“We noticed a login from a device you don’t usually use” is a scam email designed to steal personal information. This fraudulent message masquerades as a security alert, falsely informing you that there has been a login attempt from an unfamiliar device. The email includes convincing details like the type of device and location to appear legitimate. It urges you to click a link to ‘secure’ your account, but this link is deceptive. It directs you to a fake website that looks like a real login page. When you enter your login details on this page, they are captured by scammers. In this article, we will discuss how to identify this type of scam, what to do if you receive such an email, and how to safeguard your online accounts against similar threats.

Table of Contents
Understanding the Scam
“We noticed a login from a device you don’t usually use” is a classic example of a phishing scam, a type of email-based fraud aimed at stealing personal information. These scams are characterized by posing as legitimate security alerts from well-known services.
The Scam Email reads as follow:
Subject: New login to xxx from Safari on Mac OS
We Noticed a New Login,
We noticed a login from a device you don’t usually use.
Mac OS X · Safari · Toronto, ON, Canada
xxx (PDT)If this was you, you can safely disregard this email. If this wasn’t you, you can secure your account here .
Learn more about keeping your account secure.
In this specific case, the email falsely alerts recipients about an unauthorized login attempt and pressures them into clicking a malicious link, all under the guise of protecting their account.
Signs of the Scam:
To recognize this phishing email and others like it, watch for these common signs:
- 🧐 Generic Greeting: The email does not address you by name.
- ⏱️ Urgent Wording: It uses urgent language to create a sense of emergency.
- 🔗 Suspicious Links: There’s a prompt to click on a link that leads to an unfamiliar website.
- 📧 Questionable Email Address: The sender’s email may not match the official format of the service it claims to represent.
How the “We noticed a login from a device you don’t usually use” Email Scam Works
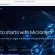
🔍 The scam starts when you receive an email that appears to be from a legitimate service, often disguised as a security alert. It lands in your inbox just like any regular email, making it hard to distinguish from genuine communications. The subject line, “New login to …” is designed to grab your attention and create a sense of urgency. This tactic plays on the fear of unauthorized access to your account, prompting you to act quickly.
🎣 Phishing Link
Inside the email, you’ll find a message claiming that there has been a suspicious login from an unfamiliar device or location. It urges you to click on a link to verify your account or change your password immediately. This link is the phishing element of the scam; it looks like it leads to a legitimate website but doesn’t. The purpose of this link is to deceive you into visiting a fraudulent site where your sensitive information can be stolen.
VirusTotal flagged the link as phishing and malicious:

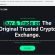
🧩 Fake Login Page
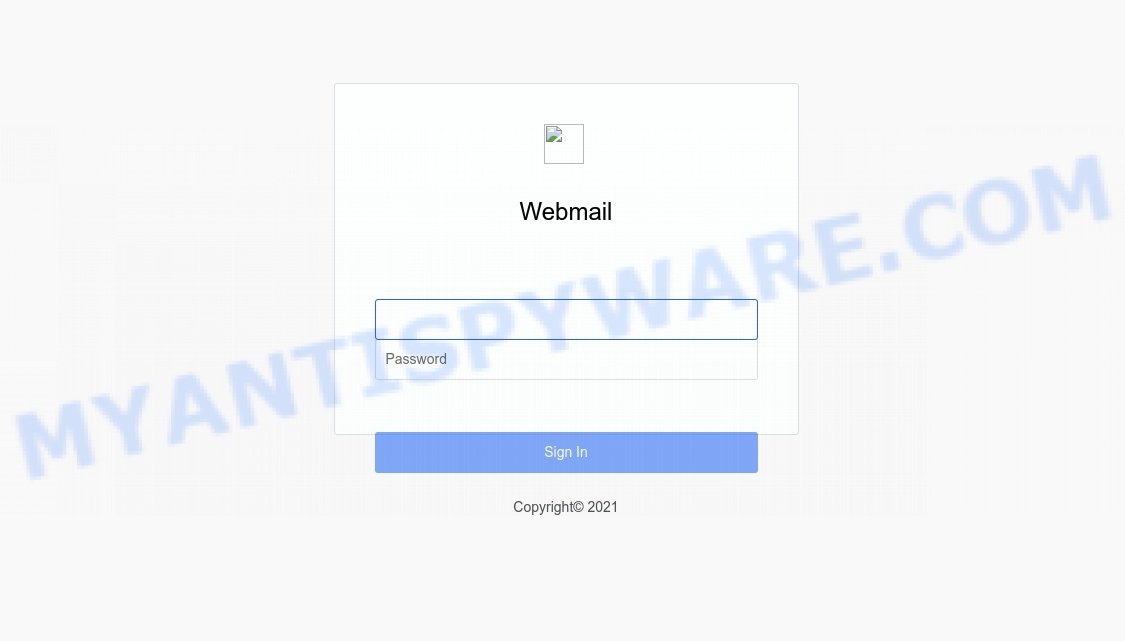
When you click on the link, it redirects you to a fake login page that closely resembles the login page of the service it’s imitating. This page is carefully crafted to look authentic, complete with logos and branding that match the real service. Here, you’re asked to enter your username and password. The purpose of this page is to capture your login credentials, which the scammers can then use to gain unauthorized access to your account and potentially commit identity theft or financial fraud.
