Is the email a Scam?
Unfortunately, I need to start our conversation with bad news for you email is an online sextortion scam. Sextortion is another word for “sexual extortion”. Sexual extortion is a type of “phishing attack”, where scammers try to trick people into paying a ransom. Scammers threaten to reveal secretly recorded compromising video if the ransom is not paid.
Scammers use stolen email credentials to send out scam messages to millions of people around the World. The messages are sent to email addresses exposed in previous known data breaches in which the user email address and password has been compromised.
Here’s an example of the “I need to start our conversation with bad news for you” scam email:
QUICK LINKS
- Is the email a Scam?
- Should you pay?
- What to do when you receive the scam message?
- How to spot a phishing email?
- Report Scam Email
The Scam in detail
The “I need to start our conversation with bad news for you” email is an example of a Sextortion scam where victims receive an email that says their email account has been hacked. Scammers falsely claim to have hacked into their device, recorded a video of them watching pornography. The email threatens to release the video to their personal contacts unless they pay a ransom.
In some cases, the email may appear to have been sent from victims’ email address. Scammers are using spoofing technology that masks their real email address by displaying a fake one.
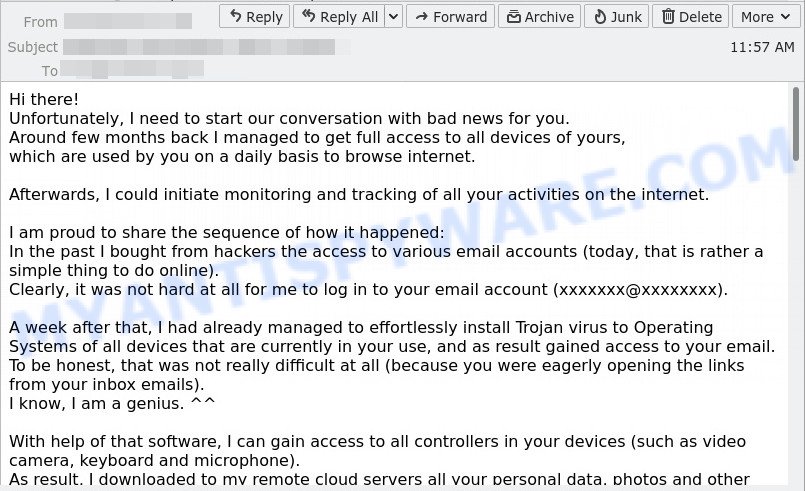
The scam email read as follows:
Hi there!
Unfortunately, I need to start our conversation with bad news for you.
Around few months back I managed to get full access to all devices of yours,
which are used by you on a daily basis to browse internet.Afterwards, I could initiate monitoring and tracking of all your activities on the internet.
I am proud to share the sequence of how it happened:
In the past I bought from hackers the access to various email accounts (today, that is rather a simple thing to do online).
Clearly, it was not hard at all for me to log in to your email account (xxxxxxx@xxxxxxxx).A week after that, I had already managed to effortlessly install Trojan virus to Operating Systems of all devices that are currently in your use, and as result gained access to your email.
To be honest, that was not really difficult at all (because you were eagerly opening the links from your inbox emails).
I know, I am a genius. ^^With help of that software, I can gain access to all controllers in your devices (such as video camera, keyboard and microphone).
As result, I downloaded to my remote cloud servers all your personal data, photos and other information including web browsing history.
Likewise, I have complete access to all your social networks, messengers, chat history, emails, as well as contacts list.
My intelligent virus unceasingly refreshes its signatures (due to its driver-based nature), and hereby stays unnoticed by your antivirus software.Herbey, I believe that now you finally start realizing how I could easily remain unnoticed all this while until this very letter…
While collecting information related to you, I had also unveiled that you are a true fan of porn sites.
You truly enjoy browsing through adult sites and watching horny vids, while playing your dirty solo games.Bingo! I also recorded several filthy scenes with you in the main focus and montaged some dirty videos, which demonstrate your passionate masturbation and cum sessions.
In case you still don’t believe me, all I need is just one-two mouse clicks to make all your unmasking videos become available to your friends, colleagues, and even relatives.
