 XP Security Tool 2010 or XP Security Tool is an updated version of earlier appeared XP Internet Security 2010, which is a rogue antispyware program. Both programs are identical except for their names and partially modified executable files, which is necessary in order to remain undetected by legitimate antispyware and antivirus applications. As before, this malware uses trojans to install itself. When the trojan is started, it will download and install XP Security Tool 2010 onto your computer with your permission and knowledge.
XP Security Tool 2010 or XP Security Tool is an updated version of earlier appeared XP Internet Security 2010, which is a rogue antispyware program. Both programs are identical except for their names and partially modified executable files, which is necessary in order to remain undetected by legitimate antispyware and antivirus applications. As before, this malware uses trojans to install itself. When the trojan is started, it will download and install XP Security Tool 2010 onto your computer with your permission and knowledge.
During installation, XP Security Tool 2010 configures itself run automatically every time when you start an application (files with “exe” extension). The rogue also uses this method of running to block the ability to run any programs, including security applications.
Immediately after launch, XP Security Tool 2010 will start to scan your computer and reports a lot of various infections that will not be fixed unless you first purchase the software. Important to know, all of these infections are a fake and do not actually exist on your computer. What is more, the rogue will also hijack Internet Explorer and Firefox and display fake warnings when you opening a web site.
As you can see, XP Security Tool 2010 is a scam and should be removed from your computer upon detection. Do not be fooled into buying the program! Instead of doing so, follow the removal guidelines below in order to remove XP Security Tool 2010 and any associated malware from your computer for free.
Use the following instructions to remove XP Security Tool 2010 (Uninstall instructions)
Step 1. Repair “running of .exe files”.
Method 1
Click Start, Run. Type command and press Enter. Type notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
Windows Registry Editor Version 5.00
[-HKEY_CURRENT_USER\Software\Classes\.exe]
[-HKEY_CURRENT_USER\Software\Classes\secfile]
[-HKEY_CLASSES_ROOT\secfile]
[-HKEY_CLASSES_ROOT\.exe\shell\open\command]
[HKEY_CLASSES_ROOT\exefile\shell\open\command]
@="\"%1\" %*"
[HKEY_CLASSES_ROOT\.exe]
@="exefile"
"Content Type"="application/x-msdownload"
Save this as fix.reg to your Desktop (remember to select Save as file type: All files in Notepad.)
Double Click fix.reg and click YES for confirm.
Reboot your computer.
Method 2
Click Start, Run. Type command and press Enter. Type notepad and press Enter.
Notepad opens. Copy all the text below into Notepad.
[Version]
Signature="$Chicago$"
Provider=Myantispyware.com
[DefaultInstall]
DelReg=regsec
AddReg=regsec1
[regsec]
HKCU, Software\Classes\.exe
HKCU, Software\Classes\secfile
HKCR, secfile
HKCR, .exe\shell\open\command
[regsec1]
HKCR, exefile\shell\open\command,,,"""%1"" %*"
HKCR, .exe,,,"exefile"
HKCR, .exe,"Content Type",,"application/x-msdownload"
Save this as fix.inf to your Desktop (remember to select Save as file type: All files in Notepad.)
Right click to fix.inf and select Install. Reboot your computer.
Step 2. Remove XP Security Tool 2010 associated malware.
Download MalwareBytes Anti-malware (MBAM). Once downloaded, close all programs and windows on your computer.
Double-click on the icon on your desktop named mbam-setup.exe. This will start the installation of MalwareBytes Anti-malware onto your computer. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to “Update Malwarebytes’ Anti-Malware” and Launch “Malwarebytes’ Anti-Malware”. Then click Finish.
MalwareBytes Anti-malware will now automatically start and you will see a message stating that you should update the program before performing a scan. If an update is found, it will download and install the latest version.
As MalwareBytes Anti-malware will automatically update itself after the install, you can press the OK button to close that box and you will now be at the main menu. You will see window similar to the one below.
Malwarebytes Anti-Malware Window
Make sure the “Perform quick scan” option is selected and then click on the Scan button to start scanning your computer for XP Security Tool 2010 infection. This procedure can take some time, so please be patient.
When the scan is finished a message box will appear that it has completed scanning successfully. Click OK. Now click “Show Results”. You will see a list of infected items similar as shown below.
Note: list of infected items may be different than what is shown in the image below.
