⚠️ Have you received an email with the subject “A new payment schedule has been approved” claiming to have compromising information on you? Be cautious, as this is a scam known as “Sextortion“.
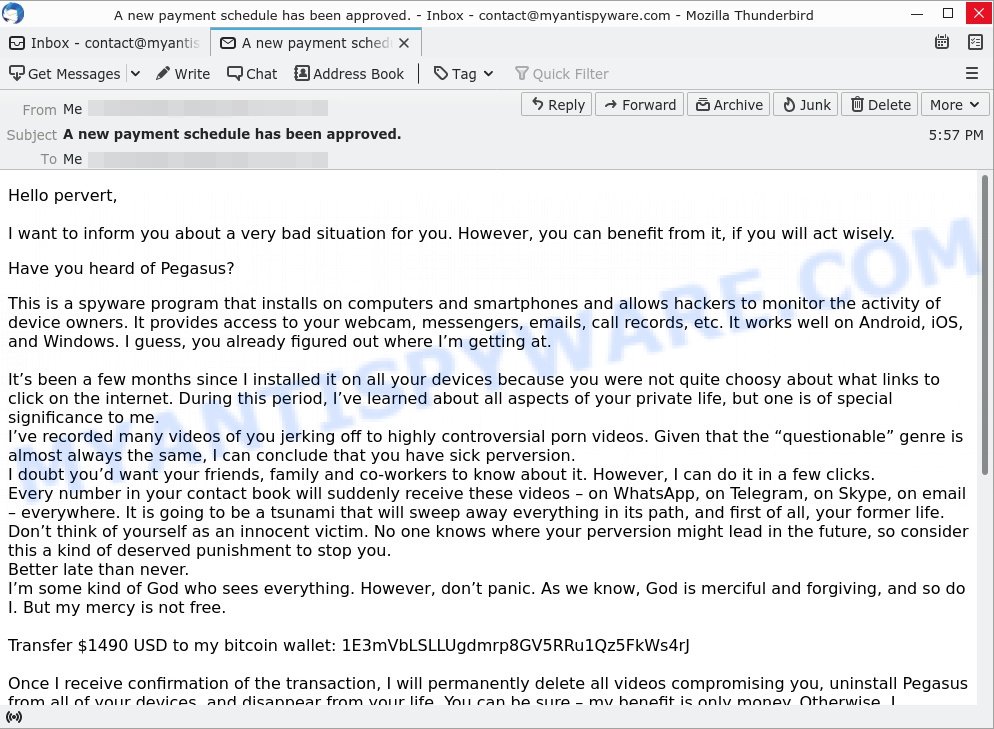
Here’s what happens: The email starts off with an unsettling greeting ‘Hello pervert’ and quickly moves to inform you that they’ve supposedly installed a sophisticated spyware called Pegasus on all your devices. This spyware has allegedly allowed them to monitor your activities, access your webcam, and even record you in private moments. The scammer threatens to release these supposed recordings to all your contacts unless you pay a ransom, usually in Bitcoin, to a specified wallet address.
But here’s the catch: these claims are false, designed to exploit your fear and coerce you into paying money without any real evidence of the recordings they claim to have.
The “A new payment schedule has been approved” Email Scam preys on fear and embarrassment to manipulate victims into complying. It’s crucial to remember that engaging with or paying the scammers does not guarantee your safety; it only marks you as an easy target for future scams. Always be skeptical of alarming emails that demand money or personal information and prioritize your online security with regular updates and caution about the links you click on. Awareness and skepticism are your best defenses against such online scams.
Table of Contents
🚨 Is the “A New Payment Schedule Has Been Approved” Email a Scam?
Yes, the email claiming that “A New Payment Schedule Has Been Approved” is a scam. 🚫 If you’ve received an email with this subject line or a similar message attempting to blackmail you by claiming to have compromising information, be very cautious. These threats are not based on real incidents but are designed to exploit your fear and coerce you into paying a ransom.
Examples of claims made in the scam email:
- I have installed spyware on all your devices and monitored your private life.
- I have recorded videos of you engaging in private activities and will send them to all your contacts unless you pay.
- You must transfer $1490 USD to my Bitcoin wallet to prevent the release of these videos.
- Do not contact the police or try to reset or destroy your devices, as it will lead to the immediate publication of the videos.
- This message was sent from a temporary email, so do not reply.
