‘.Kvag file extension‘ is a sign that your computer has become a victim of ransomware attack. During this attack, the ransomware virus infects the computer and encrypts the files. In each folder where there is at least one encrypted file, the virus creates a document with the name ‘_readme.txt’, which says about the need to contact the authors of the virus to decrypt all encrypted files.
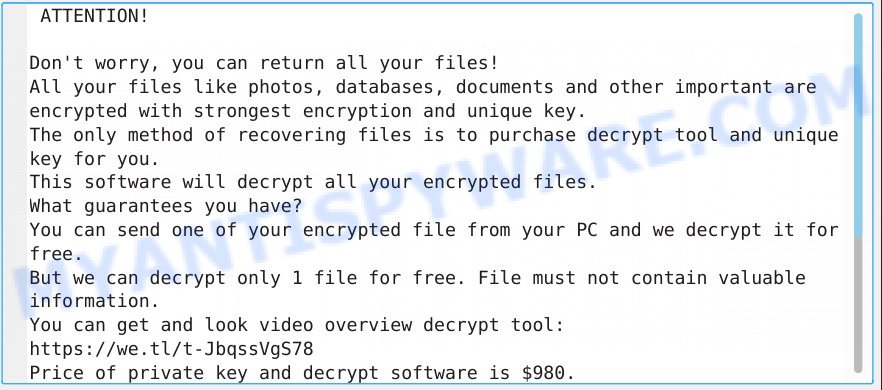
Kvag virus ransomnote
The ransomware encrypts almost all the files that are on the computer. All files that have been encrypted receive a new extension. For example, document.doc after encryption becomes document.doc.kvag. Even if you rename the files and delete the .kvag extension, it will not help you unlock the encrypted files, since the extension is just a sign that the files were encrypted. Experts confirm that the virus can encrypt the following types of files:
.wmv, .wn, .ppt, .hvpl, .xdl, .wbz, .ai, .apk, .wpd, .sidn, .wmf, .wmd, .ff, .xyp, .erf, .sid, .dmp, .xlsm, .m3u, .kdc, .wp7, .xlsx, .odt, .crw, .vpk, .xy3, .bkp, .wotreplay, .tor, .pptm, .cr2, .pdf, .litemod, .cdr, .desc, .sql, .syncdb, .mef, .wp4, .rw2, .xlk, .odp, .epk, .m4a, .svg, .raf, .pkpass, .pst, .arch00, .arw, .orf, .kdb, .jpe, .fsh, .doc, .wmv, .zi, .srf, .wav, .gho, .vtf, .big, .png, .wma, .xxx, .ltx, .rofl, .sr2, .map, .wire, .1, .wgz, .wb2, .rar, .x3f, .rb, .xar, .xmind, .wp, .itm, .dba, .wpb, .bay, .p12, .wma, .sb, .dwg, .zabw, .z, .blob, .fpk, .indd, .xml, .sis, .wsc, .ztmp, .y, .snx, .esm, .xbplate, .gdb, .wbm, .xlgc, .vdf, .asset, .mrwref, .3fr, .das, .wp6, .pak, .1st, .bsa, .lvl, .xpm, .xx, .t13, .wpg, .hkx, .xmmap, .rim, .layout, .qic, .2bp, .pdd, .ysp, .xlsm, .0, .flv, .jpeg, .wcf, .wpl, .p7b, .r3d, .tax, .d3dbsp, .mpqge, .bik, .pptx, .rgss3a, .wbmp, .wmo, .csv, .wsh, .pef, .kf, .menu, .wbc, .wbk, .lbf, .zip, .bar, .itl, .ncf, .eps, .m2, .lrf, .mp4, .psk, .wbd, .iwi, .wri, .xf, .xwp, .3ds, .wp5, .wdp, .xbdoc, .slm, .css, .db0, .webp, .jpg, .xls, .mdf, .pem, .w3x, .zdb, .xlsb, .odm, .hplg, .vfs0, .mddata, .mlx, .sum, .z3d, .wot, .rtf, .srw, .x3f, .bkf, .re4, .ibank, .accdb, .sidd, .wsd, .mcmeta, .wpe, .x3d, .docm, .pfx, .bc7, .cas, .p7c, .ybk, .ntl, .3dm, .dbf, .crt, .wps, .vcf, .wps, .qdf, .xld, .raw, .dazip, .vpp_pc, .txt, .nrw, .t12, .xyw, .wm, .wdb, .upk, .7z, .yal, .docx, .wpt, .cer, .xll, .wpd, .xlsx, .zif, .mdb, .webdoc, .odb, .zdc, .zip, .sav, .dcr, .xls, .wpa, .psd, .forge
As already mentioned, the virus creates a file named ‘_readme.txt’, which contains a message from the authors of the virus. It says that it is possible to decrypt files with .krag extension, for this you need to write a request at the following addresses: gorentos@bitmessage.ch or gerentoshelp@firemail.cc. But you can’t return the files for free, the authors of the virus demand to pay them a ransom in the amount of $980. If the ransom is transferred within 72 hours, then the size of the ransom is halved. In order to confirm the ability to decrypt files, the authors of the ransomware suggest sending them one file, which they will decrypt for free. In addition, they also provide a link (https://we.tl/t-JbqssVgS78) to the video, which shows the process of decrypting files.
