One more development of malware of ransomware family is Ingibitor366@cumallover.me ransomware that, like the preexisting malicious programs of this family, is designed to encrypt important documents, photos and music, which will lead to their dysfunction, for the elimination of which the user will have to pay ransom to the online criminals.
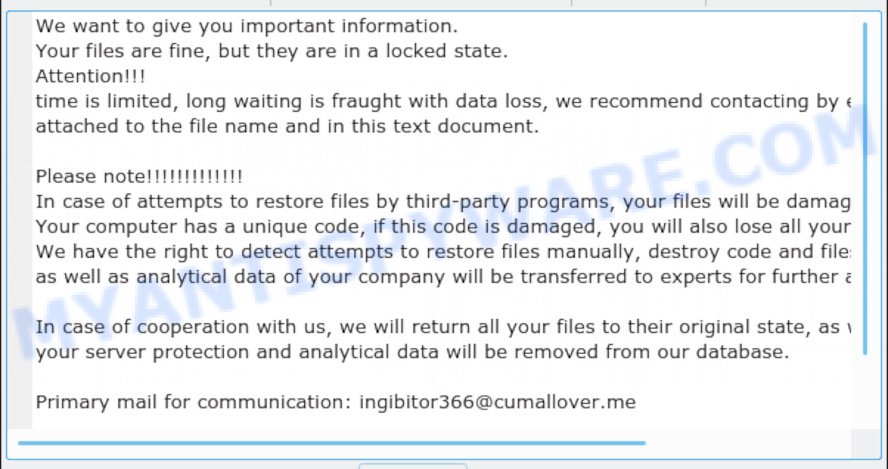
Ingibitor366@cumallover.me virus ransomnote
Getting to the user’s PC, the Ingibitor366@cumallover.me virus starts searching for files in all folders and recursively, and after their detection, locks up each of them using a strong encryption method that completely blocks them and leads to their dysfunction. This ransomware is capable of blocking various files like documents, photos, archives, database, web application-related files, drawings and video materials, as well as its destructive effects can be subjected to backups. Ingibitor366@cumallover.me virus locks up almost of files, including common as:
.odt, .srw, .mrwref, .kdb, .xwp, .map, .db0, .1, .hvpl, .wpg, .wp, .vcf, .hkx, .ltx, .wmf, .forge, .m4a, .layout, .wbd, .wp6, .zip, .sidd, .mpqge, .pak, .wgz, .tax, .wav, .tor, .sql, .bay, .re4, .m3u, .psd, .bkf, .nrw, .xlk, .xld, .accdb, .wma, .mcmeta, .wmd, .z3d, .xls, .wsh, .wmv, .xyw, .hkdb, .xar, .pem, .eps, .itdb, .rofl, .syncdb, .vpk, .dcr, .gho, .wpl, .dwg, .bar, .yal, .odm, .vdf, .xx, .zip, .dbf, .kf, .blob, .css, .ysp, .csv, .odb, .wpd, .ods, .wp4, .0, .xmmap, .wpt, .menu, .wbmp, .arch00, .rb, .kdc, .x, .pptm, .pkpass, .wsc, .wpw, .raf, .ztmp, .2bp, .raw, .esm, .apk, .xlsx, .xll, .desc, .odp, .crw, .psk, .doc, .flv, .sidn, .sum, .yml, .wps, .dxg, .bik, .pfx, .xlgc, .py, .mdf, .hplg, .wp7, .bc6, .d3dbsp, .p7c, .ybk, .fsh, .ff, .jpeg, .y, .crt, .dazip, .docx, .slm, .icxs, .cdr, .das, .wpb, .vpp_pc, .big, .cas, .mdbackup, .wmv, .wpd, .zw, .pdf, .fpk, .t13, .mdb, .docm, .mp4, .wma, .wdp, .wbm, .bkp, .srf, .xlsx, .ptx, .svg, .3dm, .rgss3a, .wm, .wot, .snx, .dng, .zif, .jpg, .itm, .dba, .cr2, .sb, .wotreplay, .zdc, .vtf, .xbplate, .cfr, .xml, .ppt, .zdb, .x3d, .wp5, .vfs0, .xlsb, .z, .wcf, .p12, .wbk, .1st, .xyp, wallet, .erf, .der, .itl, .sid, .lrf, .wb2, .wpe, .xdl, .pef, .txt, .webp, .wsd, .arw, .png, .odc, .wn, .wpa, .upk, .r3d, .x3f, .qdf, .xf, .xlsm, .orf, .w3x, .rwl, .rtf, .mef, .webdoc, .iwd, .ibank, .wbc, .xbdoc, .indd, .litemod, .bsa, .rw2, .ws, .pptx, .sie, .p7b, .epk, .x3f, .ntl, .7z, .pdd, .dmp, .fos, .wdb, .m2, .sis, .zi, .cer, .mov, .wps, .asset, .xxx, .3fr, .qic, .jpe
