Did you receive an e-mail saying “I have bad news for you. * on this day I hacked your operating system and got full access to your account“? Since you are reading this article, then probably Yes. And here comes the main question: Is the “I hacked your operating system and got full access” mail real? Scary, right? This email is nothing more than a phishing scam.
Thousands of people around the world have received this email spam, so you are one of many. In this fraudulent message the someone claims to have hacked the operating system of your device and took a screenshot of your computer screen while you were engaged in visiting an intimate website, then threats to send the screenshot to everyone in your address book if you don’t pay a $813 ransom through bitcoin (BTC wallet: 17vzpL7n29egdeJF1hvUE4tKV81MqsW4wF).
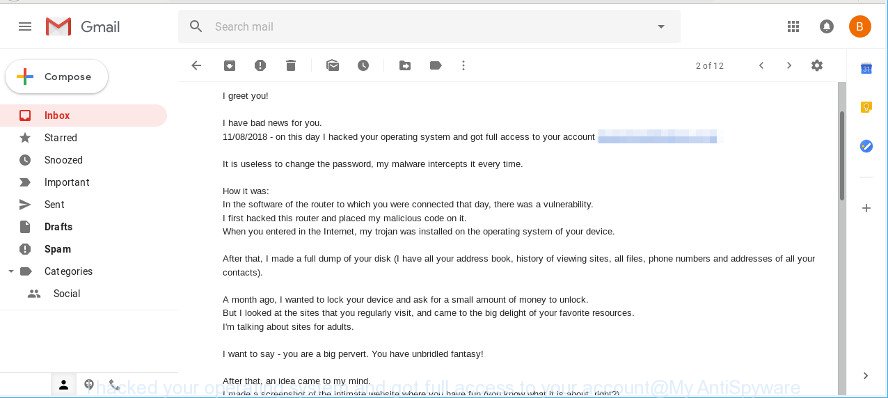
The original “I hacked your operating system” email with the ransom note:
I greet you! I have bad news for you. 11/08/2018 - on this day I hacked your operating system and got full access to your account *** It is useless to change the password, my malware intercepts it every time. How it was: In the software of the router to which you were connected that day, there was a vulnerability. I first hacked this router and placed my malicious code on it. When you entered in the Internet, my trojan was installed on the operating system of your device. After that, I made a full dump of your disk (I have all your address book, history of viewing sites, all files, phone numbers and addresses of all your contacts). A month ago, I wanted to lock your device and ask for a small amount of money to unlock. But I looked at the sites that you regularly visit, and came to the big delight of your favorite resources. I'm talking about sites for adults. I want to say - you are a big pervert. You have unbridled fantasy! After that, an idea came to my mind. I made a screenshot of the intimate website where you have fun (you know what it is about, right?). After that, I took off your joys (using the camera of your device). It turned out beautifully, do not hesitate. I am strongly belive that you would not like to show these pictures to your relatives, friends or colleagues. I think $813 is a very small amount for my silence. Besides, I spent a lot of time on you! I accept money only in Bitcoins. My BTC wallet: 17vzpL7n29egdeJF1hvUE4tKV81MqsW4wF You do not know how to replenish a Bitcoin wallet? In any search engine write "how to send money to btc wallet". It's easier than send money to a credit card! For payment you have a little more than two days (exactly 50 hours). Do not worry, the timer will start at the moment when you open this letter. Yes, yes .. it has already started! After payment, my virus and dirty photos with you self-destruct automatically. Narrative, if I do not receive the specified amount from you, then your device will be blocked, and all your contacts will receive a photos with your "joys". I want you to be prudent. - Do not try to find and destroy my virus! (All your data is already uploaded to a remote server) - Do not try to contact me (this is not feasible, I sent you an email from your account) - Various security services will not help you; formatting a disk or destroying a device will not help either, since your data is already on a remote server. P.S. I guarantee you that I will not disturb you again after payment, as you are not my single victim. This is a hacker code of honor. From now on, I advise you to use good antiviruses and update them regularly (several times a day)! Don't be mad at me, everyone has their own work. Farewell.
This email spam appears to be sent from your own email address, giving the perception of being legitimate. Spammers use your email address to commit your mailbox is hacked (such as potential identity theft). But do not be fooled. Email spoofing has been around for a long time! Scammers use it in phishing attacks to force users into thinking they have received mail message from a friend or trusted person.
Threat Summary
| Name | “I hacked your operating system and got full access” EMAIL SCAM |
|---|---|
| Type | Bitcoin Blackmail Scam |
| Ransom amount | $813 |
| Variants | |
| Distribution method | spam email campaigns |
What to do when you receive the “I hacked your operating system and got full access” EMAIL SCAM
We advice to someone who gets this email scam:
- Do not panic.
- Scammers try to scare you and make you pay a ransom. We recommend you do not pay a ransom, because your payment will only increase attacks against you.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/
- Scan your computer for malware.
- Install an anti-phishing software.
How can you protect your security and privacy online?