Threat Summary
| Name | Kvag virus (ransomware) |
| Type | File locker, Ransomware, Crypto virus, Crypto malware, Filecoder |
| Encrypted files extension | .kvag |
| Ransom note | _readme.txt |
| Contact | gorentos@bitmessage.ch, gerentoshelp@firemail.cc |
| Ransom amount | $980 in Bitcoins |
| Symptoms | Your files fail to open. All of your files have a odd file extension appended to the filenames. Files called such as ‘_readme.txt’, ‘READ-ME’, ‘_open me’, _DECRYPT YOUR FILES’ or ‘_Your files have been encrypted” in every folder with an encrypted file. Ransom note in every directory where there is at least one encrypted file. |
| Distribution methods | Phishing email scam that attempts to scare users into acting impulsively. Drive-by downloading (when a user unknowingly visits an infected webpage and then malware is installed without the user’s knowledge). Social media, like web-based instant messaging programs. USB keys containing malicious software. |
| Removal | To remove Kvag ransomware use the removal guide |
| Decryption | To decrypt Kvag ransomware use the steps |
Unfortunately, at the moment there is no way to decrypt files. Even companies, developers of the best modern antiviruses will not be able to help decrypt files. But there is one way that will allow you to restore .kvag files to their original state. This method is given below in our article.
Quick links
How to remove Kvag ransomware
Before you start recovering encrypted files, you need to find and remove the Kvag virus. Malware removal utilities will help you with this. Even if you have an antivirus program, we recommend that you additionally check your computer. There is one reason for this, you need to be 100% sure that this virus is no longer active.
Remove Kvag with Zemana Anti-Malware
Zemana is a utility that can help you check your computer for malware. This program will scan your computer very quickly and display a list of active malware. After that, you can delete everything found completely free. This program works great with an already installed antivirus, that is, you don’t need to remove or disable your antivirus.
Download Zemana from the following link.
165500 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
Run the downloaded file and install the program on your computer by following the instructions of the Setup wizard. When the installation is complete you will see a window as in the figure below

Press the Scan button and wait for the end of the scanning process.

When the scan is complete, you will see a list of active malware found. Review the report and then click “Next” button.
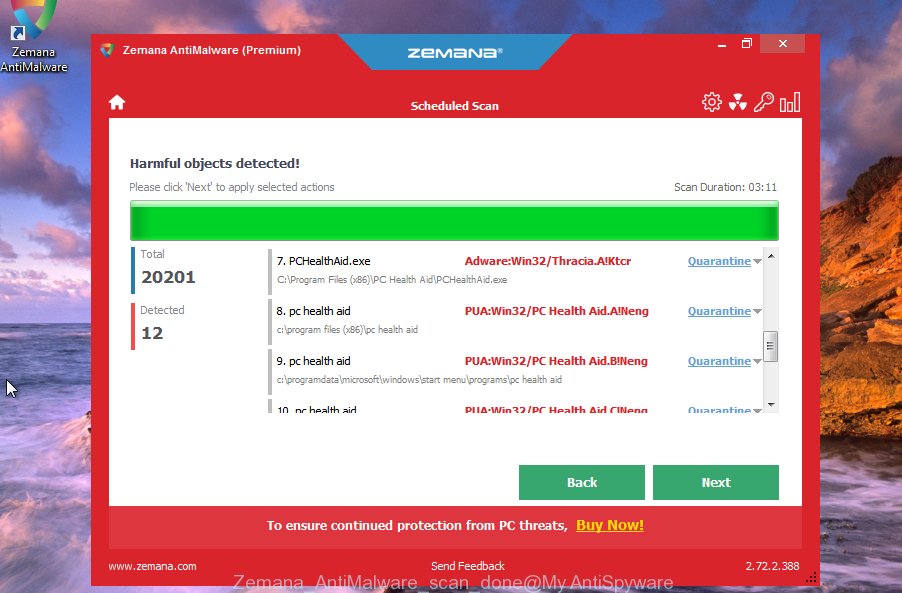
The program will remove the malware and move it to quarantine. You can clear the quarantine later.
