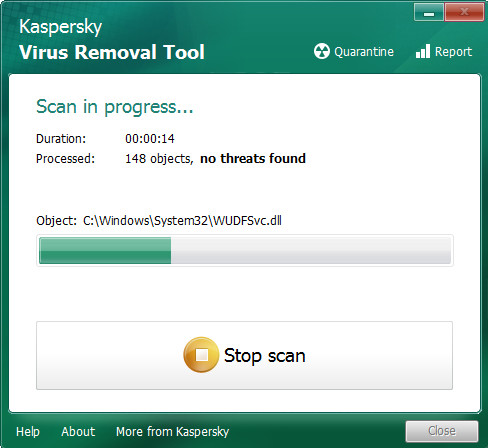
After Kaspersky virus removal tool has finished scanning your computer, it will open the Scan Results as shown on the screen below.
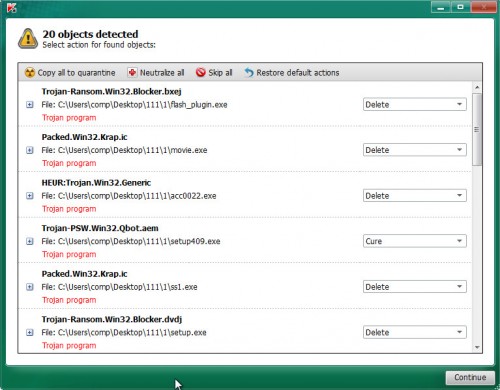
Review the results once the tool has done the system scan. If you think an entry should not be quarantined, then uncheck it. Otherwise, simply click on Continue to begin a cleaning procedure.
How to decrypt .[easybackup@aol.com].easy files
Files with the extension ‘.[easybackup@aol.com].easy’ are encrypted files. In other words, the contents of these files are locked. Their contents cannot be read even if you rename files or change their extension. Unfortunately, today there is no way to decrypt files encrypted by Easy ransomware virus, because to decrypt them you need a unique key, and this key is in the hands of criminals.

Never pay the ransom! Nevertheless, everyone has to remember that paying the developers of the Easy ransomware virus who are threatening you is a terrible idea. You can pay this money, but there is no guarantee that your files will be yours again. That is the reason why you should consider other options (that do not involve paying the makers of the Easy ransomware) in order to decrypt locked personal files. There still are some ways to defuse crypto malware without paying ransom, so you would not need to pay hackers and you would not let them reach their goal.

Files encrypted with .Easy extension
Fortunately, there are several alternative methods that do not require the use of a key and therefore allow you restore the contents of encrypted files. Try to recover the encrypted files using free tools listed below.
How to restore .[easybackup@aol.com].easy files
If all your files are encrypted with .[easybackup@aol.com].easy file extension, then you only have one thing left, use alternative methods to restore the contents of the encrypted files. There are several alternative methods that may allow you to restore the contents of encrypted files. These methods of file recovery do not use decryption, so there is no need for a key and decryptor. Before you begin, you must be 100% sure that the computer does not have active ransomware. Therefore, if you have not yet checked your computer for ransomware, do it right now, use free malware removal tools or return to step 1 above.
Use ShadowExplorer to restore .easy files
A free tool named ShadowExplorer is a simple solution to use the ‘Previous Versions’ feature of MS Windows 10 (8, 7 , Vista). You can recover your documents, photos, and music encrypted by Easy ransomware from Shadow Copies for free. Unfortunately, this method does not always work due to the fact that the ransomware almost always deletes all Shadow copies.
Click the following link to download the latest version of ShadowExplorer for Microsoft Windows. Save it on your Desktop.
439685 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
Once downloading is done, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as displayed in the following example.
