Gesd file extension
.Gesd file extension is a file extension that is appended to the name of files affected by the latest version of STOP (djvu) ransomware. Ransomware is a malware that encrypts victims’ files and thus locks up the information contained in them. Ransomware developers demand a ransom in exchange for a decryptor and a key, which are necessary for decrypting the files. Fortunately, since Gesd is one of the variants of STOP (djvu), in some cases you can use the free STOP (Gesd) decryptor to decrypt files affected by it. More details about this decryptor, as well as other ways of recovering encrypted files, will be discussed in this article.
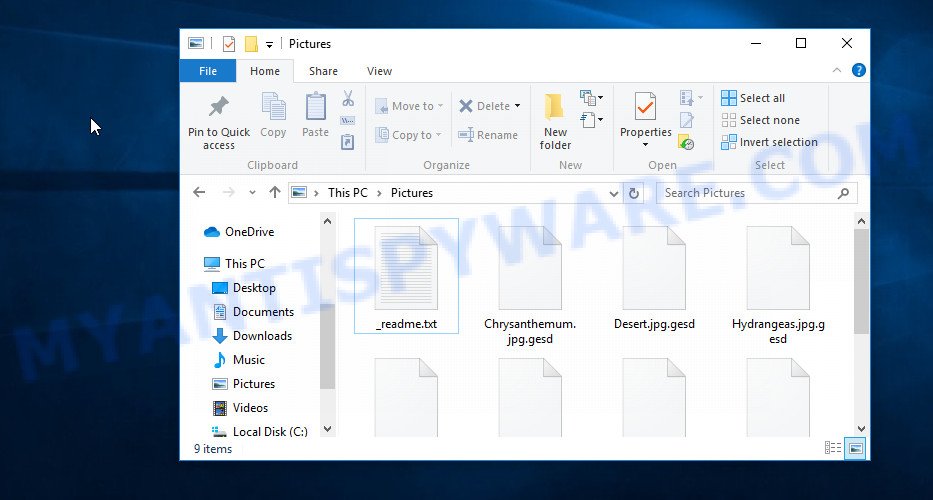
Screenshot of files encrypted by Gesd virus (‘.gesd’ file extension)
Gesd virus
Gesd virus is malware that is 191 version of STOP (DJVU) ransomware. Like other versions of this ransomware, it is distributed through key generators, cracked software, adware and torrents web-sites. Upon execution, Gesd creates a folder in the Windows system directory and copies itself there. Then the virus changes some Windows OS settings so that it starts automatically every time the PC is turned on or restarted.
Having collected information about the victim’s computer, Gesd virus tries to establish a connection with its command-and-control server (C&C). If the connection has been established, the virus receives a key (so called ‘online key’) from the command server that will be used to encrypt files. In addition, Gesd virus may receive additional commands and files that will be executed on the victim’s computer. If the virus could not connect to the command server, then it uses a fixed key, which the security researchers called ‘offline key’.
There is a significant difference between ‘online key’ and ‘offline key’. The online key is unique for each victim, that is, the key from one victim will not help decrypt the files of the other victim. The offline key is the same for all victims. Thus, it can be used to decrypt files regardless of where they were encrypted.

Having a key to encrypt files, Gesd virus proceeds directly to the process of encrypting files. It encrypts file-by-file, so that all files of the victim will be encrypted. It doesn’t matter where the files are located, on the internal drive, flash drive, external media, cloud storage, all of them can be encrypted. There is a small exception, the virus does not encrypt files located in the Windows system directories, files with the extension from the list ‘.lnk, .bat, ini, .sys, .dll’ and files with the name ‘_readme.txt’. Thus, almost all of the victim’s data will be encrypted, including documents, pictures, databases, archives and other types of files, such as:
.xlsx, .lbf, .xdb, .3fr, .xlk, .iwi, .mdf, .cr2, .wbz, .odb, .wp6, .wps, .7z, .mpqge, .wdb, .cer, .p7c, .1, .flv, .rgss3a, .itm, .orf, .wma, .xdl, .ltx, .epk, .desc, .xml, .wbmp, .ptx, .pfx, .cas, .db0, .xar, .rb, .rar, .bay, .dmp, .sav, .wbc, .xx, .rwl, .ai, .pak, .odm, .rofl, .hvpl, .odt, .3dm, .rtf, .itdb, .wp, .3ds, .raw, .p7b, .svg, .wp5, .fsh, .tor, .asset, .raf, .sb, .mp4, .ntl, .x, .r3d, .m3u, .bc6, .jpeg, .tax, .fos, .sid, .docx, .jpe, .js, .wcf, .mrwref, .xpm, .mcmeta, .map, .accdb, .bsa, .dbf, .qdf, .pkpass, .wpe, .hkdb, .ztmp, .zip, .pef, .wav, .crt, .w3x, .wb2, .psk, .d3dbsp, .hplg, .wpd, .wsh, .wmv, .xlsm, .cfr, .wpd, .wpt, .wmv, .snx, .ysp, .txt, .hkx, .vpk, .re4, .2bp, .kf, .indd, .t13, .ibank, .zabw, .wpa, .x3d, .mdb, .esm, .wm, .ods, .xls, .dng, .sql, .vdf, .xy3, .srf, .nrw, .rim, .wdp, .xxx, .psd, .xwp, .dxg, .z3d, .wbk, .ws, .lvl, .litemod, .wpg, .srw, .erf, .wbm, .qic, .xlsm, .dazip, .lrf, .wp7, .wma, .wpw, .forge, .cdr, .zip, .x3f, .apk, .menu, .m2, .jpg, .gdb, .sum, .wbd, .vtf, .das, .wmo, .pptm, .x3f, .mdbackup, .xmmap, .xbplate, .xll, .ppt, .zdc, .gho, .1st, .y, .upk, .docm, .pdf, .p12, .zif, .bik, .wgz, .crw, .odc, .xls, .pem, .wmd, .pdd, .rw2, .xlgc, .kdc, .arw, .eps, .wire, .vcf, .wmf, .wps, .fpk, .webdoc, .py, .xyw, .doc, .t12, .csv, .avi, .slm, .xlsb, .webp, .pst, .z, .dcr, .xmind, .xyp, .arch00, .icxs, .sis, .der, .wsd, .kdb, .wot, .bkf, .mddata, .zw, .iwd, .yml, .xlsx, .blob, .wp4, .png, .xbdoc, .sidd, .sie, .big, .yal, .dba, .odp, .vfs0, .vpp_pc, .wri, wallet, .0, .mlx, .ff, .xld, .wpb, .sidn, .css, .wpl, .zdb, .bc7, .pptx, .zi, .syncdb, .sr2, .itl, .layout, .mef, .m4a, .ybk, .bkp, .ncf
Each file that has been encrypted by Gesd virus will be renamed. It will append the extension ‘.gesd’ at the end of the name of the affected file. Thus, a file named ‘image.jpg’, after it is encrypted, will receive the name ‘image.jpg.gesd’. To encrypt as many files as possible in the minimum time, the virus does not encrypt the entire file, but only its initial part in the amount of 154 kb. Gesd virus encrypts files sequentially, when all files in the directory are encrypted, it places a new file in it. This file is called ‘_readme.txt’ and its contents are shown below.
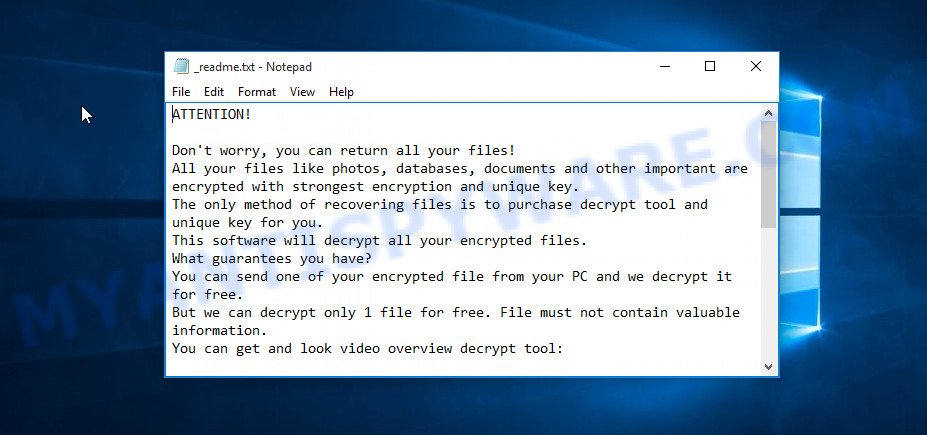
Screenshot of the contents of ‘_readme.txt’ file (Gesd ransom note).
This file is a ransom note that is a message from Gesd creators. In this message, the criminals report that the victim’s files are encrypted and there is only one way to decrypt them – buy the key and the decryptor from them. Attackers set the price for the key and decryptor at $980. If the victim pays the ransom within 72 hours, then Gesd authors agree to make a discount of half the ransom, that is, reduce the size of the ransom to $490. Criminals offer to decrypt one file for free. To do this, the victim needs to send this file to one of the email addresses listed in the ransom demand message. But successful decryption of one file does not guarantee the possibility of decryption of files even after payment of the ransom.
Threat Summary
| Name | Gesd |
| Type | Filecoder, Crypto virus, Crypto malware, Ransomware, File locker |
| Encrypted files extension | .gesd |
| Ransom note | _readme.txt |
| Contact | datarestorehelp@firemail.cc, datahelp@iran.ir |
| Ransom amount | $980/$490 in Bitcoins |
| Detection Names | UDSDangerous: ObjectMultiGeneric, Trojan.Win32: Kryptik, FileRepMalware, TRCrypt.Agent, Malware.Win32.Ransom, TrojanRansom.Win32.Stop, Trojan.Encoder, TrojanRansom.Crypted, RansomWin32.STOP |
| Symptoms | Documents, photos and music encrypted with .gesd file extension. Windows Explorer displays a blank icon for the file type. Files called such as ‘_readme.txt’, and “_readme” in every folder with an encrypted file. |
| Distribution methods | Malicious links in emails. Adware. Drive-by downloads from a compromised webpage. Torrents. Social media, like web-based instant messaging programs. Cracked software. |
| Removal | Gesd virus removal guide |
| Decryption | Free Gesd Decryptor |
In the ransom note, the authors of Gesd virus report that it is impossible to decrypt files without a key and a decryptor. In general, this is true; to decrypt .gesd files, you must use the key and the decryptor. This is confirmed by the security researchers.
