Security researchers recently discovered a new variant of Bitcoin email scam that targets Japanese users. The subject line of this scam is “あなたのパスワードが侵害されました”. This email scam tries to extort money by claiming to have a secretly created screenshots. Like before, this bitcoin blackmail scam spreads via spam emails. The spam is sent out to thousands of emails at a time. Below is an example of the new Bitcoin Scam with the ransom note:
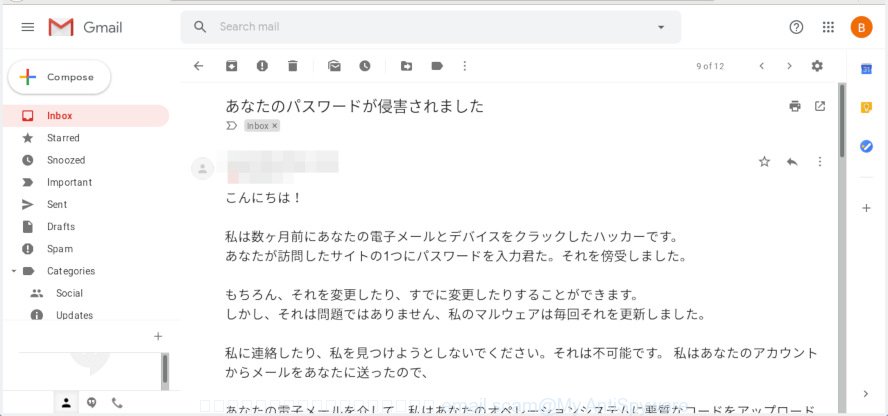
“あなたのパスワードが侵害されました” message is a new email scam
While terrifying at first, this email message is classic Bitcoin Blackmail Scam. It is old extortion scheme – which try to guilt people into paying off someone claiming to have secretly created screenshots, recorded video or compromising information. It is based on the fact that:
- the scam has been sent to countless people like any other widespread email spam
- the fraudulent message have the “spam” style grammar
- security researchers has determined that these emails attempts to force users into paying the requested ransom and that no actual screenshots and video exists
Myantispyware team continue to receive reports of fraudulent messages. Here below is an example of the latest variations of the “あなたのパスワードが侵害されました” Email Scam. There are variations in the wording of the email body, but all of these messages are basically the same:
Subject line: あなたのパスワードが侵害されました こんにちは! 私は数ヶ月前にあなたの電子メールとデバイスをクラックしたハッカーです。 あなたが訪問したサイトの1つにパスワードを入力君た。それを傍受しました。 もちろん、それを変更したり、すでに変更したりすることができます。 しかし、それは問題ではありません、私のマルウェアは毎回それを更新しました。 私に連絡したり、私を見つけようとしないでください。それは不可能です。 私はあなたのアカウントからメールをあなたに送ったので、 あなたの電子メールを介して、私はあなたのオペレーションシステムに悪質なコードをアップロードしました。 私は友人、同僚、親戚とのあなたの連絡先のすべてを保存し、インターネットリソースへの訪問の完全な履歴を保存しました。 また、あなたのデバイスにトロイの木馬をインストールしました。 あなたは私の唯一の犠牲者ではない、私は通常、デバイスをブロックし、身代金を求める。 しかし、私は頻繁に訪れる親密なコンテンツのサイトにショックを受けました。 私はあなたの幻想にショックを受けている! 私はこれのようなものを見たことがない! だから、あなたがサイトで楽しむとき(あなたは私が何を意味するか知っています!) あなたのカメラのプログラムを使用してスクリーンショットを作成しました。 その後、私はそれらを現在閲覧されているサイトのコンテンツに結合しました。 これらの写真を連絡先に送信すると素晴らしいことがあります。 しかし、あなたがそれを望んでいないと確信しています。 したがって、私は沈黙のためにあなたからの支払いを期待しています。 私は$681が良い価格だと思います! Bitcoin経由で支払う。 私のBTCウォレット: 1K6bUuopj2v9azMSGTDmH3TXQ9tAnK9E3P あなたがこれを行う方法を知らない場合 - Googleに「BTCウォレットに送金する方法」を入力します。 難しくない。 指定された金額を受け取ると、妥協しているすべての材料は自動的に破壊されます。私のウイルスはあなた自身のオペレーティングシステムからも削除されます。 私のトロイの木馬は自動アラートを持っています。私はこのメールを読んだ後でメッセージを受け取ります。 私はあなたに支払いのための2日間を与える(正確に48時間)。 これが起こらない場合 - すべてのあなたの連絡先はあなたの暗い秘密の生活からクレイジーショットを取得します! あなたが妨害しないように、あなたのデバイスはブロックされます(また、48時間後) ばかなことしないで! 警察や友人はあなたを確実に助けません... p.s. 私はあなたに将来のアドバイスを与えることができます。 安全でないサイトにはパスワードを入力しないでください。 私はあなたの慎重さを願っています。 お別れ。
There is one thing that it does to make itself appear real. It uses your own e-mail address as the “From” address, but do not be fooled. This phishing scam uses so-called “email spoofing”. Email spoofing is the creation of email messages with a forged sender address. Email spoofing has been around for a long time! Scammers use it in phishing attacks to force users into thinking they have received mail message from a friend or trusted person.
