If you are seeing a Spyware Alert box that stats that Worm.Win32.Netsky detected on your machine, then you have become infected with a trojan that uses this Spyware Alert to trick you into purchasing Advanced Virus Remover, Antivirus 2009 or another rogue antispyware program. Once running, the trojan will display a fake Security alert as shown below:
Security alert
Security Warning!
Worm.Win32.Netsky detected on your machine.
This virus is distributed via the Internet through email and Active-x
objects.
The worm has its own smtp engine which means it gathers
emails from your local computer and re-distributes itself.
In worst cases this worm can allow attachers to access your
computer, stealing passwords and personal data.
Viruses can damage your confidential data and work on your
computer.
Continue working in unprotected mode is very dangerous.Recommendation: It is necessary to perform a system scan.
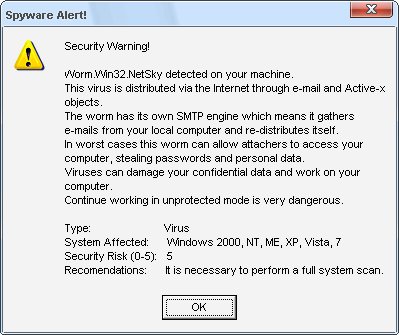
Worm.Win32.Netsky detected on your machine – Fake Spyware Alert
What is more, the troajn will also display a lot of popups, disable Windows Task Manager and change a desktop background to blue with a black window saying that you have a serious infection and need to run a spyware removal tool. However, all of these warnings are fake and supposed to scare you into thinking your computer is in danger. Use the removal guide below to remove this infections and Worm.Win32.Netsky Fake Spyware Alert from your computer for free.
Symptoms in a HijackThis Log
F2 – REG:system.ini: Shell=Explorer.exe logon.exe
F2 – REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon86.exe
O4 – HKLM\..\Run: [winupdate86.exe] C:\WINDOWS\system32\winupdate86.exe
O10 – Unknown file in Winsock LSP: c:\windows\system32\winhelper86.dll
O10 – Unknown file in Winsock LSP: c:\windows\system32\winhelper86.dll
Use the following instructions to remove Worm.Win32.Netsky Fake Spyware Alert
Step 1.
Download HijackThis from here and save it to your Desktop.
If you cannot run HijackThis, then re-download it, but before saving HijackThis.exe, rename it first to explorer.exe and click Save button to save it to desktop.
Run HijackThis. Click “Do a system scan only” button. Now select the following entries by placing a tick in the left hand check box, if present:
F2 – REG:system.ini: Shell=Explorer.exe logon.exe
F2 – REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon86.exe
O4 – HKLM\..\Run: [winupdate86.exe] C:\WINDOWS\system32\winupdate86.exe
Place a checkmark against each of them. Once you have selected all entries, close all running programs then click once on the “fix checked” button. Close HijackThis.
Step 2.
Download LSPFix from here and unzip it to your Desktop.
Run LSPFix. Place a tick in the “I know what i`m doing”.
In the KEEP box select winhelper86.dll and press “>>” button.
Press Finish>> button. When LSPFix is done removing the LSP you will see a summary box. Press OK.
Step 3.
Download MalwareBytes Anti-malware (MBAM). Close all programs and Windows on your computer.
Double Click mbam-setup.exe to install the application. When the installation begins, keep following the prompts in order to continue with the installation process. Do not make any changes to default settings and when the program has finished installing, make sure a checkmark is placed next to Update Malwarebytes’ Anti-Malware and Launch Malwarebytes’ Anti-Malware, then click Finish.
If an update is found, it will download and install the latest version.
Once the program has loaded you will see window similar to the one below.
Malwarebytes Anti-Malware Window
Select Perform Quick Scan, then click Scan, it will start scanning your computer. This procedure can take some time, so please be patient.
When the scan is complete, click OK, then Show Results to view the results. You will see a list of infected items similar as shown below. Note: list of infected items may be different than what is shown in the image below.
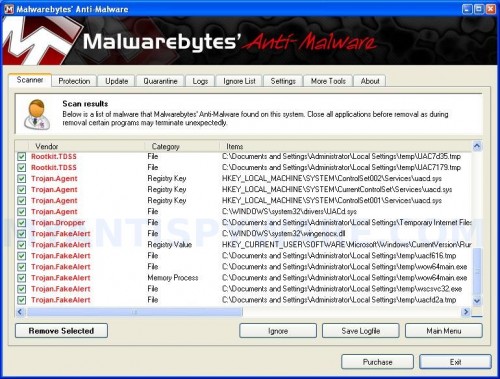
Malwarebytes Anti-malware, list of infected items
Make sure that everything is checked, and click Remove Selected for start removal process. When disinfection is completed, a log will open in Notepad and you may be prompted to Restart.
Note: if you need help with the instructions, then post your questions in our Spyware Removal forum.
