What is a file with extension ‘.Bora’? .Bora file extension is the mark that the ransomware applies to files that have been encrypted. Thus, if you find files with this extension on your computer, then you are the victim of a ransomware attack. You are not the first victim of this ransomware, security experts have already reported on other cases of Bora infection. This ransomware encrypts files during infection, and then changes their extension. For example, a file named ‘document.doc‘, after encryption by the virus, will have the name document.doc.bora. If you rename files or remove the new extension, this will not unlock the files, they will remain encrypted.
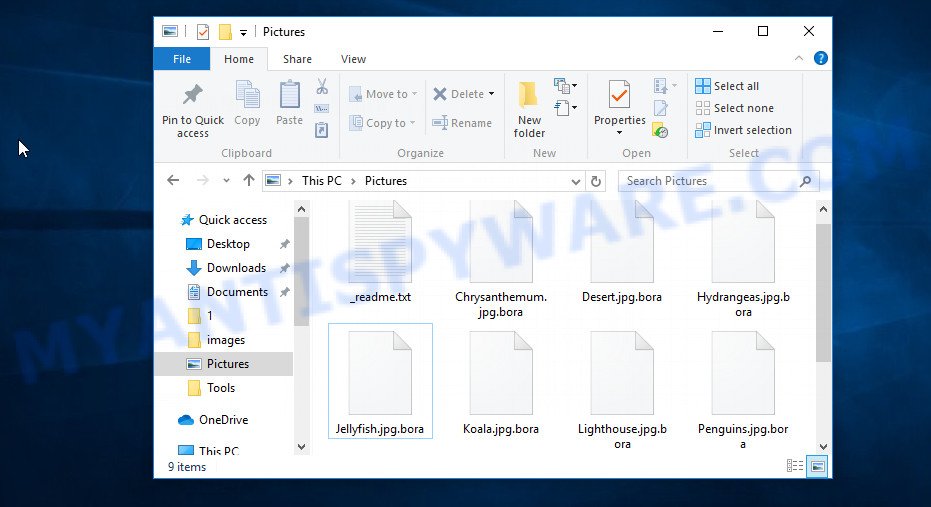
Files with extension ‘.Bora’ are encrypted files
Bora uses a very strong encryption mode and a long key to encrypt files. This eliminates the possibility of determining the key or breaking it. For each case of infection, a new key is used, so the key from one computer will not work for another. During encryption, files located on local disks, network drives, and connected devices will be encrypted. Windows system files are excluded from the encryption process in order not to block the normal operation of the computer. Bora can encrypt almost any type of file, including the following:
.vdf, .xlsm, .dbf, .srw, .xf, .bik, .arch00, .sb, .crw, .lbf, .icxs, .vcf, .gdb, .xbdoc, .rar, .rofl, .db0, .wbd, .wp4, .flv, .crt, .xlsb, .x3f, .odp, .srf, .wpg, .mdf, .m4a, .odm, .vpk, .wmf, .1, .lrf, .desc, .wps, .sidn, .docm, .csv, .docx, .xlsx, .kf, .bc6, .cer, .wcf, .qic, .xlk, .wotreplay, .dazip, .vtf, .pkpass, .p12, .fsh, .wsc, .js, .bkp, .p7c, .t12, .ltx, .t13, .iwd, .wp, .z3d, .bkf, .sis, .wpw, .wsh, .big, .wbm, .xlsm, .rim, .snx, .ws, .wpe, .raf, .py, .1st, .rtf, .xmind, .ai, .wpt, .x, .7z, .wp5, .itm, .iwi, .forge, .3dm, .xpm, .wmv, .accdb, .raw, .ibank, .avi, .asset, .xmmap, .odb, .der, .bay, .bar, .mdbackup, .pdd, .cr2, .odt, .erf, .dmp, .zw, .qdf, .wmd, .wbc, .ysp, .ptx, .0, .indd, .wdb, .gho, .xar, .pdf, .zi, .syncdb, .wpb, .sql, .cfr, .sie, .wpd, .wpd, .pem, .xyw, .xdl, .txt, .xyp, .slm, .wbk, .dng, .ztmp, .zabw, .dxg, .r3d, .bsa, .sidd, .mpqge, .kdc, .esm, .2bp, .rgss3a, .webdoc, .x3f, .mdb, .pak, .mef, .wire, .epk, .wgz, .doc, .m3u, .ntl, .hplg, .lvl, .rwl, .xls, .upk, .z, .png, .webp, .apk, .xx, .xdb, .map, .zif, .yml, .cas, .tor, .das, .mcmeta, .hvpl, .wav, .litemod, .xy3, .ff, .cdr, .wma, .nrw, .pst, .wb2, .jpe, .blob, .y, .wmo, .psd, .xbplate, .wp6, .3ds, .mddata, .pfx, .kdb, .dcr, .hkx, .wsd, .psk, .xml, .zdc, .pef, .dba, .ppt, .xll, .xxx, .pptx, .wpa, .yal, .wdp, .mrwref, .ods, .sav, .rb, .wmv, .xlgc, .wn, .xld, .wps, .xlsx, .wma, .fpk, wallet, .tax, .bc7, .mlx, .w3x, .wbz, .itdb