How to automatically delete Kvag with MalwareBytes
If you are having problems with the Kvag removal, then try MalwareBytes AntiMalware (it is free for home use).
Download MalwareBytes AntiMalware from the link below.
327717 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
When downloading is finished, close all windows on your computer. Further, open the file named mb3-setup. It will display the “Setup wizard”. Follow the prompts and don’t make any changes to default settings.
Once setup is finished successfully, click Finish button. Then MalwareBytes Anti-Malware (MBAM) will automatically start and you can see its main window as displayed in the following example.
Next, press the “Scan Now” button to perform a system scan. During the scan MalwareBytes Free will detect malicious software exist on your computer.
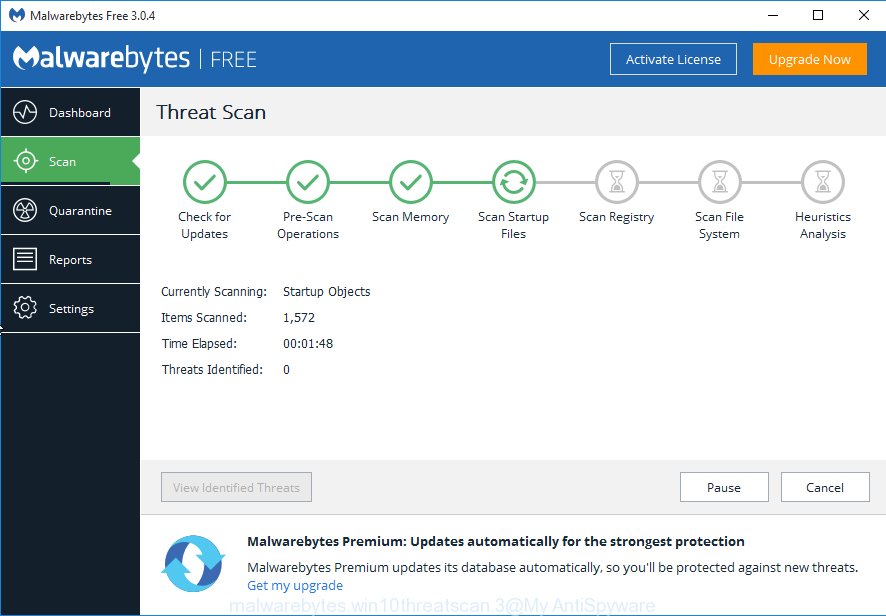
After MalwareBytes Anti Malware (MBAM) has finished scanning your machine, it will open you the results. Now click “Quarantine Selected” button.