Well, if you still doubt me, I can easily make recorded videos of your orgasms become a public.
I truly believe that you surely would avoid that from happening,
taking in consideration the type of the XXX videos you love watching, (you are clearly aware of what I mean) it will result in a huge disaster for you.Well, there is still a way to settle this tricky situation in a peaceful manner:
You will need to transfer $960 USD to my account (refer to Bitcoin equivalent based on the exchange rate at the moment transfer),
so once funds transfer is complete, I will straight away proceed with deleting all that dirty content from servers once and for all.Afterwards, you can consider that we never met before. You have my honest word, that all the harmful software will also be deactivated and deleted from all your devices currently in use.
Worry not, I keep my promises.
That is truly a win-win solution that comes at a relatively reduced cost, mostly knowing how much effort I spent on monitoring your profile and traffic for a considerably long time.
In event that you have no idea about means of buying and transferring bitcoins – don’t hesitate to use any search engine for your assistance (e.g., Google, Yahoo, Bing, etc.).My bitcoin wallet is as follows: 19yaJM8qhsyXnwoQP7zQbMkqJStoMYxPmE
I have allocated 48 hours for you to do that, and the timer started right after you opened this very email (2 days to be exact).
Don’t even think of doing anything of the following:
*Abstain from attempting to reply me (this email was created by me inside your inbox page and the return address was generated accordingly).
*Abstain from attempting to get in touch with police or any other security services. Moreover, don’t even think of sharing this to you friends.
Once I discover this (apparently, that is absolutely easy for me, taking in consideration that I have complete control over all systems you use) – your kinky video will straight away be made public.
*Don’t even think of attempting to find me – that is completely useless. Don’t forget that all cryptocurrency transactions remain completely anonymous.
*Don’t attempt reinstalling the OS on all your devices or getting rid of them. That won’t lead you to success either, because I have already saved all videos at my remote servers as a backup.Things you should not be concerned about:
*That your funds transfer won’t reach my wallet.
– Worry not, I can see everything, hence after you finish the transfer, I will get a notification right away
(trojan virus of mine uses a remote-control feature, which functions similarly to TeamViewer).
*That I will still distribute your videos although you make the funds transfer.
– My word, I have no intention or interest in continuing making your life troublesome.
Anyway, If I truly wanted that, it would happen long time ago without me notifying you!Everything can be settled in a peaceful and just way!
And lastly… make sure you don’t get caught afterwards in such type of incidents anymore!
My fair advice – ensure you change all your passwords on a regular basis.
Scam emails may also contain information such as passwords designed to trick victims into thinking the email is genuine. Usually passwords are appended to these emails as proof, that is, if the password was actually used by the victim, then what is described in the email is true. Scammers get these real passwords by buying them on darknet.
Typically, sextortion scams are sent via email, thousands at a time, and are part of larger spam campaigns. As with many other types of scams, scammers are evolving their methods to deliver their messages to potential victims. Such attacks can be personalized and sent out in smaller numbers to avoid detection. Scammers can use reputable services, change and personalize the content of each message, and avoid including links or attachments – all in an attempt to bypass security.
There are many sextortion scams circulating via email. Scammers often change the content of emails in order to deceive victims and bypass the security system. I hacked your device, I’m a hacker who hacked your operating system, I have to share bad news with you EMAIL are other examples of sextortion scam emails.
- Let me get straight to the point Email Scam
- Leaked uncensored photos from your device Email Scam
- Your personal data has leaked due to suspected harmful activities. Email Scam
- I hacked your device EMAIL SCAM
- “There is an overdue payment under your name. Please, settle your debts ASAP.” email is a SCAM
To summarize, the “I need to start our conversation with bad news for you” email is a SCAM. It can lead to financial losses and other serious problems.
Should you pay?
The best advice is: Don’t pay the ransom and do not reply! Sometimes scammers will escalate if you reply. If you receive the sextortion email scam, just ignore the scammers. The best way to deal with the scam email is simply to move it to trash!

