 TDSS trojan also known as Backdoor.Tidserv [PCTools], Backdoor.Tidserv.I!inf [Symantec], Rootkit.Win32.TDSS.y [Kaspersky Lab], Patched-SYSFile.a [McAfee], Mal/TDSSRt-A [Sophos], Virus:Win32/Alureon.F [Microsoft] is very dangerous. It installs onto your computer through a vulnerability in an already installed programs (mostly in InternetExplorer) or with the help of a rogue antispyware programs. Trojan TDSS uses rootkit-specific techniques designed to hide the software presence in the system. It is practically not detected by standard means Windows, you will not find its files on the disk, as well as writing about it in the Windows registry.
TDSS trojan also known as Backdoor.Tidserv [PCTools], Backdoor.Tidserv.I!inf [Symantec], Rootkit.Win32.TDSS.y [Kaspersky Lab], Patched-SYSFile.a [McAfee], Mal/TDSSRt-A [Sophos], Virus:Win32/Alureon.F [Microsoft] is very dangerous. It installs onto your computer through a vulnerability in an already installed programs (mostly in InternetExplorer) or with the help of a rogue antispyware programs. Trojan TDSS uses rootkit-specific techniques designed to hide the software presence in the system. It is practically not detected by standard means Windows, you will not find its files on the disk, as well as writing about it in the Windows registry.
When installed, it will be configured to start automatically when Windows starts. While is running, TDSS (Backdoor.Tidserv, Alureon) trojan may:
- display a lot of popups and fake security alerts
- hijack Internet Explorer
- redirect search results in Google, Yahoo, MSN to non related sites
- block an access to security websites
- disable Windows Task Manager, Windows Security Center and Registry editor
What is more, TDSS, Backdoor.Tidserv, Alureon trojan blocks the ability to run a lot of antivirus and antispyware programs, including Malwarebytes Anti-Malware. Also it is usually installed in conjunction with a rogue antispyware programs.
If your computer is infected with the trojan, then use these removal instructions below, which will remove TDSS, Backdoor.Tidserv, Alureon trojan and any associated malware for free.
Symptoms in a RootRepeal Log
Hidden Services
——————-
Service Name: H8SRTd.sys
Image Path: C:\WINDOWS\system32\drivers\H8SRTnfvywoxwtx.sys
Service Name: _VOIDd.sys
Image PathC:\WINDOWS\system32\drivers\_VOIDaabmetnqbf.sys
Use the following instructions to remove TDSS, Backdoor.Tidserv, Alureon trojan.
1. Use TDSSKiler by Kaspersky lab to detect and remove a rootkit.
2. Use Malwarebytes Anti-malware to remove TDSS, Backdoor.Tidserv, Alureon rootkits associated malware.
1. Use TDSSKiler by Kaspersky lab to detect and remove the TDSS rootkit.
Download TDSSKiller from th link above.
Right click to it and select Extract all. Follow the prompts.
Open TDSSKiller folder. Double click the TDSSKiller icon to run it. You will a screen like below.

Click Start scan button to start scanning and disinfection process. Once the process is complete, your computer will be rebooted.
2. Use Malwarebytes Anti-malware to remove TDSS, Backdoor.Tidserv, Alureon rootkits associated malware.
Download MalwareBytes Anti-malware from the following link.
MalwareBytes Anti-malware download link.
Close all programs and Windows on your computer. Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
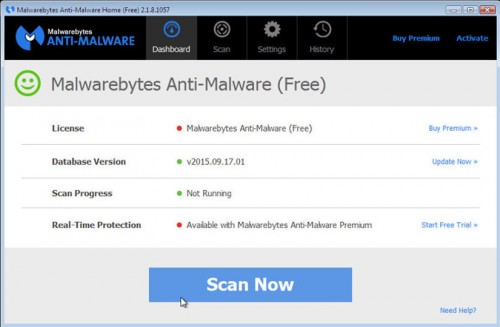
Click Scan Now button. It will start scanning your computer for TDSS, Backdoor.Tidserv, Alureon infection associated malware. This procedure can take some time, so please be patient.
When the scan is complete you will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
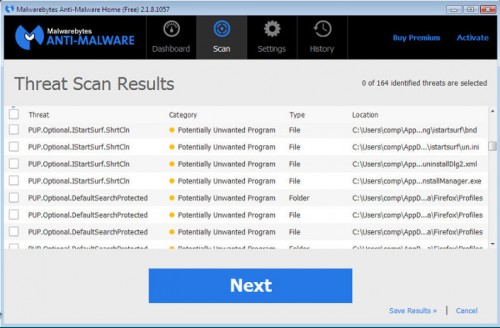
Make sure that everything is checked, and click Remove Selected for start TDSS, Backdoor.Tidserv, Alureon associated malware removal process. When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
TDSS, Backdoor.Tidserv, Alureon trojan creates the following files:
C:\Windows\System32\TDSS[RANDOM CHARACTERS].tmp
C:\Windows\System32\drivers\TDSS[RANDOM CHARACTERS].sys
C:\Windows\System32\TDSS[RANDOM CHARACTERS].sys
C:\Windows\System32\TDSS[RANDOM CHARACTERS].dat
C:\Windows\System32\TDSS[RANDOM CHARACTERS].log
C:\Windows\System32\TDSSserv.sys
C:\Windows\System32\TDSSerrors.log
C:\Windows\System32\TDSSservers.dat
C:\Windows\System32\TDSSl.dll
C:\Windows\System32\TDSSlog.