Upon encryption, all locked files will then be appended with the RT4BLOCK extension (e.g., ‘photo.jpg is renamed to ‘photo.jpg!-information-…___ingibitor366@cumallover.me___….RT4BLOCK’). Ransomware leaves a ransom demanding message named ‘NEWS_INGiBiToR.txt’ with instructions for extortion and ransom payment, threatening destruction of files if payment is not made. The ransom demanding message directs victims to contact to the creators of this ransomware by ingibitor366@cumallover.me email immediately.
We want to give you important information. Your files are fine, but they are in a locked state. Attention!!! time is limited, long waiting is fraught with data loss, we recommend contacting by email immediately attached to the file name and in this text document. Please note!!!!!!!!!!!!! In case of attempts to restore files by third-party programs, your files will be damaged forever! Your computer has a unique code, if this code is damaged, you will also lose all your files! We have the right to detect attempts to restore files manually, destroy code and files irrevocably, as well as analytical data of your company will be transferred to experts for further action! In case of cooperation with us, we will return all your files to their original state, as well as get information on your server protection and analytical data will be removed from our database. Primary mail for communication: ingibitor366@cumallover.me 15 days to reply, after a while the data will be erased
Threat Summary
| Name | Ingibitor366@cumallover.me ransomware |
| Type | Crypto virus, Crypto malware, Filecoder, Ransomware, File locker |
| Encrypted files extension | !-information-…___ingibitor366@cumallover.me___….RT4BLOCK |
| Ransom note | NEWS_INGiBiToR.txt |
| Contact | ingibitor366@cumallover.me |
| Detection Names | Trojan.Encoder.29037, Win32/Filecoder.RotoCrypt.C, Win32:Heim |
| Symptoms | Personal files won’t open. All of your documents, photos and music have a new file extension appended to the filenames. Files called like ‘NEWS_INGiBiToR.txt’, or ‘NEWS_INGiBiToR” in every folder with an encrypted file. |
| Distribution methods | Malicious e-mail spam. Exploit kits (cybercriminals use ransomware packaged in an ‘exploit kit’ that can find a vulnerability in Web-browser, Microsoft Windows OS, PDF reader, Adobe Flash Player). Social media, like web-based instant messaging applications. Malvertising campaigns. |
| Removal | To remove Ingibitor366@cumallover.me ransomware use the removal guide |
| Decryption | To decrypt Ingibitor366@cumallover.me ransomware use the steps |
We recommend you to delete Ingibitor366@cumallover.me ransomware as quickly as possible, until the presence of the ransomware virus has not led to even worse consequences. You need to follow the step-by-step guidance below that will allow you to completely remove Ingibitor366@cumallover.me ransomware from your PC system as well as restore encrypted documents, photos and music, using only few free utilities.