Threat Summary
| Name | I need to start our conversation with bad news for you SCAM |
| Type | Sextortion, Phishing, Bitcoin Blackmail Scam |
| Ransom amount | $960 |
| Bitcoin Address | 1PMP68a3iw2X4Ruq2XoENc1jNNaGVELCh6, 19yaJM8qhsyXnwoQP7zQbMkqJStoMYxPmE |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like I need to start our conversation with bad news for you, our computer security experts recommend follow some easy steps below |
What to do when you receive the scam email
We advice to someone who gets this fraudulence message:
- Do not panic.
- Don’t send any payments to the scammer.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- If you recognize your password in a scam email, then immediately change the password. Use Have I Been Pwned (https://haveibeenpwned.com/) to check if your email address/password has been compromised.
- Report Scam Email to the FTC at https://www.ftc.gov/.
- Mark the scam email as SPAM/JUNK and delete it.
- Scan your computer for malware.
If you suspect that your computer is infected with spyware, you accidentally clicked on a link in the scam email, or just want to scan your computer for malware, then use one of the free malware removal tools.
How to spot a phishing email?
Phishing emails often share common characteristics; they are designed to trick victims into clicking on a phishing link or opening a malicious attachment. If you know these characteristics, you can detect phishing emails and prevent identity theft.
