What is “Don’t miss your unsettled payment. Complete your debt payment now.” EMAIL?
Don’t miss your unsettled payment. Complete your debt payment now. is a ‘sextortion’ scam. Sextortion is a scam that targets victims via Email/SMS/text messages. This scam tries to guilt victims into paying off someone claiming to have secretly recorded video or compromising information. Scammers use a database of stolen email credentials to send out scam messages to millions of people around the World. The messages are sent to email addresses exposed in previous known data breaches in which the user email address and password has been compromised.
In some cases, sextortion scam emails may contain real passwords that the victim has used in the past (or even uses). Usually passwords are appended to these messages as proof, that is, if the password was actually used by the victim, then what is described in the email is true. Scammers get these real passwords by buying them on darknet.
The “Don’t miss your unsettled payment. Complete your debt payment now.” email is a sextortion SCAM
QUICK LINKS
- What is “Don’t miss your unsettled payment. Complete your debt payment now.” EMAIL?
- Should you pay?
- What to do when you receive the scam email?
The Scam Email in detail
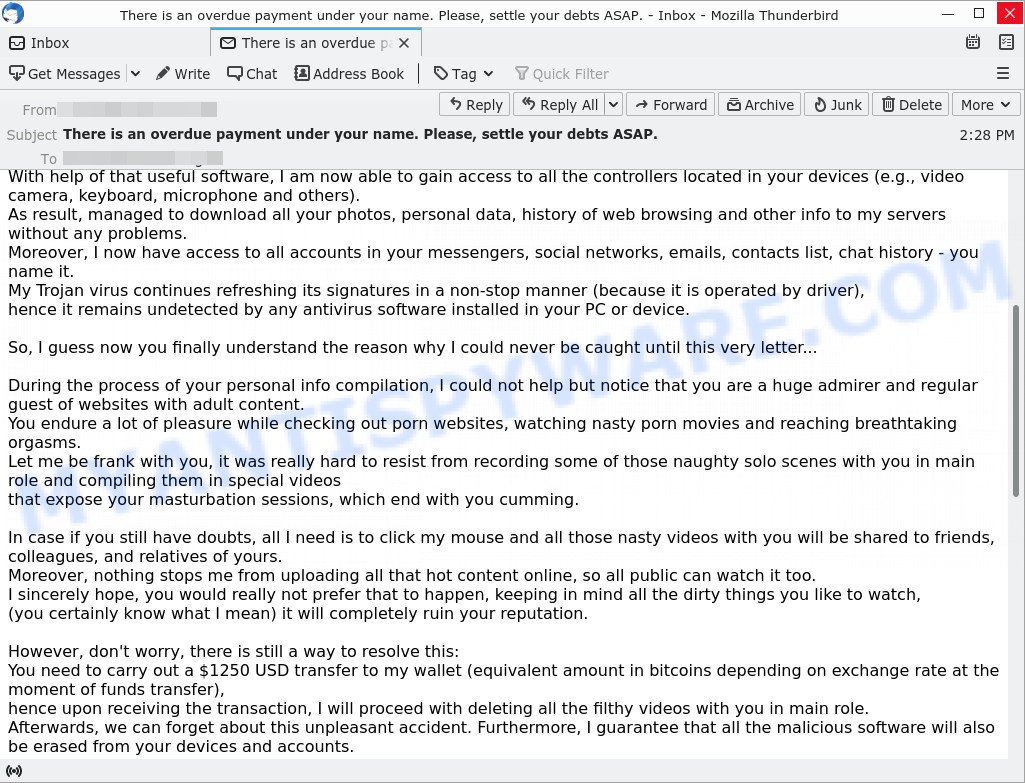
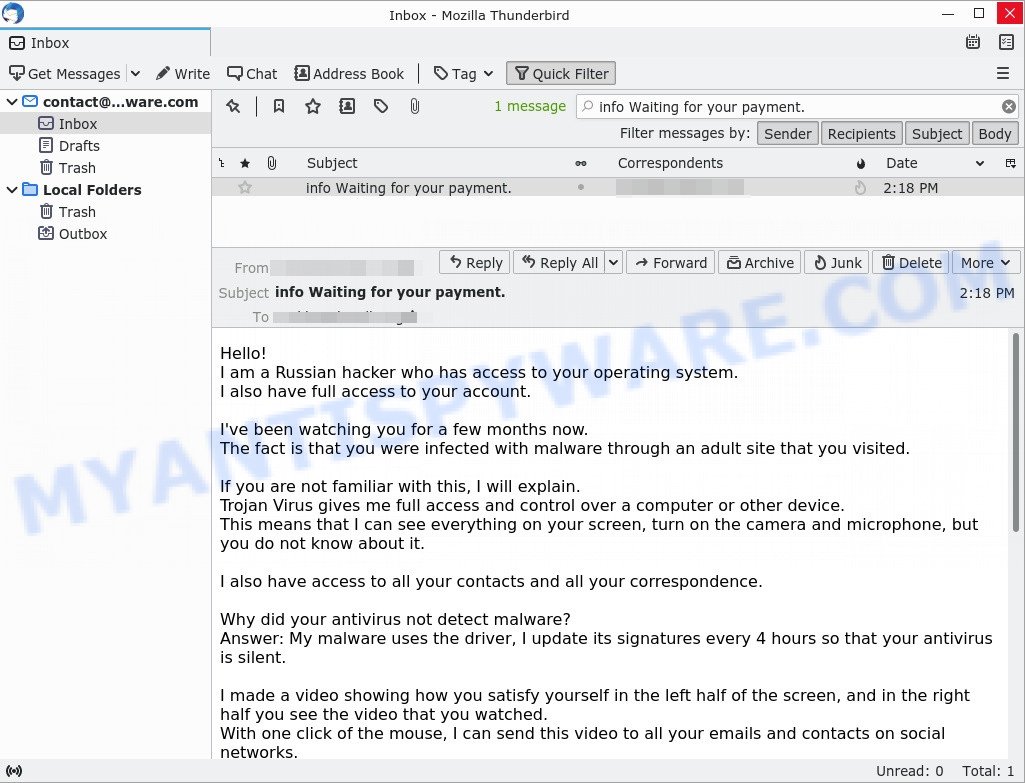
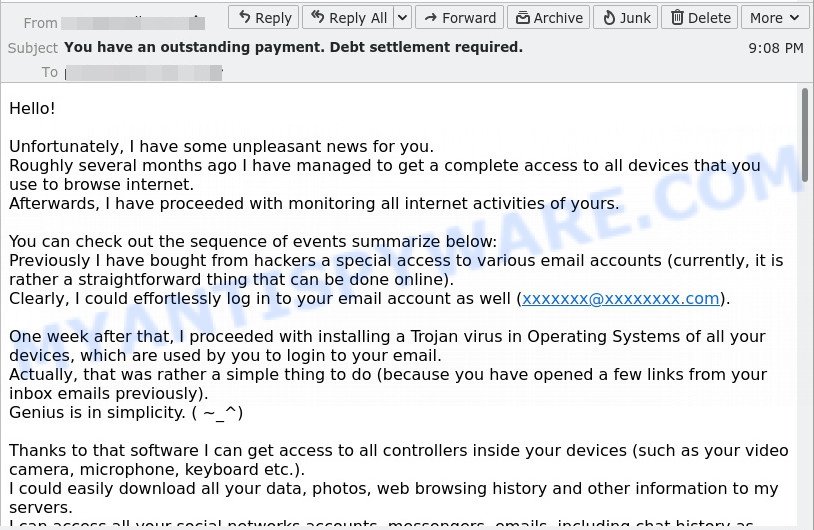
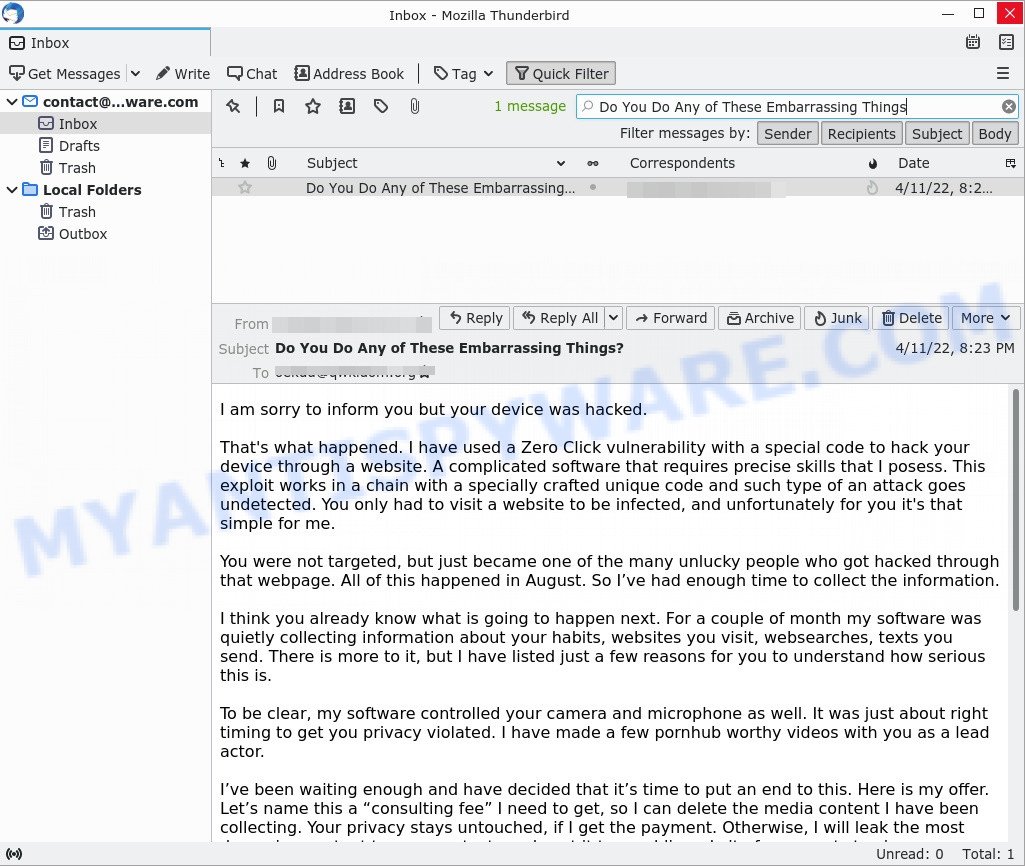
The “Don’t miss your unsettled payment. Complete your debt payment now.” scam is not the only one of its kind, there are many similar ones. They all have similar features: spelling and grammatical errors, statement that the victim’s computer and webcam were hacked, threats that the attackers recorded a compromising video, and a ransom demand.
Depending on the scam, victims are given 24 to 48 hours to pay a ransom in Bitcoin. The sextortion scams also contain claims that the victim’s contact information was stolen, allegedly the hacker copied the victim’s contact list and social media credentials. And finally, Sextortion scams contain threats, the victims must pay a ransom, or compromising materials will be sent to their contacts.
To summarize, the “Don’t miss your unsettled payment. Complete your debt payment now.” message is just a sextortion scam. All claims and threats made in this email message are false. Therefore, recipients are not in danger, this email and similar emails can be safely ignored.