Quick links
- How to remove Ingibitor366@cumallover.me ransomware virus
- How to decrypt RT4BLOCK files
- How to restore RT4BLOCK files
- How to protect your PC system from Ingibitor366@cumallover.me ransomware virus?
How to remove Ingibitor366@cumallover.me crypto virus
The Ingibitor366@cumallover.me crypto malware can hide its components which are difficult for you to find out and uninstall completely. This may lead to the fact that after some time, the ransomware again infect your system and encrypt your documents, photos and music. Moreover, I want to note that it’s not always safe to remove crypto malware manually, if you do not have much experience in setting up and configuring the Microsoft Windows operating system. The best method to scan for and delete Ingibitor366@cumallover.me ransomware virus is to use malware removal programs which are listed below.
How to remove Ingibitor366@cumallover.me virus with Zemana
Zemana Anti-Malware is a complete package of anti-malware utilities that can help you delete Ingibitor366@cumallover.me ransomware virus. Despite so many features, it does not reduce the performance of your computer. Zemana AntiMalware (ZAM) is able to remove almost all the types of ransomware malware as well as trojans, worms, adware, browser hijackers and PUPs. Zemana AntiMalware (ZAM) has real-time protection that can defeat most malicious software and ransomware virus. You can use Zemana with any other anti-virus without any conflicts.
Installing the Zemana is simple. First you will need to download Zemana on your Windows Desktop by clicking on the link below.
165507 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
After the downloading process is done, close all programs and windows on your computer. Double-click the install file named Zemana.AntiMalware.Setup. If the “User Account Control” prompt pops up as shown in the figure below, click the “Yes” button.
It will open the “Setup wizard” which will help you install Zemana Free on your PC system. Follow the prompts and don’t make any changes to default settings.
Once setup is done successfully, Zemana Anti Malware will automatically start and you can see its main screen as displayed in the following example.

Now click the “Scan” button . Zemana program will scan through the whole computer for the Ingibitor366@cumallover.me crypto virus, other kinds of potential threats like malware and trojans. A system scan can take anywhere from 5 to 30 minutes, depending on your PC system. While the Zemana AntiMalware (ZAM) tool is checking, you can see how many objects it has identified as being infected by malicious software.

After finished, Zemana Free will display a scan report. When you’re ready, click “Next” button. The Zemana Free will delete Ingibitor366@cumallover.me crypto virus, other kinds of potential threats like malware and trojans and add items to the Quarantine. When the procedure is done, you may be prompted to restart the machine.
Use MalwareBytes Free to remove Ingibitor366@cumallover.me virus
We suggest using the MalwareBytes Free. You can download and install MalwareBytes Anti-Malware to scan for and remove Ingibitor366@cumallover.me virus from your personal computer. When installed and updated, this free malware remover automatically finds and removes all threats present on the computer.
Visit the following page to download the latest version of MalwareBytes for Microsoft Windows. Save it to your Desktop.
327726 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
When the download is done, close all software and windows on your personal computer. Double-click the install file named mb3-setup. If the “User Account Control” dialog box pops up as displayed in the following example, click the “Yes” button.
It will open the “Setup wizard” which will help you set up MalwareBytes Free on your PC. Follow the prompts and do not make any changes to default settings.
Once install is finished successfully, press Finish button. MalwareBytes Free will automatically start and you can see its main screen as displayed on the image below.
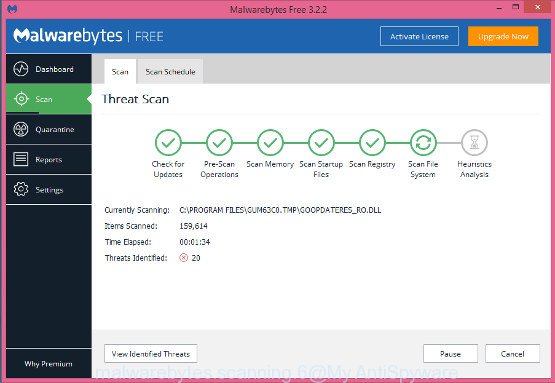
Now click the “Scan Now” button . MalwareBytes Anti-Malware application will scan through the whole PC system for the Ingibitor366@cumallover.me crypto virus and other security threats. A scan can take anywhere from 10 to 30 minutes, depending on the number of files on your PC system and the speed of your PC system. While the MalwareBytes tool is scanning, you can see how many objects it has identified as being infected by malware.