As we reported at the very beginning of this article, there is a free decryptor, which in some cases can decrypt .gesd files. In the case when it could not decrypt the files, there are several more methods, each of which can help the victim restore the files encrypted by Gesd virus. These methods do not require the use of a key and decryptor, and therefore are suitable for all victims.
How to remove Gesd virus, Recover, Decrypt .gesd files
If you are a victim of ransomware, your files have been encrypted, then we recommend that you follow the simple steps described above. These steps will help you remove Gesd virus, and decrypt .gesd files that were affected by it. Moreover, we will also show you how to recover encrypted files if the decryption of the files was unsuccessful. Read the entire manual carefully. To make it easier for you to follow the instructions, we recommend that you print it or open it on your smartphone.
- How to remove Gesd ransomware virus
- How to decrypt .gesd files
- How to restore .gesd files
- How to protect your computer from Gesd ransomware virus
How to remove Gesd ransomware virus
The first thing you need to do before decrypting .gesd files is to make sure that Gesd virus is no longer active, as well as find all its components and remove them. An active ransomware is very dangerous because it can encrypt all files that were recovered during decryption. Therefore, you need to check your computer for ransomware and other malware. To do this, we recommend using free malware removal tools that will find Gesd virus and remove it for free.
How to remove Gesd ransomware with Zemana Free
We recommend using a malware removal tool called Zemana AntiMalware because it can find and remove Gesd ransomware, other malware, trojans and worms. If you have any Gesd removal problems, which cannot be fixed by this tool automatically, then Zemana provides 24X7 online assistance from the highly experienced support staff.
Download Zemana Anti-Malware by clicking on the link below.
165094 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
When the downloading process is done, start it and follow the prompts. Once installed, the Zemana Free will try to update itself and when this procedure is finished, press the “Scan” button to perform a system scan with this tool for Gesd virus related folders,files and registry keys.

This task can take quite a while, so please be patient. While the Zemana tool is checking, you may see how many objects it has identified as being infected by malicious software. You may remove items (move to Quarantine) by simply press “Next” button.
The Zemana will begin to delete Gesd ransomware related folders,files and registry keys.
Remove Gesd ransomware with MalwareBytes
MalwareBytes is a malware removal utility. It is created to search for and remove various security threats including ransomware, malware, trojans, worms, adware and so on. MalwareBytes have an advanced system monitoring tool that uses a white-list database to stop suspicious processes and programs.
- First, visit the page linked below, then press the ‘Download’ button in order to download the latest version of MalwareBytes Anti Malware.
Malwarebytes Anti-malware
327319 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
- At the download page, click on the Download button. Your internet browser will show the “Save as” dialog box. Please save it onto your Windows desktop.
- After downloading is done, please close all programs and open windows on your system. Double-click on the icon that’s called mb3-setup.
- This will launch the “Setup wizard” of MalwareBytes Free onto your computer. Follow the prompts and do not make any changes to default settings.
- When the Setup wizard has finished installing, the MalwareBytes Free will launch and display the main window.
- Further, click the “Scan Now” button . MalwareBytes Free program will scan through the whole machine for Gesd ransomware virus and other security threats. This task can take quite a while, so please be patient. While the MalwareBytes Anti Malware (MBAM) program is scanning, you may see count of objects it has identified as threat.
- When MalwareBytes has completed scanning your personal computer, MalwareBytes AntiMalware will show a list of all items detected by the scan.
- When you’re ready, press the “Quarantine Selected” button. When the cleaning process is complete, you may be prompted to restart the system.
- Close the AntiMalware and continue with the next step.
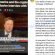
Video instruction, which reveals in detail the steps above.
Remove Gesd ransomware virus with KVRT
Kaspersky virus removal tool (KVRT) is a free malware removal utility that uses the anti-virus engine from Kaspersky antivirus. It can remove ransomware, adware, trojans, worms and other malicious software from your computer for free. You can use this utility to locate and remove security threats even if you have an antivirus or any other security software.
Download Kaspersky virus removal tool (KVRT) from the link below. Save it on your MS Windows desktop.
129312 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
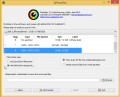
After the download is complete, double-click on the KVRT icon. Once initialization process is complete, you will see the KVRT screen as on the image below.
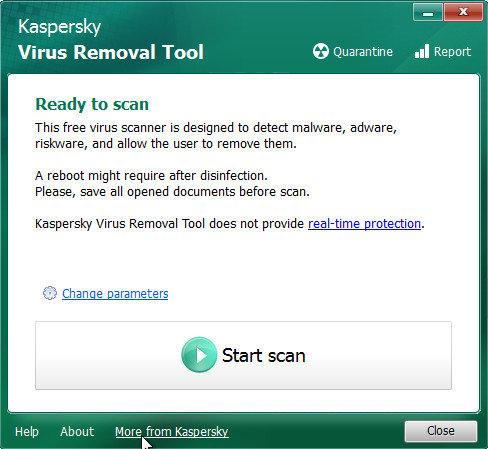
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next press Start scan button to perform a system scan with this utility for Gesd ransomware virus, other trojans and malicious applications. While the Kaspersky virus removal tool tool is scanning, you can see how many objects it has identified as being affected by malware.
