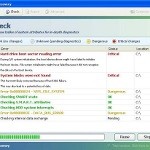
 File Recovery is a fake computer optimization software that detects numerous false problems and displays various critical errors alerts on the computer. The rogue program from the same family of malware as System Check, System Fix, Data Recovery, Master Utilities, PC Repair, System Repair, Windows XP Repair, etc. It is promoted and installed itself on your computer without your permission and knowledge through the use of trojans or other malicious software. Moreover, the scammers may also use various other misleading methods to distribute their bogus software, e.g. Twitter, Facebook and spam emails. Please be careful when opening attachments and downloading files or otherwise you can end up with a rogue program on your PC
File Recovery is a fake computer optimization software that detects numerous false problems and displays various critical errors alerts on the computer. The rogue program from the same family of malware as System Check, System Fix, Data Recovery, Master Utilities, PC Repair, System Repair, Windows XP Repair, etc. It is promoted and installed itself on your computer without your permission and knowledge through the use of trojans or other malicious software. Moreover, the scammers may also use various other misleading methods to distribute their bogus software, e.g. Twitter, Facebook and spam emails. Please be careful when opening attachments and downloading files or otherwise you can end up with a rogue program on your PC
Once installed, File Recovery will be configured to run automatically when Windows starts. Next, the rogue does a fake scan of your computer then tells you it has found numerous critical errors, e.g. “Drive C initialization error”, “Read time of hard drive clusters less than 500 ms”, “32% of HDD space is unreadable”, “Bad sectors on hard drive or damaged file allocation table”, etc. It will require you to pay for the fake software before it “repairs” your machine of the problems. Of course, all of these errors are a fake. So, you can safety ignore the false scan results.
While File Recovery is running, it will block legitimate Windows applcations on your computer and won’t let you download anything from the Internet. Moreover, it will display various fake critical errors alerts that the computer’s hard drive is corrupt in order to frighten you into purchasing this useless application. Some of the fake errors are:
The system has detected a problem with one or more installed IDE / SATA hard disks.
It is recommended that you restart the system.
Critical Error
A critical error has occurred while indexing data stored on hard drive. System restart required.
Critical error
Windows can`t find disk space. Hard drive error.
System Restore
The system has been restored after a critical error. Data integrity and hard drive integrity verification required.
Windows – No Disk
Exception Processing Message 0×0000013.
Of course, all of these warnings are a fake. This is an attempt to make you think your computer in danger. Like false scan results you can safely ignore them.
As you can see, obviously, File Recovery is a scam, which created with only one purpose – to steal your money. Most important, don`t purchase the program! You need as quickly as possible to remove the malicious software. Follow the removal instructions below, which will remove File Recovery and any other infections you may have on your computer for free.
Use the following instructions to remove File Recovery infection
Click Start, Type in Search field %allusersprofile% and press Enter (if you use the Windows XP, then click Start, Run and type a command in Open field). It will open a contents of “ProgramData” folder (“All Users” folder for Windows XP).
File Recovery hides all files and folders, so you need to change some settings and thus be able to see your files and folders again. Click Organize, select ”Folder and search options”, open View tab (if you use Windows XP, then open Tools menu, Folder Options, View tab). Select “Show hidden files and folders” option, uncheck “Hide extensions for known file types”, uncheck “Hide protected operating files” and click OK button.
Open “Application Data” folder. This step only for Windows XP, skip it if you use Windows Vista or Windows 7.
Now you will see File Recovery associated files as shown below.
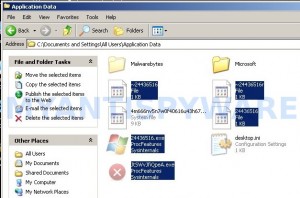
Basically, there will be files named with a series of numbers or letter (e.g. 2636237623.exe or JtwSgJHkjkj.exe), right click to it and select Rename (don`t rename any folders). Type any new name (123.exe) and press Enter.
![]() You can to rename only files with .exe extension. Its enough to stop this malware from autorunning.
You can to rename only files with .exe extension. Its enough to stop this malware from autorunning.
Reboot your computer.
Now you can unhide all files and folders that has been hidden by File Recovery. Click Start, type in Search field cmd and press Enter. Command console “black window” opens. Type cd \ and press Enter. Type attrib -h /s /d and press Enter. Close Command console.
If your Desktop is empty, then click Start, type in Search field %UserProfile%\desktop and press Enter. It will open a contents of your desktop.