After the scan get completed, MalwareBytes will open a list of all threats found by the scan. All detected threats will be marked. You can remove them all by simply click “Quarantine Selected” button. The MalwareBytes Anti Malware will delete Ingibitor366@cumallover.me ransomware related files, folders and registry keys and add items to the Quarantine. Once finished, you may be prompted to reboot the PC system.
We suggest you look at the following video, which completely explains the process of using the MalwareBytes Anti Malware to remove adware, hijacker infection and other malicious software.
Use KVRT to remove Ingibitor366@cumallover.me ransomware malware from the PC
KVRT is a free portable program that scans your personal computer for malware and ransomware and helps delete them easily. Moreover, it’ll also help you remove any malicious web-browser extensions and add-ons.
Download Kaspersky virus removal tool (KVRT) on your machine by clicking on the following link.
129497 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
Once the download is complete, double-click on the Kaspersky virus removal tool icon. Once initialization procedure is done, you’ll see the Kaspersky virus removal tool screen like below.
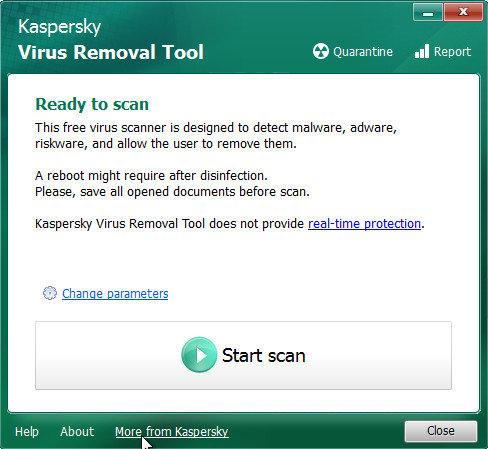
Click Change Parameters and set a check near all your drives. Click OK to close the Parameters window. Next press Start scan button to locate Ingibitor366@cumallover.me ransomware virus . This task may take quite a while, so please be patient. While the KVRT is scanning, you can see how many objects it has identified either as being malware.
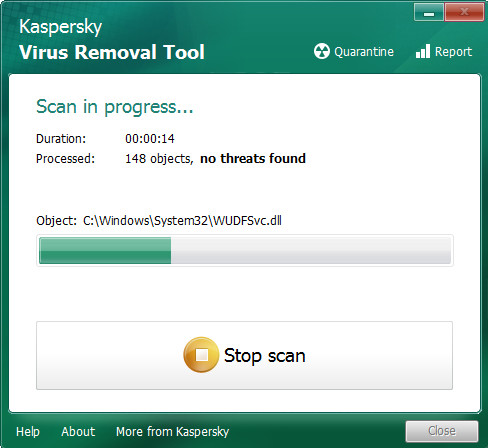
When the checking is finished, it will show the Scan Results as displayed on the image below.
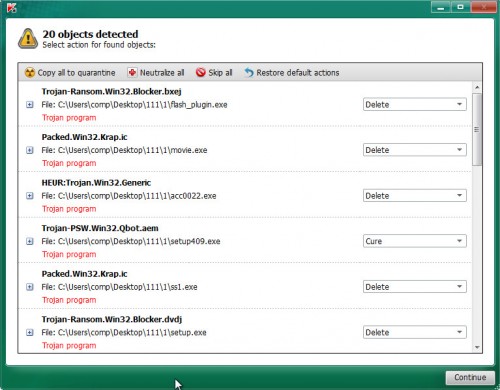
Make sure to check mark the threats that are unsafe and then click on Continue to start a cleaning process.