Here are some ways to recognize a phishing email
- Inconsistencies in Email Addresses. The most obvious way how to spot a scam email is finding inconsistencies in email addresses and domain names. If the email claims to be from a reputable company, like Amazon or PayPal, but the email is being sent from a public email domain, such as “gmail.com” it’s probably a scam.
- The domain name is misspelt. Look carefully for any subtle misspellings in the domain name. Like arnazon.com where the “m” has been replaced by “rn”, or paypa1.com, where the “l” has been replaced by “1”. These are common tricks of scammers.
- Generic greetings. If the email starts with a generic “Dear”, “Dear sir” or “Dear madam” that is a warning sign that it might not really be your shopping site or bank.
- Suspicious links. If you have the slightest suspicion an email may be a scam, do not click on the links you see. Instead, hover over the link, but don’t click it. This will pop up a small box that contains the actual URL. This works on image links as well as text links.
- Unexpected attachments. Email attachments should always be verified before clicking. Any attachments should be scanned for viruses – especially if they have an unfamiliar extension or one commonly associated with malware (.zip, .exe, .scr, etc.).
- The email creates a sense of urgency. Creating a false sense of urgency is a common trick of phishing emails. Be suspicious of emails that claim you must call, open an attachment or click a link immediately.
Report Scam Email
If you receive a scam email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. This helps us to warn users about current scams, monitor trends and disrupt scams where possible.
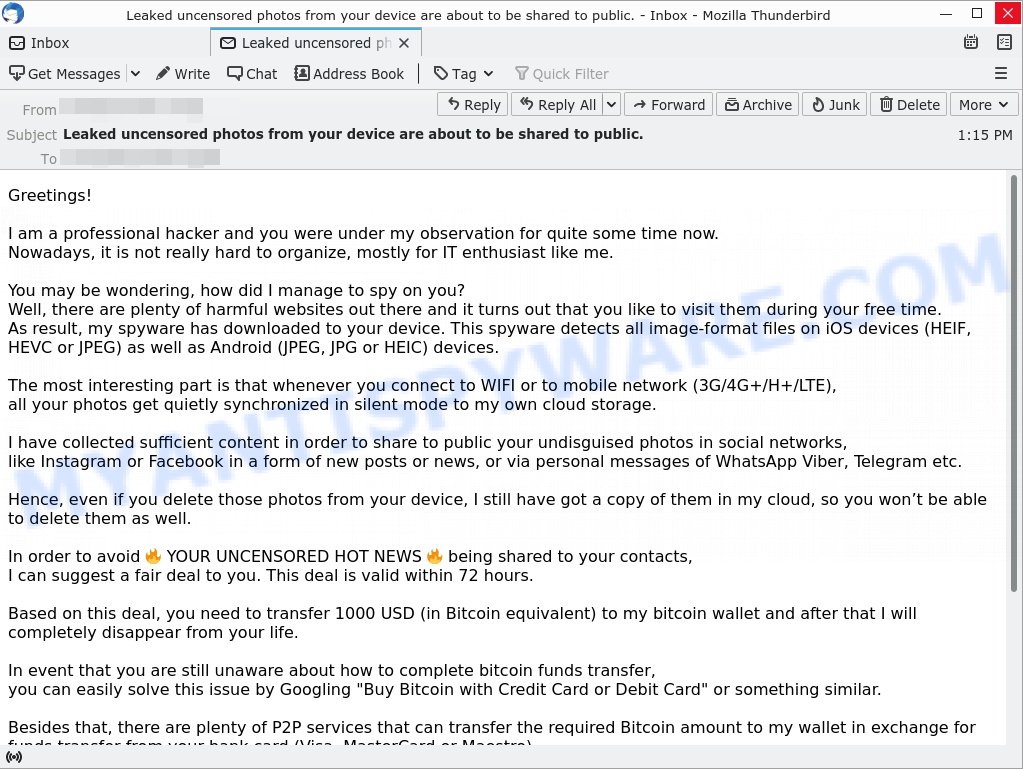
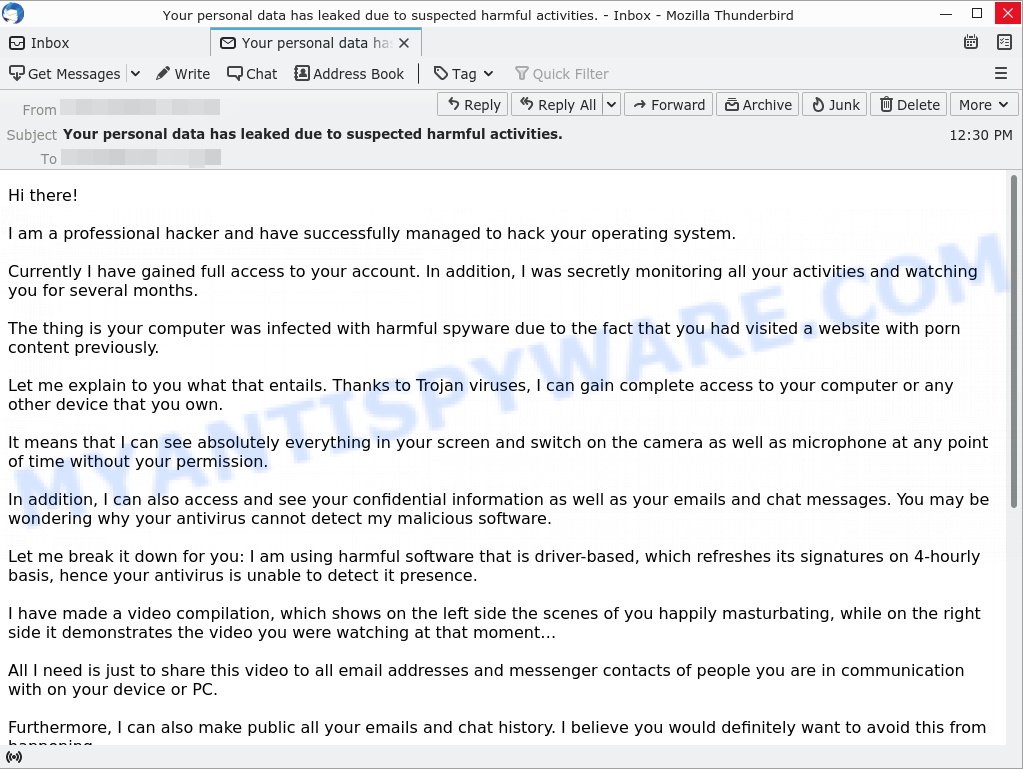
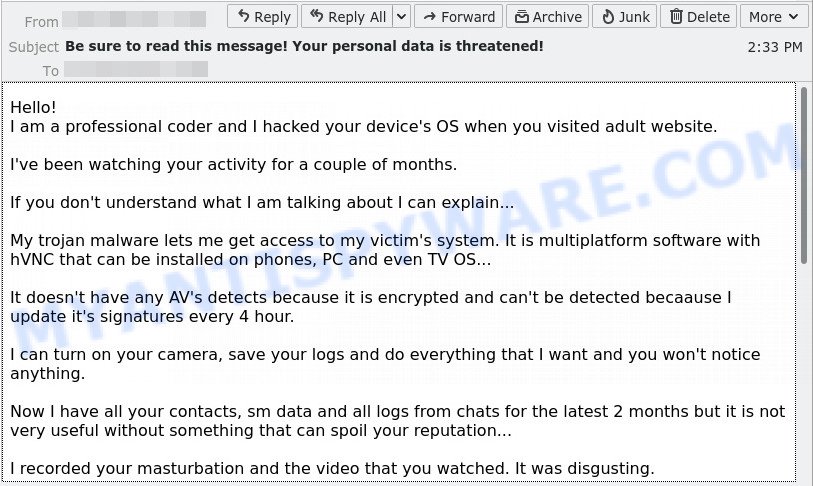
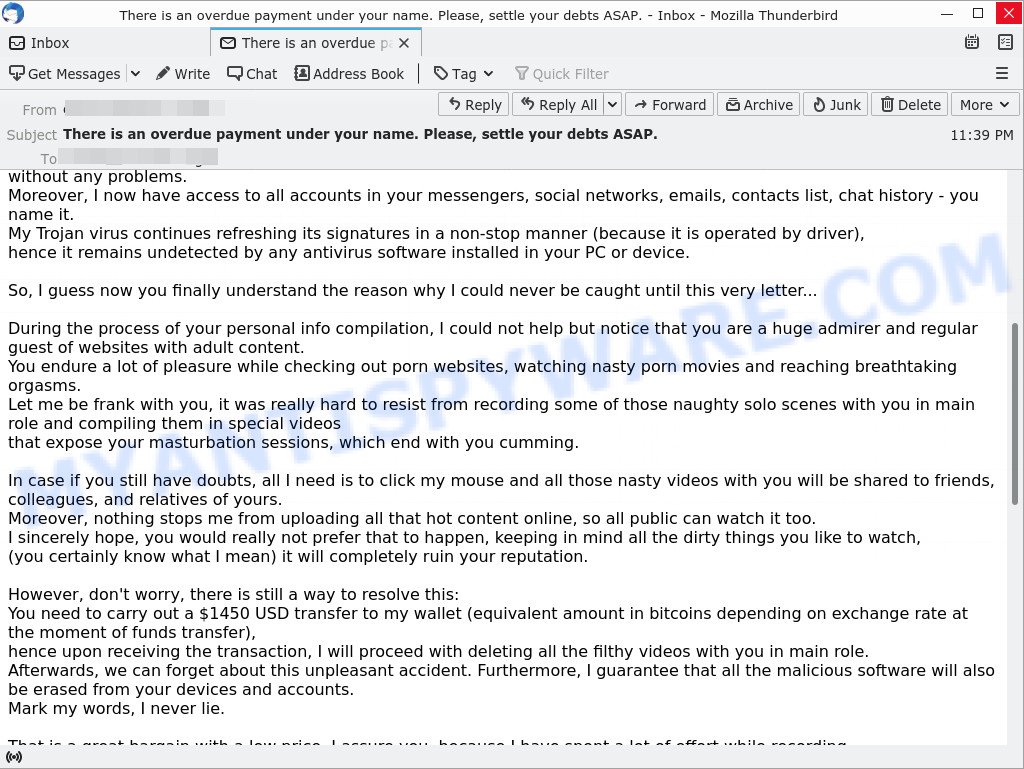












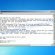
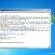

I got one of these and a follow up email to a bitcoin wallet on goggle drive. The first email can from a spoof of one of my own email and the second from:
Brian Clark (Google Docs)
reply-to: Reply
to: JamesPillar23 at gmail.com
date: Feb 3, 2023, 8:00 AM
subject: 💫 Last warning a… – Hey guys! I have a new Bitcoin transa…
mailed-by: docos.bounces.google.com
signed-by: docs.google.com
There are a few differences but basically the same.
Hi there!
Unfortunately, I need to start our conversation with bad news for you.
Around few months back I managed to get full access to all devices of yours,
which are used by you on a daily basis to browse internet.
Afterwards, I could initiate monitoring and tracking of all your activities on the internet.