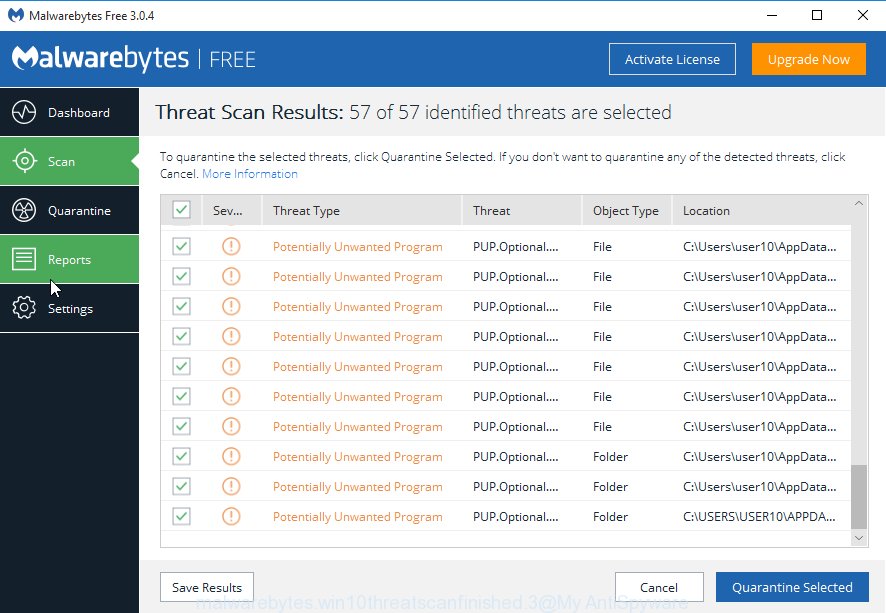
The MalwareBytes Anti Malware (MBAM) will delete Kvag ransomware virus and other security threats. After finished, you can be prompted to reboot your PC system. We recommend you look at the following video, which completely explains the procedure of using the MalwareBytes Free.
If the problem with Kvag is still remained
KVRT is a free removal utility that can check your system for a wide range of security threats including the Kvag crypto malware. Download Kaspersky virus removal tool (KVRT) from the following link.
129491 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
Double-click on the Kaspersky virus removal tool icon. Once initialization procedure is complete, you’ll see a screen such as the one below.
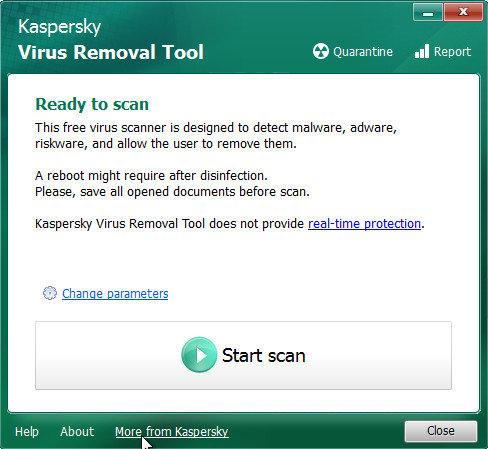
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next press Start scan button.
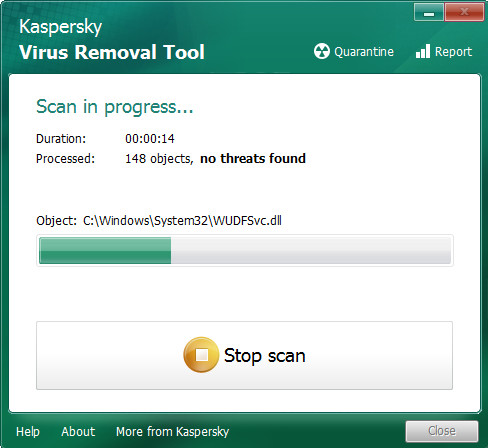
After Kaspersky virus removal tool has completed scanning your system, a list of all threats found is produced as shown in the following example.
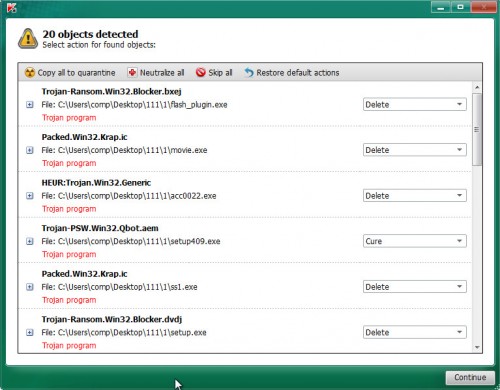
All detected threats will be marked. You can remove them all by simply click on Continue to start a cleaning task.
How to decrypt .kvag files
The first thing every user thinks about when he sees .kvag files and finds out that they are encrypted with a virus – is how to decrypt them. Fortunately, there is one small opportunity to recover all files for free. This method does not require the purchase of any programs, and does not require much knowledge in computers. Everyone can take steps to recover encrypted files.