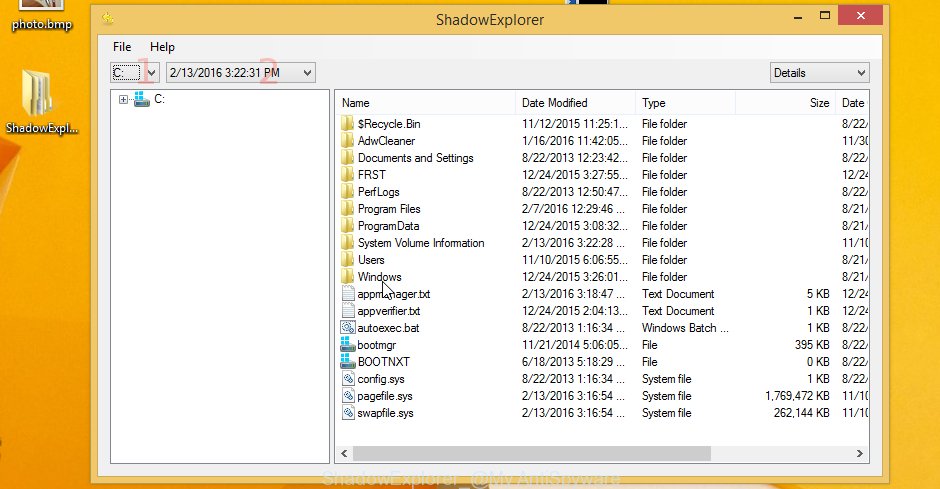
Run the ShadowExplorer utility and then select the disk (1) and the date (2) that you want to restore the shadow copy of file(s) encrypted by the Easy ransomware as shown on the screen below.
Now navigate to the file or folder that you want to recover. When ready right-click on it and click ‘Export’ button similar to the one below.

This video step-by-step guide will demonstrate How to recover encrypted files using Shadow Explorer.
Restore .[easybackup@aol.com].easy files with PhotoRec
There is another way to recover the contents of the encrypted files. This method is based on using data recovery tools. We recommend using a tool called PhotoRec. It has all the necessary functions and is completely free.
Download PhotoRec from the link below.
Once the downloading process is done, open a directory in which you saved it. Right click to testdisk-7.0.win and choose Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as shown on the screen below.

Double click on qphotorec_win to run PhotoRec for Windows. It’ll display a screen as shown in the following example.
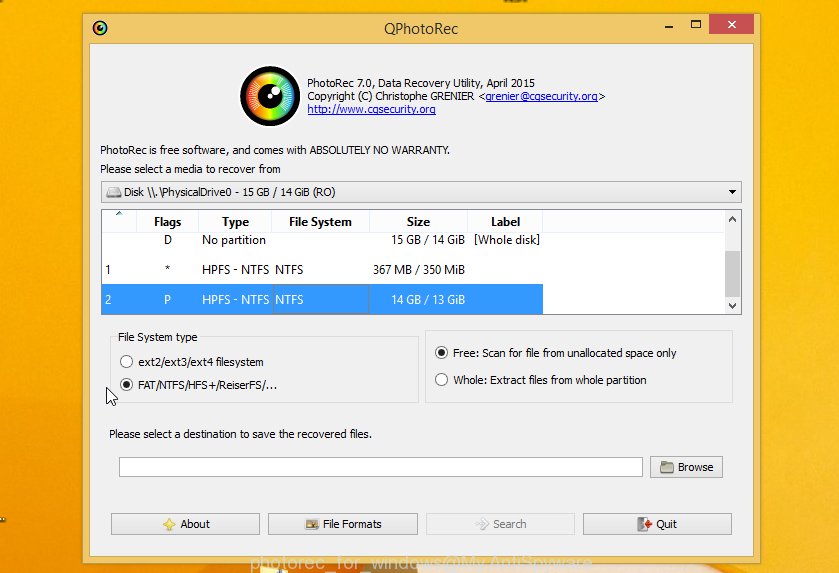
Choose a drive to recover like below.
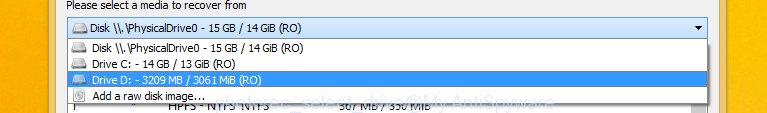
You will see a list of available partitions. Choose a partition that holds encrypted documents, photos and music as shown in the figure below.