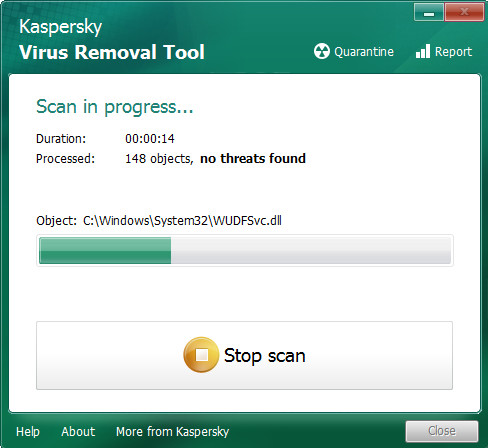
Once the system scan is complete, Kaspersky virus removal tool will prepare a list of unwanted software and ransomware as displayed in the following example.
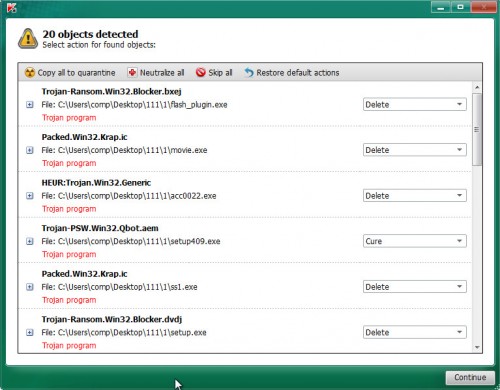
Review the scan results and then click on Continue to start a cleaning procedure.
How to decrypt .gesd files
To decrypt .gesd files, you need to use a unique key and decryptor. Security researchers confirm that it is impossible to access the contents of encrypted files without decryption. Renaming the affected files, changing their extension cannot help the victim, the files will still remain encrypted. Fortunately, Emsisoft created a free decryptor, which in some cases can decrypt .gesd files.
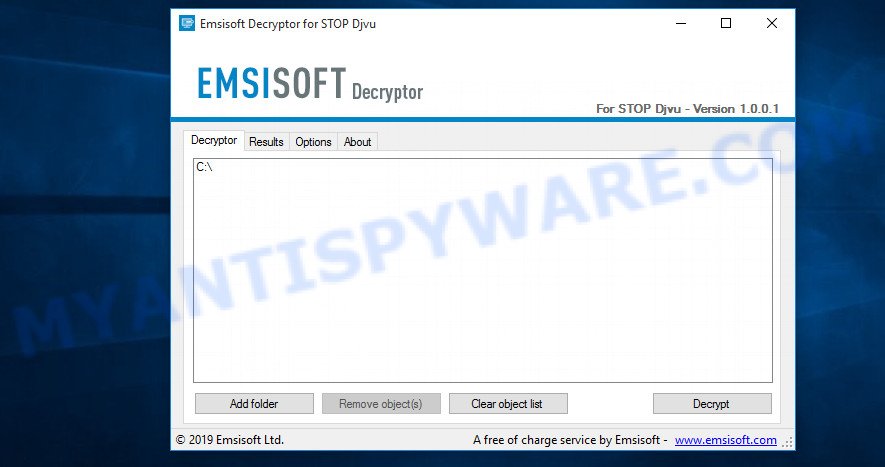
STOP Djvu decryptor
To decrypt .gesd files, use free STOP (Gesd) decryptor
- Download STOP (Gesd) decryptor from the following link.
STOP Djvu decryptor - Scroll down to ‘New Djvu ransomware’ section.
- Click the download link and save the decrypt_STOPDjvu.exe file to your desktop.
- Run decrypt_STOPDjvu.exe, read the license terms and instructions.
- On the ‘Decryptor’ tab, using the ‘Add a folder’ button, add the directory or disk where the encrypted files are located.
- Click the ‘Decrypt’ button.
As we have said several times, this decryptor can decrypt files only in some cases, when the files were encrypted with an ‘offline key’. If the files were encrypted with an ‘online key’, then they cannot be decrypted. The reason for this is that the decryption key is in the hands of criminals and this key can not be determined. But even in this case, there is a chance to restore the contents of encrypted files, we will talk about how to do this a little later.
How to find out which key was used to encrypt files
Below we show two ways to help you determine what type of key was used to encrypt your files. This is very important, since the type of key determines whether it is possible to decrypt .gesd files. We recommend using the second method, as it is more accurate.
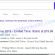
First of all, you can look at the personal ID that is given in the ‘_readme.txt’ file (ransom note).