How to decrypt RT4BLOCK files
As mentioned earlier, the ransom payment is the only way to unlock RT4BLOCK files, unfortunately. After the victim transfers the specified amount of money (usually $300-$1000 in Bitcoins) to the cybercriminals, they provide a special code key to decrypt the affected data.

Never pay the ransom! Some users, wishing to restore access to blocked files, pay the ransom amount of money to scammers. However, it is important to remember before performing this action that you are interacting with unscrupulous and dishonest people, and the probability that after transferring money they will not provide you with a private key and decryption utility to unlock RT4BLOCK files or increase the amount of ransom is high enough.
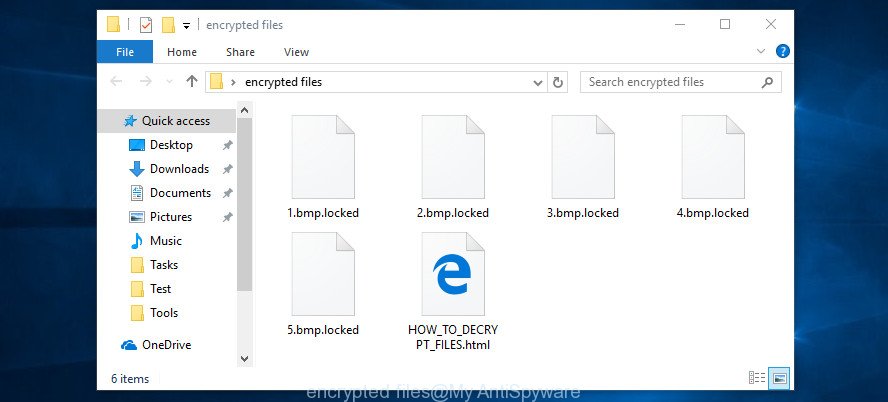
There is no such solution to this problem, which is suitable for everyone. However, paying for the decryption key is not an obvious answer. If you pay for it, remember that no one gives you a guarantee that you will receive it. There is also a possibility that even the attackers themselves do not have this key. Most probably, they are just trying to defraud you and use you in order to get money. You should try the steps in this article. The guide will help you completely remove Ingibitor366@cumallover.me ransomware and you will be able to restore some of the encrypted data without paying any money. Given the fact that fighting crypto malware is incredibly difficult, we cannot promise you that you will defuse it. Nevertheless, it is still worth a try.
How to restore RT4BLOCK files
In some cases, you can restore files encrypted by Ingibitor366@cumallover.me crypto virus. Try both methods. Important to understand that we cannot guarantee that you will be able to restore all encrypted photos, documents and music.
Recover .RT4BLOCK encrypted files using Shadow Explorer
If automated backup (System Restore) is enabled, then you can use it to recover all encrypted files to previous versions.
First, click the link below, then click the ‘Download’ button in order to download the latest version of ShadowExplorer.
440041 downloads
Author: ShadowExplorer.com
Category: Security tools
Update: September 15, 2019
Once the download is finished, extract the downloaded file to a folder on your machine. This will create the necessary files as displayed on the screen below.
Launch the ShadowExplorerPortable program. Now select the date (2) that you want to restore from and the drive (1) you want to recover files (folders) from as displayed in the following example.
