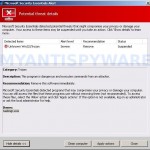
 If you are seeing a Microsoft Security Essentials Alert box that states that Unknown Win32/Trojan was detected on your computer, then you have become infected with a trojan FakeAlert that uses this fake alert to trick you into thinking your PC is infected so that you will then install and purchase one of 5 rogue antivirus programs: Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard.
If you are seeing a Microsoft Security Essentials Alert box that states that Unknown Win32/Trojan was detected on your computer, then you have become infected with a trojan FakeAlert that uses this fake alert to trick you into thinking your PC is infected so that you will then install and purchase one of 5 rogue antivirus programs: Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard.
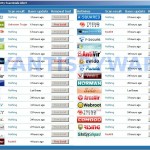
The “Microsoft Security Essentials Alert” trojan come from fake malware online scanners or malicious websites that ask users to download an Adobe Flash Player update or player needed to view a movie online. Once running, it will display a fake alert that looks like an alert from legitimate Windows Microsoft Security Essentials. As already stated above, it will state that your computer is infected with a trojan that have Severe level and then prompt you to clean your PC by clicking on the Clean Computer or Apply actions buttons. When you click on these buttons, it will say that unable to cure your computer and then prompt your to perform an online scan. During the scan, it will list various antivirus programs and only 5 of which find that your computer is infected with a trojan or rootkit. These 5: Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard. The “Microsoft Security Essentials Alert” trojan does it to force you into clicking to the Free Install button to install a rogue antivirus from the list above onto your PC. All of these rogues are perfectly similar to each other, just have different names and GUI interfaces.
When a selected rogue antivirus is installed, it will reboot your computer to complete the installation process. Once Windows loaded, it will simulate a system scan and detect a lot of infected files. When the scan is complete, the rogue will report that was able to clean the majority of infected files, but was not able to cure a few important Windows files, such as firefox.exe, taskmgr.exe, iexplore.exe and offer to purchase its full version to clean them.
While is running, the “Microsoft Security Essentials Alert” trojan can block the Windows Task Manager, legitimate Windows applications, as well as display numerous fake security warnings and alerts. Some of the alerts:
Microsoft Security Essentials Alert
Microsoft Security Essentials detected potential threats that might compromise your privacy or damage your
computer. Your access to these items may be suspender until you take an action.
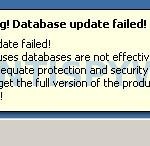
Warning! Database update failed!
Database update failed!
Outdated viruses databases are not effective and can`t
guarantee adequate protection and security for your PC!
Click here to get the full version of the product and update
the database!
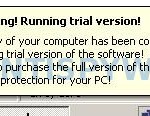
Warning! Running trial version!
The security of your computer has been compromised!
Now running trial version of the software!
Click here to purchase the full version of the software
and get full protection for your PC!
Like false scan results above, all of these alerts and warnings are just a fake and you can safely ignore them.
As you can see, Microsoft Security Essentials Alert trojan wants to trick you into thinking your computer is infected with a lot of viruses and malware as a method to force to install and next purchase one of Red Cross Antivirus, Peak Protection 2010, Pest Detector 4.1, Major Defense Kit, AntiSpySafeguard. Do not be fooled into buying it! Instead of doing so, follow the removal guidelines below in order to remove fake Microsoft Security Essentials Alert and the related rogues from your computer for free.
More screen shoots of Microsoft Security Essentials Alert
Symptoms in a HijackThis Log
O4 – HKCU\..\Run: [tmp] C:\Documents and Settings\comp\Application Data\defender.exe
O4 – HKCU\..\RunOnce: [SelfdelNT] cmd /C del “C:\Documents and Settings\username\Desktop\111\exe.exe”
Use the following instructions to remove Microsoft Security Essentials Alert
Click Start, Run. Type %AppData% and press Enter. It will open the contents of Application Data folder (for Windows XP) or the contents of Roaming folder (for Windows Vista, Windows 7). Rename defender to defender1, antispy to antispy1, hotfix to hotfix1, tmp to tmp1. This is normal if some files listed above does not exist. Next, reboot your computer.
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
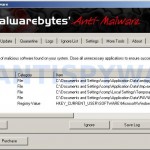
Once the program has loaded you will see window similar to the one below.
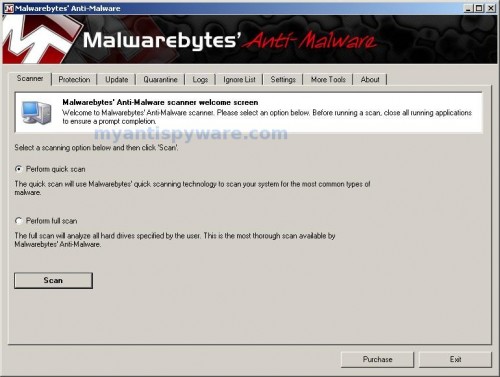
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer for Microsoft Security Essentials Alert infection. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
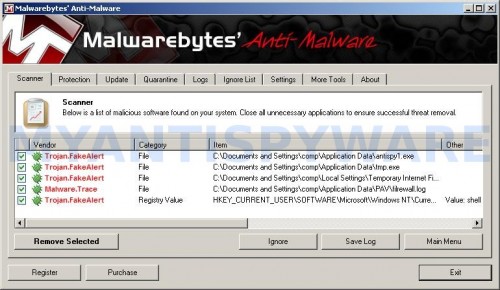
Malwarebytes Anti-malware, list of infected items
Make sure that everything is checked, and click Remove Selected for start Microsoft Security Essentials Alert removal process. When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
Microsoft Security Essentials Alert removal notes
Note 1: if you can not download, install, run or update Malwarebytes Anti-malware, then follow the steps: Malwarebytes won`t install, run or update – How to fix it.
Note 2: if you need help with the instructions, then post your questions in our Spyware Removal forum.
Note 3: your current antispyware and antivirus software let the infection through ? Then you may want to consider purchasing the FULL version of MalwareBytes Anti-malware to protect your computer in the future.
Microsoft Security Essentials Alert creates the following files and folders
%UserProfile%\Application Data\PAV\
%UserProfile%\Application Data\antispy.exe
%UserProfile%\Application Data\defender.exe
%UserProfile%\Application Data\tmp.exe
Microsoft Security Essentials Alert creates the following registry keys and values
HKEY_CURRENT_USER\Software\PAV
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings | “WarnonBadCertRecving” = “0”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings | “WarnOnPostRedirect” = “0”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run | “tmp”
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce | “SelfdelNT”
HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Winlogon | “Shell” = “%UserProfile%\Application Data\antispy.exe”














Worked beautifully. Thank you so much!