Files are encrypted in turn, directory by directory. In each directory where there is at least one encrypted file, a new file is created with the name ‘_readme.txt’. This file is so called ‘ransom note’ that was created by the Bora authors and is necessary to explain to the victim why the files do not open in associated programs and how to restore access to the files, that is, how to decrypt them. The victim is informed that all the files were encrypted and that the only way to decrypt them is to buy a key, that is, to pay a ransom. If the victim pays the ransom within 72 hours, then the attackers are ready to make a discount of 50%. Below we give an example of a similar message:
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
https://we.tl/t-iBpEhjntw2
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
The attackers behind Bora offer to write them an email letter in response to which they will give the address to which the ransom will need to be transferred. To remain anonymous, most often, attackers use a bitcoin wallet to obtain ransom from the victim. Although attackers offer to decrypt one file for free in order to confirm the possibility of decrypting files, there is no guarantee that after receiving a ransom, they will provide the key necessary to decrypt all files.
Threat Summary
| Name | Bora ransomware |
| Type | Crypto virus, Crypto malware, File locker, Ransomware, Filecoder |
| Encrypted files extension | .bora |
| Ransom note | _readme.txt |
| Contact | gorentos@bitmessage.ch, gerentosrestore@firemail.cc |
| Ransom amount | $490,$980 in Bitcoins |
| Symptoms | Your photos, documents and music fail to open. Files are encrypted with a .bora file extension. Files called such as ‘_readme.txt’, or ‘_readme’ in each folder with at least one encrypted file. |
| Distribution methods | Unsolicited emails that are used to deliver malware. Drive-by downloads from a compromised web-page. Social media, like web-based instant messaging applications. USB keys containing malicious software. |
| Removal | To remove Bora ransomware use the removal guide |
| Decryption | To decrypt Bora ransomware use the steps |
Bora is not the first of its kind and probably not the last. Almost every day new ransomware is created. Only in the last week we have reported several, such as Reco, Noos and BadutClowns. All of these malicious programs combine similar symptoms. They encrypt files and require ransom for decrypting them. Ransomware authors leave ransom note in a file that is located in directories with encrypted files, but there are often cases when ransom demand message is placed on the desktop, replacing the background. The ransom amount varies from a few hundred dollars to several tens of thousands in case of infection of any large organization. In all cases, it is not possible to decrypt files manually, this is practically impossible. But this does not mean that the victim is left alone with his problem. Anti-virus companies and independent experts analyze the ransomware code and try to create a decryptor that helps victims decrypt their files. Already for many ransomware, decryptors were created that helped thousands of victims to decrypt their files.
