Is the email a Scam?
Leaked uncensored photos from your device are about to be shared to public email is a ‘sextortion’ scam that relies on psychological manipulation tactics. Scammers claim to have obtained information that could damage the victims reputation. Criminals usually contact potential victims through email, but in some cases, criminals can use online web forms, whatsapp and sms messages.
Scammers use stolen email credentials to send out scam messages to millions of people around the World. The messages are sent to email addresses exposed in previous known data breaches in which the user email address and password has been compromised.
In some cases, sextortion scam emails may contain real passwords that the victim has used in the past (or even uses). Usually passwords are appended to these messages as proof, that is, if the password was actually used by the victim, then what is described in the email is true. Scammers get these real passwords by buying them on darknet.
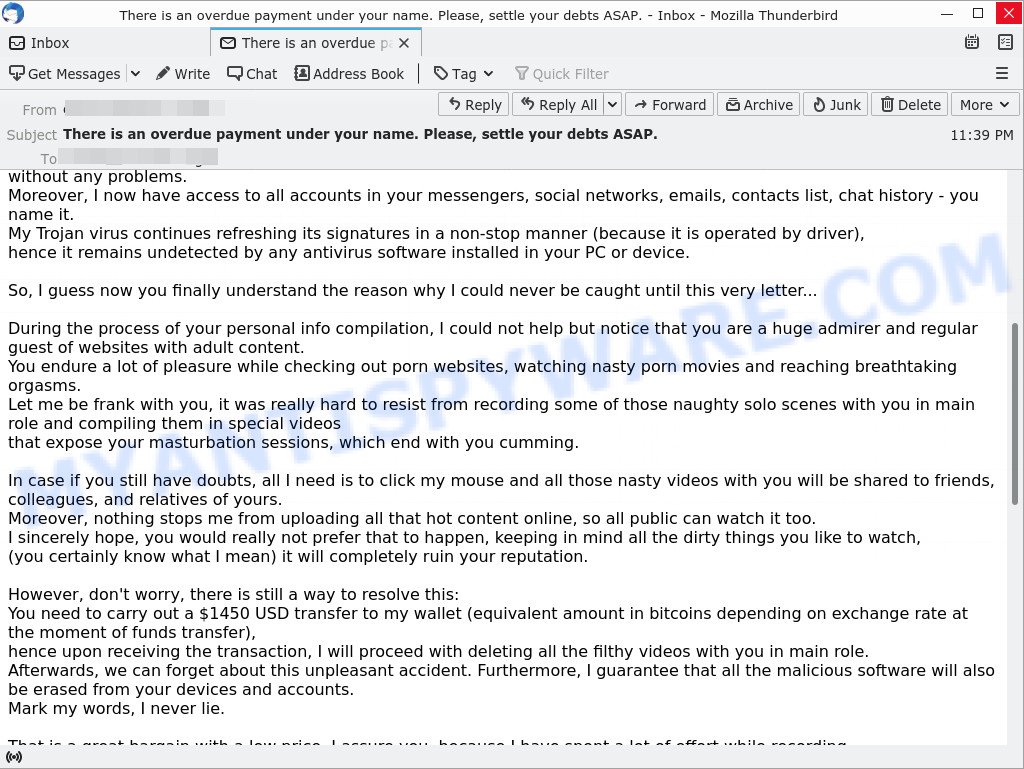
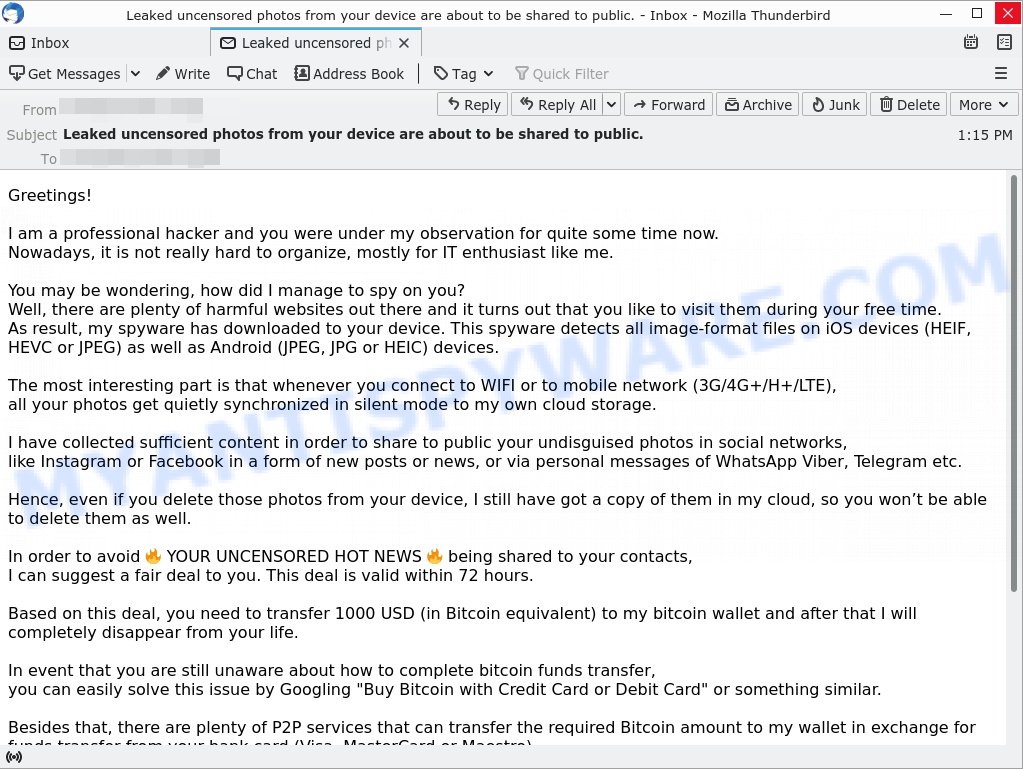
Here’s an example of the “Leaked uncensored photos from your device are about to be shared to public.” scam email:
QUICK LINKS
- Is the email a Scam?
- Should you pay?
- What to do when you receive the scam message?
- How to spot a phishing email?
- Report Scam Email
The Scam Email in detail
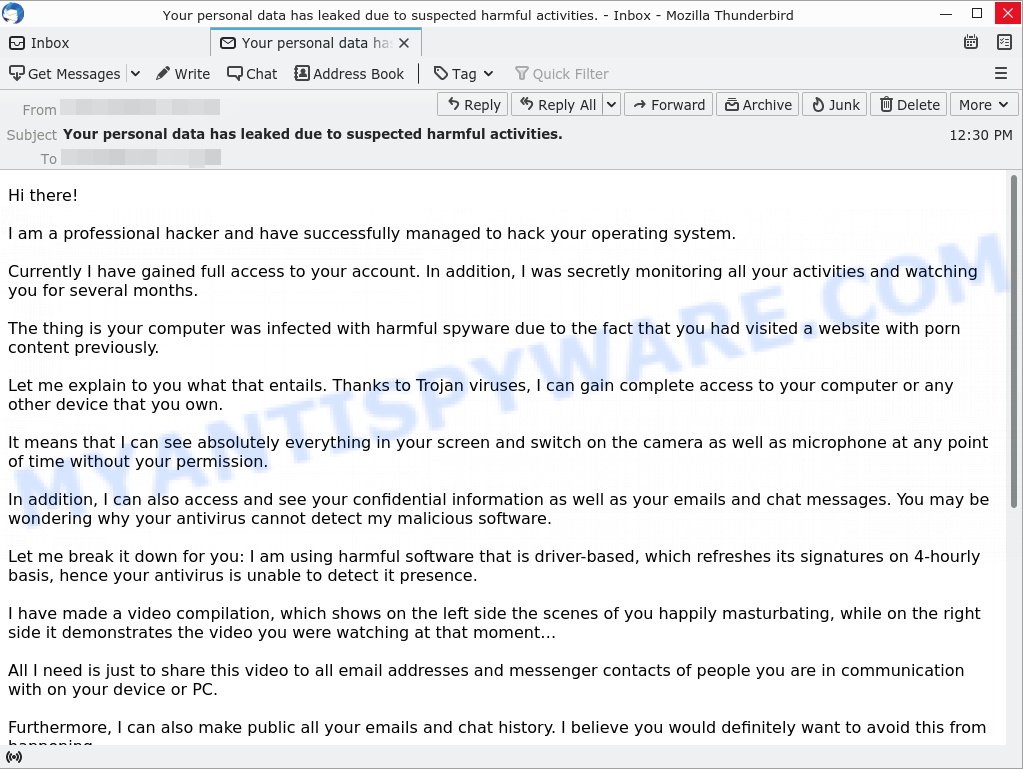
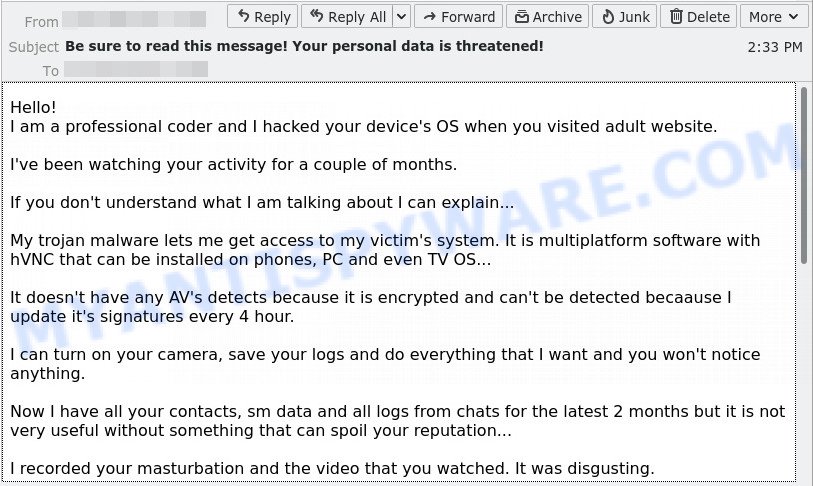
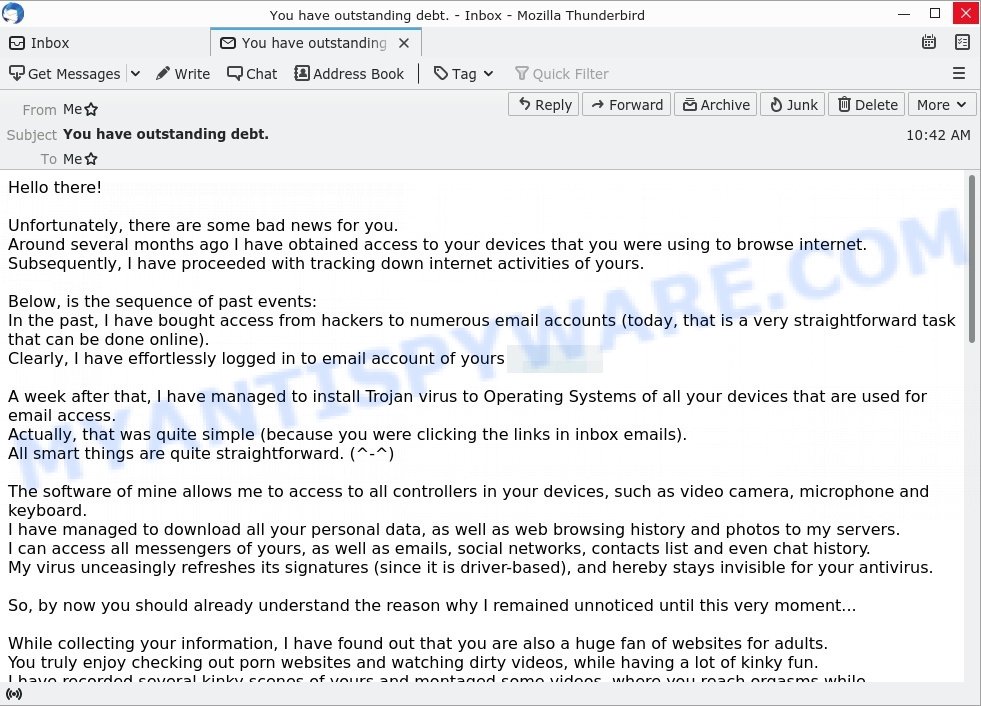
