If your antivirus detects Exploit:HTML/Phominer.A then it indicates that your computer is infected with a malicious software. This unwanted software usually come with some freeware or from malicious websites that ask users to download and run a Flash Player or Java update. Once started, the malware will be configured to start automatically when Windows starts. It may display lots of unwanted popup ads, inject malicious code into web pages that you are opening in your web browser, hijack the web-browser’s settings such as homepage and search engine, and so on.
Common symptoms of malware infection
If you still are not sure that your computer is infected with this adware, then check your computer for the common symptoms of the infection:
- Your browser displays banner ads where previously you have never seen
- Google Chrome, Mozilla Firefox and Microsoft Internet Explorer (Edge) shows a lot of annoying advertisements
- Web browser’s settings such as homepage and default search engine are hijacked
- Your an antivirus or antispyware software detects an infection
- Internet connection may be slow
Don’t panic because we have got the solution. Here’s a instructions on how to remove any malware and thereby get rid of Exploit:HTML/Phominer.A threat from your computer for free.
How to remove Exploit:HTML/Phominer.A
Even if you’ve the up-to-date classic antivirus installed, and you’ve checked your personal computer for malware and removed anything found, you need to do the guidance below. The Exploit HTML/Phominer.A removal is not simple as installing another antivirus. Classic antivirus programs are not developed to run together and will conflict with each other, or possibly crash MS Windows. Instead we recommend complete the steps below, run Zemana and Malwarebytes Anti-malware, which are free software dedicated to find and remove malware. Use these utilities to ensure any malware is removed.
- Scan your computer with Zemana
- Scan your computer with MalwareBytes Anti-malware
- Disinfect browser’s shortcuts
- Protect your computer from annoying ads and malicious sites
Scan your computer with Zemana
We suggest using the Zemana Anti-malware which are completely clean your PC system of Exploit:HTML/Phominer.A and other malware. The utility is an advanced malicious software removal program designed by (c) Zemana lab. It’s able to help you delete potentially unwanted software, hijackers, malware, toolbars, ransomware and adware that causes tons of intrusive Exploit HTML/Phominer.A pop-ups.
Download Zemana Anti-Malware on your PC from the link below. Save it on your Windows desktop or in any other place.
165069 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
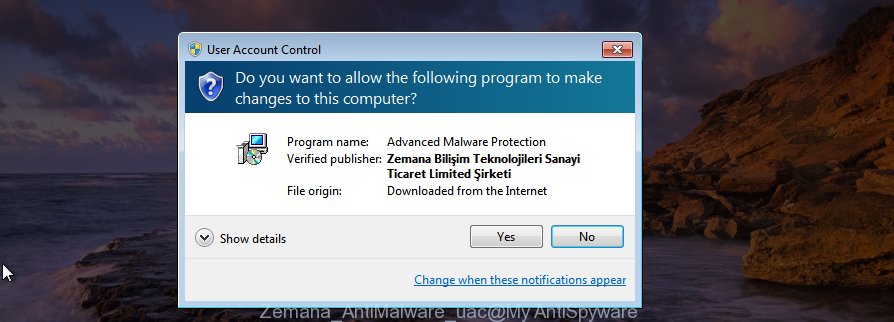
When downloading is complete, close all software and windows on your system. Double-click the install file named Zemana.AntiMalware.Setup. If the “User Account Control” prompt pops up as on the image below, click the “Yes” button.
It will open the “Setup wizard” that will help you setup Zemana AntiMalware on your computer. Follow the prompts and don’t make any changes to default settings.
Once install is done successfully, Zemana Anti Malware will automatically start and you can see its main screen like below.

Now click the “Scan” button to perform a system scan for various malicious software. A scan can take anywhere from 10 to 30 minutes, depending on the number of files on your PC and the speed of your PC system. While the application is scanning, you can see count of objects it has identified as threat.

When that process is finished, you’ll be shown the list of all detected items on your computer. When you’re ready, click “Next” button. The Zemana Anti-Malware will start to get rid of Exploit HTML/Phominer.A and other malware. When that process is done, you may be prompted to restart the machine.
Scan your computer with MalwareBytes Anti-malware
Get rid of Exploit HTML/Phominer.A is difficult and often the malware is not completely removed. Therefore, we recommend you to run the Malwarebytes Free which are completely clean your computer. Moreover, the free program will help you to remove malicious software, PUPs, toolbars and hijackers that your computer may be infected too.
Download Malwarebytes on your PC system by clicking on the link below. Save it on your Windows desktop or in any other place.
327294 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
Once the downloading process is finished, close all applications and windows on your computer. Double-click the set up file called mb3-setup. If the “User Account Control” dialog box pops up as shown on the image below, click the “Yes” button.

It will open the “Setup wizard” that will help you install Malwarebytes on your computer. Follow the prompts and don’t make any changes to default settings.