Text presented in the scam email:
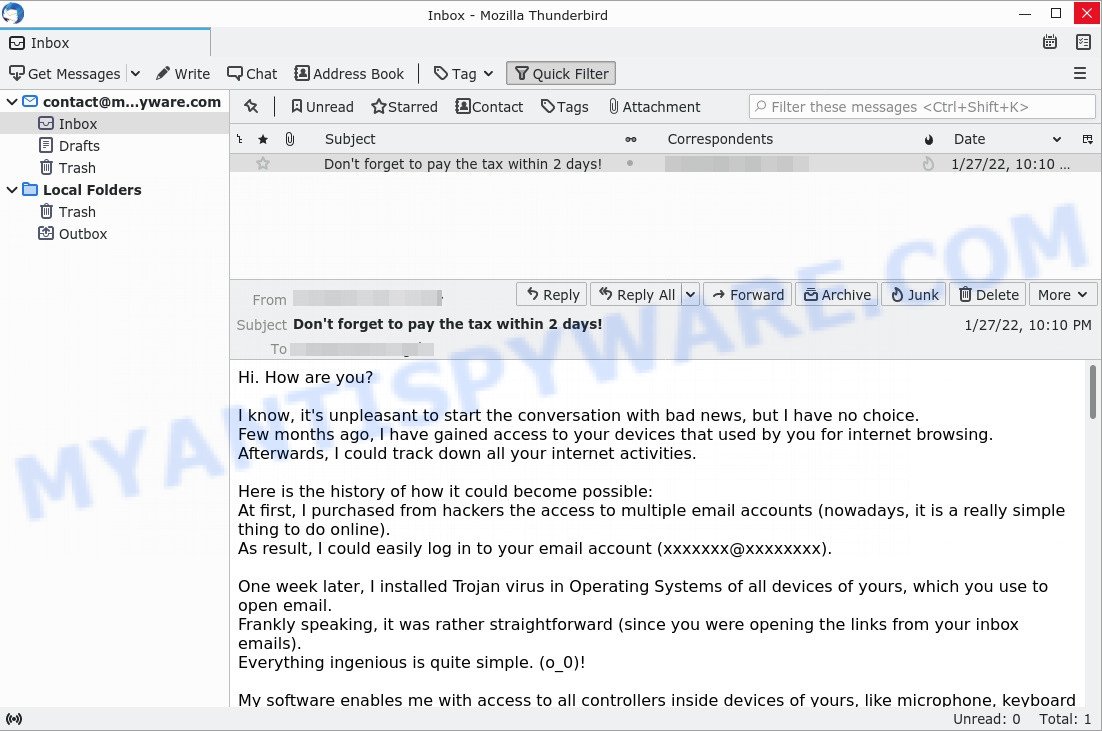
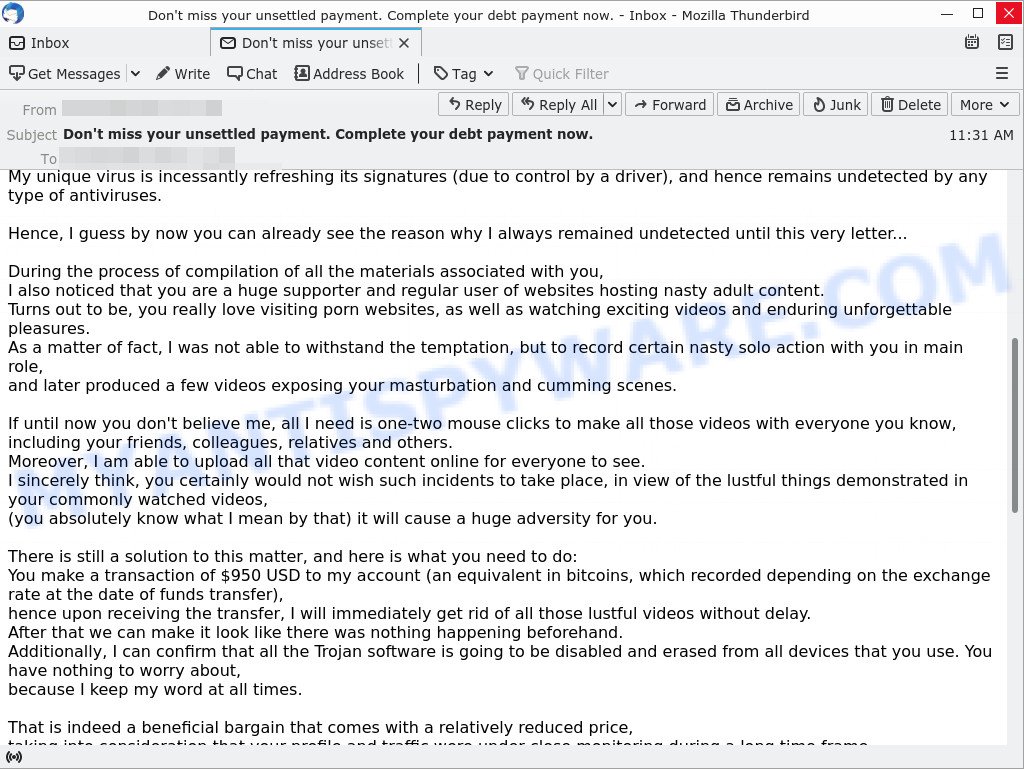
Hi there!
I regret to inform you about some sad news for you.
Approximately a month or two ago I have succeeded to gain a total access to all your devices utilized for browsing internet.
Moving forward, I have started observing your internet activities on continuous basis.Go ahead and take a look at the sequence of events provided below for your reference:
Initially I bought an exclusive access from hackers to a long list of email accounts (in today’s world, that is really a common thing, which can arranged via internet).
Evidently, it wasn’t hard for me to proceed with logging in your email account (xxxxxxxx@xxxxxxxx.com).Within the same week, I moved on with installing a Trojan virus in Operating Systems for all devices that you use to login to email.
Frankly speaking, it wasn’t a challenging task for me at all (since you were kind enough to click some of the links in your inbox emails before).
Yeah, geniuses are among us.Because of this Trojan I am able to gain access to entire set of controllers in devices (e.g., your video camera, keyboard, microphone and others).
As result, I effortlessly downloaded all data, as well as photos, web browsing history and other types of data to my servers.
Moreover, I have access to all social networks accounts that you regularly use, including emails, including chat history, messengers, contacts list etc.
My unique virus is incessantly refreshing its signatures (due to control by a driver), and hence remains undetected by any type of antiviruses.Hence, I guess by now you can already see the reason why I always remained undetected until this very letter…