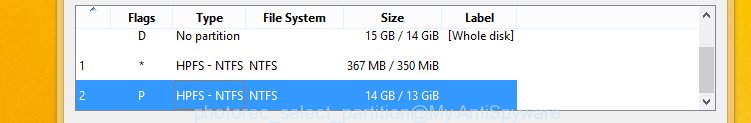
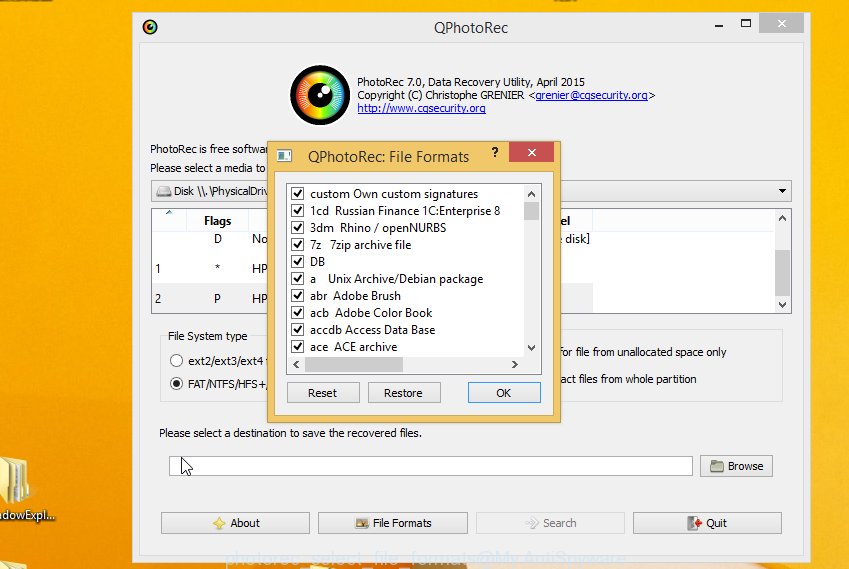
Press File Formats button and choose file types to restore. You can to enable or disable the recovery of certain file types. When this is finished, click OK button.
Next, click Browse button to select where recovered documents, photos and music should be written, then press Search. We strongly recommend that you save the recovered files to an external drive.
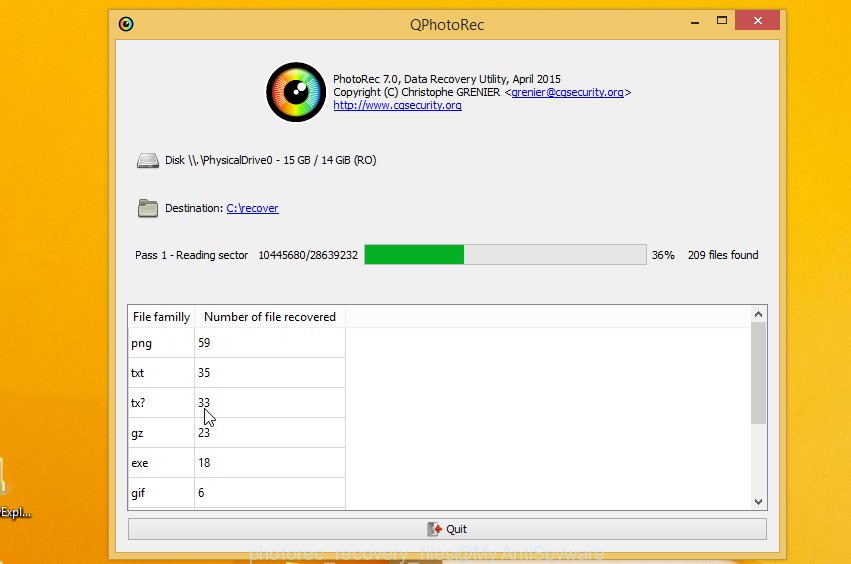
Count of recovered files is updated in real time. All recovered personal files are written in a folder that you have chosen on the previous step. You can to access the files even if the restore process is not finished.