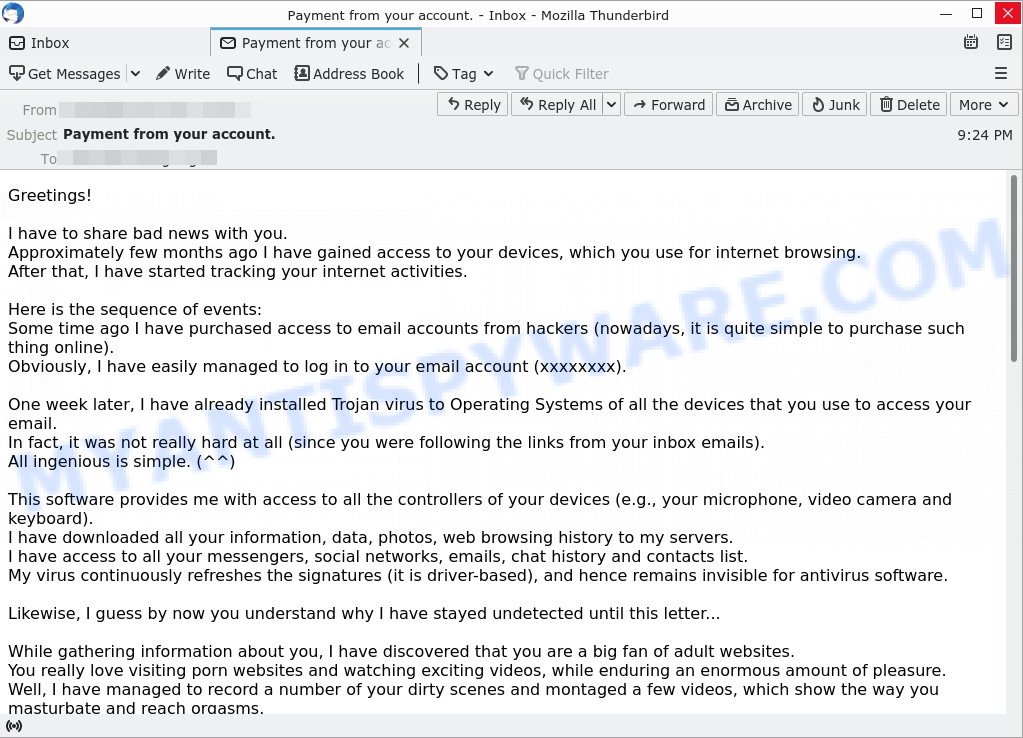
In this particular case, the scam email says that someone calling himself a professional hacker has been watching the victim, because the victim’s device has a harmful spyware, which is a Trojan that allows the attacker to to find all image-files stored on the device. The scam email claims that among the files found were uncensored photos that will be shared on social media if the victim does not pay the ransom to the bitcoin address provided in the email.