During the process of compilation of all the materials associated with you,
I also noticed that you are a huge supporter and regular user of websites hosting nasty adult content.
Turns out to be, you really love visiting porn websites, as well as watching exciting videos and enduring unforgettable pleasures.
As a matter of fact, I was not able to withstand the temptation, but to record certain nasty solo action with you in main role,
and later produced a few videos exposing your masturbation and cumming scenes.If until now you don’t believe me, all I need is one-two mouse clicks to make all those videos with everyone you know,
including your friends, colleagues, relatives and others.
Moreover, I am able to upload all that video content online for everyone to see.
I sincerely think, you certainly would not wish such incidents to take place, in view of the lustful things demonstrated in your commonly watched videos,
(you absolutely know what I mean by that) it will cause a huge adversity for you.There is still a solution to this matter, and here is what you need to do:
You make a transaction of $950 USD to my account (an equivalent in bitcoins, which recorded depending on the exchange rate at the date of funds transfer),
hence upon receiving the transfer, I will immediately get rid of all those lustful videos without delay.
After that we can make it look like there was nothing happening beforehand.
Additionally, I can confirm that all the Trojan software is going to be disabled and erased from all devices that you use. You have nothing to worry about,
because I keep my word at all times.That is indeed a beneficial bargain that comes with a relatively reduced price,
taking into consideration that your profile and traffic were under close monitoring during a long time frame.