The email uses intimidation and threats to create a sense of urgency and fear. 🚨 The goal? To trick you into sending money to the scammer without any proof that the claimed videos exist. These scammers rely on the embarrassment and panic of their victims to achieve their aims. Remember: genuine communication regarding personal matters will not come through such threatening and anonymous messages. Always verify the authenticity of such claims through trusted channels before taking any action.
🚩 Red Flags to Watch Out For:
Stay alert and verify the legitimacy of such emails if you notice these signs. 🔍🛡️
- 📧 Intimidating Content: Emails that use threats and claim to have compromising information about you.
- 🔗 Demands for Cryptocurrency: The scammer asks for payment in Bitcoin or another cryptocurrency, exploiting its anonymity.
- ⏳ Urgency and Deadlines: The email may include a tight deadline to pressure you into acting quickly out of fear.
- 🖼️ Claims of Spyware: Be skeptical of emails claiming to have installed sophisticated spyware on all your devices without any proof.
- ✍️ Language of Blackmail: These emails often contain explicit threats to share private videos or information with your contacts.
- 👤 Anonymity of the Sender: The scammer will typically use a temporary or untraceable email address to avoid detection.
- 🔄 No Evidence Provided: Genuine claims would likely come with some form of evidence, whereas scammers rely purely on intimidation without substantiating their claims.
🕵️♂️ How the “A new payment schedule has been approved” Email Scam Works
The email scam with the subject “A new payment schedule has been approved” is a sophisticated form of digital extortion. Understanding its tactics is crucial for protecting yourself from becoming a victim. 💡🔐
🚨 Exploitation of Fear and Embarrassment
The scam initiates with an email accusing the recipient of having engaged in compromising activities. It exploits the natural human emotions of fear and shame, pushing recipients to comply with the scammer’s demands without questioning the legitimacy of the claims.
🔗 False Claims of Spyware Infection
The email falsely claims that a spyware program, named Pegasus, has been installed on the recipient’s devices. This supposed spyware is said to grant the scammer access to sensitive information and the ability to monitor the victim’s activities, including recording videos of private moments.
False Claims Examples:
- Installation of Pegasus spyware on all your devices
- Access to webcams, messengers, emails, and call records
- Recordings of you watching controversial content
- Threats to distribute these recordings to your contacts
🎭 Fabricated Evidence and Ultimatums
Scammers create a sense of urgency by claiming they have recorded videos of the victim engaging in embarrassing activities. They then issue an ultimatum, demanding a ransom in cryptocurrency within a short timeframe, typically 48 hours.
📥 Demands for Cryptocurrency Payment
The scammer demands a payment, usually in Bitcoin, to delete the supposed recordings and remove the non-existent spyware. This method is chosen for its anonymity, making it difficult to trace the scammer.
🔄 Illusion of Control and Anonymity
The scammer maintains an illusion of omnipotence and anonymity, claiming to have control over the victim’s devices and to be untraceable due to the use of cryptocurrency and temporary email addresses.
🕳️ Threats and Psychological Manipulation
The email includes multiple threats to share the alleged recordings with the victim’s contacts, coupled with a pretense of offering mercy in exchange for money. This psychological manipulation is designed to make the victim act out of fear and desperation.
Examples of such scams
Scammers have developed a variety of tactics to intimidate and exploit unsuspecting individuals. Here are a few common examples:
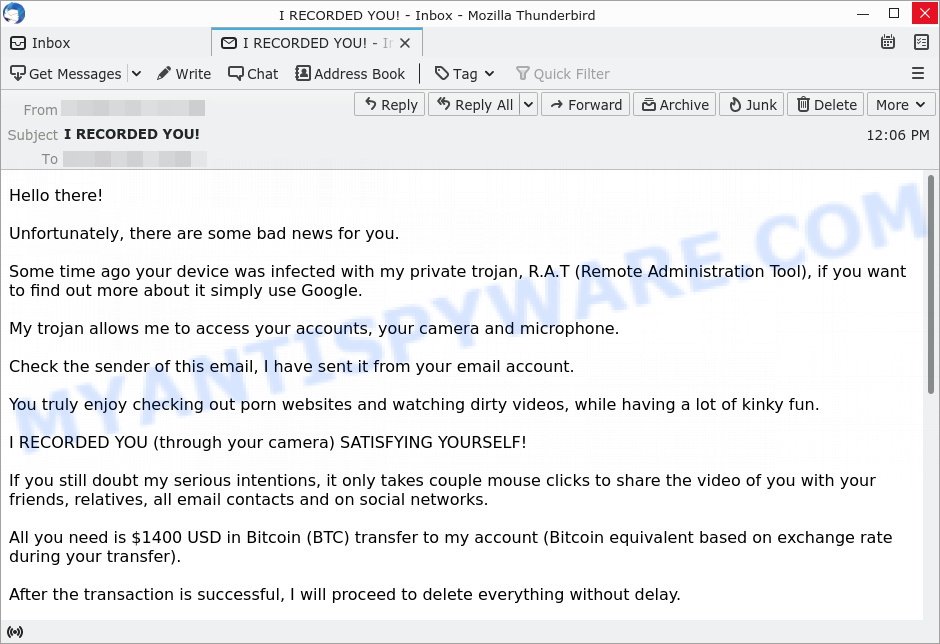
📹 I RECORDED YOU Email Scam
In this scam, the sender claims to have control over your camera and alleges they have recorded you during private moments. They typically demand payment to keep the footage private. Beware: this is a bluff to get you to pay up out of fear.