The scam email is not the only one of its kind, there are many similar ones. They all have similar features: statement that the victim’s computer and webcam were hacked, threats that the attackers recorded a compromising video, and a ransom demand. Explanations that scammers use to explain how they have access to your camera and privacy:
- They set up malware on adult (porn) website.
- They penetrated with “zero-click” vulnerability on Zoom or Pegasus.
- They got your credentials (login and password) from hackers.
Depending on the scam email, victims are given 24 to 48 hours to pay a ransom in Bitcoin. The sextortion emails also contain claims that the victim’s contact information was stolen, allegedly the hacker copied the victim’s contact list and social media credentials. And finally, Sextortion scams contain threats, the victims must pay a ransom, or compromising materials will be sent to their contacts.
Typically, sextortion scams are sent via email, thousands at a time, and are part of larger spam campaigns. As with many other types of scams, scammers are evolving their methods to deliver their messages to potential victims. Such attacks can be personalized and sent out in smaller numbers to avoid detection. Scammers can use reputable services, change and personalize the content of each message, and avoid including links or attachments – all in an attempt to bypass security.
Full text of the scam email:
Greetings!
I am a professional hacker and you were under my observation for quite some time now.
Nowadays, it is not really hard to organize, mostly for IT enthusiast like me.You may be wondering, how did I manage to spy on you?
Well, there are plenty of harmful websites out there and it turns out that you like to visit them during your free time.
As result, my spyware has downloaded to your device. This spyware detects all image-format files on iOS devices (HEIF, HEVC or JPEG) as well as Android (JPEG, JPG or HEIC) devices.The most interesting part is that whenever you connect to WIFI or to mobile network (3G/4G+/H+/LTE),
all your photos get quietly synchronized in silent mode to my own cloud storage.I have collected sufficient content in order to share to public your undisguised photos in social networks,
like Instagram or Facebook in a form of new posts or news, or via personal messages of WhatsApp Viber, Telegram etc.Hence, even if you delete those photos from your device, I still have got a copy of them in my cloud, so you won’t be able to delete them as well.
In order to avoid 🔥 YOUR UNCENSORED HOT NEWS 🔥 being shared to your contacts,
I can suggest a fair deal to you. This deal is valid within 72 hours.Based on this deal, you need to transfer 1000 USD (in Bitcoin equivalent) to my bitcoin wallet and after that I will completely disappear from your life.
In event that you are still unaware about how to complete bitcoin funds transfer,
you can easily solve this issue by Googling “Buy Bitcoin with Credit Card or Debit Card” or something similar.Besides that, there are plenty of P2P services that can transfer the required Bitcoin amount to my wallet in exchange for funds transfer from your bank card (Visa, MasterCard or Maestro).
Here is my Bitcoin address: 18bSTrufLfuvHwS7JYuF626MBGULSmxTgR
I really want to settle this situation in a peaceful manner and I believe you want that too.
Nothing personal, it is simply my job.
Make sure you use valid Antivirus software and stay away from unwanted websites.
Take care of yourself.
Should you pay?
The best advice is: Don’t pay the ransom and do not reply! Sometimes scammers will escalate if you reply. If you receive the sextortion email scam, just ignore the scammers. The best way to deal with the scam email is simply to move it to trash!

Threat Summary
| Name | Leaked uncensored photos from your device SCAM |
| Type | Sextortion, Phishing, Bitcoin Blackmail Scam |
| Ransom amount | 1000 USD |
| Bitcoin Address | 18bSTrufLfuvHwS7JYuF626MBGULSmxTgR |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like Leaked uncensored photos from your device, our computer security experts recommend follow some easy steps below |
Examples of such scams
There are many sextortion scams circulating via email. Scammers often change the content of emails in order to deceive victims and bypass the security system. I am a professional hacker Email, FINAL WARNING Email, I’m a hacker who hacked your operating system, I hacked your device are other examples of sextortion scam emails.