If you are still unclear regarding how to buy and perform transactions with bitcoins – everything is available online.Below is my bitcoin wallet for your further reference: 1DnDfzKAjTYWcn6nCVfkXLh5RRaGBUZ7nE
All you have is 48 hours and the countdown begins once this email is opened (in other words 2 days).
The following list includes things you should remember and avoid doing:
> There’s no point to try replying my email (since this email and return address were created inside your inbox).
> There’s no point in calling police or any other types of security services either. Furthermore, don’t you dare sharing this info with any of your friends.
If I discover that (taking into consideration my skills, it will be really simple, because I control all your systems and continuously monitor them) –
your nasty clip will be shared with public straight away.
> There’s no point in looking for me too – it won’t result in any success. Transactions with cryptocurrency are completely anonymous and untraceable.
> There’s no point in reinstalling your OS on devices or trying to throw them away. That won’t solve the issue,
since all clips with you as main character are already uploaded on remote servers.Things that may be concerning you:
> That funds transfer won’t be delivered to me.
Breathe out, I can track down everything right away, so once funds transfer is finished,
I will know for sure, since I interminably track down all activities done by you (my Trojan virus controls all processes remotely, just as TeamViewer).
> That your videos will be distributed, even though you have completed money transfer to my wallet.
Trust me, it is worthless for me to still bother you after money transfer is successful. Moreover, if that was ever part of my plan, I would do make it happen way earlier!We are going to approach and deal with it in a clear manner!
In conclusion, I’d like to recommend one more thing… after this you need to make certain you don’t get involved in similar kind of unpleasant events anymore!
My recommendation – ensure all your passwords are replaced with new ones on a regular basis.
Should you pay?

The best advice is: Don’t pay the ransom! If you receive the sextortion scam email, just ignore the scammers’ empty threats. The best way to deal with the scam email is simply to move it to trash!
Threat Summary
| Name | Don’t miss your unsettled payment. Complete your debt payment now. SCAM |
| Type | Sextortion, Phishing, Bitcoin Blackmail Scam |
| Ransom amount | $1370, $1950, $950, $1200, $1490 (USD) |
| Bitcoin Address | 1P5vLEEuGawo33WLs3pVdxTuyjqt7Ymf9C, 1EtgSZtpMMY3AEbAoctNYfRYaY3NXrZbAj, 1DnDfzKAjTYWcn6nCVfkXLh5RRaGBUZ7nE, 1HmvPgkmdkaSr6R1KA31fW8kpw1EvZJo9H, 1r8KDQsoFUWLdV1D2L1vc66YibNDrrYys |
| Distribution method | spam email campaigns |
| Removal | If you gets an email like There is an overdue payment under your name, our computer security experts recommend follow some easy steps below |
Scam examples
There are many variants of the sextortion scam, scammers constantly change the text of emails so that spam filters do not work. In addition, in some cases, criminals can translate the text of sextortion messages into other languages, thus targeting a specific group of Internet users. Have you recently noticed that I have e-mailed you from your account, I am sorry to inform you that your device was compromised, Unfortunately, there are some bad news for you are other examples of sextortion scam emails. Such emails are also often used to distribute ransomware, trojans, worms and other malware. Regardless of what is in the scam emails, scammers and the criminals behind them use these emails to generate profit by tricking the users, the recipients of these emails.
- “There is an overdue payment under your name. Please, settle your debts ASAP.” email is a SCAM
- “I am a Russian hacker who has access to your operating system” email message is a sextortion SCAM
- “You have an outstanding payment. Debt settlement required.” Email SCAM
- “Do You Do Any of These Embarrassing Things” email message is a sextortion SCAM
- Don’t forget to pay the tax within 2 days EMAIL SCAM
What to do when you receive the scam email
We advice to someone who gets this fraudulence message:
- Do not panic.
- Do not pay a ransom.
- If there’s a link in the scam email, do not click it, otherwise you could unwittingly install malware or ransomware on your computer.