A fake Fake Login Page:
📧 What to Do If You Receive Such a Phishing Email
Here are the steps you should take if you receive an email that appears to be a phishing attempt:
🚫 Do Not Click Links
The most crucial step is to avoid clicking on any links or downloading any attachments from suspicious emails. Phishing emails often rely on these links to lead you to fraudulent websites or download malware onto your device.
🔍 Verify Legitimacy
Instead of acting on the email’s content, contact the organization or service directly through official channels. Use contact information you find independently, not any provided in the suspicious email, to verify if the email is legitimate. For example, if you receive a suspicious email about your email account, go directly to your email provider’s website and contact their support.
🚀 Report It
Most email providers have built-in features to report phishing emails. Use these features to help protect yourself and others. Reporting the email can trigger an investigation by your email provider or relevant authorities.
🔒 Change Password
If, unfortunately, you’ve already clicked on a suspicious link and entered your login credentials, it’s vital to change your password immediately for the affected account. This action helps secure your account against unauthorized access.
By following these steps, you can protect yourself from falling victim to phishing scams, maintain the security of your accounts, and contribute to the fight against cybercrime. Remember, staying cautious and informed is your best defense against phishing attempts.
Summary Table
| Name | “We noticed a login from a device you don’t usually use” Email Scam |
|---|---|
| Type | Email phishing scam |
| Danger Level | High |
| Damage | Unauthorized access to email accounts, identity theft |
| Tactics | Urgent language, fraudulent links, impersonation |
| Distribution | Via spam emails |
| Prevention Tips | Verify emails with the sender, hover over links to check their destinations, be cautious with personal information |
| Reporting Info | Use the reporting features of your email provider to report phishing attempts |
Other Similar Scam Emails
Security Alert for [Account]
This scam email mimics a security alert from a reputable service like Google, informing you of a login from a new Windows device. It stresses the importance of the email being a recovery email for the account and urges you to click a link to “check activity” or “unlink” if unknown. Despite its official appearance, complete with Google’s address and branding, the purpose is to lead you to a phishing site where your credentials could be compromised.
Subject: Security alert for xxx
This email is a copy of the security alert sent to xxx. [-Email-]] is the recovery email address for this account. If you don’t know this account, unlink it .
The new device is signed in to:
xxx
Your Google Account has just been signed in from a new Windows device. This e-mail was sent to make sure you are the one signing in.
Check activity
You can see the security activity if you want
xxx
This email has been sent to notify you of important changes to your Google Account and services.
© 2021 Google LLC, 1600 Amphitheater Parkway, Mountain View, CA 94043, USA
Unrecognized Login Attempt
This email claims there has been an “Unusual Signing” into your account, creating a sense of urgency by warning of restricted access and potential loss of files and data. It prompts you to click a “Recover Mail” link to confirm your email and reclaim your account. However, this link is a trap, intended to redirect you to a fake website to steal your login information.
Subject: Unrecognized Login Attempt xxx
Unrecognized Login Attempt
xxx
We received some notification regarding Unusual Signing into your account and recent changes.
You will be restricted to your account and might lead to loss of files, data, contacts, documents and transactions if we do not hear from you
Please kindly click below to Confirm your Email and reclaim your account.
Recover Mail© 2021 xxx
Login Attempted from Your IP Address
Here, the scam email alerts you to a login attempt from a different IP address on your computer, asking if you initiated this login. It provides details like the date and time of the attempt and offers a link to “review your security now.” The aim is to create confusion and concern, leading you to a fraudulent site under the guise of enhancing security.
