What is YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES?
YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES is a phishing SCAM that masquerades as a Google Chrome notification and aimed at Android users worldwide. It claims that the visitor’s device is infected due to recently visited phishing (malware) sites and recommends to follow some instructions to secure the phone. In fact, there are no websites that can detect the presence of viruses on a user’s device (computer, Android phone, iPhone, etc), so the alerts about ‘infected device’ are fake. The purpose of this scam is to trick users to install untrustworthy apps, among which may be malware, trojans, browser hijackers and adware.
Usually, users end up on YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES and similar scams by going to a misspelled URL or, clicking on a fake link. In addition, they can be redirected to this scam by malicious advertisements (malvertising) and Adware.
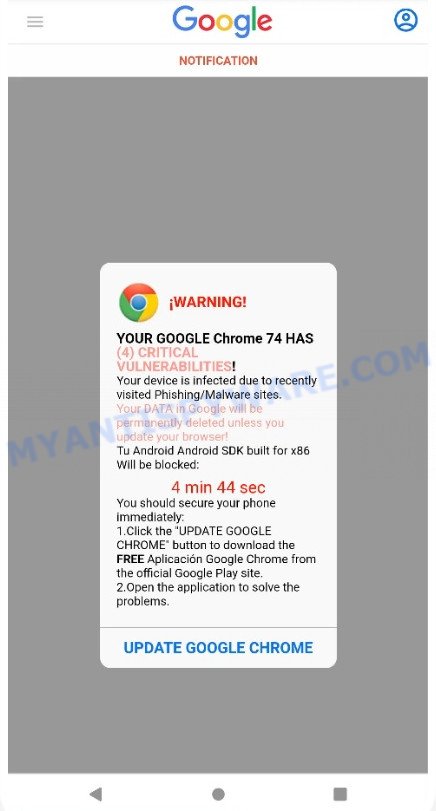
YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups are a scam
QUICK LINKS
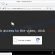
When users land on one of the sites running the “YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES” scam, they are presented with an alert disguised as a Google Chrome notification. This fake notification informs that the user’s device is infected as a result of visiting a phishing site. The user is prompted to download the FREE Google Chrome from the official Google Play site to update the browser and secure the phone. This message also contains a warning that if the recommended actions are not taken, the phone will be locked.
Text presented in the scam pop-up:
NOTIFICATION
¡WARNING!
YOUR GOOGLE Chrome 94 HAS
(4) CRITICAL VULNERABILITIES!
Your device is infected due to recently visited Phishing/Malware sites.Your DATA in Google will be permanently deleted unless you update your browser!
Tu Android Phone Will be blocked:
You should secure your phone immediately:
1.Click the “UPDATE GOOGLE CHROME” button to download the FREE Aplicación Google Chrome from the official Google Play site.
2.Open the application to solve the problems.
UPDATE GOOGLE CHROME
The scam can promote legitimate software, but is more often used to distribute potentially unwanted applications (PUAs). Although these apps look harmless, they often have malicious capabilities. Such applications can forcibly redirect users to deceptive sites, promise fake features that they really do not have (for example, remove viruses, block ads), display unwanted ads, change browser settings to promote fake search engines, collect user personal data (including logins and passwords, browser history) and so on.
To summarize, the “YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES” scam can lead to malware infection, financial losses, theft of personal information and other serious problems.
How to protect against the YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES scam
To avoid becoming a victim of scammers, it is important to always keep in mind:
- There are no sites that can detect viruses and other security threats.
- Never install software promoted by scam sites, as it can be useless, and besides, it can be dangerous for you and your computer.
- Close the “YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES” scam as soon as it appears on your device screen. Scammers can prevent you from closing it in various ways. In such cases, close your browser using Recent applications screen. If the next time you launch the browser, it prompts you to restore the previous session, abandon it, otherwise this scam will reopen on your screen.
Threat Summary
| Name | YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES |
| Type | scam, phishing, fake alerts |
| Fake claims | Your device is infected due to recently visited Phishing/Malware sites, Your DATA in Google will be permanently deleted unless you update your browser, Android Phone Will be blocked |
| Symptoms |
|
| Removal | YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES removal guide |
Cleaner Update for Android is Recommended, Your IP address & personal information might be exposed, Your iPhone Has Been Hacked are other scams aimed at tricking victims into downloading/installing and/or purchasing untrustworthy apps. Some of these scams are positioned as a legitimate Apple, Google or Microsoft pages, but in fact have nothing to do with these companies.