- Report the email spam to the FTC at https://www.ftc.gov/.
- Mark the scam email as SPAM/JUNK and delete it.
- Scan your computer for malware.
- Install an anti-phishing software.
How to scan your computer for malware
If you suspect that your computer is infected with malware, you accidentally clicked on a link in the scam email, or just want to scan your computer, then use one of the best free malware removal tools. MalwareBytes is an antivirus that can be used to perform a virus scan, detect and remove almost all the forms of malicious programs including ransomware, trojans, worms, adware, browser hijackers, potentially unwanted software and spyware. MalwareBytes has real-time protection that can defeat most malicious software and ransomware. Despite so many features, it does not reduce the performance of your computer. You can use MalwareBytes with any other antivirus without any conflicts.
First, please go to the link below, then click the ‘Download’ button in order to download the latest version of MalwareBytes.
327319 downloads
Author: Malwarebytes
Category: Security tools
Update: April 15, 2020
When the downloading process is done, close all windows on your computer. Further, launch the file named MBSetup. If the “User Account Control” dialog box pops up like below, click the “Yes” button.
It will show the Setup wizard which will assist you install MalwareBytes on the computer. Follow the prompts and do not make any changes to default settings.
After the setup is complete successfully, press “Get Started” button. Then MalwareBytes AntiMalware will automatically run and you can see its main window such as the one below.
Next, click the “Scan” button for scanning your computer for malicious software and other security threats. A system scan can take anywhere from 5 to 30 minutes, depending on your computer. While MalwareBytes is scanning, you can see how many objects it has identified as threat.
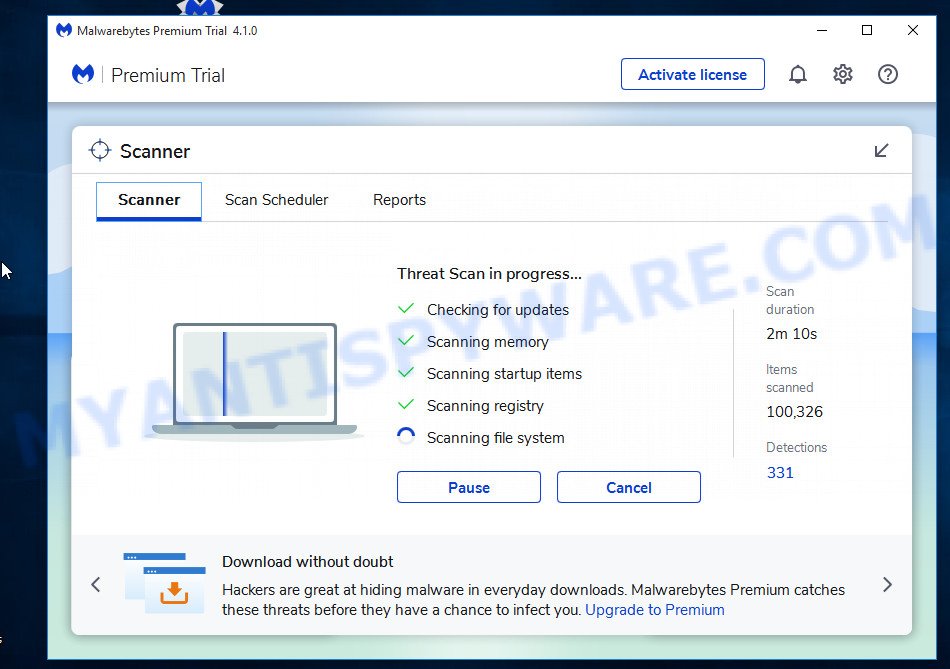
When the scanning is done, the results are displayed in the scan report. In order to remove all threats, simply press “Quarantine” button.