Quick links
- How to remove Bora ransomware
- How to decrypt .bora files
- How to restore .bora files
- How to protect your machine from Bora crypto malware?
- To sum up
How to remove Bora ransomware
Of course, if you become a victim of ransomware, the first thing you need to do is perform a full scan of your computer, find and remove Bora. If there is no antivirus on your computer, then you need to install it; if there is an antivirus, update it and then perform a full scan. In addition to antivirus, we strongly recommend that you use malware removal tools. The utilities below will help you find all the components of the ransomware, and then remove it. Do not use only one utility, at least two, since they use different engines, this will significantly increase the chances that Bora will be completely removed.
How to remove Bora ransomware with Zemana
Zemana Anti Malware is a tool to remove various types of malware for free. It can find and delete ransomware, trojans, worms, adware, browser hijackers and other malicious software that most ‘classic’ antivirus software fail to pick up on. Zemana is well suited for any user, as it has a simple interface, small size and quick scan. Set up and run Zemana Anti-Malware (ZAM) to uninstall Bora ransomware from computer by following the steps below:
Visit the following page to download Zemana install package named Zemana.AntiMalware.Setup on your computer. Save it to your Desktop so that you can access the file easily.
165525 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
Run the installer after it has been downloaded successfully and then follow the prompts to install this tool on your personal computer.
During setup you can change certain settings, but we recommend you do not make any changes to default settings.
When installation is finished, this malicious software removal utility will automatically run and update itself. You will see its main window like the one below.

Now click the “Scan” button to perform a system scan with this utility for Bora ransomware, other kinds of potential threats like malicious software and trojans. During the scan Zemana Anti Malware will search for threats exist on your system.

Once Zemana Anti-Malware has completed scanning, Zemana Free will display a screen which contains a list of malicious software that has been found. Make sure all threats have ‘checkmark’ and click “Next” button.
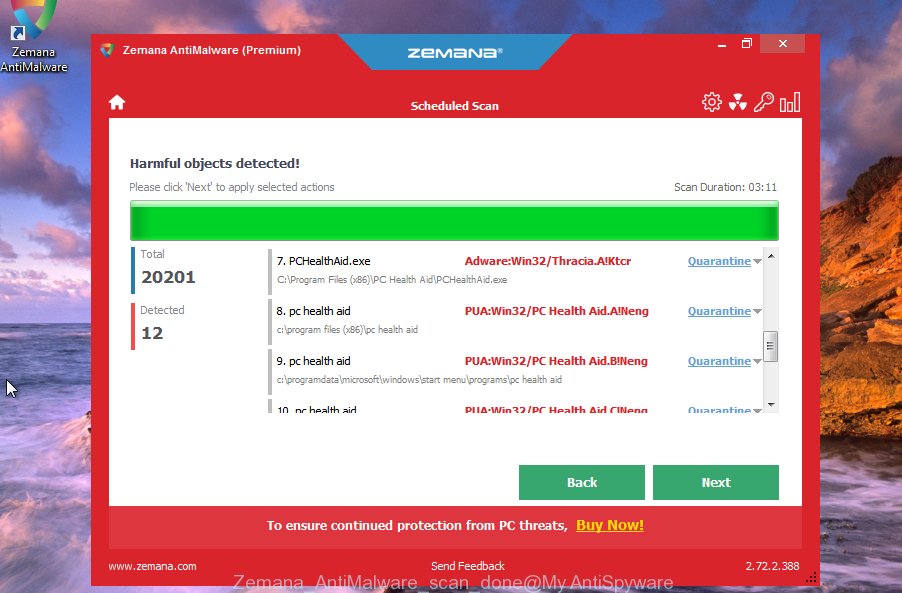
Remove Bora with Kaspersky virus removal tool
The next removal tool that we want to recommend is ‘Kaspersky virus removal tool’ (KVRT). This utility uses the engine of the world famous Kaspersky Security software. That is, this program has great potential for finding and removing Bora ransomware. If malware is found during the scanning process, you can remove it for free by clicking one button.
