Beware of the “You Visited Some Hacked Websites With Exploit” Email Scam — A Dangerous Cyber Extortion Trick. Recently, scammers have been sending out frightening emails under the subject line “Cooperation Offer”, designed to scare recipients into paying large sums of money in Bitcoin. These emails claim the sender has hacked your devices through compromised websites, installed malware that records your private activity, and now holds compromising videos to blackmail you.
Despite the alarming tone and disturbing threats, this is a well-known scam tactic aimed to sow panic and rush victims into payment. The scammers say they’ve installed invisible malware that steals your data and filmed you in embarrassing situations — all without any solid proof. Their demands to send thousands of dollars in Bitcoin leverage fear and shame rather than facts.
The message usually includes a Bitcoin wallet address for payment and pressures you to act quickly, warning that they will share the alleged recordings with your contacts and online if you refuse or delay. They also falsely claim that authorities cannot help because they use untraceable methods like TOR and darknet.
This extortion scheme uses common scare tactics but is almost always empty of real evidence. If you receive such a message, don’t panic or engage. Do not pay or respond, as it only encourages the scammer. Instead, delete the email, change your account passwords, run a trusted antivirus scan, and keep your system updated.
A typical “You Visited Some Hacked Websites With Exploit” scam email reads as follows:
Subject: Cooperation Offer.
Hello!
As you can see, this is not a formal email, and unfortunately, it does not mean anything good for you.
BUT do not despair, it is not critical. I am going to explain to you everything right now.I have access to your electronic devices, which are the part of the local network you regularly use.
I have been tracking your activity for the last few months.How did that happen?
You visited some hacked websites with Exploit, and your device was exposed to my malicious software (I bought it in Darknet from specialists in this field).
This is a very complex software, operating as Trojan Horse. It updates regularly, and your antivirus can not detect it.
The program has a keylogger; it can turn your camera and microphone on and off, send files and provide access to your local network.It took me some time to get access to the information from other devices, and as of now, I have all your contacts with conversations, info about your locations, what you like, your favourite websites, etc.
Honestly, I meant nothing bad at first and did that just for fun. This is my hobby.But I got HIV and unfortunately lost my job.
And I figured out how to use “my hobby” to get money from you!
I recorded a video of you masturbating. This video has a separated screen, where you can be easily recognised; also, it can be clearly seen what sort of video you prefer.
Well, I am not proud of this, but I need money to survive.Let’s make a deal. You pay me as much as I ask you to, and I won’t send this video to your friends, family, and other acquaintances.
You should understand, this is not a joke. I can send it by email, through SMS-link, social media, even post it in mass media (I have got some hacked accounts of their admins).
So you can become Twitter or Instagram “Star”!To avoid this, you should send me 1,290 USD in Bitcoins on my BTC wallet:1Q3ZMhxXKNdpySDFhtu6i8meoQLauuNo2S
If you don’t know how to use Bitcoins, search it in Bing or Google <> or other stuff like that.
I will delete the video as soon as I receive the money. I will also delete the malicious software from your device, and you will never hear from me again.
I’ll give you 2 days, that’s more than enough, I think. Time tracking will start as soon as you open this email, I am monitoring this!And one last thing:
It makes no sense to report about this to the police since I am using TOR, so there is no way to track Bitcoin transactions.
Don’t respond to me (I generated this letter in your account and put the real address of the man who has no idea about this). In such a way, I make it impossible to track me.If you ever do something stupid or against my expectations, I will immediately share this video.
Good luck!
🚨 Is the “You Visited Some Hacked Websites With Exploit” Email a Scam?
This email is a classic example of a blackmail phishing attempt designed to scare recipients into sending money. The email claims that the sender has hacked your devices through exploited websites and recorded compromising footage of you, threatening to send it to your contacts unless you pay a ransom in Bitcoin. These scare tactics are common among scammers who prey on fear and embarrassment to extort money without any real evidence or access.
Key Red Flags:
- 🌐 Generic and Fear-Inducing Language: The email uses vague threats about hacking, video recordings, and personal data to create panic but provides no specific details that prove the sender actually has compromising information.
- ⭐ Unverifiable Claims: The scammer claims to have access to your contacts, camera, microphone, and personal files, but this is a standard scare tactic with no proof or technical verification.
- 🔒 Demands for Bitcoin Payment: The email requests payment exclusively in Bitcoin, a common method for scammers because it is difficult to trace and irreversible.
- ⚠️ Pressure and Deadlines: The scam creates urgency by giving only two days to pay, attempting to rush you into a hasty decision without verifying the claims.
- 📉 Threats Against Reporting: The email warns against contacting law enforcement by falsely claiming the use of TOR and untraceable Bitcoin transactions, aiming to discourage victims from seeking help.
- 👤 Spoofing Techniques: The scammer admits to forging the sender’s email address, making it impossible to track or trace the real source.
In summary, the “You Visited Some Hacked Websites With Exploit” email is a typical phishing scam trying to extort money through intimidation. There is no credible evidence that your devices have been hacked or that any compromising video exists. It is strongly advised not to respond or pay any ransom. Instead, maintain your cybersecurity by updating passwords, running trusted antivirus scans, and consulting IT security professionals if you suspect a breach. If you receive such emails, mark them as spam and report them to your email provider or anti-fraud authorities.
Summary Table
| Name | You Visited Some Hacked Websites With Exploit Email Scam |
| Type | Sextortion scam / Email scam |
| Method | Scammer claims device hacked after visiting hacked websites, demands Bitcoin payment with threat of sharing private video |
| Scam Message Subject | Cooperation Offer. |
| Bitcoin Wallet | 1Q3ZMhxXKNdpySDFhtu6i8meoQLauuNo2S |
| Advice | Do not pay or respond. Delete the email. Change passwords and scan your devices for malware. |
📧 What to Do When You Receive the “You Visited Some Hacked Websites With Exploit” Scam Email
We advise everyone who receives this email to follow the simple steps below to protect yourself from potential scams:
- ❌ Do not believe this email.