If your browser redirects to the YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES scam regularly, then it is possible that Adware or PUAs are installed on your device. Adware is type of malware that can cause problems for your Android device. It can generate numerous additional popup, banner, pop-under and in-text link advertisements flooding on your web-browser; gather your personal data such as login details, online searches, etc; run in the background and drag down your Android OS running speed; give more chances for other adware, PUAs even malware to get on your phone.
How Adware gets installed
Usually, adware gets into computers and smartphones as part of a bundle with free software, sharing files and other unsafe apps that users downloaded from the Web. The adware developers pays freeware creators for distributing adware within their apps. Therefore, always download free applications and paid applications from reputable developers and official sites.
How to Remove YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups (removal tutorial)
In the steps below, we’ll provide general help to get rid of YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-up scam. You may find some minor differences in your Android device. No matter, you should be okay if you follow the steps outlined below: remove all suspicious and unknown apps, reset web browsers settings, run free malicious software removal utilities. Certain of the steps below will require you to close this webpage. So, please read the step-by-step instructions carefully, after that bookmark it or open it on your smartphone for later reference.
To remove YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups, please follow the steps below:
- Uninstall unknown and suspicious apps
- Remove YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups using Malwarebytes
- Reset Android browser
- Reset Android phone (Factory Reset)
Remove unknown and suspicious apps
The best way to start removing YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups is to uninstall all unknown and suspicious apps. Using the standard features of Android, you can do it easily and quickly. This step, despite its simplicity, should not be missed, as removing unnecessary and suspicious apps, you can clean your phone of unwanted advertisements, browser redirects, malware, adware and viruses.
First of all, make sure that the Android phone does not have any apps running. To do this, open the list of running applications and remove all apps from it. Another option, just restart the phone, after which do not start anything.
Now you can start removing unnecessary apps. Open Android Phone settings, select APPS here. You will be shown a list of installed applications, similar to the one shown in the following example.
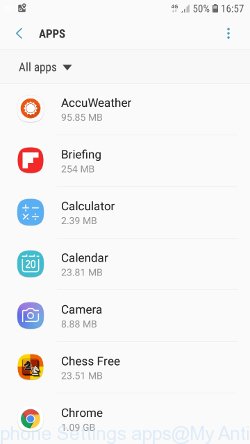
Several times, very carefully review this list, most likely one of the apps listed here is a virus, adware or malware that shows ads or installs unwanted games on your phone. To remove a suspicious app from Android Phone, just click on its name and select UNINSTALL in the window that appears, as shown in the figure below.
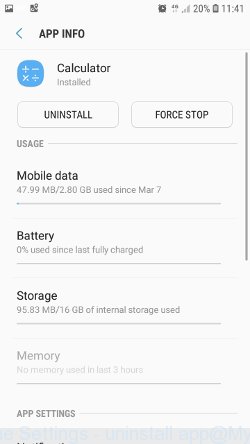
If you can not figure out what to delete and what to leave, use the following criteria for determining adware, malware and viruses. The app is suspicious if: it consumes a lot of memory (for example, it’s called a calculator, and consumes hundreds of megabytes of memory), the app name is completely unfamiliar to you (check the app name through Google search), the app requires strange permissions (for example, a calculator requires permission to send sms and access to the address book). At this stage, you need to be even a bit suspicious than usual.
Remove YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups using Malwarebytes
Malwarebytes Mobile Security (Malwarebytes for Android) is a free app for phones running Android operating system. It can easily find and quickly remove viruses, potentially unwanted programs (PUPs), adware, trojans and other malicious software.
Download Malwarebytes, using the following link, and install it on your phone. After the application is installed, start it. You will see a window similar to the one shown in the example below.
Read the information about the Malwarebytes for Android, and then click “Got it” button.
You will see the main window, as shown in the figure below. Click “Fix now” button.
Malwarebytes will attempt to automatically update the virus database, and then immediately start the full scan procedure. In the process of scanning, Malwarebytes for Android will check your phone for the presence of Trojans, viruses and other malicious programs.
When the scan is completed, Malwarebytes will report the detected viruses and in case of detection of malicious programs, offer to remove them. Just follow the prompts.
To use Malwarebytes for Android, you do not need to buy a premium (paid) version of the app. The first 30 days you can use all the features of this antivirus completely for free, and after 30 days, the device’s auto-protection will be turned off, but you can continue to use Malwarebytes for Android to check your phone for malware and remove it in case of detection.