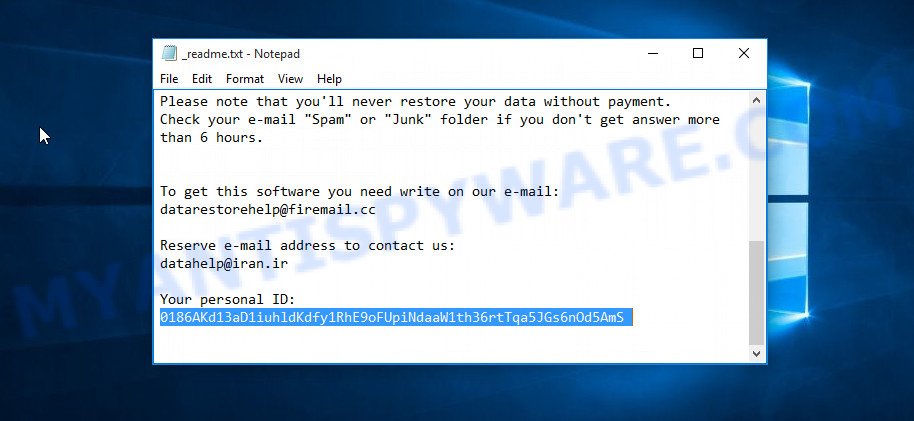
Personal ID is highlighted here
Another way, look on disk ‘C’ for ‘SystemID\PersonalID.txt’ file. This is a file in which Gesd virus stores the Personal IDs used for encryption.
The ‘Personal ID’ is not a key, it is a set of characters by which everyone can find out which key was used to encrypt files. If the ID ends with ‘t1’, then the files are encrypted with an offline key. If the ID does not end with ‘t1’, then Gesd virus used an online key. If you could not understand which key was used to encrypt the files, then we can help you. Just write a request in the comments below.
What to do if STOP (Gesd) decryptor says “Error: Unable to decrypt file with ID”
If during decryption of .gesd files the decryptor reports ‘Error: Unable to decrypt file with ID’, skips files without decrypting them, then two cases are possible why this happens:
- files are encrypted with an ‘online key’, in this case, you need to use alternative methods to restore the contents of encrypted files;
- files are encrypted with an ‘offline key’, but the key itself has not yet been found by security researchers, in this case, you need to be patient and wait a while, in addition, you can also use alternative ways for recovering encrypted data;
How to restore .gesd files
If the free decryptor did not help you, or your files are encrypted using an online key, then there is no need to panic! There are several other alternative methods that may allow you to restore the contents of encrypted files. Once again, remember to be sure to check your computer for ransomware and malware using free malware removal tools. You must be sure that Gesd virus is completely removed.
Each of the methods presented below uses a different mechanism for recovering encrypted files. So try each one. It often happens that if the first method did not help, then the second helped.
Use shadow copies to restore .gesd files
First of all, try to recover .gesd files from Shadow Volume Copies, which are automatically created by Windows OS. In order to recover photos, documents and music encrypted by Gesd virus from Shadow Volume Copies you can use a tool called ShadowExplorer. We recommend using this free utility because it is small in size, has a simple interface and does not require installation on a computer. Unfortunately, ransomware often removes all Shadow copies. Therefore, if Shadow Explorer cannot help you, then immediately proceed to the second method, which is given below.
ShadowExplorer can be downloaded from the following link. Save it on your MS Windows desktop.
439713 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
Once the download is done, extract the downloaded file to a directory on your PC. This will create the necessary files as displayed below.
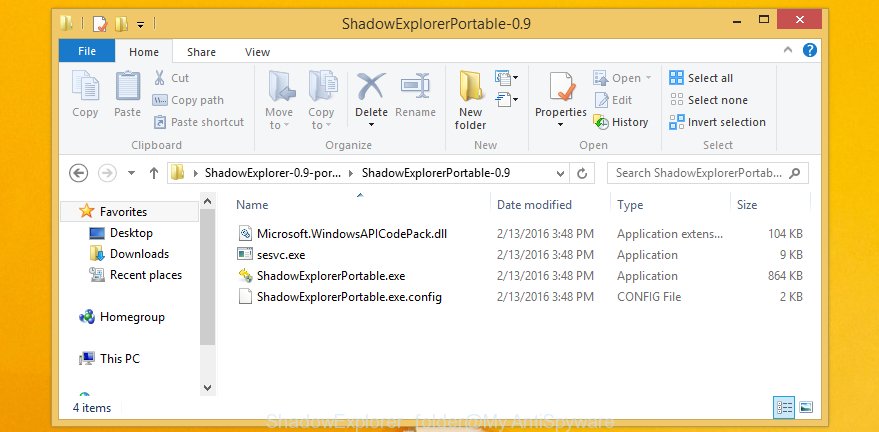
Run the ShadowExplorerPortable program. Now choose the date (2) that you wish to restore from and the drive (1) you wish to recover files (folders) from like below.