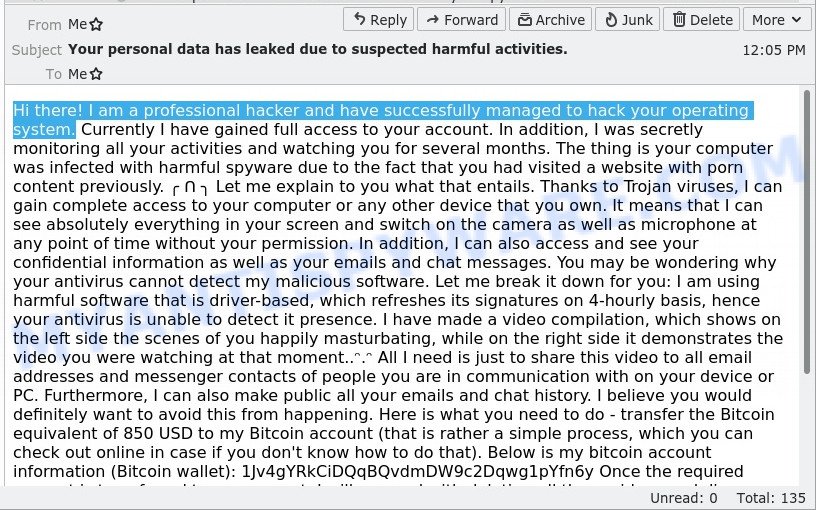
💼 I am a professional hacker EMAIL SCAM
Posing as a hacker, the sender of this email might say they’ve infiltrated your system. They may even claim they have proof of embarrassing activity and will publish it unless you send them money. Remember, a real hacker wouldn’t announce their presence—it’s a tactic to pressure you into paying.
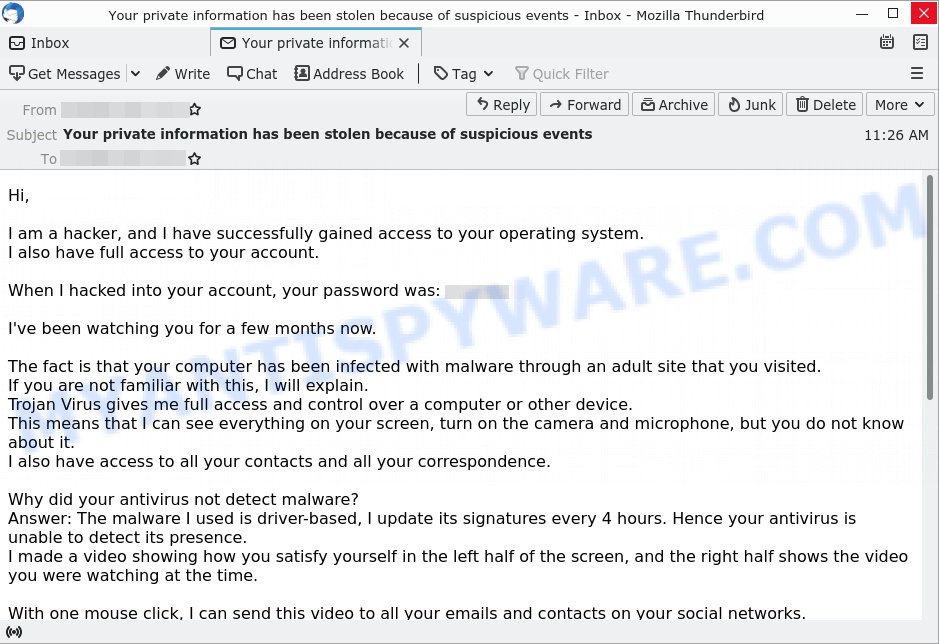
🔒 Your Private Information has been Stolen Email Scam
Here, the scammer will claim they’ve stolen sensitive information from you and threaten to release it unless you pay a ransom. They rely on the scare factor, hoping you’ll pay to protect your reputation, even though they likely have no data at all.