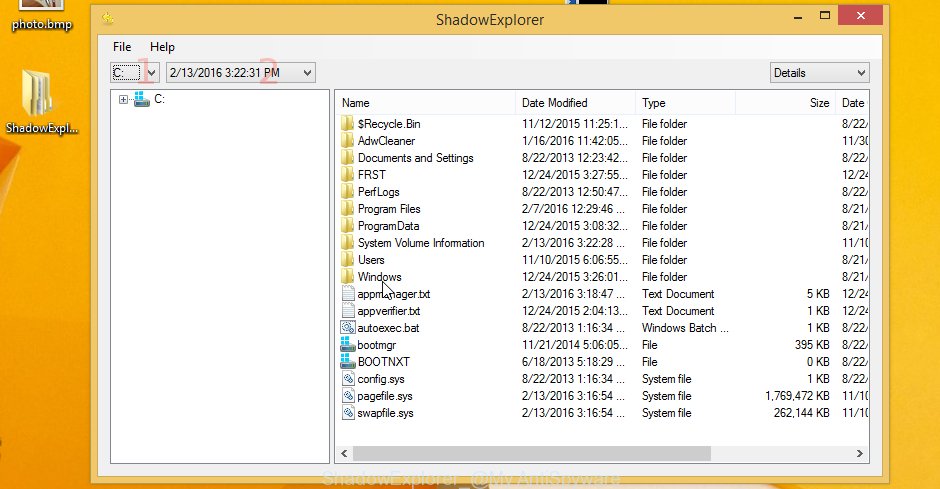
On right panel navigate to the file (folder) you wish to recover. Right-click to the file or folder and click the Export button as on the image below.

And finally, specify a folder (your Desktop) to save the shadow copy of encrypted file and click ‘OK’ button.
Use PhotoRec to restore .RT4BLOCK files
Before a file is encrypted, the Ingibitor366@cumallover.me crypto virus makes a copy of this file, encrypts it, and then deletes the original file. This can allow you to restore your files using file restore apps like PhotoRec.
Download PhotoRec from the link below. Save it on your Microsoft Windows desktop.
After downloading is done, open a directory in which you saved it. Right click to testdisk-7.0.win and choose Extract all. Follow the prompts. Next please open the testdisk-7.0 folder like below.

Double click on qphotorec_win to run PhotoRec for Windows. It will show a screen as displayed below.
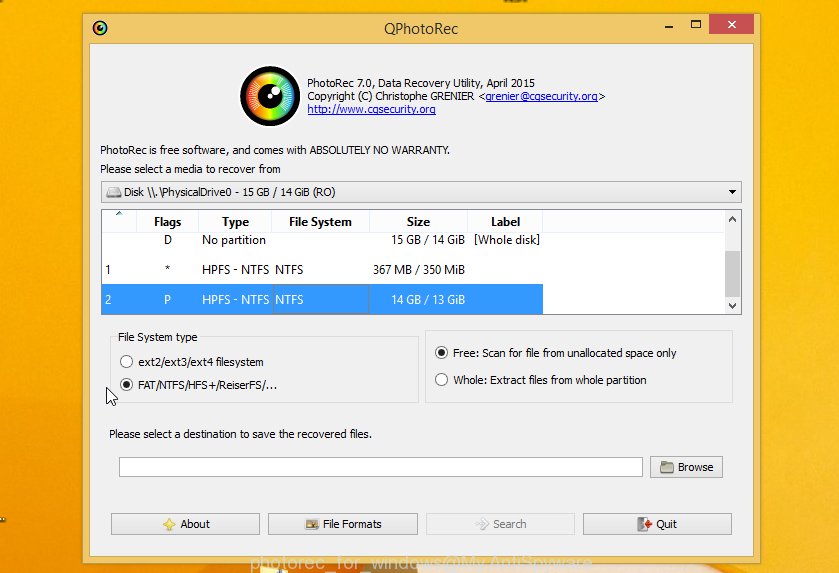
Choose a drive to recover like below.
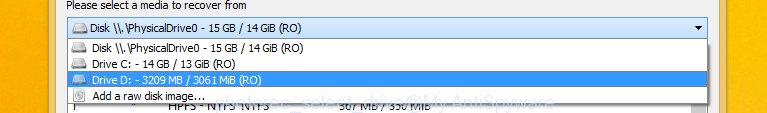
You will see a list of available partitions. Select a partition that holds encrypted documents, photos and music as displayed in the following example.