Subject: [ xxx ] Login Attempted from Your IP address xxx(UTC)
Did You Login From Your IP Address on Your PC Device?
We noticed your Email account – was accessed from another IP address on your computer.When : xxx (UTC)
IP Address : Your IP Address (Secured)
Review your security now
Should we continue to secure your email? Please security access key or customer support immediately.This is an automated message, please do not reply.
Stay connected!
New Device Login Detected
This email informs you of a login from a new device, providing specific details like the date, time, and location of the login (e.g., near Moscow on Windows 10 Pro). It gives options to ignore the message if it was you or to review unauthorized logins otherwise. This approach is to make the email seem personalized and legitimate, encouraging you to click on provided links.
Subject: New device login detected
Hi xxx,
We’re writing to inform you that we detected a login to your account from a new device.
When: xxx UTC
Device: Windows 10 Pro
Near: Moscow
If this was you, you can ignore this message.
If this wasn’t you, go to Settings and privacy and review unauthorized logins.
This is an automatically generated email.
Replies to this email address aren’t monitored.This email was generated for xxx
Privacy Policy
New Device Login from Mac OS
Similar to the first scam, this one notifies you of a login from an unfamiliar device, listing detailed sign-in information like country, IP address, platform, and browser. It presents a relaxed tone, saying you can ignore the email if the login was yours but provides a link to secure your account if it wasn’t. This is another sophisticated attempt to lure you to a fake website.
Subject: New device login from Mac OS
Hello xxx
We noticed a login from a device you don’t usually use.
Sign-in details
Country/region: North Korea
IP address: 79.69.72.66
Date: xxx p.m. (GMT)
Platform: Mac OS
Browser: SafariIf this was you, you can safely disregard this email.
If this wasn’t you, you can Go to Email Account Settings to keep your account secure.Email Account Settings
This e-mail was sent to make sure you are the one signing in.
Sincerely, – Mail ServerCopyright© 2022 All Rights Reserved.
Account Sign-in from an Unrecognized Device
This email alerts you of a sign-in from an unrecognized device, using direct language and urgent calls to action like “AUTHENTICATE YOUR SIGN-IN NOW!” It threatens the suspension of email services and mailbox deletion to push you into acting hastily. Despite its professional tone and privacy assurance, the real aim is to redirect you to a phishing site through the provided link.
Subject: Account Sign-in from an Unrecognized-Device!
Account-Sign-in-for-xxx!
Dear xxx,Your e-mail – has just been signed-in from an unrecognized device at xxx.
AUTHENTICATE YOUR SIGN-IN NOW!
Failure to follow our above instruction will lead to the temporary suspension of some of your incoming and outgoing mail.
Afterwhich mailbox deletion countdown will be activated within 48hrs.Regards,
Accounts Service Inc,You have received this message because you have an xxx account. xxx respects your privacy.
This is an automatic message. Please do not reply to this message.
We Noticed a Suspicious Login Attempt
This scam email alerts you to a supposed suspicious login attempt on your account, providing specific details like location (Lufkin, TX, USA), device (iPhone), and even mentioning that the location is based on the login’s IP address. It asks whether this login attempt was made by you and then splits into two paths: one if it was you, suggesting security questions for verification, and the other if it wasn’t, urging you to change your password and review app access. The email cleverly uses detailed information and a sense of urgency to appear legitimate, aiming to lead you to a fake website where your personal information could be compromised. The detailed instructions and the mention of security measures give it an air of authenticity, making it a sophisticated phishing attempt.
We noticed an attempt to log in to your account xxx that seems suspicious. Was this you?
Suspicious login
Location
Device
xxx, USA xxx on iPhone
“Location is approximate based on the login’s IP address.
If this was you
Just to be safe, to log in to this account you’ll need to verify this is really you by answering some security questions.
If this wasn’t you
Complete these steps now to protect your account.
• Change your password. You’ll be logged out of all your active Twitter sessions except the one you’re using at this time.
• Review the apps that have access to your account and revoke access to any unfamiliar apps. Leam more.
Conclusion
Phishing emails like “We noticed a login from a device you don’t usually use” are common tactics used by cybercriminals to steal sensitive information. By staying vigilant, verifying the legitimacy of emails, and avoiding clicking on suspicious links, you can protect yourself from falling victim to such scams and maintain the security of your online accounts.