Should you pay?
The best advice is: Don’t pay the ransom! If you receive the blackmail scam, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
Threat Summary
| Type | Bitcoin Email Scam |
|---|---|
| Subject line | あなたのパスワードが侵害されました |
| Ransom amount | $681 in Bitcoins |
| BTC Wallet | 1K6bUuopj2v9azMSGTDmH3TXQ9tAnK9E3P |
What to do when you receive the “あなたのパスワードが侵害されました” email scam
We advice to someone who gets this fraudulence message:
- Do not panic.
- Scammers will try to rush you, pressure you to make a decision to pay him. We recommend you do not pay a ransom, because your payment will only increase attacks against you.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/
- Scan your computer for malware.
- Install an anti-phishing software.
- If you receive an email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. It will help our team monitor the latest scams.
How to scan your PC for malware
There are a few methods which can be used to detect and remove malware. In many cases you’re not able to remove any malicious software using standard Microsoft Windows options. In order to get rid of malware you need use reliable removal tools. Most IT security specialists states that Zemana Anti-malware is a right choice. This tool is able to find and remove malware from your computer for free.
Zemana can look for all kinds of malicious software, including ransomware, as well as a variety of Trojans, viruses and rootkits. After the detection of malware, you can easily and quickly remove it.
Installing the Zemana is simple. First you will need to download Zemana Anti-Malware (ZAM) on your machine by clicking on the link below.
165525 downloads
Author: Zemana Ltd
Category: Security tools
Update: July 16, 2019
Once downloading is finished, close all apps and windows on your computer. Open a directory in which you saved it. Double-click on the icon that’s named Zemana.AntiMalware.Setup as displayed below.
![]()
When the install starts, you will see the “Setup wizard” that will help you install Zemana AntiMalware on your computer.
Once installation is finished, you will see window like below.

Now click the “Scan” button . Zemana Anti-Malware (ZAM) program will scan through the whole PC system for malicious software. While the Zemana AntiMalware (ZAM) is checking, you can see number of objects it has identified either as being malicious software.

When the scan get completed, you’ll be shown the list of all found items on your system. Once you have selected what you want to delete from your computer press “Next” button.
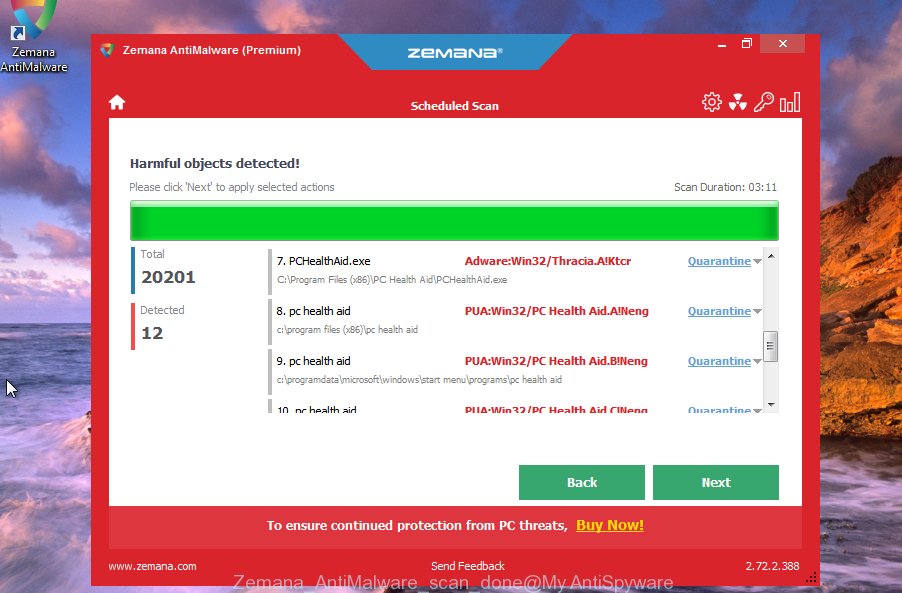
The Zemana Free will start to remove malware related files, folders and registry keys.
How to protect yourself from phishing web-sites
If you browse the Internet, you cannot avoid phishing web-sites and malicious advertising. But you can protect your web browser against it. Download and run an ad-blocker application. AdGuard is an ad-blocking which can filter out a huge count of of the malvertising, stoping dynamic scripts from loading malicious content.
- Download AdGuard by clicking on the link below.
Adguard download
27041 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
- Once the download is complete, launch the downloaded file. You will see the “Setup Wizard” program window. Follow the prompts.
- When the installation is finished, click “Skip” to close the installation program and use the default settings, or click “Get Started” to see an quick tutorial which will help you get to know AdGuard better.
- In most cases, the default settings are enough and you don’t need to change anything. Each time, when you start your PC system, AdGuard will start automatically and stop unwanted ads, block phishing web-sites, as well as other harmful or misleading web pages. For an overview of all the features of the application, or to change its settings you can simply double-click on the icon named AdGuard, that is located on your desktop.