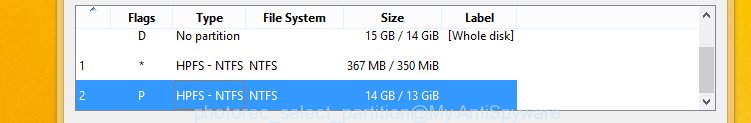
Click File Formats button and specify file types to recover. You can to enable or disable the restore of certain file types. When this is done, press OK button.
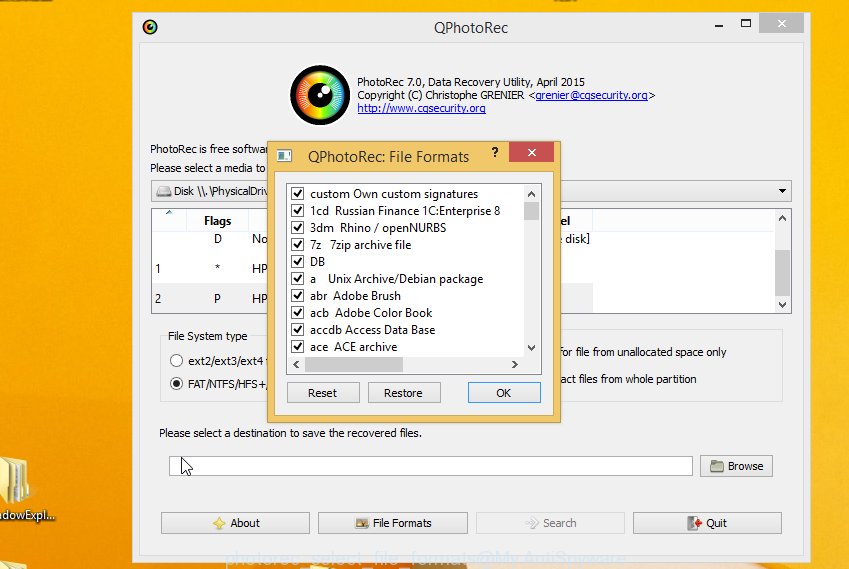
Next, press Browse button to select where recovered photos, documents and music should be written, then click Search.
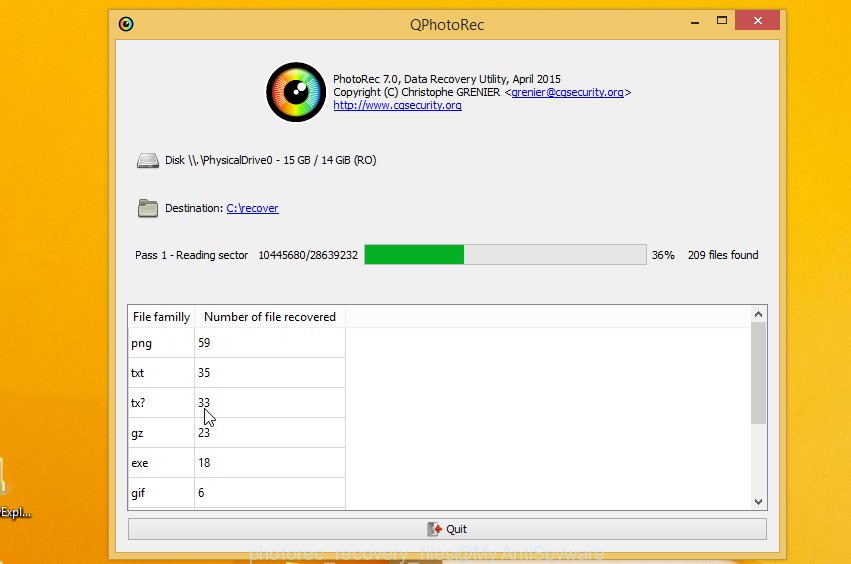
Count of recovered files is updated in real time. All recovered files are written in a folder that you have selected on the previous step. You can to access the files even if the recovery process is not finished.