Download Kaspersky virus removal tool (KVRT) on your personal computer by clicking on the following link.
129501 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
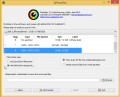
Once downloading is done, double-click on the Kaspersky virus removal tool icon. Once initialization process is complete, you will see the Kaspersky virus removal tool screen as displayed in the following example.
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next click Start scan button to perform a system scan for Bora and other known infections. While the Kaspersky virus removal tool is scanning, you can see number of objects it has identified either as being malware.
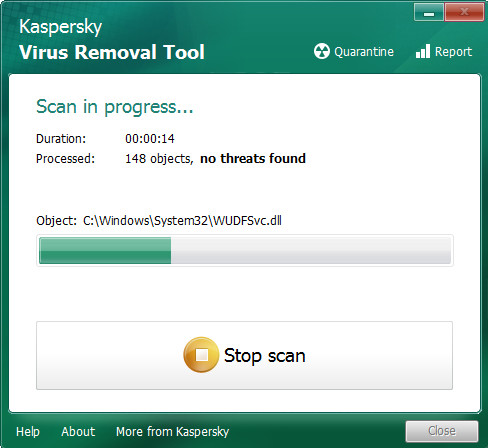
When the scan is finished, you will be displayed the list of all detected items on your PC as displayed below.
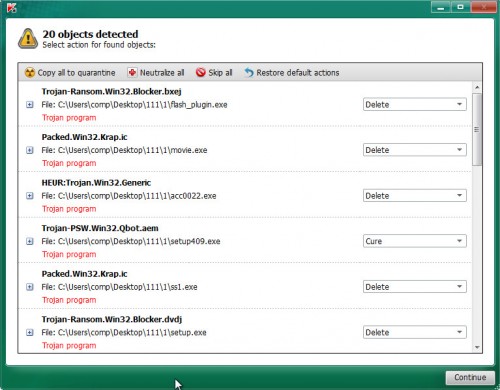
In order to remove all threats, simply click on Continue to begin a cleaning process.
How to decrypt .bora files
If your files are encrypted with .bora extension, then unfortunately at the moment there is no way to decrypt the files. Bora is already 171th version of the same ransomware, but security experts have not yet created an universal decryptor. There is only one reason, we already reported about it above, the ransomware uses a very long key and a strong encryption system. Fortunately, there is a loophole, which in some cases allows you to decrypt some or all of the files.
This loophole is so called ‘offline key’. Bora uses two different keys, depending on whether there is a connection to the control server during encryption. If there is no connection to the server, then the virus uses an offline key, this key is the same for all victims and can be used on any computer. Although experts have not yet found this key, it may be found in the near future. This gives hope to the victims that their files will be decrypted.
How to determine which key Bora used to encrypt your files. First of all, you can look at the personal ID that is given in the ‘_readme.txt’ file (ransom note). Another way, look on disk ‘C’ for ‘systemid\personalid.txt’ file. This is a file in which Bora stores the PersonalIDs used for encryption.
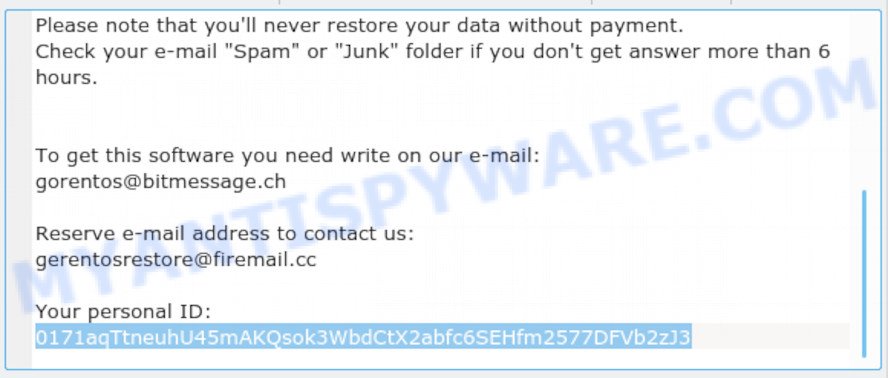
Bora Personal ID is highlighted here
If there is an ID ending in ‘t1’, then you are lucky, your files are encrypted using an offline key, and when security experts find this key, you can decrypt your files. If your Personal ID does not end with ‘t1’, then the ransomware used an online key. In this case, you only have one option left, to use tools that are created to recover data. We will describe this method in detail below.