It might be smart to change passwords for all important accounts, remove any suspicious and unknown programs, install Anti-Phishing Protection software, perform a scan your personal computer for malware, spyware and adware. Follow the step-by-step guide below for more tips on how to protect your security and privacy online.
- Uninstall dubious applications using Microsoft Windows Control Panel
- Protect your security and privacy online with Malwarebytes
- Run AdBlocker to stay safe online
Uninstall dubious applications using Microsoft Windows Control Panel
Go into the MS Windows “Control Panel”, then “Uninstall a program” console. Take a look at the list of programs on your machine and see if there are any suspicious and unknown applications. If you see any, you need to remove them. Of course, before doing so, you can do an Web search to find details on the program. If it is a potentially unwanted program, ad supported software or malicious software, you will likely find information that says so.
Windows 8, 8.1, 10
First, click the Windows button
Windows XP, Vista, 7
First, press “Start” and select “Control Panel”.
It will display the Windows Control Panel like below.
Next, click “Uninstall a program” ![]()
It will show a list of all applications installed on your PC. Scroll through the all list, and uninstall any suspicious and unknown programs.
Protect your security and privacy online with Malwarebytes
We suggest using the MalwareBytes Anti-Malware (MBAM). You can download and install MalwareBytes Free to protect your security and privacy online. When installed and updated, this free malicious software remover automatically identifies and removes all security threats present on the computer.
MalwareBytes Free can be downloaded from the following link. Save it to your Desktop so that you can access the file easily.
327294 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
When the downloading process is done, close all programs and windows on your PC system. Open a directory in which you saved it. Double-click on the icon that’s called mb3-setup as displayed below.
![]()
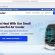
When the installation starts, you will see the “Setup wizard” which will help you install Malwarebytes on your machine.
Once installation is done, you will see window as displayed in the figure below.
Now press the “Scan Now” button to perform a system scan for potential security threats. A system scan can take anywhere from 5 to 30 minutes, depending on your personal computer.
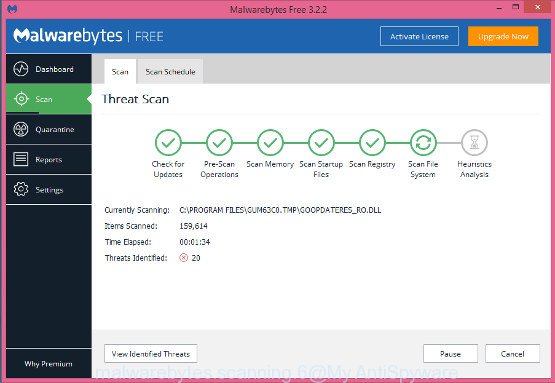
After MalwareBytes Anti Malware (MBAM) has finished scanning your PC, MalwareBytes Free will display a scan report. In order to remove all items, simply click “Quarantine Selected” button.
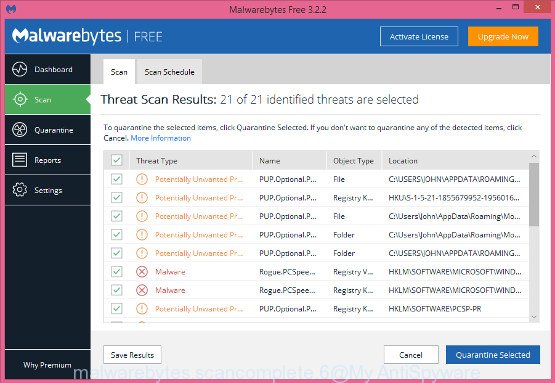
The Malwarebytes will now remove all security threats. After finished, you may be prompted to restart your computer.
The following video explains few simple steps on how to remove any security threats with MalwareBytes AntiMalware.
Run AdBlocker to stay safe online
In order to increase your security and protect your PC system against misleading, phishing and malicious websites, you need to run ad blocker application that stops an access to harmful web pages. Moreover, the application can block the display of annoying ads, which also leads to faster loading of web-pages and reduce the consumption of web traffic.
Installing the AdGuard is simple. First you’ll need to download AdGuard by clicking on the link below. Save it on your Desktop.
26904 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, start the downloaded file. You will see the “Setup Wizard” screen like below.
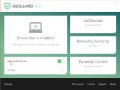
Follow the prompts. When the installation is complete, you will see a window as displayed on the image below.

You can press “Skip” to close the installation application and use the default settings, or click “Get Started” button to see an quick tutorial that will help you get to know AdGuard better.
In most cases, the default settings are enough and you don’t need to change anything. Each time, when you start your system, AdGuard will start automatically and stop unwanted ads, as well as harmful, phishing or misleading web pages. For an overview of all the features of the program, or to change its settings you can simply double-click on the AdGuard icon, that can be found on your desktop.











This is the main account: blockchain.com/btc/address/3GSB5QGszUXX8ELp34EzoPeye8P7pVcWta
09/18/2018 – $100 000
This may be a letter sent by a program, in other words, it is not a virus but a scam.
This is a big internet SCAM not spam.
i received this email today