Once installation is finished successfully, click Finish button. Malwarebytes will automatically start and you can see its main screen as on the image below.
Now click the “Scan Now” button for scanning your computer for Exploit HTML/Phominer.A and other malware. This process may take quite a while, so please be patient. While the utility is scanning, you can see number of objects and files has already scanned.
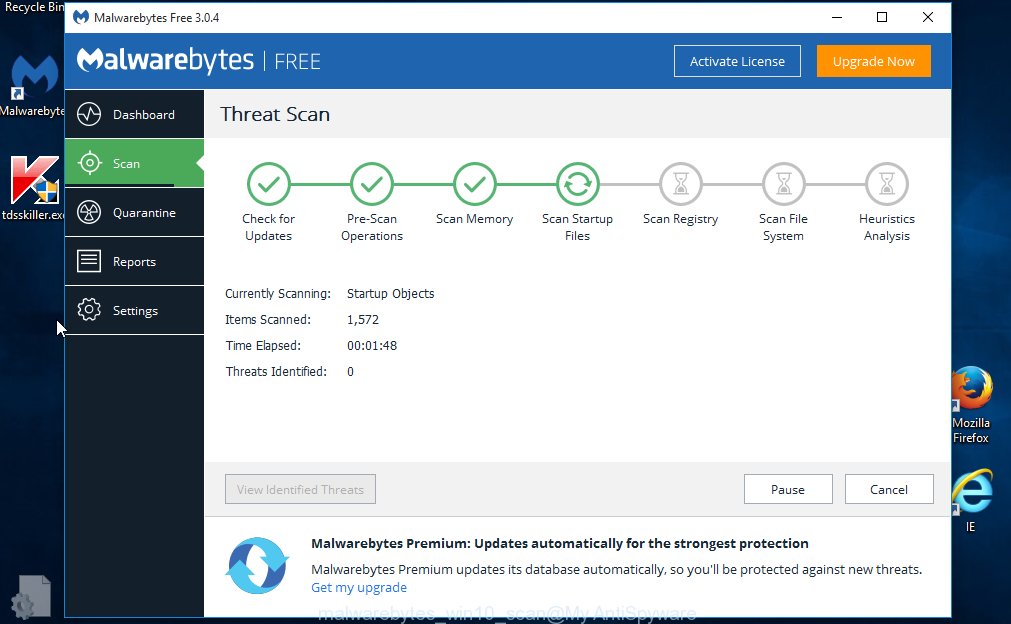
Once that process is finished, it’ll open a list of found threats. When you are ready, click “Quarantine Selected” button. The Malwarebytes will begin to remove malicious software. Once the cleaning procedure is done, you may be prompted to reboot the computer.
We recommend you look at the following video, which completely explains the process of using the Malwarebytes to get rid of adware, browser hijacker and other malware.
Disinfect browser’s shortcuts
After the malware is started, it can also alter the web browser’s shortcuts, adding an argument such as “http://site.address” into the Target field. Due to this, every time you start the web browser, it will show an annoying web site.
Right click to a desktop shortcut for your web browser. Choose the “Properties” option. It will open the Properties window. Select the “Shortcut” tab here, after that, look at the “Target” field. The ad-supported software can change it. If you are seeing something similar “…exe http://site.address” then you need to remove “http…” and leave only, depending on the internet browser you are using:
- Google Chrome: chrome.exe
- Opera: opera.exe
- Firefox: firefox.exe
- Internet Explorer: iexplore.exe
Look at the example as shown on the image below.

Once is finished, click the “OK” button to save the changes. Please repeat this step for web-browser shortcuts which redirects to an annoying web sites. When you have completed, go to next step.
Protect your computer from annoying ads and malicious sites
It is also critical to protect your web-browsers from harmful web-sites and pop-ups by using an adblocker program like AdGuard. Security experts says that it will greatly reduce the risk of malicious software, and potentially save lots of money. Additionally, the AdGuard can also protect your privacy by blocking almost all trackers.
Download AdGuard program by clicking on the following link.
26904 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After the download is finished, run the downloaded file. You will see the “Setup Wizard” screen as shown in the figure below.
Follow the prompts. After the install is complete, you will see a window as shown on the screen below.

You can press “Skip” to close the install application and use the default settings, or click “Get Started” button to see an quick tutorial which will assist you get to know AdGuard better.
In most cases, the default settings are enough and you do not need to change anything. Each time, when you run your computer, AdGuard will start automatically and stop popups, as well as other harmful or misleading web sites. For an overview of all the features of the program, or to change its settings you can simply double-click on the AdGuard icon, that may be found on your desktop.
Finish words
After completing the step-by-step instructions above, your machine should be clean from Exploit:HTML/Phominer.A, malware and other unwanted software. Your antivirus will no longer detect Exploit HTML/Phominer.A threat. Unfortunately, if the few simple steps does not help you, then you have caught a new malware, and then the best way – ask for help.
- Download HijackThis from the link below and save it to your Desktop.
HijackThis download
5007 downloads
Version: 2.0.5
Author: OpenSource
Category: Security tools
Update: November 7, 2015
- Double-click on the HijackThis icon. Next click “Do a system scan only” button.
- As the scanning ends, the scan button will read “Save log”, press it. Save this log to your desktop.
- Create a Myantispyware account here. Once you’ve registered, check your e-mail for a confirmation link, and confirm your account. After that, login.
- Copy and paste the contents of the HijackThis log into your post. If you are posting for the first time, please start a new thread by using the “New Topic” button in the Spyware Removal forum. When posting your HJT log, try to give us some details about your problems, so we can try to help you more accurately.
- Wait for one of our trained “Security Team” or Site Administrator to provide you with knowledgeable assistance tailored to your problem with the Exploit HTML/Phominer.A threat.