How to restore .bora files
If your files were encrypted with .bora extension, then there is a chance that you can recover the files without decryption. We recommend using PhotoRec and ShadowExplorer that are designed to find and recover lost and deleted data. Mostly such programs are paid, but these tools can restore your files for free. Each of these tools has helped many times to recover files after ransomware infection in what would seem to be the most hopeless cases. We want to remind you that before you try to recover files, you need to check your computer for malware, find and remove Bora ransomware.
Use shadow copies to restore .bora files
Modern versions of the Windows OS have one very useful feature. The Windows automatically makes copies of the files you use. These copies are called ‘Shadow Volume Copies’ and are not directly visible to the user. ShadowExplorer will allow you to get easy access to these files, and thus restore the original state of encrypted files. Of course, not everything is so simple, unfortunately very often ransomware deletes these copies, thus preventing the simple recovery of encrypted files. But in some cases, copies of the files remain and allow for quick file recovery. Therefore, our opinion, you need to try this method.
Installing the ShadowExplorer is simple. First you’ll need to download ShadowExplorer from the following link.
440047 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
After downloading is finished, open a directory in which you saved it. Right click to ShadowExplorer-0.9-portable and select Extract all. Follow the prompts. Next please open the ShadowExplorerPortable folder as displayed in the figure below.
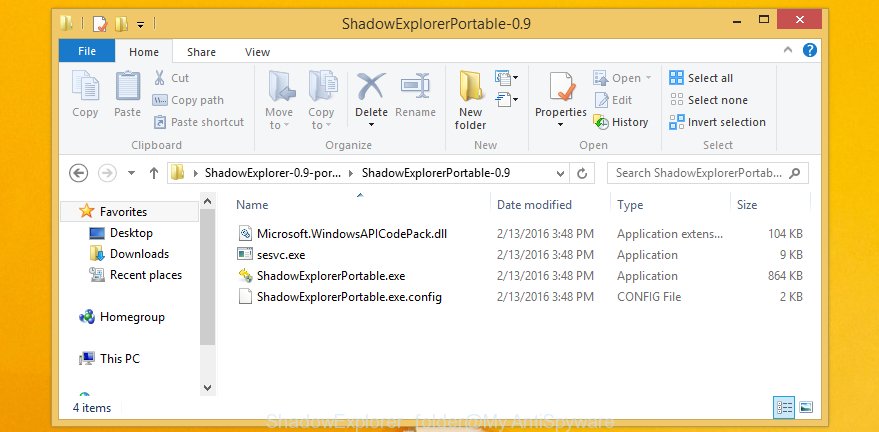
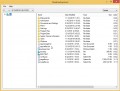
Run the ShadowExplorer utility and then select the disk (1) and the date (2) that you want to restore the shadow copy of file(s) encrypted by the Bora crypto malware as displayed on the image below.