When the recovery is done, press on Quit button. Next, open the directory where restored files are stored. You will see a contents as on the image below.
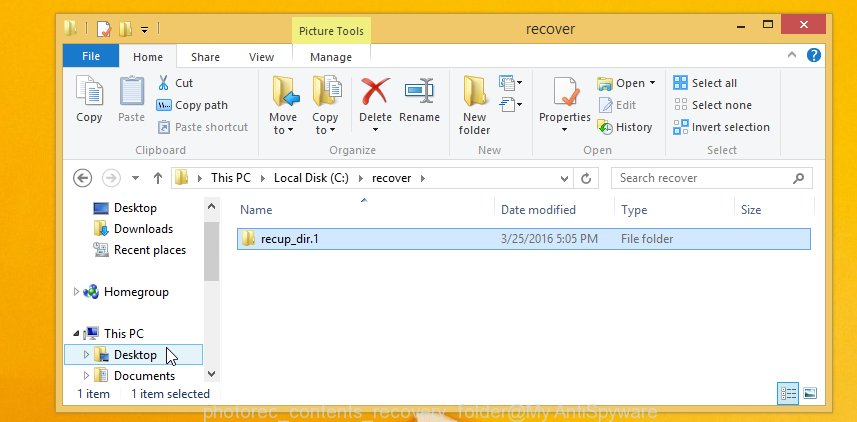
All restored photos, documents and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you’re looking for a specific file, then you can to sort your restored files by extension and/or date/time.
This video step-by-step guide will demonstrate How to recover encrypted files using PhotoRec.
How to protect your computer from Easy ransomware
Most antivirus apps already have built-in protection system against the crypto malware. Therefore, if your PC system does not have an antivirus program, make sure you install it. As an extra protection, use the HitmanPro.Alert. HitmanPro.Alert is a small security tool. It can check the system integrity and alerts you when critical system functions are affected by malware. HitmanPro.Alert can detect, remove, and reverse ransomware effects.
HitmanPro.Alert can be downloaded from the following link. Save it directly to your MS Windows Desktop.
When the downloading process is complete, open the file location. You will see an icon like below.

Double click the HitmanPro.Alert desktop icon. Once the utility is launched, you’ll be shown a window where you can choose a level of protection, as shown in the figure below.
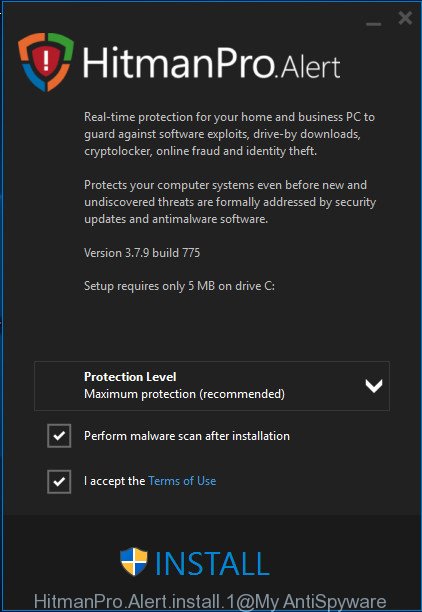
Now press the Install button to activate the protection.
To sum up
This guide was created to help all victims of Easy ransomware virus. We tried to give answers to the following questions: how to remove ransomware; how to decrypt .Easy files; how to recover the encrypted files. We hope that the information presented in this manual has helped you.
If you have questions, then write to us, leaving a comment below. If you need more help with Easy virus related issues, go to here.













![[buydecrypt@qq.com].bip ransomware](https://www.myantispyware.com/wp-content/uploads/2020/12/buydecrypt.qq_.com_.bip_.ransomware-55x55.jpg)