C:\Windows\System32\TDSSmain.dll
C:\Windows\System32\TDSSinit.dll
C:\Windows\System32\TDSSlog.dll
C:\Windows\System32\TDSSadw.dll
C:\Windows\System32\TDSSpopup.dll
TDSS, Backdoor.Tidserv, Alureon trojan creates the following registry keys and values
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\connections
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\disallowed
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\injector
HKEY_LOCAL_MACHINE\SOFTWARE\TDSSserv\versions
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\TDSSserv.sys










WOW…I nice end to a frustrating problem. Instructions worked as layed out and I seem to be TDSS free…Thanks!!!!!!!!!
Great article and nasty trojan – I couldn’t have started system in normal mode, only safe worked. A lot of security pages were blocked and I was also unable to use system recovery. You helped me out of big trouble, thanks! 🙂
It did work for me without downloading malware bytes, Thx for registry strings
Hi, please help
I followed the above instructions correctly but when avenger went into reboot, my computer is in a startup loop. when windows starts to load it blacks out and attempts to start again.
What can I do to fix this.
A heartfelt thankyou! Killed the trojan in one evening! This works!
Bless you! This really works! These remedies saved my PC! And the trojan and virus was permanently deleted in less than 3 hours! You are a Life Saver!
Thank you so much! I was driving myself nuts trying to get rid of this.
Thank you so much! I was driving myself nuts trying to get rid of this!
i have a problem.. after that i have re booted the computer and checked that the TDSsserv is gone i still can`t acces the websites were i can download avenger and malwerebytes.. any ideas for what to do?
We are having the exact same symptons mentioned at the beginning of this thread, but there is no TDSServ files located on the server.
It is probably named something else. Any idea how I can identify it?
Thanks,
Please follow these steps. I will help you.
I just wanted to say thank you very much and this worked and i love u 🙂
I had a variant that left files starting with “seneka???”. Nothing worked, although combofix detected it. However, every reboot combofix would detect it again. Here is how I fixed it. Only run this way if you are in the combofix reboot cycle and nothing else works!:
1) Run combofix. If it detects the root kit write down the file names.
2) Let combofix reboot your machine
3) Boot into the Recovery Console (either from startup or from the XP CD)
4) Login and at the command prompt type “fixmbr”. Answer ‘Y’ to the prompt.
5) Go to the first directory identified by combofix. For example, on my machine it was
c:\windows\system32\drivers\senekanisovjkq.sys
so I typed “cd \windows\system32\drivers”
6) do a directory listing to find all related files. BE CAREFUL TO USE ENOUGH CHARACTERS TO UNIQUELY IDENTIFY RELATED FILES! If you are not sure, I do not recommend that you proceed.
dir seneka*.*
7) Delete each file, one at a time (‘del’ in Recovery Console does not support wildcards).
8) Repeat step 7 for all directories identified by combofix.
9) Reboot normally
10) Allow combofix to run again.
11) Follow instructions
Rick, thank you for the information.
I have a problem with the trojan too I did tried to follow the firts step displayed in this forum but it didn’t work for me because de files didn’t appear. So the name of the virus is Seneka971e7.tmp Please Help I already did a system restore and lost all of my pictures and important info.
If in the list of drivers you have found Seneka971e7.tmp, than disable it. If you need help, then read and follow these steps.
I am cannot boot my pc in normal mode only in safe mode and when the only option i have in device manager is unistall \
Then try it.
thank’s God bless you from Puerto Rico it work’s perfect
Fantastic ! 4 days of banging my head against .tmp files, backdoor detections by symantec antivirus, deleting, rebooting just to have everything come back after reboot. Your instruction worked a treat. After running MBAM and rebooting I re-ran symantec and everything is clear. Very cool. I had to reboot a couple of times but my computer looks clean as a bell. THANK YOU …life saver.
thank you Iam glad I found this site.
Thank you, Thank you, Thank you!!!!!!!!
I fought with this POS for 12 hours.
Thanks Bro! You’re the BEST! 4.5 hours of wasted time until I found your instructions.
Downloaded Avenger but when the exe is executed Winrar throw up cannot execute, any ideas???
Download avenger file to your Desktop, rigth click to avenger and select Extract.
I found seneka but it comes up as a temp file. I looked on my computer none of the regs are in there.
When I try to remove it everything I try it shuts down my computer. I tried all the software on this and many other sights. I use Macafee and a couple other malware things shredders don’t work. And I have to much stuff to reload.
YOU ARE THE BESTTTTTTTTTTTTTT!!!!!!!!!!!!!!!!!!
thanks for sharing
Jeff, read and follow these steps.
Thank you veryyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy much. really you are Brilliant.
You save many computers.
Thank you so much. My pc got so jammed up I couldnt download Avanger or Malware. So I downloaded them to a USB memory stick on another PC and then booted them on the infected PC from stick… Brilliant got on and followed your excellent instructions. Now working again properly.
I dont understand why an up to date McAfee didnt sort it out first, its supposed to.
Anyway thanks again for well worded instructions