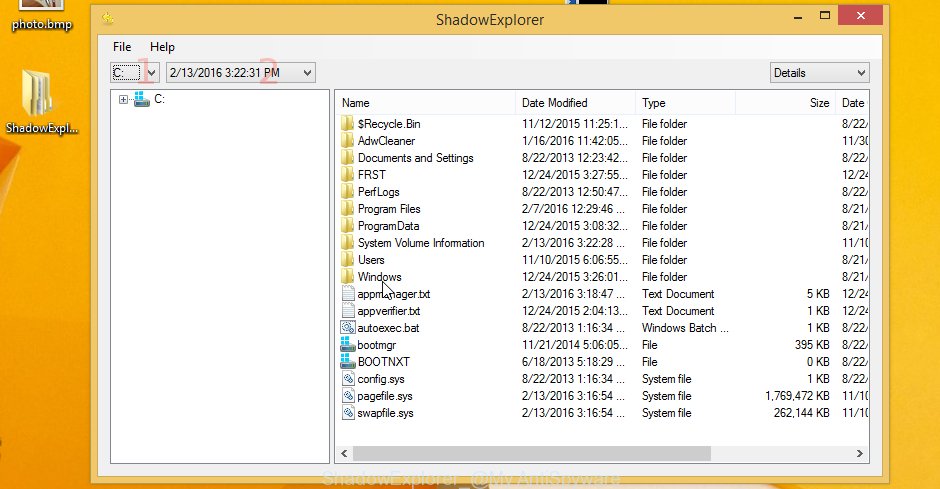
Now navigate to the file or folder that you want to restore. When ready right-click on it and click ‘Export’ button like below.

Use PhotoRec to restore .bora files
There is another very good way to recover encrypted files – use a tool that finds and restores deleted files. We recommend using PhotoRec. This is one of the few programs that allows you to do this for free. The reason that allows you to recover encrypted files using this method is simple – when you or any program, including the ransomware, deletes the file, this file is not deleted, the Windows OS marks it as deleted and hides it. PhotoRec finds such deleted files and restores them. Thus, at the output, you get files in an unencrypted state. The only thing I want to draw your attention to is that the less you used your computer after ransomware infection, the higher your chance of recovering encrypted files.
Download PhotoRec by clicking on the link below.
When the downloading process is finished, open a directory in which you saved it. Right click to testdisk-7.0.win and select Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as displayed in the figure below.

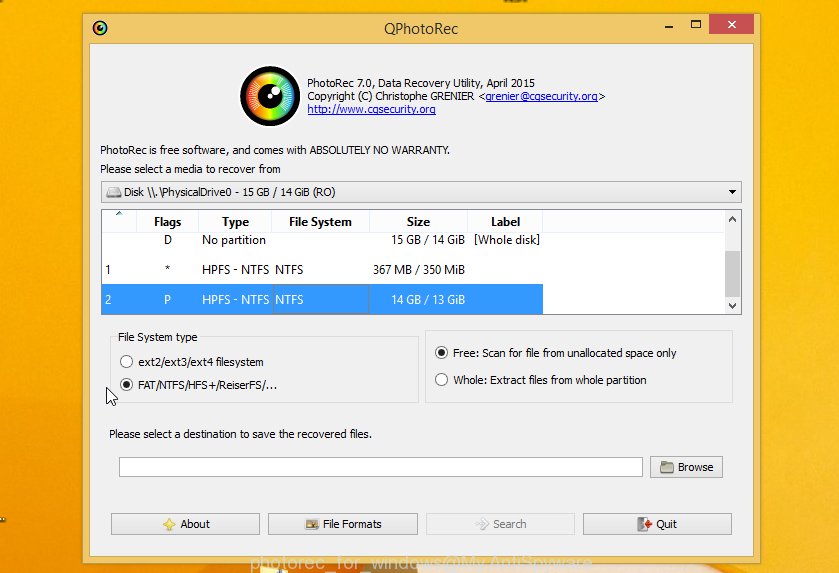
Double click on qphotorec_win to run PhotoRec for MS Windows. It’ll show a screen as displayed in the following example.
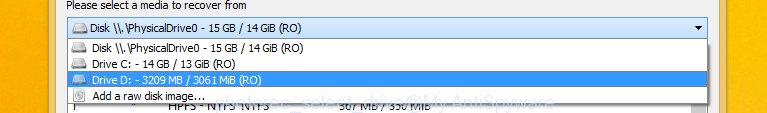
Select a drive to recover as displayed on the screen below.