I am proud to share the sequence of how it happened:
In the past I bought from hackers the access to various email accounts (today, that is rather a simple thing to do online).
Clearly, it was not hard at all for me to log in to your email account (joe@totalprotective.com).
A week after that, I had already managed to effortlessly install Trojan virus to Operating Systems of all devices that are currently in your use,
and as result gained access to your email.
To be honest, that was not really difficult at all (because you were eagerly opening the links from your inbox emails).
I know, I am a genius. (=
With help of that software, I can gain access to all controllers in your devices (such as video camera, keyboard and microphone).
As result, I downloaded to my remote cloud servers all your personal data, photos and other information including web browsing history.
Likewise, I have complete access to all your social networks, messengers, chat history, emails, as well as contacts list.
My intelligent virus unceasingly refreshes its signatures (due to its driver-based nature), and hereby stays unnoticed by your antivirus software.
Herbey, I believe that now you finally start realizing how I could easily remain unnoticed all this while until this very letter…
While collecting information related to you, I had also unveiled that you are a true fan of porn sites.
You truly enjoy browsing through adult sites and watching horny vids, while playing your dirty solo games.
Bingo! I also recorded several filthy scenes with you in the main focus and montaged some dirty videos,
which demonstrate your passionate masturbation and cum sessions.
In case you still don’t believe me, all I need is just one-two mouse clicks to make all your unmasking videos become available to your friends,
colleagues, and even relatives.
Well, if you still doubt me, I can easily make recorded videos of your orgasms become a public.
I truly believe that you surely would avoid that from happening, taking in consideration the type of the XXX videos you love watching,
(you are clearly aware of what I mean) it will result in a huge disaster for you.
Well, there is still a way to settle this tricky situation in a peaceful manner:
You will need to transfer $1450 USD to my account (refer to Bitcoin equivalent based on the exchange rate at the moment transfer),
so once funds transfer is complete, I will straight away proceed with deleting all that dirty content from servers once and for all.
Afterwards, you can consider that we never met before. You have my honest word,
that all the harmful software will also be deactivated and deleted from all your devices currently in use. Worry not, I keep my promises.
That is truly a win-win solution that comes at a relatively reduced cost,
mostly knowing how much effort I spent on monitoring your profile and traffic for a considerably long time.
In event that you have no idea about means of buying and transferring bitcoins –
don’t hesitate to use any search engine for your assistance (e.g., Google, Yahoo, Bing, etc.).
My bitcoin wallet is as follows: 18z7GJZjP2eAK4M2DvmzsEAYFFndnBEi7o
An important notice: I have specified my Bitcoin wallet with spaces,
hence once you carry out a transfer, please make sure that you key-in my bitcoin address without spaces to be sure that your funds successfully reach my wallet.
I have allocated 48 hours for you to do that, and the timer started right after you opened this very email (2 days to be exact).
Don’t even think of doing anything of the following:
! Abstain from attempting to reply me (this email was created by me inside your inbox page and the return address was generated accordingly).
! Abstain from attempting to get in touch with police or any other security services. Moreover, don’t even think of sharing this to you friends.
Once I discover this (apparently, that is absolutely easy for me, taking in consideration that I have complete control over all systems you use) –
kinky video will straight away be made public.
! Don’t even think of attempting to find me – that is completely useless. Don’t forget that all cryptocurrency transactions remain completely anonymous.
! Don’t attempt reinstalling the OS on all your devices or getting rid of them. That won’t lead you to success either,
because I have already saved all videos at my remote servers as a backup.
Things you should not be concerned about:
! That your funds transfer won’t reach my wallet.
– Worry not, I can see everything, hence after you finish the transfer, I will get a notification right away
(trojan virus of mine uses a remote-control feature, which functions similarly to TeamViewer).
! That I will still distribute your videos although you make the funds transfer.
– My word, I have no intention or interest in continuing making your life troublesome.
Anyway, If I truly wanted that, it would happen long time ago without me notifying you!
Everything can be settled in a peaceful and just way!
And lastly… make sure you don’t get caught afterwards in such type of incidents anymore!
My fair advice – ensure you change all your passwords on a regular basis.