- Your personal data has leaked due to suspected harmful activities. Email Scam
- I hacked your device EMAIL SCAM
- “You have outstanding debt.” email is a sextortion scam
- “Payment from your account.” email is a ‘sextortion’ scam
- “There is an overdue payment under your name. Please, settle your debts ASAP.” email is a SCAM
What to do when you receive the scam email
We advice to someone who gets this fraudulence message:
- Do not panic.
- Do not pay a ransom.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/.
- Mark the scam email as SPAM/JUNK and delete it.
- Scan your computer for malware.
- Install an anti-phishing software.
If you suspect that your computer is infected with spyware, you accidentally clicked on a link in the scam email, or just want to scan your computer for malware, then use one of the free malware removal tools.
How to spot a phishing email?
Phishing emails often share common characteristics; they are designed to trick victims into clicking on a phishing link or opening a malicious attachment. If you know these characteristics, you can detect phishing emails and prevent identity theft.
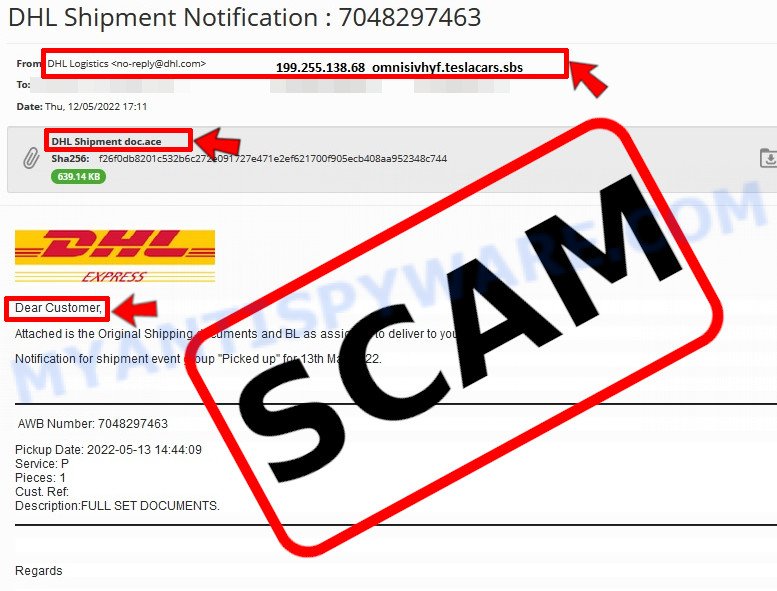
Here are some ways to recognize a phishing email
- Inconsistencies in Email Addresses. The most obvious way how to spot a scam email is finding inconsistencies in email addresses and domain names. If the email claims to be from a reputable company, like Amazon or PayPal, but the email is being sent from a public email domain, such as “gmail.com” it’s probably a scam.
- The domain name is misspelt. Look carefully for any subtle misspellings in the domain name. Like arnazon.com where the “m” has been replaced by “rn”, or paypa1.com, where the “l” has been replaced by “1”. These are common tricks of scammers.
- Generic greetings. If the email starts with a generic “Dear”, “Dear sir” or “Dear madam” that is a warning sign that it might not really be your shopping site or bank.
- Suspicious links. If you have the slightest suspicion an email may be a scam, do not click on the links you see. Instead, hover over the link, but don’t click it. This will pop up a small box that contains the actual URL. This works on image links as well as text links.
- Unexpected attachments. Email attachments should always be verified before clicking. Any attachments should be scanned for viruses – especially if they have an unfamiliar extension or one commonly associated with malware (.zip, .exe, .scr, etc.).
- The email creates a sense of urgency. Creating a false sense of urgency is a common trick of phishing emails. Be suspicious of emails that claim you must call, open an attachment or click a link immediately.
Report Scam Email
If you receive a scam email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. This helps us to warn users about current scams, monitor trends and disrupt scams where possible.