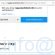
A large number of users from different countries received a suspicious email that begins with the following words: “I’m the hacker who broke your email“. In this email, someone calling himself a hacker reports that the recipient’s emailbox has been hacked and gives the password for this email account as confirmation. This email message is BITCOIN EMAIL SCAM, every word in it is a hoax. We have already reported several times about similar messages that are used by scammers to get a ransom from the recipients of such emails. Despite the fact that these emails are very suspicious, and most people simply delete them, scammers hope that at least a few recipients will be naive enough and pay a ransom.
Screenshot of the contents of “I am the hacker who broke your email” EMAIL SCAM
Attackers are constantly changing the content of these emails, making small changes to the text. Thus, they try to bypass spam filters. Below we give some examples of such letters.
Hey there So I'm the hacker who broke your email and device a several weeks ago. You entered your passcode on one of the internet sites you visited, and I intercepted it. This is your password from *** on moment of compromise: *** However you can can change it, or even already changed it. Nevertheless this would not make a difference, my personal malware modified it every time. Do not really attempt to get in touch with me or even find me, it is impossible, since I sent you mail from your account only. Through your own e-mail, I uploaded malware code to your Operation System. I saved all of your current contacts along with friends, colleagues, relatives as well as a total record of visits to the World wide web resources. Also I installed a Virus on your device. You're not my only prey, I typically lock computers and ask for the ransom. Nonetheless I ended up being struck through the web pages of intimate content material that you frequently pay a visit to. I am in great shock of your own fantasies! I have certainly not noticed something like this! Consequently, when you had fun on piquant web pages (you know what I am talking about!) I made screen shot with using my program by your camera of yours system. After that, I combined them to the content of the currently viewed site. There will be giggling when I send these images to your associates! Yet I'm certain you wouldn't like that. Hence, I expect to have payment from you for my quiet. I consider $900 is an acceptable price regarding this! Pay with Bitcoins. My BTC wallet: 16Qb89akfcw4yVP6TR9pURFkAgdHc6sC5T In case you do not really know how to do this - enter into Google 'how to transfer money to the bitcoin wallet'. It is simple. Immediately after receiving the specified amount, all your data will be immediately destroyed automatically. My virus will additionally remove itself through your os. My Trojan viruses have auto alert, so I know when this specific e mail is opened. I give you two days (48 hours) to make a payment. If this does not occur - every your associates will get insane images from your darker secret life and your device will be blocked as well after two days. Do not end up being foolish! Law enforcement or buddies won't aid you for sure ... P.S I can provide you with advice with regard to the future. Do not enter your security passwords on unsafe web pages. I wish for your discretion. Farewell.
or
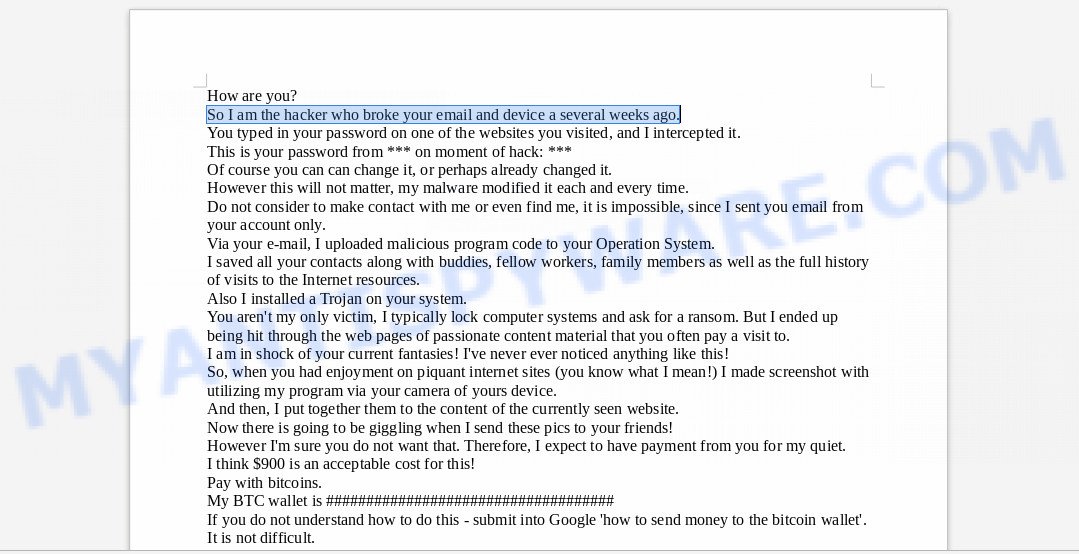
How are you? So I am the hacker who broke your email and device a several weeks ago. You typed in your password on one of the websites you visited, and I intercepted it. This is your password from *** on moment of hack: *** Of course you can can change it, or perhaps already changed it. However this will not matter, my malware modified it each and every time. Do not consider to make contact with me or even find me, it is impossible, since I sent you email from your account only. Via your e-mail, I uploaded malicious program code to your Operation System. I saved all your contacts along with buddies, fellow workers, family members as well as the full history of visits to the Internet resources. Also I installed a Trojan on your system. You aren't my only victim, I typically lock computer systems and ask for a ransom. But I ended up being hit through the web pages of passionate content material that you often pay a visit to. I am in shock of your current fantasies! I've never ever noticed anything like this! So, when you had enjoyment on piquant internet sites (you know what I mean!) I made screenshot with utilizing my program via your camera of yours device. And then, I put together them to the content of the currently seen website. Now there is going to be giggling when I send these pics to your friends! However I'm sure you do not want that. Therefore, I expect to have payment from you for my quiet. I think $900 is an acceptable cost for this! Pay with bitcoins. My BTC wallet is E6W7ANMjGrz5o2FJxFNGziD3siCeiGwqm If you do not understand how to do this - submit into Google 'how to send money to the bitcoin wallet'. It is not difficult. Following getting the given amount, all your information will be promptly eliminated automatically. My malware will also remove itself from your computer. My Trojan have auto alert, so I know when this particular e-mail is opened. I give you 2 days (Forty eight hrs) for you to make a payment. If this does not happen - all your friends will get nuts pictures from your dark secret life and your system will be blocked as well after two days. Do not end up being stupid! Cops or friends won't assist you for sure ... PS I can give you recommendation for the future. Do not key in your security passwords on unsafe websites. I expect for your wisdom. Good-bye.