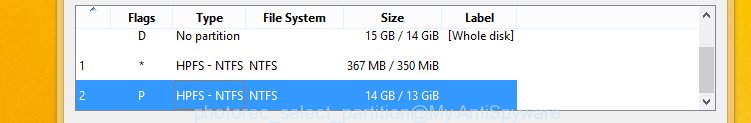
You will see a list of available partitions. Select a partition that holds encrypted photos, documents and music as shown on the image below.
Click File Formats button and specify file types to recover. You can to enable or disable the recovery of certain file types. When this is done, click OK button.
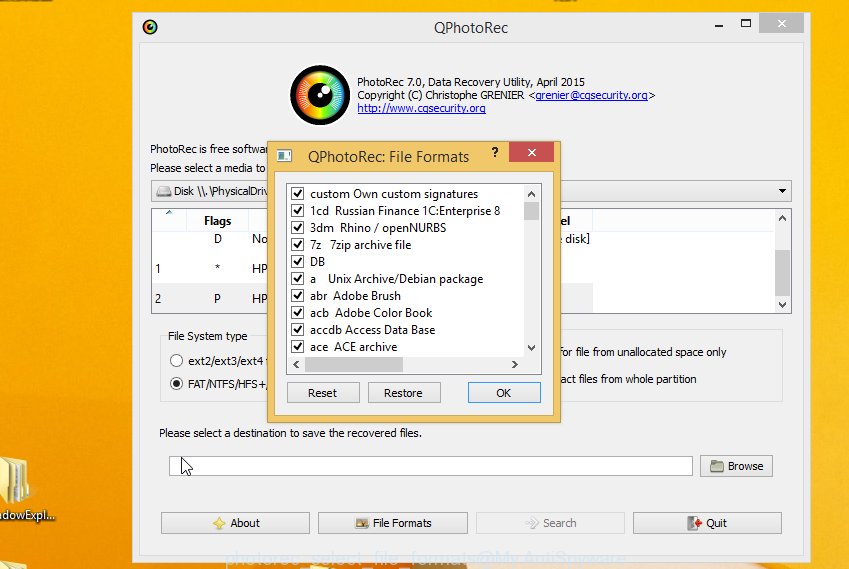
Next, press Browse button to select where recovered files should be written, then click Search.
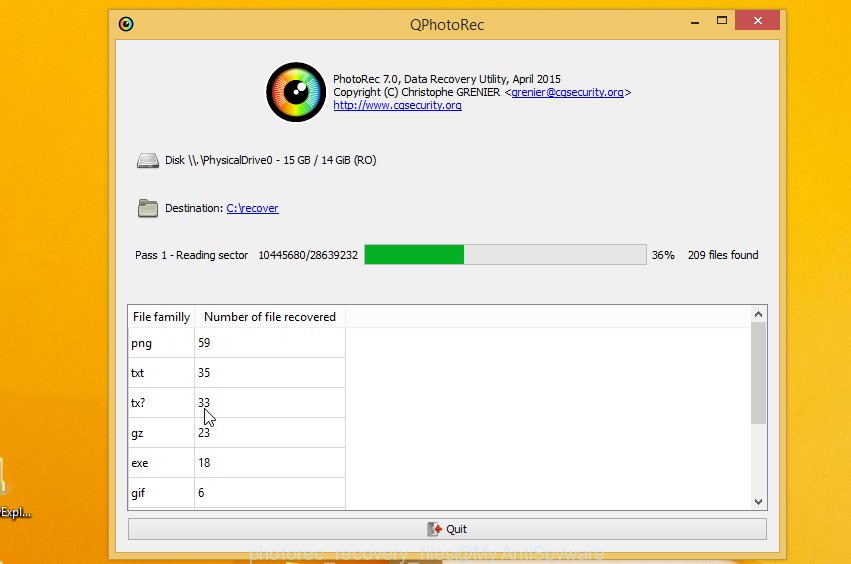
Count of recovered files is updated in real time. All restored documents, photos and music are written in a folder that you have chosen on the previous step. You can to access the files even if the recovery process is not finished.