Reset Android browser
Adware and other malware can change the Android settings. But most often malicious software makes changes to the browser settings, modifying the home page or search engine. Therefore it is very important, after scanning the Android device with antivirus software, also check the browser settings and restore its normal values.
Start the browser. Click on the icon in the form of three points, which is located in the right corner of your phone. In the menu that opens, select Settings.
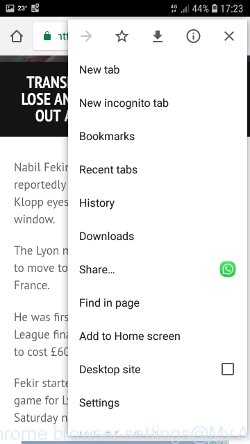
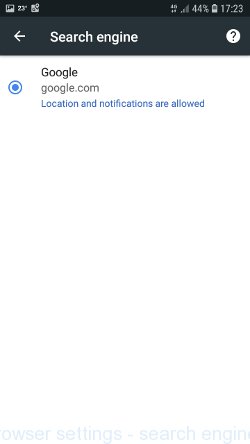
You will see a list of browser settings. Find the “Search Engine” option and click on it. In the window that opens, select Google.
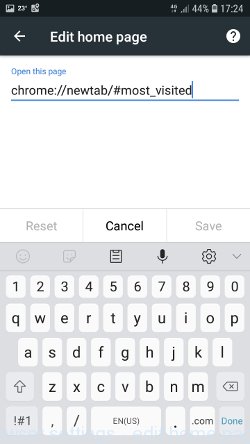
Go back to the list of browser settings. Now click “Home page”. Check that the switch is in the ON position. If necessary, move it to this position. Then click on the line below, which says “Open this page”. In the window that opens, enter the address of your home page or the line “about:blank” (without quotes). In this case, the blank page will be used as the homepage.
In addition to the above, it is also recommended to clear data that was saved by the browser while the phone was infected. To do this, in the list of settings, find the Privacy item and click it. Scroll the page to the bottom until you find “Clear browsing data”, press it. You will see the window as shown in the figure below.
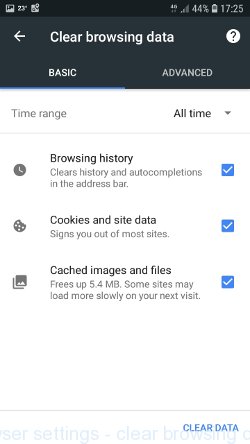
In the “Time range”, select the time period that covers the period when your Android phone was infected with malware, then click “CLEAR DATA” button. During this procedure, your Google account will not be deleted, passwords, bookmarks and other personal information will be saved.
Reset Android phone (Factory Data Reset)
If nothing of the above is helpful and you failed to get rid of YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups manually or using antivirus software, then most likely the malware can only be removed by resetting the phone.
In order to reset Android phone, and thus remove scam pop-ups, do the following. Open Phone Settings, scroll down to General management. Click it. You will see a window similar to the one shown in the pictures below.
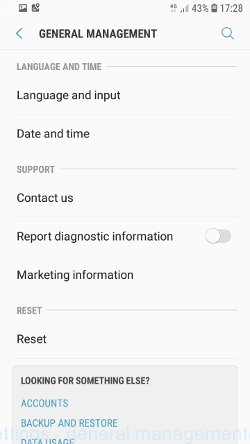
Find the “Reset” option and click on it. You will see a list of possible ways to reset the phone settings, select the “Factory Data Reset” option.
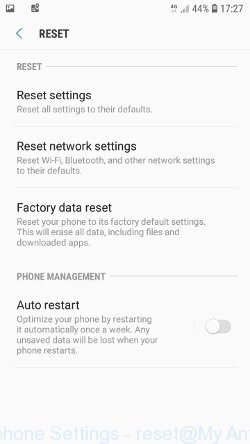
Click “Factory Data Reset” button. ATTENTION! All your personal data from the phone’s internal memory will be deleted, all phone settings will be restored to their original state. The internal memory of the phone will be TOTALLY cleared.
To sum up
After completing the few simple steps outlined above, your Android phone should be free from adware and other malware. Your web-browser will no longer display the YOUR GOOGLE HAS (4) CRITICAL VULNERABILITIES pop-ups. Unfortunately, if the step-by-step guide does not help you, then you have caught a new malicious software, and then the best way – ask for help here.