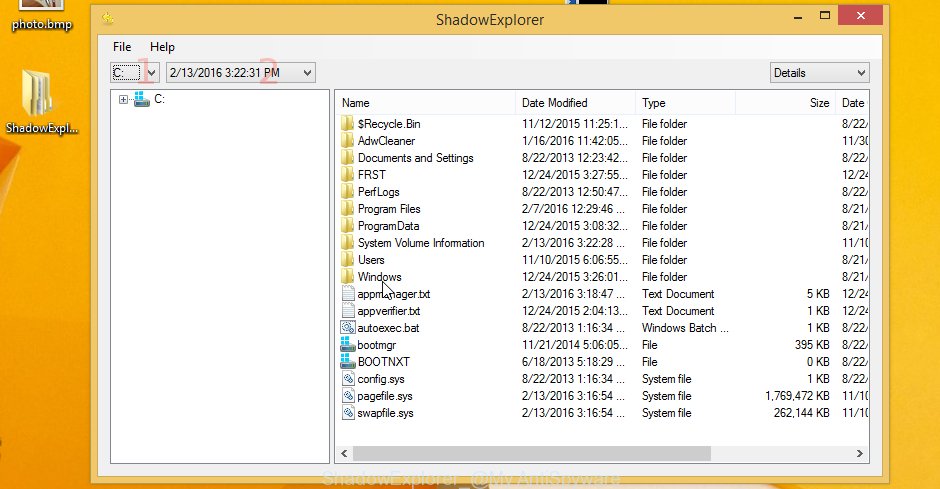
On right panel navigate to the file (folder) you wish to restore. Right-click to the file or folder and click the Export button as displayed in the following example.

And finally, specify a folder (your Desktop) to save the shadow copy of encrypted file and click ‘OK’ button.
Run PhotoRec to recover .gesd files
Another alternative way to recover .gesd files is to use data recovery software. This method requires a lot of time, but in most cases it allows you to recover part, and sometimes all, encrypted files. To restore .gesd files, use a free tool called Photo Rec. It has a simple interface and does not require installation.
Download PhotoRec on your PC from the following link.
Once downloading is complete, open a directory in which you saved it. Right click to testdisk-7.0.win and select Extract all. Follow the prompts. Next please open the testdisk-7.0 folder as displayed below.

Double click on qphotorec_win to run PhotoRec for Microsoft Windows. It will display a screen as shown on the screen below.
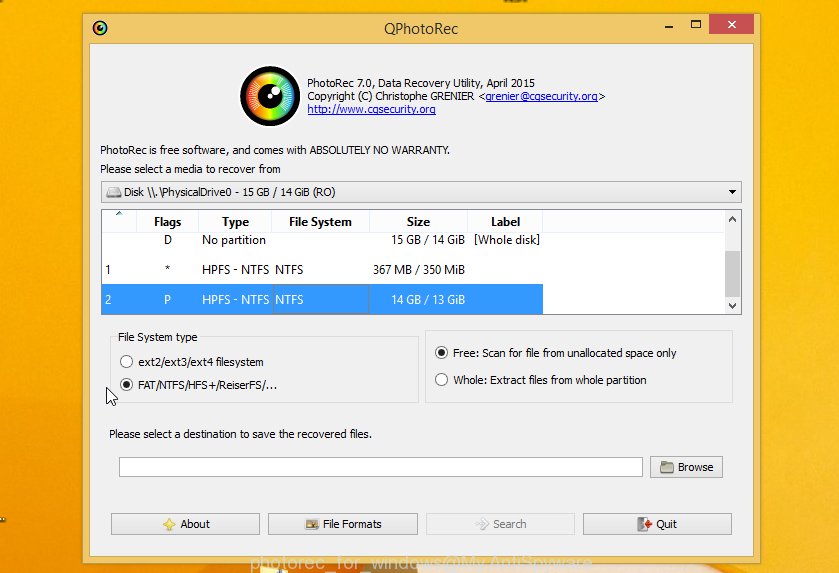
Choose a drive to recover as shown below.
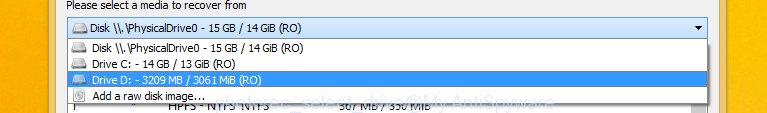
You will see a list of available partitions. Select a partition that holds encrypted photos, documents and music as shown on the screen below.
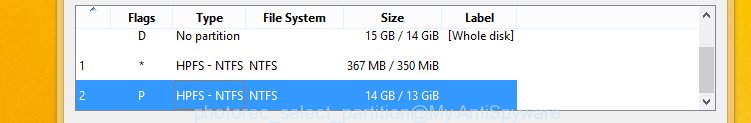
Press File Formats button and choose file types to restore. You can to enable or disable the restore of certain file types. When this is finished, click OK button.