Is this threat real?
Good news: thankfully, it’s fake. This email message is nothing more than an email scam. Scammers got your password and associated email address from data breach dumps and are using it to shake you down.
Stolen Password
What makes this email scam different?
This is your password from *** on moment of hack: [OLD.PASSWORD]
It has your stolen password and uses that information to make itself appear real. The extortionist actually found it in data breach dumps. If the password emailed to you is one that you still use, then stop using it and change it right now!
Threat Summary
| Name | “I am the hacker who broke your email” email scam |
| Type | Bitcoin Email Scam, Phishing, Fraud, Scam |
| Ransom amount | $900 |
| BTC Wallet | 16Qb89akfcw4yVP6TR9pURFkAgdHc6sC5T, E6W7ANMjGrz5o2FJxFNGziD3siCeiGwqm |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like the I am the hacker who broke your email, our computer security experts recommend follow some easy steps |
What to do when you receive “I am the hacker who broke your email” Email Scam
If you received this email scam, those most important do not worry. Do not believe anything written in it. You can just delete it. If you use Google, Yahoo or another major provider, we recommend marking it as spam before deleting the message. These you will help the system, mark such messages as suspicious. In the future, they will automatically fall into the Spam section of your mailbox.
- First and foremost, do not panic.
- Do not pay the cyber criminals!
- Avoid clicking links in email.
- Use two-factor authentication wherever possible.
- It is a good idea to run a malware scan on all your devices to be sure that there is no malicious software installed.
How to scan your computer for malware
Despite the fact that the received email is a hoax, it will never be superfluous to make sure that there is no malware on the computer. If you do not have an antivirus, and this may be, we recommend downloading and installing. Nowadays it is very dangerous to use a computer that is not protected by an antivirus program. In addition, we recommend that you scan your computer using a tool that’s created to search for and remove malicious programs, as standard antivirus software can skip it.
You can scan for and remove malware through the use of MalwareBytes Anti-Malware. We recommend this free malware removal tool because it may easily trojans, adware, potentially unwanted apps and other malware with all their components such as files, folders and registry entries.
Installing the MalwareBytes is simple. First you will need to download MalwareBytes AntiMalware (MBAM) on your MS Windows Desktop from the link below.
327273 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
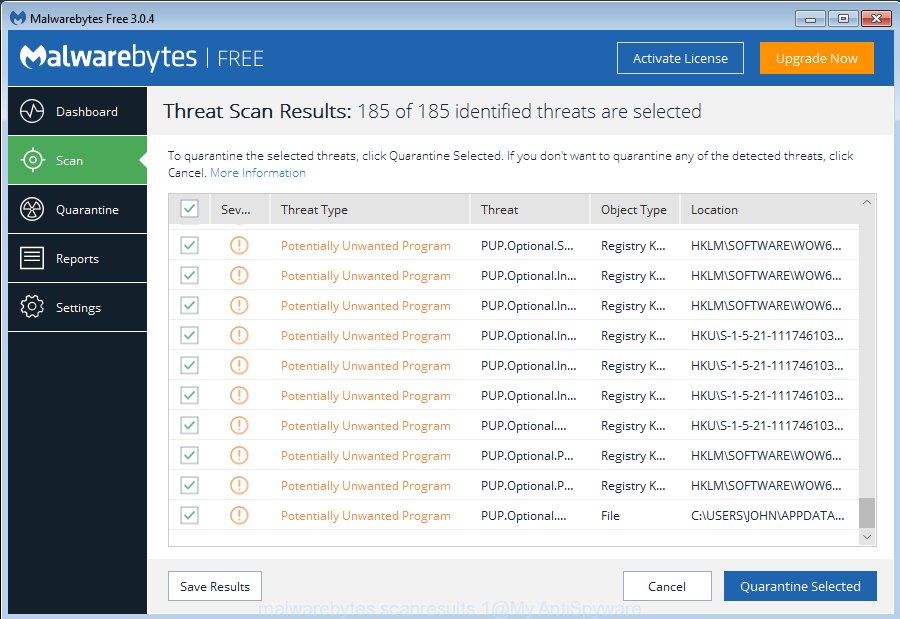
When the downloading process is finished, run it and follow the prompts. Once installed, the MalwareBytes AntiMalware will try to update itself and when this task is finished, click the “Scan Now” button to detect malware related files, folders and registry keys. A system scan can take anywhere from 5 to 30 minutes, depending on your computer. When a malware, ad supported software or potentially unwanted programs are detected, the count of the security threats will change accordingly. When you’re ready, click “Quarantine Selected” button.
The MalwareBytes Anti-Malware is a malware removal tool that you can use to remove all detected folders, files, services, registry entries and other malware related files for free. To learn more about this malicious software removal utility, we recommend you to read and follow the few simple steps or the video guide below.
To sum up
We hope that this article has helped you calm down and learn more about this email scam. If you receive an email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. It will help our team monitor the latest scams.