Each of these scams plays on fear and urgency to trick you into acting against your best interest. Always approach such emails with skepticism, verify your security, and do not engage with the scammers.
Should you pay?
No, you should not pay the ransom demanded by the scammer. Remember that this is a scam and paying the ransom will only encourage the scammer to continue their criminal activities! Additionally, paying the ransom can make you a target for future scams. It is important to stay vigilant and protect your personal information from such scams by using strong and unique passwords, enabling two-factor authentication, and regularly updating your computer’s security software. If you receive such an email, it is best to report it to the authorities and your email provider.

What to Do if You Receive the Email
Receiving the “A new payment schedule has been approved” email can be deeply unsettling, but with the right steps, you can ensure safety and peace of mind.

Here’s a specific guide on handling this scam:
Begin by reminding yourself to stay calm. The email is crafted to elicit panic, pushing recipients into rash decisions. Recognize its true nature—a manipulative attempt to exploit fear.
Resist any impulses to pay. Even if you’re tempted to make the problem go away, understand that payment doesn’t guarantee safety. It merely emboldens the scammer, possibly marking you as an easy target for future deceptions.
Do not engage with the scammer. Replying or trying to open a dialogue can inadvertently give away more information, or signal that your email is active, making you a prime candidate for further scams.
Seeing a familiar password can be particularly jarring. If the scam email mentions a password you recognize, it’s essential to check its source. Use services like haveibeenpwned.com to see if your email or credentials have been compromised in any past data breaches.
Subsequent to that, update your passwords. Always choose strong, unique combinations and activate two-factor authentication on platforms that support it.
As a precaution, run a comprehensive security scan on your device. While the scam email’s claims about malware are usually baseless, this step ensures your system remains clean and threat-free.
Report the email to relevant authorities (e.g., FTC). Sharing details with your local law enforcement or cybercrime units can contribute to ongoing investigations and aid in the crackdown on such malicious activities.
Lastly, spread awareness. Inform friends, colleagues, and family about the scam, equipping them with the knowledge to recognize and sidestep such threats. Knowledge, shared and acted upon, diminishes the effectiveness of these scams, making the digital world a bit safer for everyone.
Threat Summary
| Name | ‘A new payment schedule has been approved’ Email Scam |
| Type | Phishing/Sextortion |
| Email Subject | A new payment schedule has been approved. |
| Ransom amount | $1490 USD (in Bitcoin equivalent) |
| Bitcoin Address | 1Pd7qACCUtM1zVXixbyxuJCXmDi4D1qMjn, 1E3mVbLSLLUgdmrp8GV5RRu1Qz5FkWs4rJ |
| Fake Claims | Compromised data, webcam access, malware/backdoor installed |
| Damage | Psychological distress, potential financial loss if ransom is paid |
| Distribution | Mass emailing, likely from a purchased or hacked email list |
| Tactics | Fear induction, urgency, deception |
| Variations | Different ransom amounts, varying email content, alternative cryptocurrencies for payment |
| Prevention Tips | Use strong, unique passwords; enable two-factor authentication; be skeptical of unsolicited emails; never pay ransoms |
| Reporting Info | Forward to the Anti-Phishing Working Group at reportphishing@apwg.org; Report the scam to relevant authorities (e.g., FTC); Share information about the scam with friends and family to raise awareness; Monitor online accounts for any suspicious activity |
Conclusion
The “A new payment schedule has been approved” email is a scam that uses fear to try and extort money from its victims. Scammers behind these emails create a sense of dread, falsely claiming they’ve compromised your privacy with spyware like Pegasus. They often assert they’ve recorded you in private moments, threatening to share these imaginary recordings with your contacts and demanding payment, usually in Bitcoin for its perceived anonymity. However, it’s important to recognize that these claims are almost always baseless.
Bottom Line: Do not engage with these emails. The best defense is to ignore their demands and prioritize your online security. 🛡️💻
Stay vigilant and think critically; an email that instantly scares you or seems overly sophisticated is probably a scam. 🤔