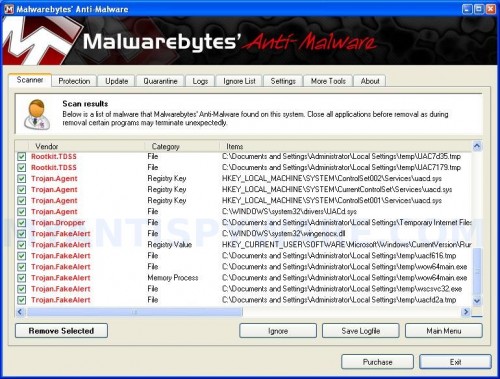
Malwarebytes Anti-malware, list of infected items
Make sure all entries have a checkmark at their far left and click “Remove Selected” button to remove XP Security Tool 2010. MalwareBytes Anti-malware will now remove all of associated XP Security Tool 2010 files and registry keys and add them to the programs’ quarantine. When MalwareBytes Anti-malware has finished removing the infection, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
XP Security Tool 2010 creates the following files and folders
%AppData%\ave.exe
XP Security Tool 2010 creates the following registry keys and values
HKEY_CURRENT_USER\Software\Classes\.exe
HKEY_CURRENT_USER\Software\Classes\.exe\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\.exe\shell
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas
HKEY_CURRENT_USER\Software\Classes\.exe\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start
HKEY_CURRENT_USER\Software\Classes\.exe\shell\start\command
HKEY_CURRENT_USER\Software\Classes\secfile
HKEY_CURRENT_USER\Software\Classes\secfile\DefaultIcon
HKEY_CURRENT_USER\Software\Classes\secfile\shell
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command
HKEY_CURRENT_USER\Software\Classes\secfile\shell\runas
HKEY_CURRENT_USER\Software\Classes\secfile\shell\runas\command
HKEY_CURRENT_USER\Software\Classes\secfile\shell\start
HKEY_CURRENT_USER\Software\Classes\secfile\shell\start\command
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | @ = “”%AppData%\ave.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe\shell\open\command | IsolatedCommand = “”%1″ %*”
HKEY_CURRENT_USER\Software\Classes\.exe | @ = “secfile”
HKEY_CURRENT_USER\Software\Classes\.exe | Content Type = “application/x-msdownload”
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command | @ = “”%AppData%\ave.exe” /START “%1″ %*”
HKEY_CURRENT_USER\Software\Classes\secfile\shell\open\command | IsolatedCommand = “”%1″ %*”











Thanks a lot! Just caught the problem today and you’re post couldn’t have come at a better time.
And it works! Thank you.
it works great….same as “dmitry” it worked just when i needed.coooool…..
I created the fix.reg as above. When I try to run it, seems it doesn’t execute. I do not get any Yes/NO or confirmation prompt. Malwarebytes too is not getting installed.
I have Windows XP Security Tool 2010 seems to block both fix.reg and Malwarebytes.
Please help. I also tried SDFix but that too didn’t owrk. Once the runthis.bat file is run, the blue screen stating checking files….appears. But after sometime the blue screen of SDFix disappears and nothing happens inspite of waiting for about 30 mins.
I have Win XP SP2. And my computer got infected on 19th March 2010.
Thanks for reading,
Jignesh
Jignesh, use method 2 of first step.
I do not get any response when i type command or cmd into the run box. My pointer looks like it is thinking, and then nothing pops up. Is there another way to get to the hkeys to remove them?
Thanks,
Joel, Click Start, Run, type notepad and press Enter. Notepad opens. Then follow the steps above.
I had this problem on an XP SP3 comp at work (I do a bit of IT). I couldn’t get MBAM to run by double-clicking it. I had to right click on it and then click “Start” to get it to work. TY for the instructions, though. It’s good to know ahead that MBAM can cut it.
When i tried method 2 on step 1, the propmpt said \windows cannot open this file\
It then directed me to browse the programs to open the file
also, method 1 did not work as it said my cpu required binarh script
any help would be appreciated
JB, try method 1 once again. but in the Save dialog check twice: File type: All Files; File encoding: ANSI.
Same problem, XP security tool keeps running and will not let me on Internet. Done the first method and still no joy, every time I click Internet explored the security tool firewall pops up and then says I’m working offline and runs a scan!!! Any ideas, driving me crazy
Kelly, follow the first step instructions, then (don`t reboot your computer) click Start, Run, type regedit and press Enter.
Registry editor opens.
Navigate in the left panel to HKEY_LOCAL_MACHINE \ SOFTWARE \ Clients \ StartMenuInternet \ IEXPLORE.EXE \ shell \ open \ command
I the right part of window click twice to “@”. You will see a screen with the contents like below: “C:\Documents and Settings\user\Local Settings\Application Data\av.exe” /START “C:\Program Files\Internet Explorer\iexplore.exe”
Remove left part, leave only “C:\Program Files\Internet Explorer\iexplore.exe”.