- We repeat, never pay the ransom. There is no guarantee that the virus developers will be able to decrypt all your files, plus transferring the ransom you will stimulate the creation of new viruses.
- Before you start recovering encrypted files, you need to remove the ransomware.
How to restore .kvag files
Fortunately, it is possible to recover encrypted files. We suggest you try two different ways. But, we can not guarantee that any of the proposed methods will help you.
Recover .kvag files with ShadowExplorer
In some cases, you have a chance to restore your files which were encrypted by the Kvag ransomware virus. This is possible due to the use of the utility called ShadowExplorer. It is a free program which created to obtain ‘shadow copies’ of files.
ShadowExplorer can be downloaded from the following link. Save it on your Desktop.
440038 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
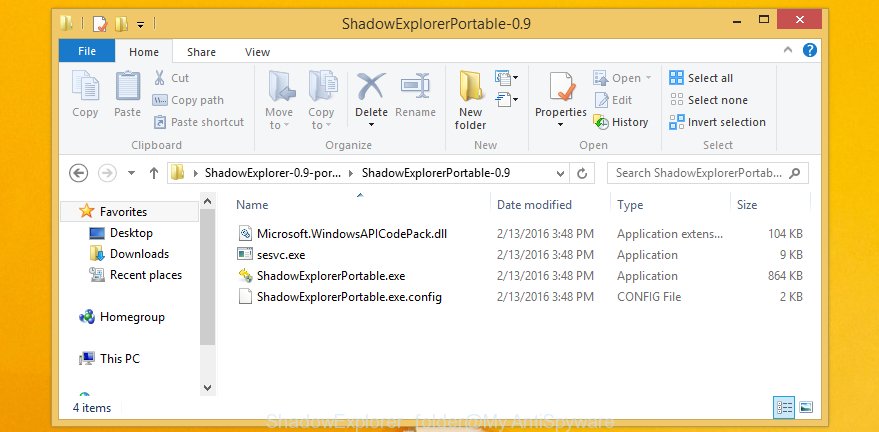
Once the downloading process is complete, extract the downloaded file to a folder on your machine. This will create the necessary files as shown on the image below.
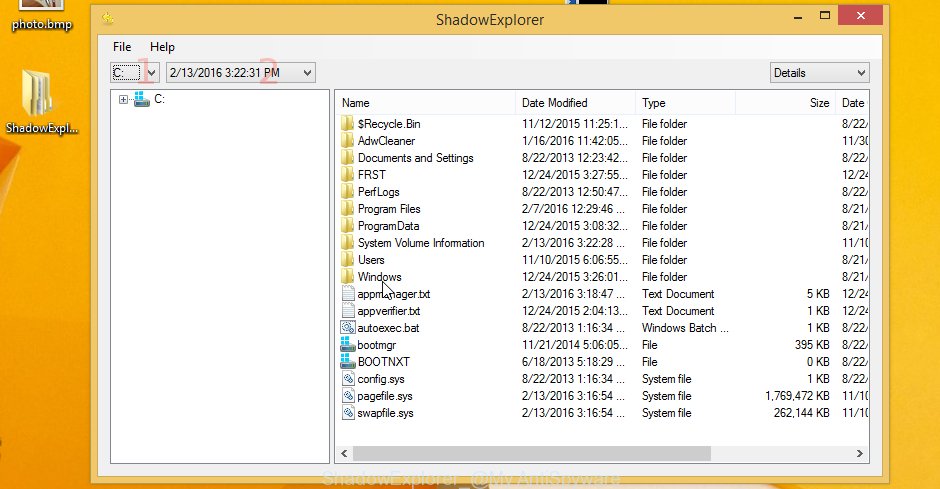
Start the ShadowExplorerPortable program. Now choose the date (2) that you wish to recover from and the drive (1) you want to restore files (folders) from as displayed in the figure below.
On right panel navigate to the file (folder) you want to recover. Right-click to the file or folder and press the Export button like below.

And finally, specify a directory (your Desktop) to save the shadow copy of encrypted file and press ‘OK’ button.
Run PhotoRec to recover .kvag files
Before a file is encrypted, the Kvag ransomware makes a copy of this file, encrypts it, and then deletes the original file. This can allow you to restore your photos, documents and music using file recover apps like PhotoRec.