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
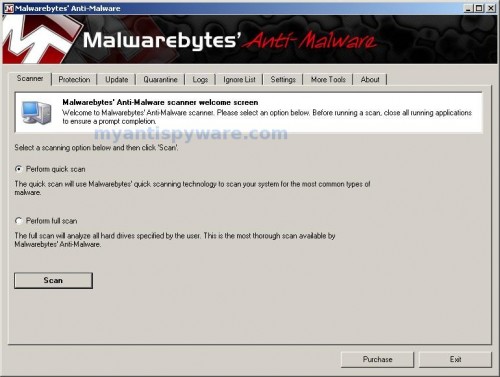
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
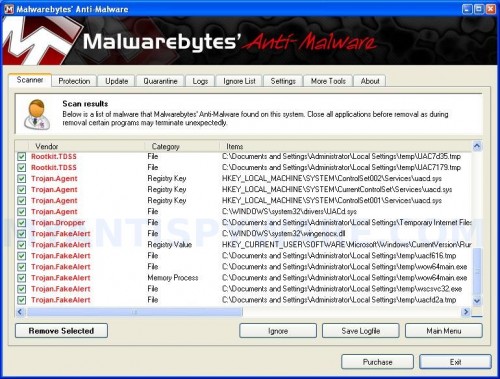
Malwarebytes Anti-malware, list of infected items
Make sure that everything is checked, and click Remove Selected for start File Recovery removal process. When disinfection is completed, a log will open in Notepad. Reboot your computer.
File Recovery may be bundled with TDSS trojan-rootkit, so you should run TDSSKiller to detect and remove this infection.
Download TDSSKiller and unzip to your desktop. Open TDSSKiller folder. Right click to tdsskiller and select rename. Type a new name (123myapp, for example). Press Enter. Double click the TDSSKiller icon. You will see a screen similar to the one below.
TDSSKiller
Click Start Scan button to start scanning Windows registry for TDSS trojan. If it is found, then you will see window similar to the one below.
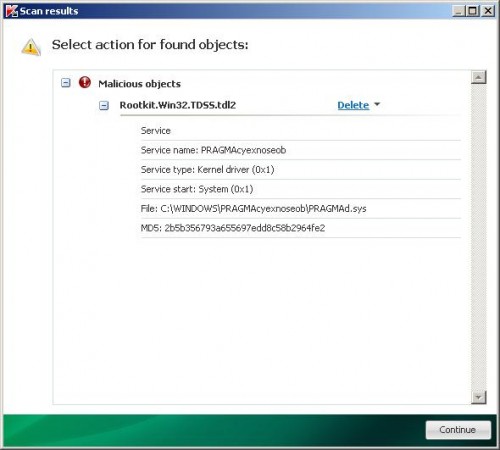
TDSSKiller – Scan results
Click Continue button to remove TDSS trojan.
![]() If you can`t to download or run TDSSKiller, then you need to use Combofix. Download Combofix. Close any open browsers. Double click on combofix.exe and follow the prompts. If ComboFix will not run, please rename it to myapp.exe and try again!
If you can`t to download or run TDSSKiller, then you need to use Combofix. Download Combofix. Close any open browsers. Double click on combofix.exe and follow the prompts. If ComboFix will not run, please rename it to myapp.exe and try again!
Your system should now be free of the File Recovery virus. If you need help with the instructions, then post your questions in our Spyware Removal forum.
File Recovery removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
File Recovery creates the following files and folders
%UserProfile%\Local Settings\Application Data\GDIPFONTCACHEV1.DAT
%CommonAppData%\[RANDOM]
%CommonAppData%\~[RANDOM]
%UserProfile%\Desktop\File Recovery.lnk
%CommonAppData%\[RANDOM].exe
%Temp%\smtmp\
%Temp%\smtmp\1
%Temp%\smtmp\2
%Temp%\smtmp\3
%Temp%\smtmp\4
Note: %CommonAppData% is C:\Documents and Settings\All Users\Application Data (for Windows XP/2000) or C:\ProgramData (for Windows 7/Vista)
File Recovery creates the following registry keys and values
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\INTERNET EXPLORER\MAIN\USE FORMSUGGEST = Yes
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\CERTIFICATEREVOCATION = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WARNONBADCERTRECVING = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\WARNONZONECROSSING = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\INTERNET SETTINGS\ZONES\3\1601 = 0
HKEY_CURRENT_USER\SOFTWARE\MICROSOFT\WINDOWS\CURRENTVERSION\WINTRUST\TRUST PROVIDERS\SOFTWARE PUBLISHING\STATE = 146944
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet\CONTROL\SESSION MANAGER\PENDINGFILERENAMEOPERATIONS = \??\%CommonAppData%\[RANDOM].exe
File Recovery removal – Video instructions
File Recovery is basically clone of Windows XP Repair, so you can use the video guide below to remove this malware.