Reboot your PC, then go to step 2.
they’ve basically killed all of these workarounds. cant access system restore, task manager, regedit. EVEN IN SAFE MODE. anti malware and spydoctor programs won’t run. i’ve had this before and was able to get rid of it, but not this time, looks like a clean wipe is the only option. back up your data, folks.
JR, probably your PC is infected with trojan-rootkit that blocks any antispyware programs. Ask for help in our Spyware removal forum.
Just done it (Method 1). It seems to have worked. Thank you for your help.
Thank you!! It worked great and removed that sucker!
I used method 2. Seems to have worked for now, no signs of the rouge XP Security Tol program anymore, though I’m not taking any chances, I’m currently scanning with MBAM…
Thank you for the informative article above! I just want to add a couple of points to clarify certain operations:
1. The registry changes assume that the repairs are applied by the same account that was infected. This might not be the case for machines with multiple logins.
2. Starting with Windows 2000, the registry hive named HKEY_CLASSES_ROOT is generated by combining both the HKEY_LOCAL_MACHINE\Software\Classes and HKEY_CURRENT_USER\Software\Classes keys and their subkeys (see <a href="http://msdn.microsoft.com/en-us/library/ms724475(VS.85).aspx" title="Microsoft article"). If keys overlap then the values associated to HKEY_CURRENT_USER\Software\Classes are assigned to the resulting HKEY_CLASSES_ROOT key, ignoring the values specified by HKEY_LOCAL_MACHINE\Software\Classes.
With this information, and verifying that the HKEY_LOCAL_MACHINE\Software\Classes .exe and exefile key and subkey values reflect what’s mentioned above, you simply need to delete these subkeys (.exe and exefile) from the HKEY_CURRENT_USER\Software\Classes. Once deleted, the HKEY_CLASSES_ROOT .exe and exefile subkeys will then reflect their key values found in the HKEY_LOCAL_MACHINE\Software\Classes. If you’re using REGEDIT as the GUI to delete these keys, don’t forget to refresh your window (press F5) to see the new key values.
Finally, to prevent future infestations, you might want to consider changing the permissions for the HKEY_CURRENT_USER\Software\Classes key to a “Read” only value. Typically, the “default” key values assigned to the HKEY_LOCAL_MACHINE\Software\Classes during an application’s install program don’t need to be configured/changed on a per account basis.
Method 1 worked for me. Thank you so much!
My security software alerted me to a process initiated called ave.exe, which I blocked, but the block was ignored. After I did Method 1 I did a search for ave.exe and there was a copy in windows/prefetch – I deleted that too.
Again, thanks a bunch 🙂
Just removed noted keys.. it worked great to remove the xp security malware
Wow! Just got it off, thanks a lot. The program attacked my computer and turned off my key board. I sent the file as a doc file via the network and then had to cut and paste using the mouse. What a job. I just wish we could find the guys that write and send these out and take them behind the barn for a little hands on virus protection.
When I tried the first method, a Registry Editor window comes up, it says:
Are you sure you want to add the information in C:\Documents and Settings\sn313523\Desktop\fix.reg to the registry?
I click “Yes” and then it says:
Cannot import C:\Documents and Settings\sn313523\Desktop\fix.reg: The specified file is not a registry script. You can only import binary registry files from within the registry editor.
So Method 1 doesn’t work for me.
When I try Method 2 a Window comes up saying:
Error
Installation failed.
Please help :I
Aha! Thank you! I thought my poor laptop was a goner once Malwarebytes got compromised but I managed to repair it in safe mode using method 1. Thank you!
Thanks alot, it worked!
THANK YOU FOR THIS!
Those pop ups were getting a heckuva lot annoying.
Michael, check please:
1. you have “Windows Registry Editor Version 5.00” as first line
2. in the save dialog you have selected “ANSI” in the encoding field.
I got as far as asking Malaware to quarantine the infections and then nothing happened, no response, just the egg timer. And clues?
Boot your PC in Safe mode, the run Malwarebytes and perform a scan.
I tried method 1 step 1, and I copied all the information correctly and saved the file correctly. However, when I tried to add the file to the registry, I received the error message: “Cannot import X:\Documents and Settings\Owner\Desktop\fix.reg: The spexified file is not a grefistry script. You can only import binary registry files from within the registry editor.
What do I do to fix this?
Thanks a lot. It worked like a dream. I wasn’t able even to start ad-aware. I appreciate your time in helping us.