The infection creates the following files and folders
c:\windows\system32\AVR10.exe
c:\windows\system32\critical_warning.html
c:\windows\system32\winhelper86.dll
c:\windows\system32\winupdate86.exe
c:\windows\system32\winlogon86.exe
The infection creates the following registry keys and values
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\winupdate86.exe










I’m in the process of doing the final scan, but had the same findings as martin so I’m expecting this to work. Assuming it does, thanks heaps!
alyssa, looks like a trojan has removed a core part of Malwarebytes Anti-malware. Reinstall malwarebytes and run it once again.
thank you so much!
i spent hours doing this before, then your help it did it in seconds!
thank you
Jimmy, looks like you have removed winlogon86.exe.
Boot your PC in the Recovery console (use Windows installation disk).
Once loaded, go to system32 folder and copy userinit.exe to winlogon86.exe
Real also the instruction: How to use Recovery console.
Patrik,
Thanks so so so so much!!!!!
Really sincerely appreciated.
I got logged back on (thanks to your help) and ran HTJ, LDPFix, and Malwarebytes and it took care of everything. Again, so many thanks!
FYI: My laptop was the infected drive and since it didn’t come with WIN install disks I had to purchase a SATA to USB connector ($15) and connect the drive to my desktop. This was a very useful way to preliminarily virus scan, eliminate the DL problems, edit the registry, and get the drive bootable to run all the software mentioned above.
MANY THANKS!!!!!!!!!!!!!!!!!!!!!!!!
ONE LAST THING
When i try to launch System Restore, i get a message saying: “System Restore has been turned off by group policy. To turn on System Restore, contact your domain Administrator.”
My guess is that the malware did this. Any help regarding reactivating System Restore.
MANY THANKS
Hi Patrik
My Dad’s PC had had this issue, ive followed your steps and was looking good until i was unable to log onto any user(as described above) i tried to user the Recovery Console to the best of my ability, but after a reboot it still wasnt working, are you able to write on here what i should follow, from what i understood i used “Copy c:\windows\system32\userinit.exe winlogon86.exe” this obviously isnt correct as i still have the issue, are you able to advise?
Thanks for all your help so far
I cannot thank you enough! I spent all day on this. Thank You!
Patrick, i am kinda having the same issue as jimmy. i can log in but i cannot get to the RegEdit because i see the virus pop up but when i exit out it just gives my a black screen. i would like to keep some of my pictures that i have saved on my computer. is there anything i can do to recover my computer and still keep my pics?
Jimmy, try following:
Click Start->Run, type regedit.exe and press Enter.
Navigate to the following key by expanding the + at left of each key at left::
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows NT\SystemRestoreIn the right-panel:
Right click to DisableConfig and select Delete. Click OK to confirm it.
Right click to the value DisableSR and select Delete. Click OK to confirm it.
Close regedit and reboot your computer.
Try make a new Restore point.
Steven, read comments here.
David, also try repair Windows registry default values using Recovery console. Use the link from my previous comment.
Thanks for that Patrik, i copied what U8MYR!CE posted but the same thing still happens, I tried to complete the steps again but just incase i had completed them inncorrectly, but it asked me to over right the file, so i can assume i did it correctly the first time. Can you think of anything else that might cause me not to be able to log on?
Thanks again
My Home PC has been hit with this, and when I start with the Hijack this, I don’t see any of the listed three files…the closest one I have is:
F2 – REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon32.exe
What should I do?
I suck…I just found the correct message board for that version of the bug, but I still don’t have all the listed files in the Hijack this. Should I just tag the ones I have and keep going?
Yes, I’m clearly a noob.
My Dell didn’t come with any Windows CDs and I am stuck in the logon loop. Do you have any suggestions?
if you are having problems this is one of the best articles I have seen for repairing stuff like this, EXCELLENT!
Hi Patrick, I ran Hijack This but the only file I found that was similar to the 3 you mentioned was F2-REG:system.ini: UserInit=C:\WINDOWS\system32\winlogon32.exe. Should I still tick the box even though it doesn’t end in 86? If I follow the rest of the steps will it still get rid of the problem?
Thanks for the help.
Never mind Patrick, I just found what I needed after searching your site a bit more… wish me luck!
Steven, try copy userinit.exe to logon.exe and winlogon32.exe.
Dean, fix the line using HijackThis.
AEH, attach your hardisk to another computer. Then copy userinit.exe from your Windows/System32 folder to winlogon86.exe.
Attach the disk to your computer and boot it.
I have copied the solution to a dvd disc but does open up, is there another way of opening it. This is just crazy. I am going to have long hard look at my security software
felix, try a flash disk (usb drive).
i tried that and it would not open them
I’ve gotten to Winstock 2 Repair Utility, but the files I have are only:
mswsock.dll, winrnr.dll, mdnsNSP.dll, helper32.dll, and rsvpsp.dll
Which of those is the one I need to remove?
I got my programs transferred over on a thumb drive finally, TY. I no longer get the error that I cannot run my registry editor, it’s infected, I now get the original symptom to it being disabled by administrator. I feel 1000% better about this situation, but could something still be lingering based on this?
Thank you.
Felix,
I got a $6.00 Kingston 2GB DataTraveler and it worked like a charm.
Update: regedit fixed, netstat -a at command prompt is probably as scary as it gets. 🙁
Sarah, remove helper32.dll