- 🔒 NEVER share your personal information and login credentials.
- 📎 Do not open unverified email attachments.
- 🚫 If there’s a link in the scam email, do not click it.
- 🔍 Do not enter your login credentials before examining the URL.
- 📣 Report the scam email to the FTC at www.ftc.gov.
If you accidentally click a phishing link or button in the “You Visited Some Hacked Websites With Exploit” Email, suspect that your computer is infected with malware, or simply want to scan your computer for threats, use one of the free malware removal tools. Additionally, consider taking the following steps:
- 🔑 Change your passwords: Update passwords for your email, banking, and other important accounts.
- 🛡️ Enable two-factor authentication (2FA): Add an extra layer of security to your accounts.
- 📞 Contact your financial institutions: Inform them of any suspicious activity.
- 🔄 Monitor your accounts: Keep an eye on your bank statements and credit reports for any unusual activity.
🔍 How to Spot a Phishing Email
Phishing emails often share common characteristics; they are designed to trick victims into clicking on a phishing link or opening a malicious attachment. By recognizing these signs, you can detect phishing emails and prevent identity theft:
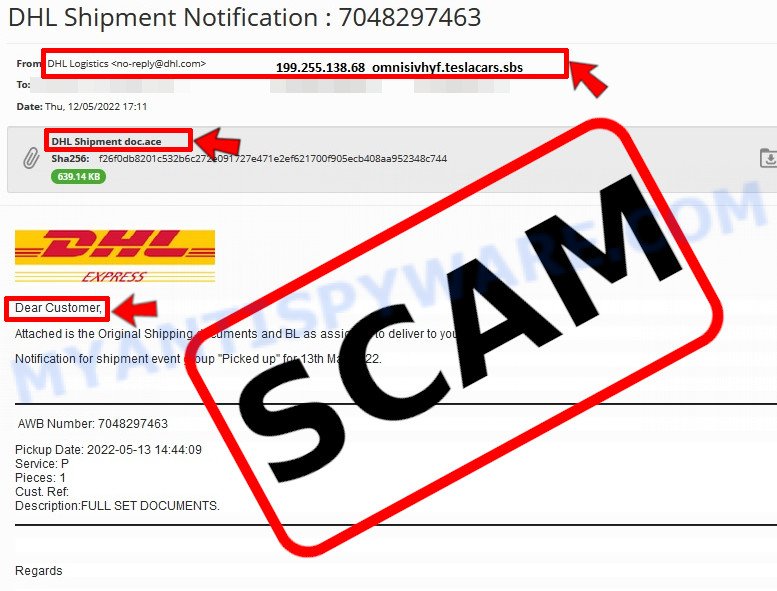
💡 Here Are Some Ways to Recognize a Phishing Email
- ✉️ Inconsistencies in Email Addresses: The most obvious way to spot a scam email is by finding inconsistencies in email addresses and domain names. If the email claims to be from a reputable company, like Amazon or PayPal, but is sent from a public email domain such as “gmail.com”, it’s probably a scam.
- 🔠 Misspelled Domain Names: Look carefully for any subtle misspellings in the domain name, such as “arnazon.com” where the “m” is replaced by “rn,” or “paypa1.com,” where the “l” is replaced by “1.” These are common tricks used by scammers.
- 👋 Generic Greetings: If the email starts with a generic “Dear Customer”, “Dear Sir”, or “Dear Madam”, it may not be from your actual shopping site or bank.
- 🔗 Suspicious Links: If you suspect an email may be a scam, do not click on any links. Instead, hover over the link without clicking to see the actual URL in a small popup. This works for both image links and text links.
- 📎 Unexpected Attachments: Email attachments should always be verified before opening. Scan any attachments for viruses, especially if they have unfamiliar extensions or are commonly associated with malware (e.g., .zip, .exe, .scr).
- ⏰ Sense of Urgency: Creating a false sense of urgency is a common tactic in phishing emails. Be wary of emails that claim you must act immediately by calling, opening an attachment, or clicking a link.
- 📝 Spelling and Grammar Errors: Many phishing emails contain spelling mistakes or grammatical errors. Professional companies usually proofread their communications carefully.
- 🔒 Requests for Sensitive Information: Legitimate organizations typically do not ask for sensitive information (like passwords or Social Security numbers) via email.
✅ Conclusion
You Visited Some Hacked Websites With Exploit is a fraudulent email designed to frighten recipients into paying a ransom. This scam falsely claims that the hacker has compromised your devices via visited hacked websites and malware, and that they have compromising videos or information on you. The scammer attempts to manipulate victims by invoking fear, embarrassment, and urgency, demanding payment in Bitcoin to avoid blackmail or public exposure.
In reality, these emails are generic and sent en masse without any actual evidence of hacking or recordings. The scam relies heavily on psychological intimidation, false claims about technical capabilities, and threats of releasing non-existent videos. It employs typical tactics such as anonymity via Tor, urging payment in untraceable cryptocurrencies, and disclaiming any possibility of law enforcement involvement to dissuade victims from seeking help.
Bottom Line: Do not respond to such scam emails or send any payment. These emails have no real proof of access to your devices or recordings, and the threats are baseless. Instead, delete the email, ensure your devices have up-to-date antivirus software, run security scans, and change any important passwords to be safe. If you feel concerned, consult with trusted cybersecurity professionals rather than engaging with the scammers. Stay vigilant and remember: these extortion scams thrive on fear, not facts.