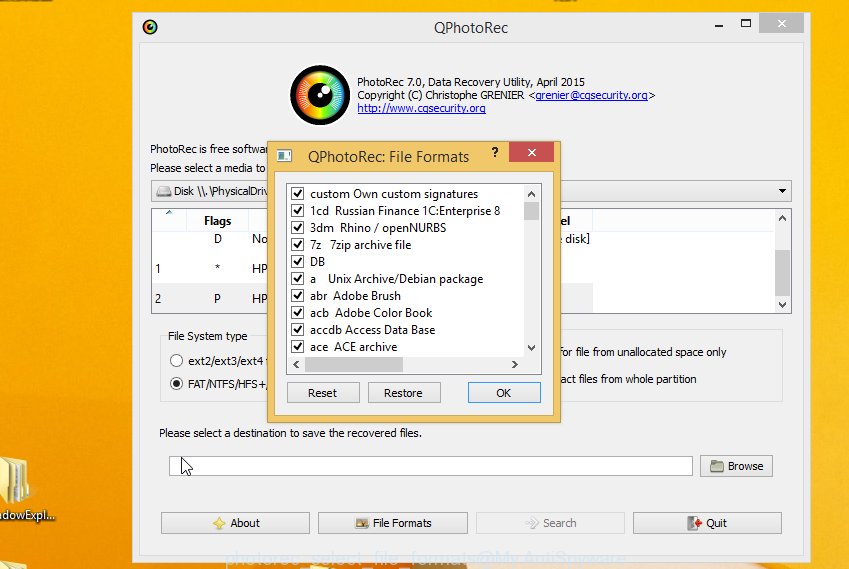
Next, click Browse button to select where restored files should be written, then click Search.
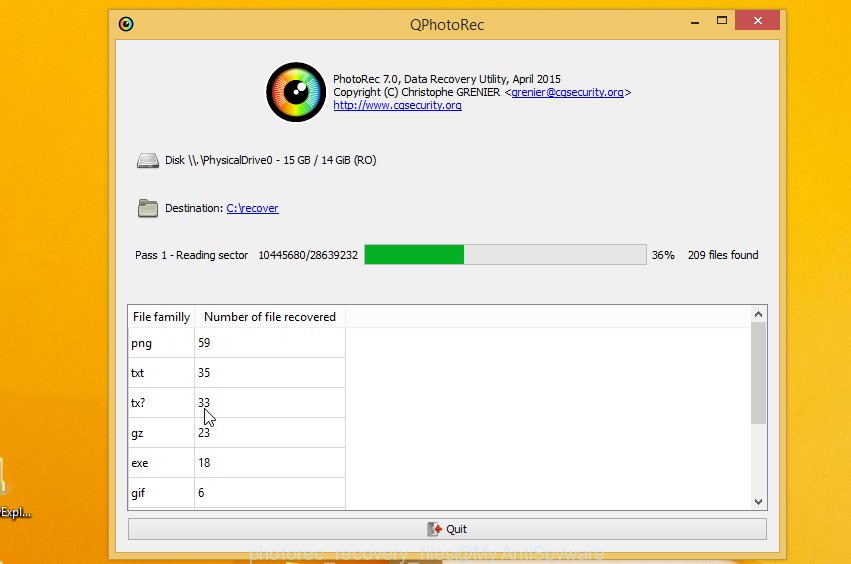
Count of recovered files is updated in real time. All recovered personal files are written in a folder that you have chosen on the previous step. You can to access the files even if the recovery process is not finished.
When the recovery is complete, click on Quit button. Next, open the directory where restored files are stored. You will see a contents as shown below.
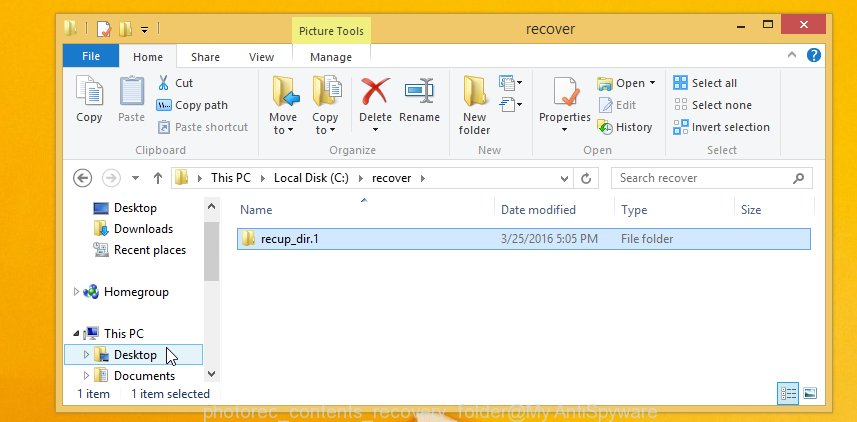
All restored documents, photos and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you’re searching for a specific file, then you can to sort your recovered files by extension and/or date/time.
How to protect your computer from Gesd ransomware virus?
Most antivirus apps already have built-in protection system against ransomware. Therefore, if your machine does not have an antivirus program, make sure you install it. As an extra protection, use the HitmanPro.Alert. All-in-all, HitmanPro.Alert is a fantastic utility to protect your PC from Gesd virus and other ransomware. If ransomware is detected, then HitmanPro.Alert automatically neutralizes malware and restores the encrypted files. HitmanPro.Alert is compatible with all versions of Windows operating system from Windows XP to Windows 10.
HitmanPro Alert can be downloaded from the following link. Save it to your Desktop so that you can access the file easily.
When downloading is finished, open the file location. You will see an icon like below.