I got infected this morning, I thought I had a bad hard disk until the “File Recovery” pop-up to my suspicion I googled it and found this page. Very clear and easy to follow, very helpful. Thanks!
You save my computer!Thanks a million!Bless you!
My computer got infected last night. I did everything you suggested and it got rid of the malware but most of my desktop icons were still missing and so were my internet favourites… I managed to find help on another website and managed to restore all my hidden/missing items with software called UnHide. Hope tis helps somebody else who has had this nightmare!
Thanks a lot for your help, much appreciated!
everything seems clear now, thanks! but the files on my desktop are still transparent like they are being hidden, and i still can’t run firefox, it says: “Firefox is already running, but is not responding. To open a new window, you must first close the existing Firefox process, or restart your system.” any way to address these 2 issues?
Hi,
Thank you so much. It was great to find this. It is inmensely appreciated.
It all worked but the right side of my start menu is missing (win xp sp2)
what now???
This virus killed my networking by disabling all my adapters. Fix was pretty easy, just go into networking and enable them again.
Thanks, solution works fine, excelent details and specifications
congrats
ozz
When my laptop got this virus .. Went to computer repair shop they told me they can get my files for $100.. N $200 for removing virus and they ll take 5-6 working days but bcoz of u saved my money n time .. Thanx a ton for ur help .. God bless u
I followed the instructions but I still cannot find my files
Step 7 does not seem to unhide all my files, I have gotten rid of everything fine. However everything is still hidden and have no visable files anywhere.
Should it be saying \access denied\ next to every option in cmd prompt while it’s scrolling after typing in the parameters you have given?
Thanks.
After changing the file names and restarting in normal mode, after a couple of minutes (same time as the virus takes to start up) I get the dread blue screen.
A problem has been detected and windows has been shut down to prevent damage etc.
Technical information:
*** STOP: 0x0000008E (0xC0000005, 0x82D2C097, 0xA6ADC954, 0x00000000)
Not sure if maybe I renamed an exe that I shouldn’t have, there were only three in the ‘all users’ file. All seemed to relate to the recovery virus.
Any answers?
Thank you so much for this post! You made it so easy to remove this! I am so thankful!
it really helps. I finally killed the file recovery virus from window 7. Thanks a lot.
I removed the malware completely (or so I believe) but have been unable to change my background back to the image it was previously. I can set it to Windows 7 base colors, but it won’t recognize an image when I set it. Is this a problem with the removal of the virus or something unrelated?
Thank you so much for this it helped a lot !
You are a life saver!!!
Thanks this worked. Now if we could only find the person who wrote this virus.
Thank you so much for this info! It was easy to follow your directions for an amateur and seemed to do the trick! With all the software that’s out there it’s rare to find a truly free fix that’s reliable. Thanks so much!
There’s another way to do this without using any software..
Just Run MSCONFIG on your PC
Choose Selective Startup
Click on the ‘Startup’ tab
Uncheck all programs
Click OK and Restart
Now your PC will start without the annoying File Recovery thing
Locate the File Recovery Shortcut on the desktop and Go to properties
Check its target file
(On my PC it was- C:\Documents and Settings\All Users\Application Data\ttffgdhsjj.exe)
Go to that location and delete the file(s) with that name
Go to the Desktop and Delete the File Recovery Shortcut
Empty you recycle bin
Nw you can get your original startup setting with MSCONFIG again
Ta-da!
My PC worked fine after that..
Hope this helps :- )
Our laptop got infected with this virus yesterday. I am glad saw this article. Pretty much followed everything except TDSS. But ComboFix did work. BTW: Combofix will take a long time but it does clean-up good. Looks like the laptop is happy now.. we are too! Thanks a bunch!
what a lifesaver thank you so much!Just two things the files on my desktop are still transparent like they are being hidden, and i still can’t run firefox, it says: “Firefox is already running, but is not responding. To open a new window, you must first close the existing Firefox process, or restart your system.” any way to address these 2 issues?
This was certainly one of the most easiest instructional information Iv read in a long time. Nothing worse then a complicated solution to what’s an already complicated situation.
Thank you for taking time out of your life to help others. That’s gotta feel great and I know Im appreciative of it..