When the restore is complete, click on Quit button. Next, open the directory where restored files are stored. You will see a contents as displayed in the figure below.
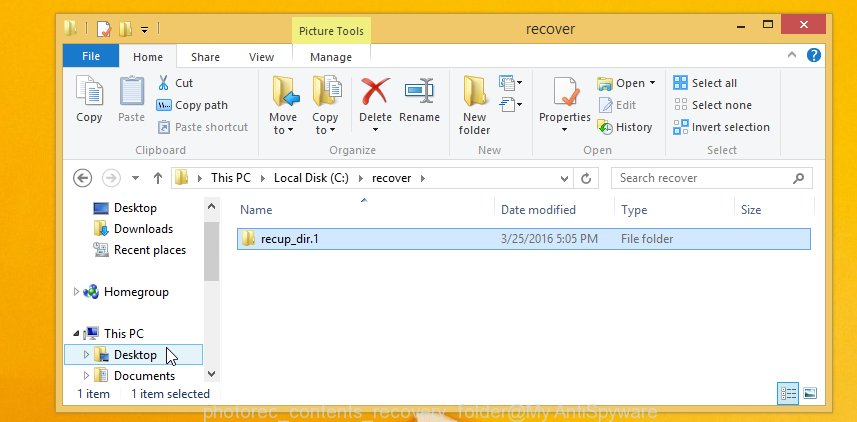
All recovered files are written in recup_dir.1, recup_dir.2 … sub-directories. If you are searching for a specific file, then you can to sort your recovered files by extension and/or date/time.
How to protect your machine from Bora crypto malware?
Most antiviruses can protect your computer from ransomware. Therefore, if you do not have an antivirus, then you need to install it. Of course, choose one that has a ransomware blocking feature. For even greater protection, we recommend installing a program called HitmanPro.Alert. It is a small utility that can check the system integrity and alerts you when critical system functions are affected by ransomware. It can detect and reverse ransomware effects.
Download HitmanPro Alert from the link below.
Once the download is complete, open the file location. You will see an icon like below.

Double click the HitmanPro Alert desktop icon. After the tool is opened, you’ll be shown a window where you can choose a level of protection, as shown below.

Now press the Install button to activate the protection.
To sum up
We hope that this article helped you understand what ransomware is, find and remove malware, and most importantly restore or decrypt .bora files. If you have any questions, comments, then leave them below. If experts find a key or other way to decrypt the files, we will report this in this article or on our Facebook page, so stay tuned.















My problem is within the backup hard drive attach to my main Hard Drive when bora virus infect all my files, I did recover the drive C from my main drive using Shadow Explorer but in the other partition which is the backup drive shadow explorer doesn’t see any encrypted files since it doesn’t have an OS? can you help me with that? thank you..
There are two options:
1. bora virus was able to delete Shadow copies of files
2. in the OS settings, the creation of Shadow copies for these partitions was disabled
However, you can try using PhotoRec, or another tool designed to search and recover data.
How I finished off the infection in the real time
Last year after my clickin on a malware link my computer was infected by several .exe files which automatically downloaded, installed and executed themselves.
The browser fell and stopped working. I immediately noticed some encrypted .bora files on my hd. Realizing what it is, I disconnected the internet and looked at task manager where I spotted three or four unknown items using a lot of processor power. I stopped them immediately and then looked up the latest files in Total Commander, finding both the encryptors and several hundred encrypted files. After deleting them I used Ccleaner, Superantispyware and Adwcleaner to clean my hd and registry. At last I restored the lost files from a backup, losing only several ones.
Since the encryption processed from the top file directories down, gradually delving into subdirs, I moved all my important files down and deeper into Windows system dirs, to buy time to react in case it would happen again. I also backup more often.
Hope this helps.