 SecurePcAv is a rogue antispyware program that installed through the use of trojans. The trojans are mostly distributed from fake online malware scanners.
SecurePcAv is a rogue antispyware program that installed through the use of trojans. The trojans are mostly distributed from fake online malware scanners.
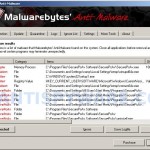
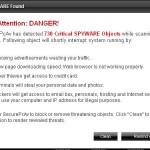
Once the trojan is running, it will download and install SecurePcAv onto your computer and register it in the Windows system registry to run automatically every time when your computer loads. The same trojan will also create a lot of fake malware files, that absolutely harmless, but SecurePcAv will detect them as viruses, trojans, worms and malware. Important to know, the program only imitates a system scan as an attempt to scare you you into thinking that your computer is infected with all sorts of malicious software. So, you can safety ignore the scan results!
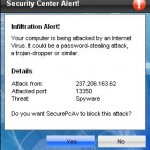
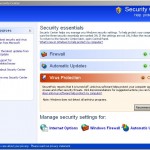
What is more, the same trojan that installs SecurePcAv will also download and install two another trojans. First trojan is a trojan FakeAlert that will display numerous fake security alerts and a fake Windows Security Center that will suggest you register the rogue. Some of the alerts:
Spyware Alert!
Your computer is infected with spyware. It could damage your
critical files or expose your private data on the Internet. Click
here to register your copy of SecurePcAv and remove
spyware threats from your PC.
Security Center Alert!
Infiltration alert!
Your computer being attacked by an Internet
Virus. It could be a password-stealing attack,
a trojan-dropper or simular.
Do you want SecurePcAv to block this attack?
However, all of these alerts are fake and should be ignored! Second trojan is a variant of TDSS trojan/rootkit. The trojan may redirect search results in Google, Yahoo, MSN, block an access to security websites and much more.
As you can see, SecurePcAv is a scam that created with one purpose to trick you into purchasing so-called “full” version of the program. If you find that your computer is infected with this malware, then be quick and take effort to remove it immediately. Use the removal guide below to remove SecurePcAv from your computer for free.
More screen shoots of SecurePcAv
Symptoms in a HijackThis Log
O4 – HKCU\..\Run: [
Spyware can do the following:
1. gather information about user habits of use of the Internet, what sites are visited most frequently (known as “tracking software”);
2. record keystrokes (keyloggers) and make a screenshots (screen scraper) and send collected data to the creator of the spyware;
3. remotely control user computer (remote control software) – backdoor, botnets, droneware;
4. download and run on user computer an additional malware;
5. analyze the state of security systems, scan an open ports, and look for vulnerabilities to crack passwords;
Use the following instructions to remove SecurePcAv (Uninstall instructions)
Download TDSSKiller from here and unzip to your desktop.
Open TDSSKiller folder and double click the TDSSKiller icon. When the scan is finished, you will see window similar to the one below.
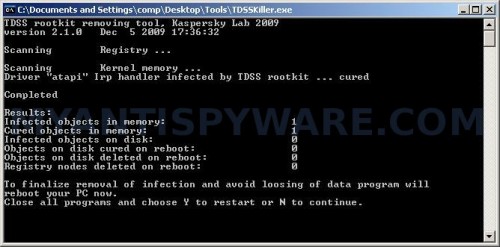
TDSS trojan remover
Close all programs and press Y key.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
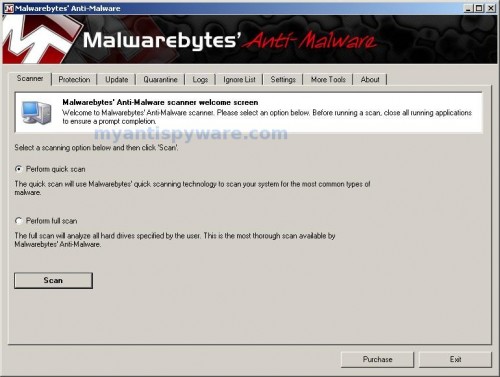
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for SecurePcAv infection. This procedure can take some time, so please be patient.
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
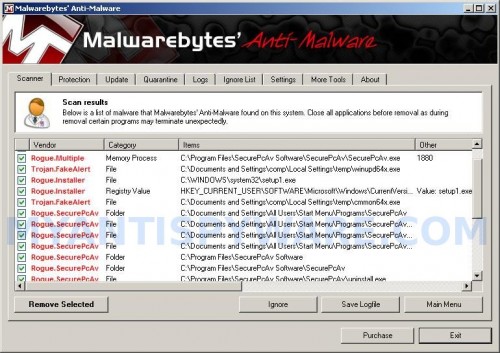
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove SecurePcAv. MalwareBytes Anti-malware will now remove all of associated SecurePcAv files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
SecurePcAv creates the following files and folders
C:\Documents and Settings\All Users\Start Menu\Programs\SecurePcAv
C:\Program Files\SecurePcAv Software
C:\Program Files\SecurePcAv Software\SecurePcAv
C:\Program Files\SecurePcAv Software\SecurePcAv\SecurePcAv.exe
C:\WINDOWS\system32\
Spyware can do the following:
1. gather information about user habits of use of the Internet, what sites are visited most frequently (known as “tracking software”);
2. record keystrokes (keyloggers) and make a screenshots (screen scraper) and send collected data to the creator of the spyware;
3. remotely control user computer (remote control software) – backdoor, botnets, droneware;
4. download and run on user computer an additional malware;
5. analyze the state of security systems, scan an open ports, and look for vulnerabilities to crack passwords;
C:\Documents and Settings\All Users\Start Menu\Programs\SecurePcAv\1 SecurePcAv.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\SecurePcAv\2 Homepage.lnk
C:\Documents and Settings\All Users\Start Menu\Programs\SecurePcAv\3 Uninstall.lnk
C:\Program Files\SecurePcAv Software\SecurePcAv\uninstall.exe
C:\Documents and Settings\All Users\Desktop\SecurePcAv.LNK
SecurePcAv creates the following registry keys and values
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Uninstall\SecurePcAv
HKEY_LOCAL_MACHINE\SOFTWARE\SecurePcAv
HKEY_CURRENT_USER\Software\SecurePcAv
HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\
Spyware software are surreptitiously installed on user`s computer to collect information about computer’s configuration, user`s private information, user’s activity without his consent. Spyware may also change Windows settings, download and install other malicious programs without the user’s knowledge.
.exe