When the restore is finished, click on Quit button. Next, open the directory where restored files are stored. You will see a contents such as the one below.
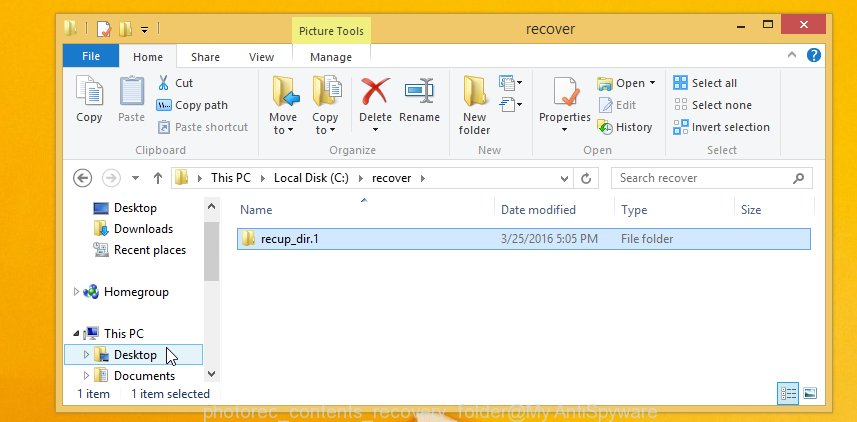
All recovered files are written in recup_dir.1, recup_dir.2 … sub-directories. If you’re searching for a specific file, then you can to sort your restored files by extension and/or date/time.
How to protect your PC system from Ingibitor366@cumallover.me crypto virus?
Most antivirus apps already have built-in protection system against the ransomware. Therefore, if your system does not have an antivirus application, make sure you install it. As an extra protection, run the HitmanPro.Alert.
Run HitmanPro.Alert to protect your machine from Ingibitor366@cumallover.me crypto malware
HitmanPro.Alert is a small security tool. It can check the system integrity and alerts you when critical system functions are affected by malware. HitmanPro.Alert can detect, remove, and reverse ransomware effects.
Download HitmanPro Alert on your Microsoft Windows Desktop from the following link.
Once the downloading process is complete, open the folder in which you saved it. You will see an icon like below.

Double click the HitmanPro.Alert desktop icon. When the tool is started, you’ll be displayed a window where you can choose a level of protection, as displayed on the screen below.
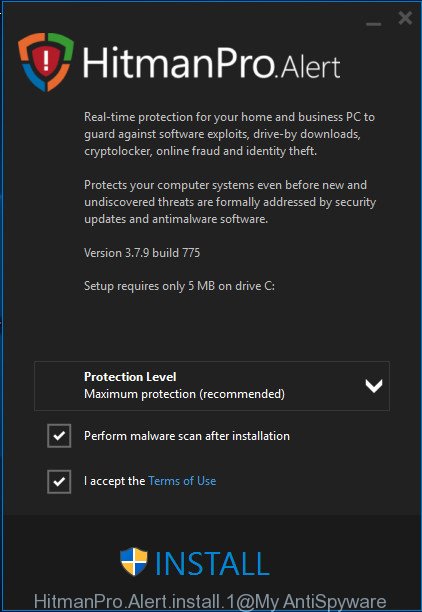
Now press the Install button to activate the protection.
To sum up
Now your computer should be free of the Ingibitor366@cumallover.me ransomware. Delete KVRT and MalwareBytes Anti Malware (MBAM). We recommend that you keep Zemana Free (to periodically scan your PC for new malicious software). Probably you are running an older version of Java or Adobe Flash Player. This can be a security risk, so download and install the latest version right now.
If you are still having problems while trying to remove Ingibitor366@cumallover.me crypto virus from your machine, then ask for help here.