Download PhotoRec on your Windows Desktop by clicking on the link below.
When the download is finished, open a directory in which you saved it. Right click to testdisk-7.0.win and choose Extract all. Follow the prompts. Next please open the testdisk-7.0 folder similar to the one below.

Double click on qphotorec_win to run PhotoRec for Windows. It will open a screen as shown in the figure below.
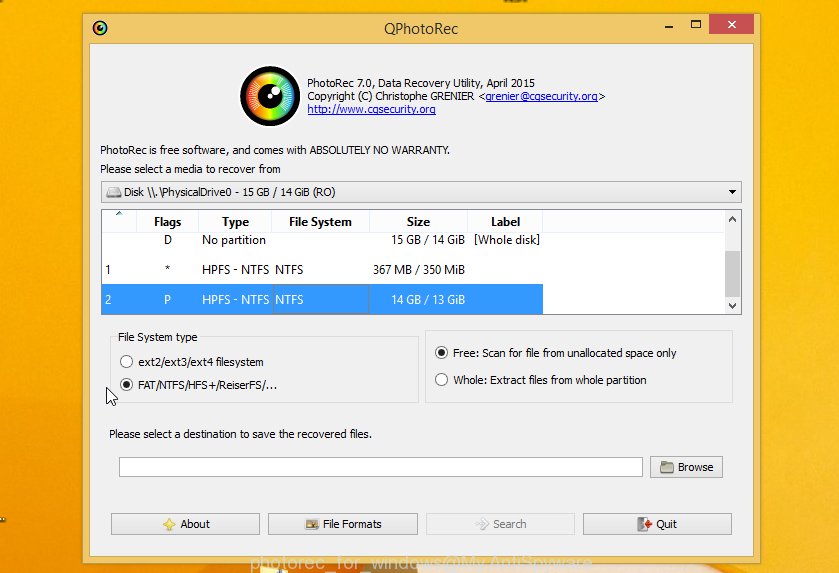
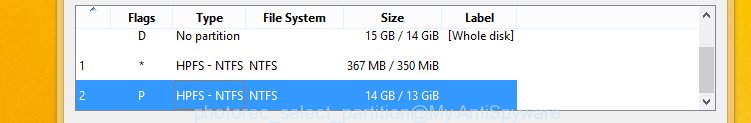
Select a drive to recover as shown in the following example.
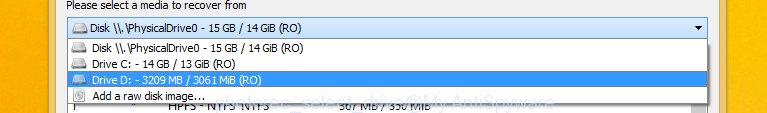
You will see a list of available partitions. Select a partition that holds encrypted photos, documents and music as displayed in the figure below.
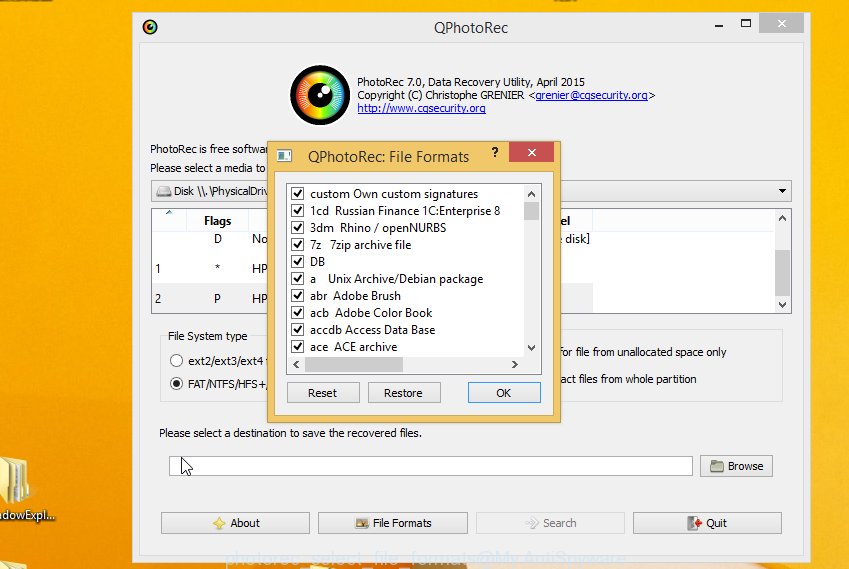
Click File Formats button and specify file types to recover. You can to enable or disable the recovery of certain file types. When this is complete, press OK button.