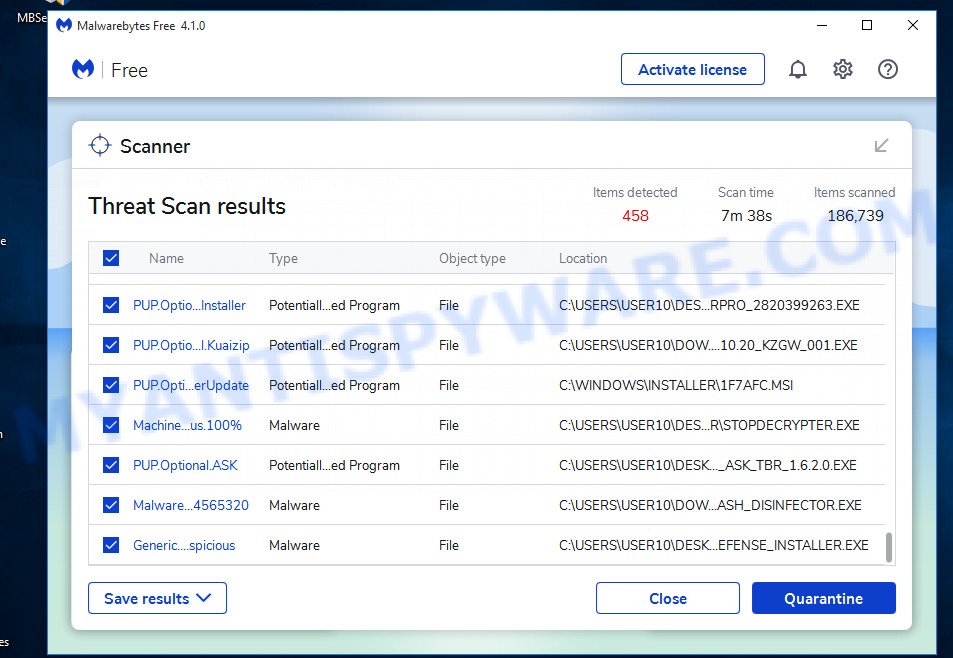
We suggest you look at the following video, which completely explains the process of using MalwareBytes to remove malicious software.
If you are having issues with malware removal, then check out Kaspersky virus removal tool. It can easily remove trojans, spyware, browser hijackers, adware, worms and ransomware with all their components such as files, folders and registry entries. Visit the page linked below to download the latest version of Kaspersky virus removal tool for Windows.
129312 downloads
Author: Kaspersky® lab
Category: Security tools
Update: March 5, 2018
How to protect yourself from phishing, malicious and misleading websites
If you want to protect yourself from phishing sites, install an ad blocking program like AdGuard. It can block malicious and misleading websites, stop unwanted ads and pop-ups while using Internet Explorer, Google Chrome, Firefox and Edge. So, if you like to surf the Internet and want to protect your computer from phishing scams, then AdGuard is your best choice.
Installing AdGuard is very easy. First you’ll need to download AdGuard by clicking on the link below.
26913 downloads
Version: 6.4
Author: © Adguard
Category: Security tools
Update: November 15, 2018
After downloading it, double-click the downloaded file to start it. The “Setup Wizard” window will show up on the computer screen as displayed below.
Follow the prompts. AdGuard will then be installed and an icon will be placed on your desktop. A window will show up asking you to confirm that you want to see a quick guide as displayed on the screen below.

Click “Skip” button to close the window and use the default settings, or press “Get Started” to see an quick guidance which will assist you get to know AdGuard better.
Each time, when you start your system, AdGuard will start automatically and stop unwanted advertisements, block phishing, as well as other harmful or misleading websites. For an overview of all the features of the application, or to change its settings you can simply double-click on the AdGuard icon, which can be found on your desktop.
Finish words
If you receive a scam email that is similar but not the same as the example above, make sure you remove any personal info in this message, then post it as comment on this article. This helps us to warn users about current scams, monitor trends and disrupt scams where possible.