Double click the HitmanPro Alert desktop icon. After the tool is launched, you will be shown a window where you can select a level of protection, like below.
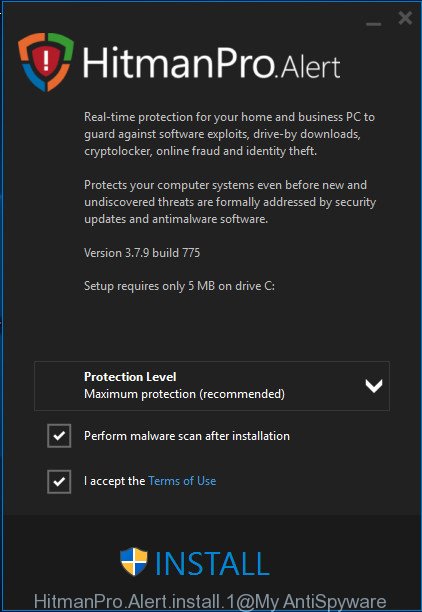
Now click the Install button to activate the protection.
Finish words
This guide was created to help all victims of Gesd ransomware virus. We tried to give answers to the following questions: how to remove ransomware; how to decrypt .gesd files; how to recover files, if STOP (Gesd) decryptor does not help; what is an online key and what is an offline key. We hope that the information presented in this manual has helped you.
If you have questions, then write to us, leaving a comment below. If you need more help with Gesd related issues, go to here.
















thank you… it worked
zF1APaVmnBzImzsIznTwJVMJZBhES0pI3MLefYdN
Can you help me encrypt gesd files with above key. Thanks in anticipation!
The “zF1APaVmnBzImzsIznTwJVMJZBhES0pI3MLefYdN” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the following guide: How to recover ransomware encrypted files.
0191gtd374y5iuhldvhLK1vWmCZPLWXMGW3vzXRq4kLHx8lFLtrJyqvMq
Can you help me encrypt gesd files with above key. please
Dear sir,
Could you please help me the ID below is offline key or online key ?
‘ 0191gtd374y5iuhldl3RftSqya8GLY6XSMtg26QJfeKrIY4K12efPaAx8 ‘
any file in my laptop can not open
how to remove .gesd ransomware
how to decrypt
how to restore my file and can work….
help me please
thanks
Could you help me decrypt my files with, please. many thanks in advance.
ID:
0191gtd374y5iuhlddZgZyk5xYlO1vW1lFGp5pweMMPeBvifO44KBCqbe
0191gtd374y5iuhldvhLK1vWmCZPLWXMGW3vzXRq4kLHx8lFLtrJyqvMq0191gtd374y5iuhldl3RftSqya8GLY6XSMtg26QJfeKrIY4K12efPaAx8
0191gtd374y5iuhlddZgZyk5xYlO1vW1lFGp5pweMMPeBvifO44KBCqbe
These IDs are related to online keys, so files cannot be decrypted. Try to restore the contents of encrypted files using the following guide: How to recover ransomware encrypted files.
Please help me out to restore my files
Your personal ID:
0191gtd374y5iuhld992ZlEktx9f8BO0OpTfqu6fxTo9JySVlarWh8vYG
Could you please help me to dycrypt my files.
ID : 91gtd374y5iuhld4fXsEy8MxPHiuqunWUDRbZPuQEL6IfAxvtzDUjYw
0191gtd374y5iuhld992ZlEktx9f8BO0OpTfqu6fxTo9JySVlarWh8vYG91gtd374y5iuhld4fXsEy8MxPHiuqunWUDRbZPuQEL6IfAxvtzDUjYw
These IDs are related to online keys, so files cannot be decrypted. Try to restore the contents of encrypted files using the following guide: How to recover ransomware encrypted files.
ATTENTION!
Don’t worry, you can return all your files!
All your files like photos, databases, documents and other important are encrypted with strongest encryption and unique key.
The only method of recovering files is to purchase decrypt tool and unique key for you.
This software will decrypt all your encrypted files.
What guarantees you have?
You can send one of your encrypted file from your PC and we decrypt it for free.
But we can decrypt only 1 file for free. File must not contain valuable information.
You can get and look video overview decrypt tool:
hxxps://we.tl/t-063L4ferhE
Price of private key and decrypt software is $980.
Discount 50% available if you contact us first 72 hours, that’s price for you is $490.
Please note that you’ll never restore your data without payment.
Check your e-mail “Spam” or “Junk” folder if you don’t get answer more than 6 hours.
My all files got corrupted please help me out
To get this software you need write on our e-mail:
helprestore@firemail.cc
Reserve e-mail address to contact us:
datarestore@iran.ir
Your personal ID:
0191gtd374y5iuhld992ZlEktx9f8BO0OpTfqu6fxTo9JySVlarWh8vYG
My all files got encrypted and converted to GESD
The “0191gtd374y5iuhld992ZlEktx9f8BO0OpTfqu6fxTo9JySVlarWh8vYG” ID is related to an online key, so files cannot be decrypted. Try to restore the contents of encrypted files using the following guide: How to recover ransomware encrypted files.