Next, click Browse button to choose where restored files should be written, then press Search.
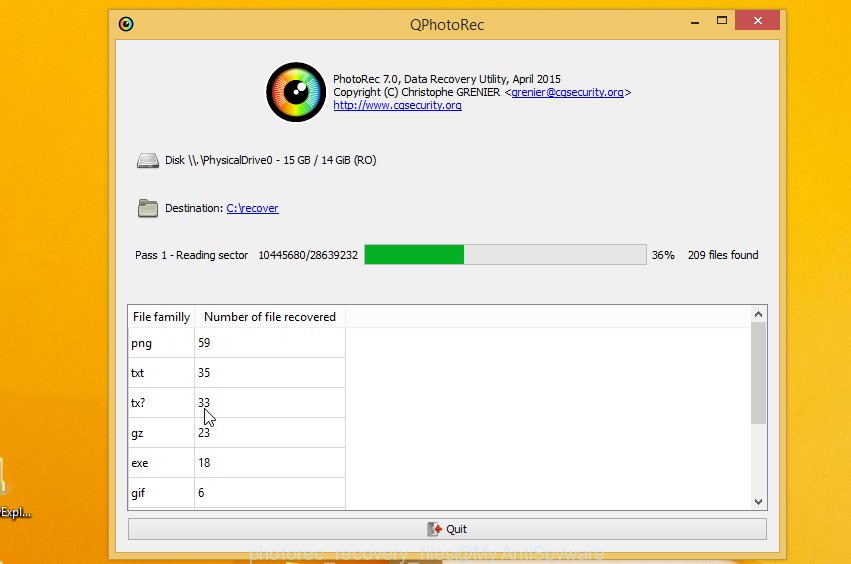
Count of recovered files is updated in real time. All recovered photos, documents and music are written in a folder that you have selected on the previous step. You can to access the files even if the recovery process is not finished.
When the restore is done, click on Quit button. Next, open the directory where recovered personal files are stored. You will see a contents as displayed on the image below.
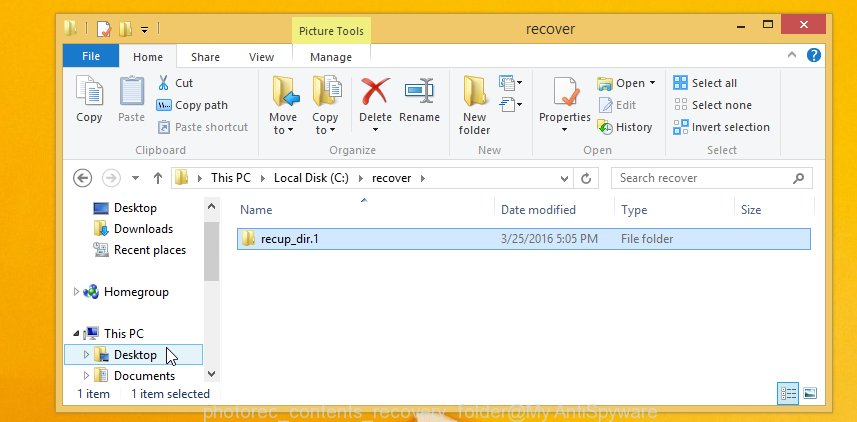
All recovered documents, photos and music are written in recup_dir.1, recup_dir.2 … sub-directories. If you are looking for a specific file, then you can to sort your restored files by extension and/or date/time. In addition, remember that the Windows OS has the ability to search the contents of files.
To sum up
Our team hopes that the instructions and tips shown in our article helped you remove the virus and restore encrypted files. If you need more help with Kvag ransomware related issues, go to here.













this worked with me for the c drive however i couldnt find any shadow copies of my d drive which i have all my photos on.. atleast i saved my work.. thank you very much for posting this.. you can never imagine my gratitude for this article..